How to Authenticate Email: Real-World Setup Guide That Works

Why Email Authentication Became Make-or-Break for Business
Remember those annoying situations where important emails mysteriously disappear into the spam folder? Or even worse, have you seen a phishing email pretending to be your company, damaging your brand's reputation? These aren't just hypothetical situations – they happen every day to businesses that haven't prioritized email authentication.
This isn't just about missing a few messages; it directly affects your bottom line. I've talked to IT professionals who've lost deals because crucial emails never reached the client. Others have shared stories of damaging phishing attacks costing them money and customer trust. The stakes are definitely higher now.
The online world is changing, and cybercriminals are getting smarter about finding vulnerabilities. Email providers like Gmail and Outlook are responding with tighter security, and they're suspicious of emails that aren't authenticated. If you aren't actively authenticating your emails, you’re basically letting spam filters and phishers control your domain. Check out this helpful guide: What is Email Authentication: Your Complete Security Guide.
The pressure isn’t just from email providers, either. Regulations are also pushing businesses to take email authentication seriously. The global email industry saw big changes in 2024-2025, with more regulations and a jump in Business Email Compromise (BEC) attacks. BEC attacks made up a whopping 73% of reported cyber incidents in 2024. DMARC has become a key defense, with organizations like the PCI Security Standards Council pushing for its adoption. This has led to more businesses using DMARC, with nearly 54% of email senders implementing it. For more on BEC attacks, take a look at these stats: Discover more insights into BEC statistics.
Stricter authentication isn’t a passing trend; it’s a permanent change in how we do business online. It's like leaving your office unlocked at night – you just wouldn't do it. Email authentication is like locking your doors, protecting your business and keeping your clients' trust. Proper email authentication isn't a technical extra anymore—it’s absolutely essential. It’s the difference between a secure online presence and risking real damage to your business.
Making Sense of SPF, DKIM, and DMARC Without the Jargon

Email authentication. Sounds complicated, right? Like a bunch of acronyms dreamt up by tech wizards just to confuse us. But trust me, on a platform like Typewire, getting your head around these protocols is key. Think of your email security like securing your office – multiple locks are better than one.
SPF: Your Front-Line Security
SPF (Sender Policy Framework) is that first line of defense. It’s like the security guard at the front desk, checking IDs. SPF verifies that the server sending email on behalf of your domain is actually authorized to do so. This stops spoofing – where bad guys try to send emails pretending to be you. So, if someone tries to send an email pretending to be from yourdomain.com, but their server isn’t on your approved list, SPF flags it as suspicious.
Imagine how much damage could be done if someone spoofed your company’s email address. Lost trust, phishing scams…it’s not a pretty picture. SPF helps prevent that.
DKIM: The Tamper-Proof Seal
Next, we’ve got DKIM (DomainKeys Identified Mail). Think of the tamper-evident seal on a medicine bottle. DKIM does something similar for your emails. It adds a digital signature, guaranteeing the message hasn't been messed with in transit. This protects your brand reputation by preventing malicious modifications – things like changing payment details or injecting nasty links.
Customer trust is everything these days, and DKIM helps you maintain it.
DMARC: The Security Orchestrator
Finally, there’s DMARC (Domain-based Message Authentication, Reporting, and Conformance). This is the big boss, the security coordinator overseeing the whole operation. DMARC tells receiving servers what to do if an email fails SPF or DKIM checks. Usually, it means sending the email to spam, or even blocking it entirely.
But DMARC does more than just block. It also provides crucial reports, showing you who’s sending emails using your domain. This can help uncover hidden security issues or even highlight misconfigurations you weren’t aware of. It’s like having a security audit built right in.
To really lock down your email security, you need all three protocols working together. They're like layers of security, each playing a distinct role. Just having one or two is like having a great lock on the front door, but leaving a window open.
Let's break down the key differences with a comparison table:
Email Authentication Protocols Comparison
| Protocol | Primary Function | Protection Level | Implementation Complexity | Failure Impact |
|---|---|---|---|---|
| SPF | Verifies sending mail server | Basic | Relatively simple | Email might be marked as spam |
| DKIM | Verifies message integrity | Moderate | More complex than SPF | Email might be marked as spam |
| DMARC | Defines actions for failed SPF/DKIM | Advanced | Most complex | Email can be rejected or sent to spam, provides reports |
This table helps visualize how these protocols work together, providing a layered approach to email security.
So, while setting up SPF, DKIM, and DMARC might seem a little daunting at first, the peace of mind and enhanced security they offer is well worth the effort. It's an investment in your brand's reputation and your customer's trust, ensuring that your Typewire emails are delivered securely.
