What Is End-to-End Encryption? Explained Simply

End-to-end encryption (often called E2EE) is a way of securing communication so that a message is scrambled on your device and can only be unscrambled by the person you're sending it to. Think of it as creating a private, digital tunnel where no one in the middle can peek inside—not even the company that runs the app.
What Is End-to-End Encryption in Simple Terms
Let's use an analogy. Imagine you want to mail a sensitive document. Instead of just putting it in an envelope, you lock it in a special box. You don't have the key to open it once it's locked. Only your friend, the recipient, has the one and only key that can unlock it. This is exactly what end-to-end encryption does for your digital messages, emails, and files.
This security method locks down your information on your device before it even hits the internet. It then travels across networks as a scrambled, unreadable mess. Only when it safely arrives on the recipient's device can it be decrypted with their unique key.
The Digital Bodyguard for Your Data
This process makes it impossible for anyone to snoop on your private conversations. Your internet service provider, the app's developers, or a cybercriminal who manages to intercept the data will see nothing but a jumble of meaningless characters. It’s a powerful layer of privacy that is no longer a "nice-to-have," but a necessity.
The growing demand for this level of security speaks for itself. The market for end-to-end email encryption is projected to hit USD 54.4 billion by 2034, showing just how critical it has become for individuals and businesses alike. You can dig into more data on the secure email market and its growth to see the trend.
End-to-end encryption guarantees that only the sender and receiver can ever access the message content. It transforms data into a secret that can only be unlocked at its final destination, providing true confidentiality.
To really get a feel for its value, it’s helpful to see how E2EE stacks up against other common types of data protection.
Encryption Types at a Glance
Each encryption method has its place, but they offer very different levels of security. This table breaks down where and how they protect your data.
| Feature | End-to-End Encryption (E2EE) | Encryption in Transit (TLS/SSL) | Encryption at Rest |
|---|---|---|---|
| Protection Point | From sender's device to recipient's device | Only while data is moving over the network | When data is stored on a server or hard drive |
| Provider Access | Provider cannot read message content | Provider can read data on their servers | Provider can access and read stored data |
| Best For | Private messaging, secure email, confidential calls | Securing website connections (HTTPS), online banking | Protecting files stored in the cloud or on a server |
As you can see, only E2EE prevents the service provider from accessing your data. While the other methods are essential, they leave a window of opportunity for your information to be exposed on the server.
How End-to-End Encryption Actually Works
So, how does this digital privacy magic really happen? The whole system is built on a clever concept called asymmetric cryptography. It sounds intimidating, but the idea behind it is surprisingly simple—think of it like having a special mailbox just for your digital messages.
In any end-to-end encrypted chat, every single person gets a pair of unique, mathematically connected keys.
- Public Key: This is like a personal, public-facing lockbox. You can give a copy of this lockbox to anyone who wants to send you something securely. They can drop their message inside, but they can't open it back up.
- Private Key: This is the only key in existence that can unlock your personal lockbox. You keep this key completely secret and never share it with anyone. Not your friends, not your family, and not even the company that runs the app.
This two-key system is what makes end-to-end encryption so robust. Even if a snooper manages to grab your lockbox while it's on its way, they can't get inside. The lock is built in such a way that only your one-of-a-kind private key will work.
The Encryption Process Step-by-Step
Let's break down the journey of a single message.
- Locking the Message: When you decide to send a message to your friend, your device grabs a copy of their public key—their lockbox—and uses it to encrypt, or lock, your message. The moment it's locked, your message turns into a jumble of unreadable code.
- Sending the Message: This scrambled, unreadable message travels across the internet. If a hacker or even the service provider themselves intercepts it, all they see is the locked box. Without the right key, it’s completely useless.
- Unlocking the Message: Once the message lands on your friend's device, their app automatically uses their unique private key to unlock it. Instantly, the scrambled code is converted back into the original, readable message you sent.
Because your message was locked using your friend's public key, only their corresponding private key can ever open it. Your own keys play no part in unlocking the message on their end, which is exactly what makes the process so secure.
This visual shows how your data stays protected every step of the way, with the lock icons representing how it remains encrypted as it passes through various servers.
