Email Password Protection A Modern Guide

Let's be honest, we all know we should use strong passwords, but it's easy to get complacent. When it comes to your email, however, "good enough" just isn't. Your email password isn't just another password; it's the master key to your entire digital life.
Think about it. Your inbox is the central hub for password resets, security notifications, and sensitive communications. If a hacker gets in, they don't just have your emails—they have the keys to your kingdom.
Why Your Email Is the Ultimate Target

It’s a scenario I’ve seen play out far too many times. A cybercriminal finds your old, reused password from a past data breach on the dark web. They try it on your primary email, and it works.
Their first move isn't to sift through your family photos. Instead, they immediately go to your banking site, click "Forgot Password," and wait for the reset link to hit your inbox. Then they do the same for your social media, your Amazon account, and any other high-value service connected to that email.
Within minutes, you're locked out of your own life while they’re on a digital shopping spree with your saved credit cards. This isn't just an inconvenience; it's a full-blown identity crisis in the making.
The Ripple Effect of a Single Compromised Email
The domino effect from a single weak email password can be catastrophic. It's the critical vulnerability that connects all your other accounts, and attackers know exactly how to exploit it.
| Initial Breach Point | Immediate Consequence | Secondary Risk Areas | Long-Term Impact |
|---|---|---|---|
| Weak Email Password | Unauthorized access to the inbox. | Password resets for banking, social media, and e-commerce. | Identity theft, reputational damage. |
| Reused Password | Attacker gains access to multiple accounts simultaneously. | Access to saved payment methods and financial data. | Significant financial loss, credit score damage. |
| Phishing Attack | You unknowingly give credentials to a malicious site. | Exposure of private conversations, photos, and documents. | Blackmail, personal and professional data leaks. |
This table shows just how quickly things can escalate. The path from one compromised email to a complete account takeover is a well-worn one for hackers.
A single weak link—your email password—can unravel the entire fabric of your digital life. It's the one point of failure that can compromise everything from your social reputation to your financial stability.
The Problem of "Password Sprawl"
This risk is amplified by what I call "password sprawl." The average person is juggling 70 to 80 passwords, and that number is only going up. By 2025, it's projected there will be 417 billion password-protected accounts worldwide. It's no wonder people reuse passwords, creating a massive attack surface for criminals.
The immediate dangers are what most people think of:
- Identity Theft: Attackers can open new lines of credit or commit fraud in your name.
- Financial Loss: Funds can be drained directly from linked banking or shopping accounts.
- Data Exposure: Sensitive documents, private photos, and confidential conversations stored in your email or cloud storage are suddenly exposed.
The Damage That Lingers
Beyond the initial chaos, the long-term consequences can be even more draining. Rebuilding a tarnished online reputation can impact your career and personal relationships. Recovering from identity theft is a bureaucratic nightmare that can take months or even years to resolve.
Protecting your email isn't just about preventing a hack today. It's about safeguarding your peace of mind for the future. Understanding the nuts and bolts of how your email works can also help; for instance, the protocol your email service uses matters. You can learn more about the differences between IMAP and POP3 to see how data is handled and stored, which has direct security implications.
How to Create Passwords That Actually Protect You
For years, we were all taught the same formula for a "strong" password: take a simple word, capitalize the first letter, add a number, and tack on a symbol. Think turning password into Password1!.
Frankly, that advice is dangerously outdated. Attackers figured this pattern out ages ago. Their software is specifically designed to test for these predictable combinations, making a password like Password1! almost as easy to crack as the original word itself. Real security isn't about following a simple formula; it's about creating something genuinely long and unpredictable.
The Power of Passphrases
A much better way to think about this is using a passphrase. Instead of trying to memorize a random string of characters like 8#k&G!zP, you build your password from a memorable, quirky sentence. This simple shift in thinking helps you create passwords that are both long and random—the two most important factors for security—without being impossible to remember.
The trick is to come up with a strange or vivid image, something completely unique to you that a computer would never guess.
A password's true strength is in its length and unpredictability. A four-word passphrase can be thousands of times stronger than a typical eight-character password because it contains far more randomness, what security pros call 'entropy.'
Let’s walk through an example. Picture this absurd sentence: "My purple cactus sings loudly on Tuesdays."