SPF Records That Actually Protect Your Domain
Let's be honest, SPF records can be tricky. They look simple enough, but I've seen countless businesses, even those using platforms like Typewire, get tripped up. They end up with SPF records that either block their own legitimate emails or leave gaping security holes. So, let's break down how to create SPF records that actually do their job.
Common SPF Mistakes That Trip People Up
One common mistake is forgetting about those other services you use. Think about your marketing team. Do they use Mailchimp, or another email marketing platform? If you don't include these platforms in your SPF record, their emails might get blocked. It's like giving your security guard a list of authorized personnel but forgetting to include the cleaning crew – they're legitimate, but they'll get turned away!
Another common gotcha is the 10-lookup limit. SPF records work by checking a chain of DNS records. If your SPF record needs more than 10 lookups, the check fails. This can happen even if the sending server is legitimate. This often trips people up when they use multiple include mechanisms. It's like asking your security guard to check 15 different ID databases – they'll just give up!
Building a Rock-Solid SPF Record: Real-World Examples
Let's say your business uses Typewire for your main email and Mailchimp for marketing. A good SPF record might look something like this (simplified, of course): v=spf1 include:typewire.com include:servers.mcsv.net -all. This gives both Typewire and Mailchimp the green light to send emails on your behalf. The -all at the end is a strict instruction, telling receiving servers to reject any emails not authorized by the includes. It's your way of saying, "If it's not on the list, it's not coming in."
Now, imagine a more complex setup: Typewire for general email, Mailchimp for marketing, and a third-party CRM sending transactional emails. You'll need to include all three in your SPF record. This is where hitting that 10-lookup limit can become a problem. A good strategy is to use mechanisms like a and mx sparingly and rely on includes for third-party services whenever you can. You’re basically simplifying things for the receiving server.
Testing and Fine-Tuning for Optimal Performance
Setting up your SPF record is only half the battle. You absolutely have to test it. Several online tools can help you check your SPF record and find any potential issues before they affect your email deliverability. It’s like a fire drill – better to make sure everything works in a test run than during a real emergency.
The goal isn't to create the most restrictive SPF record imaginable. It's about finding the right balance between security and making sure your emails actually get through. A poorly configured SPF record can be worse than none at all. By understanding the common problems and following best practices, you can create an SPF record that protects your domain and ensures your legitimate emails reach your customers. This is more than just a technical thing; it’s key to protecting your online reputation and building trust. Email authentication is more and more important in how we communicate online. Just like physical security matters for your office, email authentication on platforms like Typewire acts as a virtual security guard, protecting your communications and strengthening your brand’s online presence.
DKIM Setup: Your Email's Digital Fingerprint System
DKIM is often considered the trickiest part of email authentication to wrap your head around. But trust me, once you understand the basics, it’s not that intimidating. Think of DKIM as giving your emails a unique digital fingerprint, verifying they’re genuinely from you and haven’t been messed with in transit.
Understanding the Public-Private Key System
DKIM uses a clever two-key system: public and private keys. Your private key, which you guard like a precious secret, is used to create a signature for your outgoing emails. This is your personal seal of approval. The public key, which you publish in your DNS records, lets receiving servers check that signature. It’s like a public directory of fingerprints. If the signature matches the fingerprint on file, the email is authenticated.
This public-private key combo is essential for strong email authentication. It's all about combining secrecy with public verification.
Generating and Installing Your DKIM Keys
Generating DKIM keys usually happens behind the scenes within your email platform or hosting provider. With Typewire, it's typically automated, making it easy and secure. You’ll get a public key that you’ll need to add to your DNS records. This allows receiving servers to access the public key and verify the signatures on your emails.
Getting these keys installed correctly is critical. Incorrect DNS records will cause authentication failures. It’s like putting the wrong fingerprint in the database – the system won’t be able to verify anything.
Key Rotation: Keeping Your Email Secure
Like passwords, DKIM keys should be refreshed regularly for optimal security. Key rotation involves generating a new set of keys and updating your DNS records. While you can do this manually, many platforms like Typewire offer automated or simplified key rotation, minimizing any headaches.
Regularly refreshing your keys is essential for maintaining a strong, secure email authentication setup.
Troubleshooting Common DKIM Failures
Even with a perfect setup, you might still run into DKIM problems. A common culprit is a key mismatch, where the public key in your DNS doesn't match the private key used to sign the email. This often happens if the DNS records aren't updated correctly during key rotation. Another issue is signature tampering, where the email’s content is altered after it’s signed.
