How to Protect Email with Password Guide

When it comes to securing your digital life, protecting your email is non-negotiable. It all starts with a strong, unique password, but that’s just the beginning of modern email security. True email privacy requires a layered defense, combining a tough passphrase with multi-factor authentication and vigilant account management, especially when using hosted email platforms.
Why Your Email Is the Key to Your Digital Life

It’s easy to think of your email as just another inbox, but it's the master key to your entire online identity. Consider its role: it's the hub for password resets for your bank, notifications from your credit card, and deeply personal conversations. Your email account contains a treasure trove of private data.
If a cybercriminal gains access, they don’t just read your old messages; they get a direct path to hijacking everything else. This is why major hosted email platforms like Gmail and Outlook are such massive targets; one successful break-in can expose a lifetime of sensitive information, completely eroding your email privacy.
The Real-World Impact of a Weak Defense
The fallout from a compromised email is severe. An attacker could reset your banking password, take over your social media, or piece together enough personal data to steal your identity outright. This isn't a theoretical threat; it’s a daily reality that undermines email security for millions.
Password-related breaches remain a primary threat. It’s shocking to learn that 46% of people have had at least one password stolen, and weak credentials were the culprit in 35% of those cases. With over 24 billion credentials from data breaches circulating online each year, it’s no wonder email accounts are a hot commodity. You can dig into more of these eye-opening password statistics on Huntress.com.
Your email password isn't just protecting emails; it's the first line of defense for your bank accounts, social media presence, and personal documents. A single weak link can compromise everything.
Building a Modern Security Mindset
Today, protecting your email is about more than picking a clever word and adding a number. Real email security demands a modern, multi-layered approach that prioritizes both security and privacy.
For a quick overview, here are the most important things you can do right now to lock down your email account.
Quick Guide to Stronger Email Protection
| Security Action | Why It's Critical | Where to Start |
|---|---|---|
| Use a Password Manager | It generates and stores unique, complex passwords, preventing reuse and strengthening overall email security. | Check out trusted options like 1Password or Bitwarden. |
| Enable MFA/2FA | Adds a crucial second security layer, requiring a code from your phone to block unauthorized access. | Look in the "Security" or "Account" settings of your hosted email platform (Gmail, Outlook, etc.). |
| Create a Long Passphrase | A multi-word phrase is much harder to crack, offering a massive boost to your account's primary defense. | Ditch short, complex passwords. String together 4-5 random words. |
This table is just the starting point. In this guide, we'll walk through exactly how to put these strategies into practice, from crafting an unbreakable password to using the advanced security features built into today’s hosted email platforms. Let's turn your inbox from a potential vulnerability into a digital fortress.
Crafting a Truly Unbreakable Email Password
When it comes to locking down your email, you need to forget the old rules. The first step toward real email privacy is to unlearn everything you were taught about just swapping letters for symbols, like turning an "e" into a "3". Modern password-cracking software blows through those simple substitutions in a flash.
The secret to a genuinely strong password isn't about making it complicated—it's about making it long. A short, complex password like P@ssw0rd! might look secure, but it can be cracked almost instantly. A much longer one, even if it seems simpler, is exponentially harder for a computer to guess.
The Power of the Passphrase
So, how do you create a long password you can actually remember? The answer is the passphrase method. This is where you string together several completely unrelated words to create something long, random, and surprisingly easy to recall, forming a cornerstone of your email security.
Instead of wrestling with a jumble of special characters, just think of a sequence of four or five random words.
For example:
- Weak:
MyDogFido123!(This is a bad idea—it uses personal info and a predictable number pattern.) - Strong:
Correct-Horse-Battery-Staple(This is long, totally random, and memorable.)
Using a passphrase immediately boosts your security. The sheer number of characters creates a massive barrier against automated guessing attacks. Every single character you add makes the time required to crack it grow exponentially.
A passphrase creates a "haystack" of possible combinations so enormous that finding the "needle"—your actual password—becomes a computational nightmare for any attacker. This simple shift in strategy is one of the most effective things you can do to secure your email.
What to Avoid at All Costs
Even a great strategy can be ruined by bad habits. When you're creating your password, you have to steer clear of anything that an attacker could easily guess or find out about you.