You could just use the first letter of each word to get Mpcslot. That's a start, but we can make it much, much stronger by mixing in cases, numbers, and symbols inspired by the phrase itself.
Mycan stay asMy(capital M).- Let's swap the 'tu' in
cactusfor a '2' to getcac2s. - Let's replace the 'i' in
singswith an '!' to gets!ngs. - And we'll shorten
Tuesdaysto justTues.
Putting it all together, you get a highly secure password: Mycac2s!ngsTues. It’s long, it’s complex, and it’s tied to a sentence you can actually visualize and remember.
Password Examples: The Good, The Bad, and The Ugly
Let's look at this in practice. Here’s a breakdown of common password habits compared to the passphrase method. You'll see just how easy it is to spot the weak, predictable patterns.
| Password | Security Level | Why It Works (or Doesn't) |
|---|---|---|
| Fluffy1984! | Weak | This is a classic mistake. It uses a common pet name, a birth year, and a standard symbol at the end. It's practically begging to be cracked by anyone with a little personal information. |
| P@ssw0rd123 | Very Weak | This is a prime example of "leetspeak," where letters are swapped for similar-looking numbers and symbols. Automated cracking tools are built to check for these obvious substitutions instantly. |
| 4GreenFrogsJump! | Strong | A simple but effective passphrase. It combines four random words, is well over 15 characters long, and naturally includes numbers and symbols. |
| TheRain_in_Spain7 | Moderate | It's better than a single word, but it's also a famous line from a musical. Attackers' dictionaries are full of common phrases from books, movies, and songs. |
| B3cause$unflow3rs! | Very Strong | This is a fantastic modified passphrase. It's long, uses a creative mix of character types, and is based on a unique thought, making it incredibly difficult to guess or crack. |
The best way to protect your email account is to stop thinking in terms of old, broken formulas. When you start using passphrases, you're not just checking a box for a website's requirements—you're creating passwords that can stand up to modern attacks. The secret is to be a little creative, a little weird, and a whole lot less predictable.
Spotting Your Own Risky Password Habits

Before we can really lock down your email security, we have to start with a moment of honesty. Where are you really starting from? Most people have a few bad password habits, and they often don't realize just how much risk they're creating. These aren't just abstract threats; they're wide-open doors for attackers.
Take a hard look at your current passwords. Do any of them contain your pet’s name, your anniversary, or the street you grew up on? This kind of personal info is often surprisingly public or simple for an outsider to guess, making it a terrible choice for a password. A password like Buddy2023! might feel personal and safe, but it’s one of the first things a hacker will try.
The same goes for sequential passwords like Summer2024 or Q4report_2024. These are dangerously predictable. Hackers don’t sit there guessing these one by one—they use automated software that blasts through millions of common patterns and predictable sequences in seconds.
The Problem with Password Reuse
I've seen it time and time again: the single most dangerous habit is using the same password for different websites. It’s an understandable shortcut, but it creates a domino effect that can be devastating.
Here's how it plays out: a minor website you signed up for years ago gets breached—and it happens all the time. Your email and password from that site are now in the hands of attackers. They immediately take that list and try it on high-value accounts like your Gmail, Outlook, and, yes, your online banking.
This isn't some rare, unlucky event. It’s an epidemic. An incredible 78% of users globally admit to reusing passwords. This one habit is a major reason why around 36% of cloud data breaches happen—attackers just waltz in using perfectly valid credentials they stole from somewhere else. If you want to go deeper, you can explore more of these password statistics and their impact to see just how widespread this is.
Even security experts can get caught off guard. It's easy to think "it won't happen to me," but a single moment of distraction is all it takes for a well-crafted phishing attack to succeed, proving that no one is immune.
Unsafe Storage Is Just as Risky
Creating a strong password is only half the battle. Where you keep it matters just as much. If you’re jotting down passwords in a digital note, a plain text file, or a spreadsheet, you’re essentially undoing all your hard work.
Think about these common but insecure methods. Are you guilty of any?
- The 'Passwords.docx' file: I can tell you from experience, this is one of the first things malware and hackers look for when they get into a computer. It's the digital equivalent of leaving your key under the doormat.