Being able to identify and fix these issues is key to ensuring your DKIM authentication is doing its job. Regular monitoring and testing are your friends here.
Advanced DKIM for Enhanced Security
Beyond the basics, DKIM has some powerful extra features. You can implement DKIM signing for subdomains, which authenticates emails from different areas of your organization. You can also set up multiple selectors, useful for isolating problems with specific email streams. These advanced features offer greater security and flexibility when managing complex email systems.
By understanding DKIM and how to implement it, you’re well on your way to ensuring your Typewire emails arrive safe and sound. This isn’t just about ticking technical boxes; it’s about protecting your reputation, building trust with your audience, and making sure your message gets through.
DMARC Implementation: Your Email Security Control Center
DMARC brings all your email authentication efforts together. But it's also where things can go wrong, even on secure platforms like Typewire. The trick isn't jumping to the strictest settings. It's a measured, data-driven approach. This protects your domain without accidentally blocking legitimate emails. Imagine setting up a home alarm system – you wouldn't immediately crank the sensitivity to max, right? You'd test and adjust to avoid false alarms.
A Gradual Approach to DMARC: Monitoring and Adjustment
Effective DMARC starts with monitoring. This lets you see what’s happening before enforcing policies. Think of it like listening to your security system’s sensors before activating the alarms. You'll learn who's sending email using your domain, if they're authenticated correctly, and spot potential issues. This data is invaluable.
Next, gradually increase your protection levels based on this data. This ensures tighter security without disrupting real emails. It's like carefully adjusting your security system's sensitivity until it's just right – catching real threats, not harmless events.
The infographic below visualizes the three-step DMARC process: collecting reports, analyzing authentication pass rates, and summarizing compliance. It highlights the iterative nature of DMARC – analyze, refine, repeat.
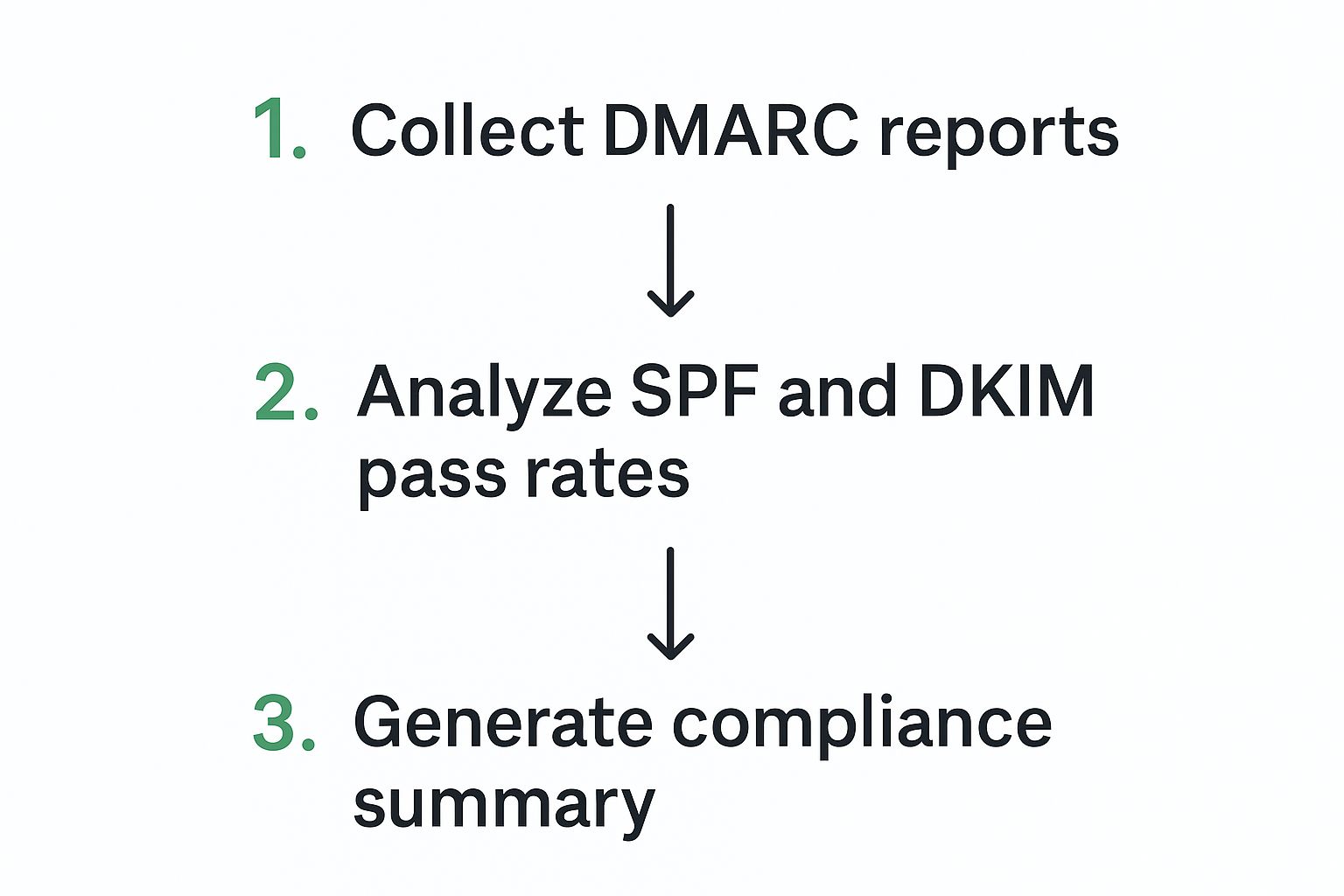
As the infographic shows, analyzing SPF and DKIM pass rates within DMARC reports helps pinpoint authentication gaps. You can then refine configurations for better compliance and security. It's about using data to make decisions, not just hoping for the best.