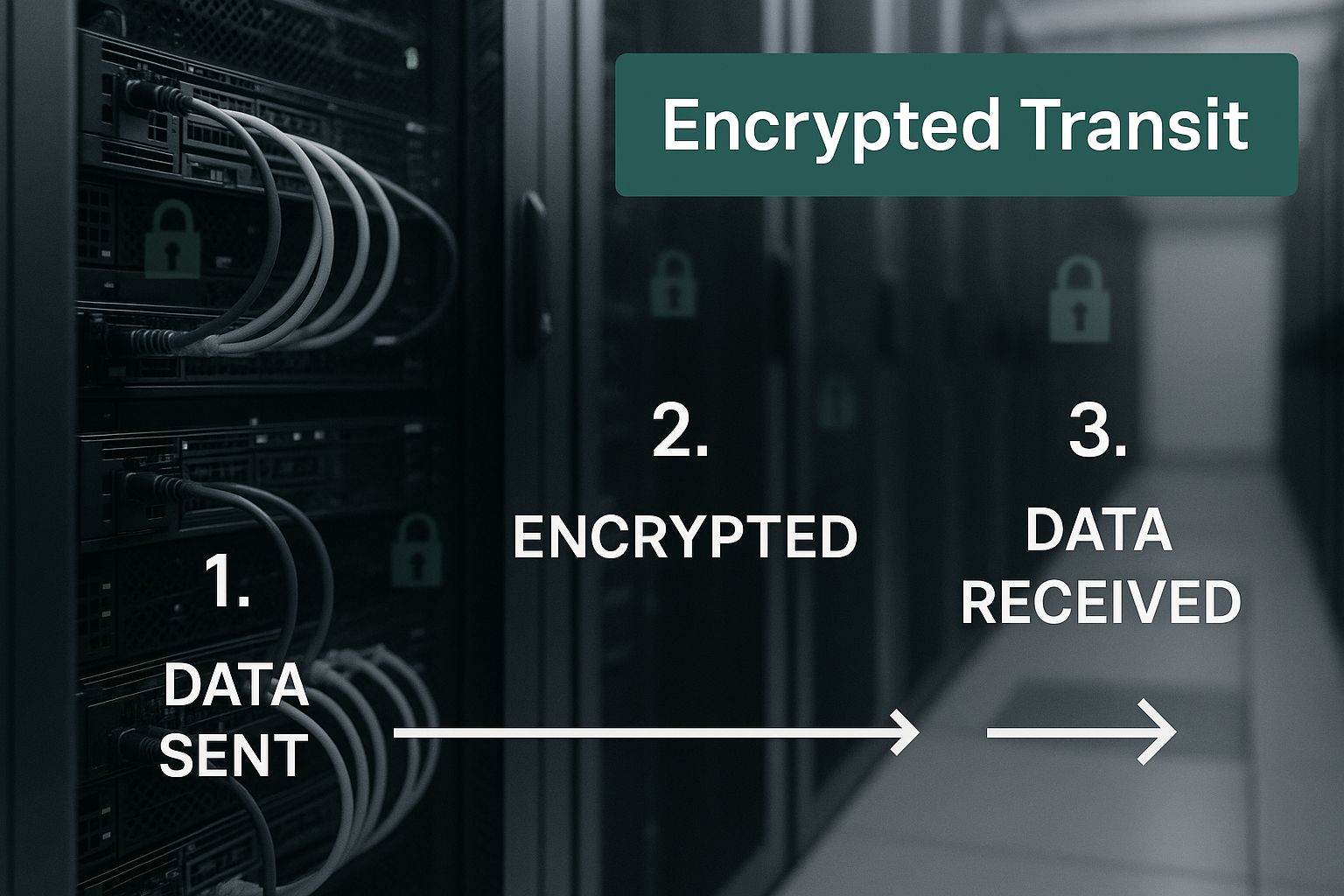
As you can see, the data is never "unlocked" or exposed while it's in transit. It stays secure from the moment it leaves your device until it reaches its final destination.
Why This Method Is So Secure
The real strength of E2EE comes from this pairing of public and private keys. They're generated using incredibly complex mathematical algorithms, making it virtually impossible for someone to figure out your private key just by looking at your public one.
The fundamental promise of E2EE is this: your message, in its original, readable form, only ever exists on the devices of the people in the conversation. The servers that route the message simply can't read it because they never have the private keys.
This is a huge step up from more common security methods. For instance, with standard encryption-in-transit (the HTTPS you see on websites), the service provider holds the keys and could technically decrypt your data on their servers. Secure email hosts like Typewire are built on E2EE to close this loophole, making it impossible for them to read your emails and giving you true control over your own data.
Why End-to-End Encryption Matters for You

It’s one thing to get the technical details of end-to-end encryption, but it's another thing entirely to grasp just how crucial it is in our everyday lives. Think of E2EE as your personal digital bodyguard, constantly on watch to protect your sensitive information from a growing list of online threats.