- A note in your phone's app: It’s convenient, but these apps are rarely encrypted. If your phone is lost, stolen, or hacked, those passwords are up for grabs.
- Sticky notes on your monitor: This one might seem obvious, but you’d be surprised how often it happens. It exposes your most sensitive info to anyone who can see your desk.
Each of these habits turns a strong password into a weak link. Recognizing these patterns in your own behavior is the critical first step. From here, we can start building a real email password protection strategy that moves you from habits of convenience to practices built on security.
Put Your Security on Autopilot with a Password Manager

Let’s be honest. Trying to invent, and then somehow remember, a unique and complex password for every single online account is a losing battle. Nobody can do it. So, it's time to stop trying and hand that impossible job over to a tool designed specifically for it.
Enter the password manager. It’s essentially a super-secure, encrypted digital vault for all your logins. You just need to remember one strong master password to unlock it. Inside, the manager not only stores your credentials but can also generate incredibly strong, random passwords for every site you use.
Now, a common question I hear is, "Isn't it risky to put all my passwords in one basket?" It’s a fair point. But the alternative—reusing the same password everywhere or using simple variations—is proven to be far, far riskier. Good password managers use a zero-knowledge architecture. This means even the company that makes the software can't see your data. Your information is encrypted right on your device before it ever goes to the cloud.
Choosing and Setting Up Your Manager
Getting started is much easier than you probably think. First, pick a reputable provider. Look for well-known names with a long track record of security and transparency—brands like 1Password or Bitwarden are great places to start. Many have excellent free versions that are more than enough to get you going.
Once you’ve picked one, the setup is pretty straightforward:
- Create your account and set up a very strong master password. This is the one password you absolutely have to remember, so make it a good passphrase like we talked about earlier.
- Save your recovery key. Print it out and put it somewhere physically safe, like a fireproof box or a safe deposit box. This is your lifeline if you forget your master password.
- Install the browser extension and the mobile app. This is what makes the whole system feel like magic.
The browser extension is what really puts your security on autopilot. It automatically recognizes login fields, fills your credentials with a click, and prompts you to save new passwords to your vault. All the friction of using unique passwords just disappears.
The biggest enemy of good password security is inconvenience. A password manager flips that script, making the most secure option the easiest one.
Transform Your Security Habits Overnight
This is where a password manager truly shines—it completely changes how you interact with passwords. Instead of racking your brain for a new login, you'll just let the generator create something like v9#K@z!pG4^tB*r for you. You don't have to see it, type it, or remember it. The tool does all the work.
This simple change is becoming a cornerstone of modern email password protection. A 2024 report revealed that 36% of American adults now use a password manager. The impact is significant: those users saw a dramatic drop in security incidents, with only 17% reporting credential theft compared to 32% of non-users. You can dive deeper into how these tools are shaping security trends in recent studies.
Even the pros get caught off guard. Security expert Troy Hunt famously shared how he fell for a sophisticated phishing attack that stole his credentials, despite his expertise. This is where a password manager offers a hidden benefit. Its autofill feature is one of your best guards against phishing because it’s tied to the website's real address. If you land on a convincing fake site, the password manager simply won't offer to fill in your login details.
This small, automated check protects you even when you're distracted. Using a password manager isn't just about convenience; it’s about building a powerful, automated defense system for your entire digital life.
Adding Your Next Layer of Digital Armor with MFA
Even with an unbreakable passphrase and a top-notch password manager, your password can still get stolen. It happens more than you think. This is precisely why email password protection shouldn't stop at just the password. You need to add another layer, and that layer is Multi-Factor Authentication (MFA), which you might also hear called Two-Factor Authentication (2FA).
Think of it this way: your password is like the key to your house. If a thief steals that key, they can walk right in. But what if you also have a deadbolt that requires a unique, secondary key? That's MFA. It's a second piece of proof that you're really you. Even if a hacker has your password, they're stopped cold because they don't have that second "key"—like a code from your phone or a tap on a physical device.
The difference it makes is staggering. Just look at how dramatically the risk of a breach drops once MFA is in the picture.