- Personal Information: Never, ever use the names of your family members, pets, birthdays, or addresses. A quick look at your social media profiles can often give an attacker all of this information, undermining your email privacy.
- Common Words and Phrases: Stay away from dictionary words, famous quotes, or obvious keyboard patterns like "qwerty" or "123456." These are the very first things automated cracking tools will try.
- Sequential or Repeated Characters: Passwords like
password123oraaaaaaare incredibly weak and offer basically zero protection.
Good vs Bad Password Examples
To really see the difference, let’s put it all into a clear comparison. This shows what works and what leaves you wide open.
| Bad Password Examples | Why They Are Weak | Good Password Examples | Why They Are Strong |
|---|---|---|---|
Summer2024! |
It's a predictable pattern that includes the current year. | BlueMountainSingsLoudly |
This is long, uses four random words, and is easy to remember. |
Jsmith#1 |
Based on a name and uses a common number sequence. | Cloud-Rides-Purple-Whistle |
Totally random, memorable, and over 20 characters long. |
P@ssw0rd! |
Uses common symbol substitutions that are easily cracked. | Vivid-Turtle-Juggles-Spoons |
It's unique, nonsensical, and exceptionally long. |
Building a strong password is the foundation of your entire email security setup. If you want to dive deeper into the principles that guide secure system access, a great resource is an official Authentication Password Policy.
Moving Beyond Passwords with MFA and Managers
Let's be honest, even with the best intentions, managing unique, strong passwords for every single online service is a nightmare. This reality, what we call "password fatigue," is why 57% of people admit to reusing old passwords and only a measly 27% bother with random password generators. This is where we need to bring in modern tools to do the heavy lifting for us. If you're curious about the data, these password statistics and user habits paint a pretty clear picture of the problem.
Your Secure Digital Vault: A Password Manager
Think of a password manager as a Fort Knox for your login credentials. Instead of trying to memorize dozens of complicated passphrases, you only have to remember one—the master password that unlocks the vault itself. It’s a beautifully simple concept that completely changes the game for your email security.
These tools do more than just remember your passwords. They generate incredibly long, random, and unique credentials for every single account you own. This one move instantly breaks the dangerous habit of reusing passwords, ensuring each of your accounts is shielded by a credential that's practically impossible to crack.
A password manager is your personal security assistant. It takes on the impossible job of creating and remembering unique passwords, freeing you up to focus on what's important while massively boosting your digital defenses.
Multi-Factor Authentication: The Ultimate Ally
If you do only one thing after reading this guide, make it this: enable Multi-Factor Authentication (MFA). Sometimes called two-factor authentication (2FA), it's the single most powerful step you can take to protect your email. It works by demanding a second piece of proof—a second "factor"—to verify it's really you trying to log in.
This means that even if a cybercriminal manages to steal your password, they're still locked out. They can't get in without that second factor, which is something only you should have.
This infographic gives you a great visual of how adding another authentication factor—like your phone or a physical key—creates a much stronger barrier against attackers.