Understanding DMARC Reports: Your Email Security Map
DMARC reports are powerful tools. They offer a detailed view of your email authentication landscape, showing which emails pass or fail SPF and DKIM. It's like a detailed map of your security system’s coverage, revealing strengths and vulnerabilities. This helps you identify legitimate senders you might have missed, spot potential phishing attempts, and fine-tune your SPF and DKIM settings.
For example, I once helped a company discover a forgotten marketing tool sending emails without proper authentication, thanks to their DMARC reports. They fixed it before it impacted their deliverability. You’d be surprised how often these "hidden" senders appear, even on platforms like Typewire.
Setting the Right DMARC Policy: Finding Your Balance
Once you understand your email traffic through DMARC reports, you can configure your DMARC policy. This tells receiving servers how to handle emails that fail authentication. Start with a "none" policy (just monitoring), then move to "quarantine" (sending suspicious emails to spam), and finally "reject" (blocking unauthenticated emails completely).
Choose a policy that fits your needs and risk tolerance. Too aggressive, and you might block legitimate emails, impacting your business. It’s a balancing act between security and smooth communication. By the way, if you're looking to optimize your email campaigns, our article on dark mode email might be helpful: Check out our guide on: Dark Mode Email Tips.
Avoiding Common DMARC Pitfalls: Lessons Learned
Implementing a strict "reject" policy too early is a common pitfall. This can backfire, blocking legitimate emails and frustrating customers. I've seen it happen firsthand, causing unnecessary disruption. Another common mistake is misinterpreting DMARC reports, which can lead to incorrect configuration changes.
DMARC isn’t a one-time fix. It's an ongoing process of building a sustainable email authentication strategy that adapts with your business. By understanding DMARC reports, you can fine-tune your setup for long-term success on Typewire and beyond. Consistent, data-driven adjustments are key to ensuring your emails reach their destination while keeping your domain safe.
This table outlines a safe and effective strategy for implementing DMARC:
DMARC Policy Progression Strategy: Recommended timeline and settings for safely implementing DMARC from monitoring to enforcement
| Implementation Phase | Policy Setting | Duration | Key Actions | Success Metrics |
|---|---|---|---|---|
| Monitoring | none | 1-2 weeks | Gather baseline data, identify sending sources | Volume of DMARC reports, understanding of email flow |
| Quarantine | quarantine | 2-4 weeks | Monitor quarantined emails, adjust SPF/DKIM as needed | Reduced volume of quarantined emails |
| Enforcement | reject | Ongoing | Continuously monitor reports, fine-tune configurations | Low to zero unauthenticated emails reaching inbox |
This phased approach allows you to gain valuable insights into your email ecosystem before implementing stricter policies, minimizing the risk of disruptions. It also allows for adjustments along the way based on real-world data.
Advanced Email Security: Beyond Basic Authentication
Alright, so you've laid the groundwork. Your SPF, DKIM, and DMARC are all set up on your Typewire account. That’s fantastic! But just like a solid house needs more than just a foundation, your email security requires more than the basics. Think of SPF, DKIM, and DMARC as the foundation, and now we're going to build the walls, add some strong doors, and install a top-notch security system.
Multi-Factor Authentication: Double-Locking Your Email
Let's talk about Multi-Factor Authentication (MFA). You're probably already familiar with it from your bank and other important accounts. It’s equally vital for your email. It's like adding a deadbolt to your front door. Someone might get your key (password), but they're not getting in without that second factor.