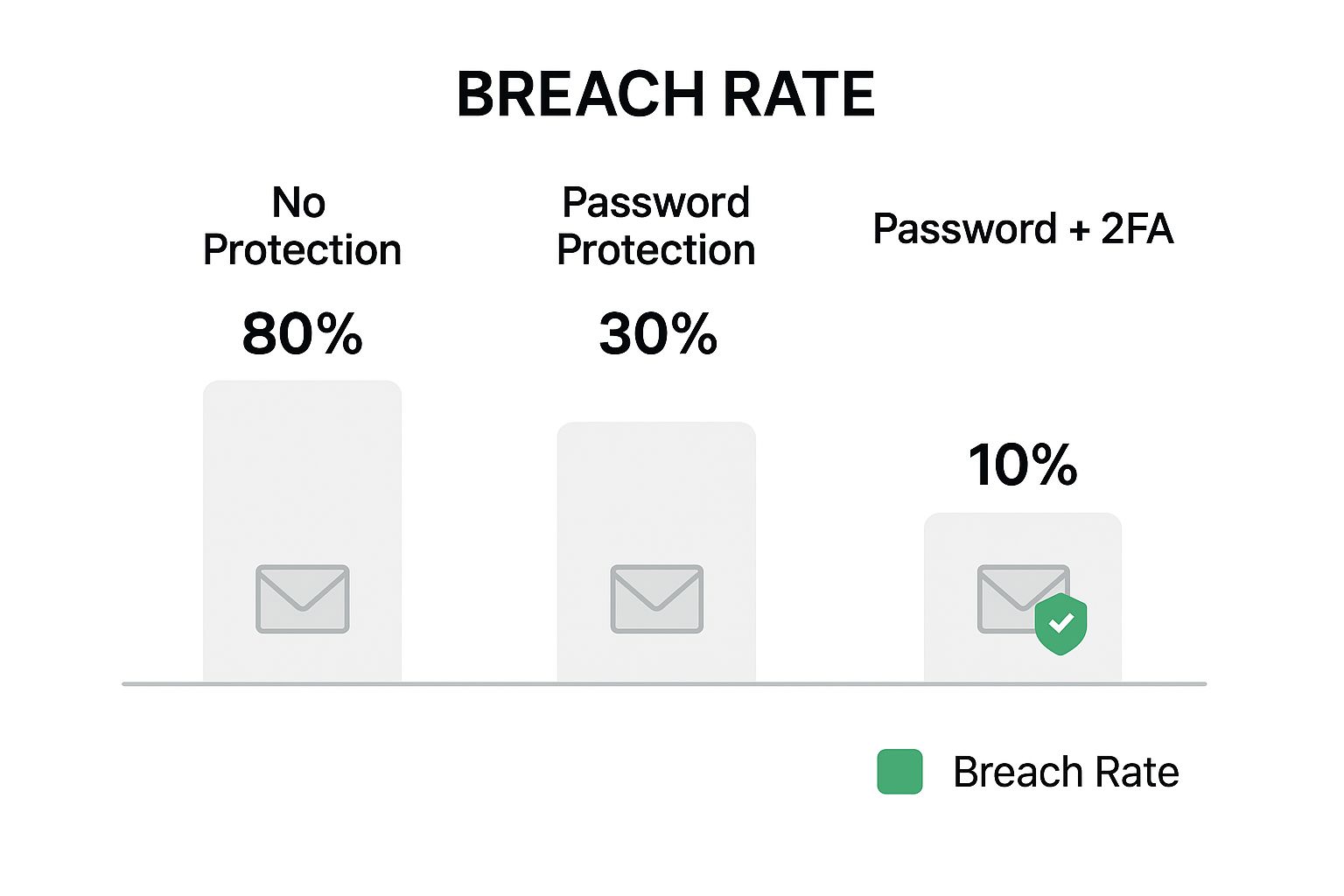
The numbers speak for themselves. A password helps, but adding that second factor is what truly fortifies your account against takeover.
Choosing Your Multi-Factor Authentication Method
So, you're ready to enable MFA. Great! But you'll notice there are a few different types. They all offer a different balance of security versus convenience, so it’s worth knowing what you’re choosing.