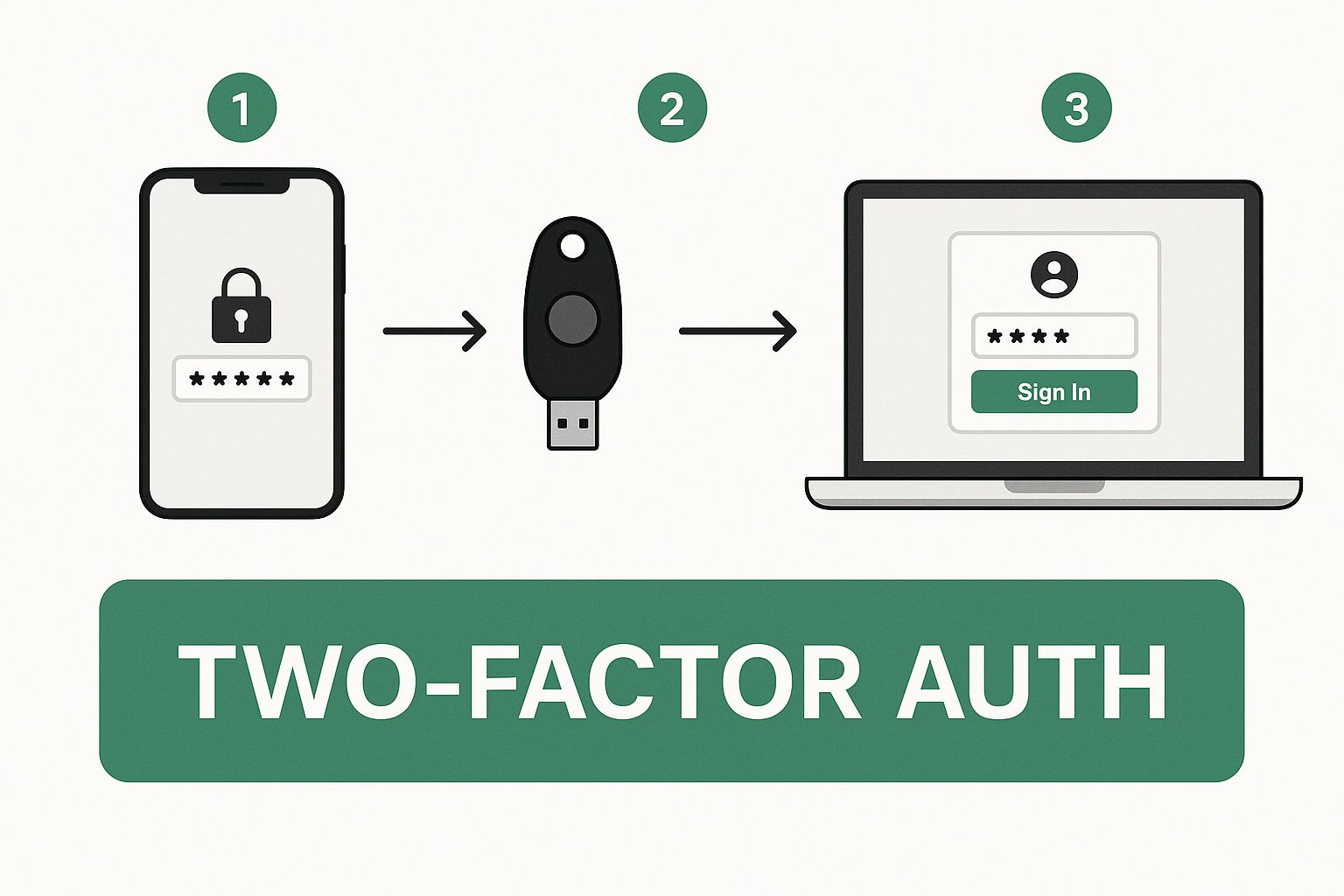
By layering something you know (your password) with something you have (your phone), you build a defense that a simple password could never match on its own.
Choosing Your Second Factor
When it comes to MFA, you have options, and they aren't all created equal. Each method strikes a different balance between convenience and rock-solid email security.
- SMS Text Codes: You get a code sent to your phone via text. While it's certainly better than nothing, this is now seen as the least secure MFA method. It's vulnerable to "SIM-swapping," where a scammer tricks your mobile carrier into giving them control of your phone number.
- Authenticator Apps: Apps like Google Authenticator or Authy generate a fresh, six-digit code on your device every 30 seconds. This is a huge security upgrade from SMS because the code is generated offline on your trusted device, not sent over a vulnerable network.
- Hardware Security Keys: This is a small physical device, like a YubiKey, that you either plug into your computer's USB port or tap on your phone. This is the gold standard for email security. It's nearly impossible for a remote attacker to compromise because they would need to physically steal the key from you.
Turning on MFA in hosted email services like Gmail or Outlook is usually simple and can be found right in the "Security" section of your account settings. If you want to dive deeper into how this all works, our complete guide to multi-factor authentication for email security has you covered. Making the shift away from a password-only mindset is the foundation of modern email privacy.
Auditing Your Hosted Email Platform Settings
A strong password and multi-factor authentication are like having a solid lock on your front door. But what about the security settings within your hosted email platform? These control panels for your data and privacy often go completely ignored.