And MFA isn't just a good idea, it's becoming essential. The global MFA market is expected to hit $17.76 billion by 2025. That tells you something about how seriously people are taking this. What’s interesting is that 95% of employees actually prefer software-based MFA because it’s just easier to use. People want security, but they want it to be convenient too. Want to dive deeper into these trends? Check this out: Discover more insights into MFA Statistics. The takeaway? With MFA enabled on Typewire, even if someone snags your password through a phishing scam, they’re locked out without that second authentication factor.
Emerging Authentication Technologies
MFA is the standard, but the world of authentication is constantly evolving. Biometrics, like fingerprint scanning and facial recognition, are adding another layer of security. And new protocols like WebAuthn are paving the way for a passwordless future. These might not be essential for every business right now, but they're worth exploring. It's like upgrading your home security from a basic alarm system to a full-blown smart home setup.
Threat Detection and Response: Staying Ahead of the Curve
Authentication is just the beginning. You also need to keep a close eye on your email traffic for anything suspicious. Advanced threat detection tools can analyze your incoming and outgoing emails, looking for patterns that might indicate phishing attempts, malware, or other threats. Think of these tools as security cameras constantly scanning your property. For more on email security best practices, check out this article: Read also: 8 Email Security Best Practices to Implement Now.
And just as important is having a solid incident response plan. What if, despite all your precautions, someone does manage to breach your security? A clear plan will minimize the damage and get you back on your feet quickly. It's like having a fire escape route – you hope you'll never need it, but it’s critical to have one in place.
Scaling Your Email Security: From Small Business to Enterprise
As your business grows, so will your email security needs. The good news is there are solutions for every size and budget. Smaller businesses can find affordable options that offer essential protection. Larger enterprises might require more sophisticated systems, like secure email gateways, to handle the increased volume and complexity of their email traffic. Think of it like scaling up your home security system as you add rooms and acquire valuable possessions.
By being proactive and implementing these advanced security measures, you're not just protecting your email; you're protecting your entire business. It's an investment in your peace of mind and the trust of your customers. It's all about building a secure and robust email ecosystem, both on Typewire and beyond.
Maintaining Your Email Authentication for Long-Term Success
Setting up email authentication (SPF, DKIM, DMARC) is like building a solid foundation for your house. It's essential, but the job doesn't end there. You need ongoing maintenance to keep everything running smoothly. Think of it like tending a garden – regular weeding and pruning are necessary for healthy growth. Email authentication, especially on platforms like Typewire, demands the same kind of attention.
Monitoring and Alerting: Staying Ahead of Issues
The best defense is a good offense. Proactive monitoring helps catch potential email authentication problems before they impact your deliverability. Several tools and services constantly monitor your authentication status, sending alerts if something goes amiss. This isn't about obsessively checking your settings every five minutes. It's about having a smart system in place that notifies you of real issues, not minor fluctuations. It’s like having a smoke detector – you want to be alerted to a real fire, not burnt toast.
Tools like MXToolbox are invaluable for monitoring your email setup. This screenshot shows some of the checks you can perform. Green checkmarks are a good sign, but regular use of these diagnostic tools helps spot and address problems early on. Think of it as your email health check-up.
Regular Reviews and Updates: Adapting to Change
Businesses are always evolving, and your email authentication needs to adapt. New services, vendors, or even seasonal changes can affect your configuration. Regularly reviewing your SPF, DKIM, and DMARC settings ensures they align with your current email practices. How often? Quarterly is a good starting point, but more frequent reviews might be needed if your email environment is particularly dynamic. It’s like changing the oil in your car – regular maintenance prevents bigger problems down the line.
Handling Business Changes: Navigating Transitions Smoothly
Significant changes, like mergers, rebrandings, or platform migrations, require extra attention to email authentication. These transitions can drastically impact your sending sources, domains, and overall infrastructure. Careful planning is key for a smooth transition that protects your email deliverability. It's like moving to a new house – you need to update your address with everyone to ensure your mail arrives.
The Human Element: Documentation and Training
Email authentication isn't purely technical. The human factor plays a vital role. Thoroughly document your setup, including configurations, policies, and troubleshooting steps. Train your team on authentication management and maintenance. This ensures that your email security remains strong, even with personnel changes. It's like having a well-documented emergency plan – everyone knows what to do, not just one person.
Start your free trial with Typewire and experience the benefits of secure and private email hosting.
How to Authenticate Email: Real-World Setup Guide That Works
Posted: 2025-06-11
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27