A comparison of common MFA types to help you decide which one offers the best balance of security and convenience for your needs.
| MFA Method | Security Level | Ease of Use | Best For |
|---|---|---|---|
| SMS/Text Message Codes | Moderate | High | Basic protection for less sensitive accounts; it’s certainly better than nothing. |
| Authenticator Apps | High | Medium | Securing your most important accounts, like email, banking, and social media. (e.g., Google Authenticator, Authy) |
| Physical Security Keys | Very High | Low | Maximum, phishing-resistant protection for truly critical accounts. (e.g., YubiKey) |
Let's be clear: while getting a code via text message is the most familiar method, it's also the most vulnerable. Hackers can use an attack called "SIM-swapping" to hijack your phone number and intercept those codes. It’s a real threat.
A much safer bet is using an authenticator app, which generates time-sensitive codes right on your device, completely separate from your phone number. For the ultimate security, nothing beats a physical key. It requires you to have the device with you, making it nearly impossible for a remote attacker to get in.
How to Turn on MFA for Your Email
Enabling MFA is probably the single most effective security measure you can take, and thankfully, it’s pretty simple to set up.
- For Gmail: Head to your Google Account settings, find the "Security" tab, and look for "2-Step Verification." From there, it’ll walk you through adding your preferred method. I strongly recommend using an authenticator app.
- For Outlook: In your Microsoft Account, go to the "Security" dashboard. Click on "Advanced security options," and then find the option to turn on two-step verification.
Activating MFA changes the game entirely. Your account goes from being protected by something you know (your password) to being protected by something you know and something you have (your phone or a physical key). That simple change creates a massive headache for attackers.
With MFA enabled, your account login is rock-solid. But what about the messages themselves? Securing your account is one thing; sending messages securely is another. For anyone interested in taking that next step, this practical guide to sending secure email dives into encrypting your communications. When you pair strong account security with safe sending habits, you build a truly comprehensive defense.
Common Questions About Email Password Protection
Even with the best intentions, you're bound to run into some practical questions when you start overhauling your email security. It's a process, and a few common hangups tend to trip people up. Let's walk through some of the most frequent ones I hear.
How Often Should I Really Change My Password?
For years, we were all told to change our passwords every 90 days. That advice is now officially outdated.
If you've followed the steps to create a truly strong, unique passphrase and have enabled Multi-Factor Authentication (MFA), there's no need for a fixed change schedule. A powerful, one-of-a-kind password is much more secure than rotating through weaker, predictable ones.
So, when should you change it? The new rule is simple: change your password immediately only under specific circumstances.
- You see suspicious activity and think your account might be compromised.
- A service you use—any service where you've used that email—announces a data breach.
The focus has shifted from frequency to strength. Your energy is better spent creating an unbreakable password from the start, rather than constantly changing a mediocre one.
Are Free Password Managers Actually Safe?
This question comes up a lot, and it's a good one. The short answer is yes, for the most part.
Reputable password managers like Bitwarden or Proton Pass offer free versions that use the same robust, zero-knowledge encryption as their paid plans. This means even the company itself can't see your passwords. Using a trusted free manager is infinitely safer than reusing passwords or scribbling them on sticky notes.
The paid versions usually just add bells and whistles like extra secure storage or emergency access features, which are nice to have but not essential for everyone.
What if I Forget My Master Password?
This is the big one. It's the key to your entire digital kingdom, so what happens if you lose it? Let's be clear: this is a serious problem.
Your password manager is designed with zero-knowledge architecture. This is a security feature, not a bug. It means no one—not even the company's support team—can recover your master password for you. If you forget it, you're locked out.
The only way back in is through the recovery methods you set up beforehand. This almost always involves a recovery key—a very long, unique code generated when you create your account.
You absolutely must save this key. Print it out and store it somewhere physically secure, like a fireproof safe or a bank deposit box. Do not save a digital copy on your computer. Think of it as your emergency escape hatch; setting it up properly is the most important thing you'll do.
For more on locking down your communications, our guide on how to send a password protected email the right way has some excellent advanced tips.
Ready to take back control of your inbox? With Typewire, you get secure, private email hosting that puts you in charge. Say goodbye to tracking, ads, and data mining. Start your free 7-day trial and experience email the way it should be. Explore Typewire today.
Email Password Protection A Modern Guide
Posted: 2025-07-29
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31