Hackers know this. They don't always bother with a brute-force attack when they can exploit weak or misconfigured settings. This allows them to maintain a hidden, persistent presence in your account. A quick, regular audit of your platform's settings is crucial for maintaining robust email security.
Reviewing Third-Party App Access
One of the most common ways an attacker compromises email privacy is through third-party apps. Every time you use your Google or Microsoft account to sign up for a new service, you grant it a set of permissions. Over the years, that list of connected apps can become a tangled mess of services you've long since forgotten.
Take a few minutes and dig into your account's security settings. You're looking for a section called something like "Connected Apps" or "Third-Party Access."
- Scrutinize every single app: Do you recognize it? Do you actually still use it?
- Check the permissions: Does that simple photo editing app really need full access to read, send, and delete all your email? Almost certainly not.
- Be aggressive with revoking access: If you don't know what it is or you don't use it anymore, hit "remove." There's zero reason to leave that digital door open.
Think of third-party permissions as spare keys to your digital life. You wouldn't hand them out to strangers, and you’d ask for them back when no longer needed. Your email privacy deserves the same caution.
Inspecting Your Login and Forwarding Rules
The next critical piece of your audit is hunting for signs of unauthorized activity. Clever attackers often set up subtle rules that can go unnoticed for weeks, or even months, silently compromising your email security.
First, pull up your account's recent login history. Most hosted email platforms show a list of recent sessions, complete with the location, IP address, and device type. A login from a city you've never visited is a blaring alarm bell.
This example from Wikipedia illustrates the kind of detailed information you can find, which is invaluable for spotting something out of place.
This data gives you the power to immediately identify and terminate any session that isn't you, stopping an intruder right in their tracks.
Next up—and this is a big one—check your email forwarding and filter rules. A classic hacker move is to create a rule that silently forwards a copy of every incoming email to an address they control. They can sit back and monitor your conversations, steal sensitive data, and plan their next move, all without you having a clue. Go through your settings and delete any forwarding addresses or filters that you didn't create yourself.
Running through these checks is essential for maintaining control over your hosted email account. For a more structured walkthrough, you can follow our complete 7-point email security audit checklist to make sure you don't miss anything. It also helps to understand the security principles happening on the backend; for example, learning how to store passwords securely in the database gives you a better appreciation for the measures your email provider should be taking to protect you.
Spotting Threats That Bypass Strong Passwords

It's a hard truth: the most complicated password in the world won't protect you if a scammer simply tricks you into giving it away. While technical defenses are your first line of defense, cultivating a vigilant mindset—your personal "human firewall"—is just as critical for maintaining email security and privacy.
Attackers have perfected social engineering attacks that prey on basic human psychology, using urgency and fear to make us act before we think. These schemes are dangerously clever because they sidestep your security measures entirely, targeting you instead of your password. Learning their playbook is the only way to see them coming.
The Anatomy of a Modern Phishing Scam
Forget the old, typo-ridden phishing emails of the past. Today's scams are slick, professional, and designed to look and feel completely legitimate. They create a sense of panic that nudges you toward making a critical mistake.
Keep an eye out for these red flags:
- Spoofed Sender Addresses: The display name might say "Microsoft Security," but a closer look at the actual email address reveals a jumble of random letters from an unfamiliar domain. Always, always inspect the full sender details.
- Urgent and Threatening Language: Phrases like "Your account has been compromised!" or "Suspicious login attempt detected!" are engineered to spike your adrenaline and make you click without thinking.
- Malicious Links and Attachments: These emails often contain links that take you to a pixel-perfect clone of a real login page. The goal is simple: to harvest your password and MFA code the moment you try to "sign in."
A healthy dose of skepticism is your best tool for email security. If an email demands you take immediate action, stop. Take a breath, and verify the claim through a separate, trusted channel. That means opening a new browser tab and navigating to the official website yourself, never clicking the link in the email. You can find more practical advice in our guide on how to identify phishing emails.
Dangers Beyond Your Inbox
Threats to your email privacy don't just come from phishing attempts. How and where you check your messages can open up serious vulnerabilities that attackers are more than happy to exploit.
The weakest link in email security is often not the password itself, but the human element. Attackers know that a well-crafted phishing email or an insecure network can bypass even the strongest technical defenses.
One of the biggest culprits is public Wi-Fi. Those free networks at coffee shops, airports, and hotels are often unsecured, making them a playground for attackers. Using what's known as a "man-in-the-middle" attack, they can intercept everything you send and receive—including your email password. The rule of thumb? Always use a trusted VPN on public networks to encrypt your connection and protect your privacy.
And, of course, old-fashioned password cracking is still a massive threat. In a study involving over 160 million simulated cyber-attacks, brute-force password cracking was successful in a staggering 46% of the environments tested. Even worse, once those credentials were stolen, they were successfully used to take over valid accounts in 98% of the breaches. This really drives home how exposed our accounts are when we rely on weak passwords. Staying vigilant against this mix of threats is a huge part of learning how to protect email with a password effectively.
Got Questions About Protecting Your Email?
Even when you're doing everything right, some questions always seem to pop up as you're trying to lock down your email security. Let's tackle some of the most common ones I hear, digging into what really matters for keeping your email private and secure today.
How Often Should I Actually Change My Email Password?
You can officially forget that old advice about changing your passwords every 90 days. That's a relic from a different era. Today, the consensus among security pros is to create an incredibly strong, unique passphrase and stick with it. Only change it if you have a good reason to believe your email security has been compromised.
Think about it: forcing people to change passwords constantly just encourages bad habits. We end up making tiny, predictable tweaks like changing Summer2024! to Fall2024!, which is a gift to any attacker. Your energy is much better spent creating one powerhouse of a password and then layering on Multi-Factor Authentication (MFA). That combination is far more effective.
Is a Longer Password Really Better Than a Super Complicated One?
Absolutely. When it comes to brute-force attacks—where a computer tries to guess your password over and over—length is king. A 16-character password made of simple words is exponentially stronger than a complex 8-character password packed with symbols.
It all comes down to math. A longer password creates a vastly larger pool of possible combinations for a machine to churn through. Of course, the best-case scenario is to have both: a long passphrase that's also complex. That's where a good password manager becomes your best friend, since it can generate and remember passwords that are both incredibly long and ridiculously complex.
"I feel so stupid." – Troy Hunt, Security Expert, after falling for a phishing attack. This quote from a top expert really sticks with me. It’s a powerful reminder that human error is the great equalizer. No matter how strong your password is, staying vigilant and a little bit skeptical is your ultimate defense.
What’s the First Thing I Should Do If My Email Password Was Stolen?
Okay, don't panic, but you do need to move fast and be methodical. The goal is to lock the attacker out and reclaim your account immediately to restore your email security.
Here’s your action plan:
- Change Your Password: This is priority number one. Log in right away and change it to something completely new, strong, and unique.
- Turn on MFA: If it wasn't on before, enable Multi-Factor Authentication now. Use an authenticator app or a physical security key if you can. This is the single most important step you can take.
- Audit Your Account: Go through your recent account activity. Look for sent emails you didn't write, strange new email forwarding rules, or any unfamiliar apps connected to your account.
- Force a Global Logout: Dive into your security settings and find the option to "log out of all active sessions." This will kick the attacker out from any other device they might be using.
- Clean Up Other Accounts: Now, the tedious part. If you reused that password anywhere else—and be honest with yourself—you need to change those passwords too. Start with your most critical accounts, like banking and financial services.
Is It Safe to Let My Browser Save My Email Password?
I get it, it's convenient. But relying on your browser's built-in password manager is a pretty big gamble for your email privacy. If someone gets physical access to your unlocked computer, they can often see all of your saved passwords in plain text with just a few clicks. It's shockingly easy.
A dedicated password manager is a much safer bet. These tools are built from the ground up for security, using strong end-to-end encryption and protecting your entire vault behind a single, strong master password. Plus, they come with extra features like security audits that flag weak or reused passwords, making them a fundamentally better solution for your entire digital life, not just your email.
At Typewire, we believe true email security starts with a platform that’s private by design. We offer secure, private email hosting that puts you in control, completely free from invasive tracking and ads. With our advanced security features and unwavering commitment to user privacy, you can build your digital communications on a foundation you can trust. Explore secure email with Typewire and feel the difference.
How to Protect Email with Password Guide
Posted: 2025-10-19
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31