This isn’t just some niche feature for cybersecurity experts—it’s a fundamental tool for everyone. E2EE is what keeps your private chats, financial records, and confidential business plans from being exposed. Without it, your data is an open book for service providers to snoop on, corporations to mine, and cybercriminals to steal.
Protecting Your Digital Identity
Every single day, you share pieces of information that make up who you are: personal stories, business ideas, and even your deepest feelings. End-to-end encryption builds a secure bubble around these communications, ensuring only you and the person you're talking to can ever access them.
The need for this kind of robust protection is more pressing than ever. As cybercrime becomes more frequent and costly, industries are scrambling to adopt stronger security measures like E2EE. With the average cost of a single data breach hitting $4.88 million in 2024, it’s clear that weak security carries a massive financial risk. For more on this trend, check out the latest statistics on advanced security tech adoption from SecureITConsult.com.
Guaranteeing Data Integrity and Authenticity
Beyond just keeping secrets, E2EE delivers another massive benefit: data integrity. This is a fancy way of saying you can be absolutely sure the message you receive is identical to the one that was sent, with zero tampering in between.
Imagine you're sending a legal contract or your bank account details. The cryptographic seal from E2EE ensures that no one can secretly change a number or a clause while it's in transit. If they tried, the encryption would break, instantly flagging the message as corrupted on the recipient's device. This gives you complete confidence that your information is authentic.
Simply put, end-to-end encryption isn't just about hiding your data—it's about trusting that your data is exactly as it should be. It preserves both the secrecy and the truthfulness of your communications.
This is the bedrock of trust for all our digital interactions. Whether you’re sending a message through a private app or an email through a secure service, the integrity that E2EE provides is non-negotiable. To learn more about how this applies to your inbox, take a look at our guide on the top benefits of encrypted email you need to know.
Where You Already Use End-to-End Encryption
End-to-end encryption might sound like something reserved for spies or cybersecurity experts, but chances are you use it every single day. It’s one of the most powerful privacy tools available, and it’s quietly become a standard feature in many of the apps you already have on your phone. It works silently in the background, protecting your private conversations from anyone who might be trying to listen in.
This digital shield is the default setting for billions of people around the world. When you fire off a message on an app like WhatsApp or Signal, E2EE is working for you automatically. Every text, photo, and voice note is scrambled the moment it leaves your device and can only be unscrambled by the person you sent it to.
Everyday Apps with Built-in Privacy
A lot of modern communication platforms have embraced this high level of security. Some, like Signal, have it turned on for everything by default. Others make it an optional feature you can enable for conversations that need an extra layer of confidentiality.
Here are a few common places where you’ll find E2EE at work:
- Secure Messaging Apps: Signal and WhatsApp are the big names here, encrypting all communications from the get-go. Apple’s iMessage also uses E2EE for those signature "blue bubble" chats between Apple devices.
- Optional Encryption: Facebook Messenger has "Secret Conversations," an opt-in mode that applies E2EE to specific chats. Telegram works similarly with its "Secret Chats" feature.
- Secure Email Services: Old-school email is notoriously insecure, like sending a postcard through the mail. But a new generation of providers is fixing that. Services like Typewire build their entire platform on end-to-end encryption, ensuring your emails stay completely private—a massive departure from mainstream services that often scan your inbox.
This screenshot from Typewire's homepage really drives home its commitment to a private, ad-free experience, which is only possible because of strong security like E2EE.

The promise of "No ads, no tracking, no data mining" is the real payoff. When a service uses E2EE correctly, it locks itself out of your data. Your information truly belongs to you.
Making Smart Choices for Your Security
Once you know which of your tools are genuinely secure, you can make better decisions about where you share sensitive information. When a service offers E2EE, it’s sending a clear signal: it values your privacy more than its ability to mine your data.
This is especially critical when it comes to email, where so much of our confidential lives are stored. To find a provider that aligns with your privacy needs, you can explore our list of the top 10 best encrypted email services for privacy in 2025. By consciously choosing apps with strong encryption, you’re taking a huge step toward locking down your digital life.
Understanding the Limits of Encryption
While end-to-end encryption is an incredibly powerful tool for privacy, no technology is a perfect shield. It's important to know where its protection ends so you can have realistic expectations about your security. Many people think E2EE makes their communication completely invisible, but that's not quite the whole story.
A key point to understand is that while E2EE scrambles the content of your messages, it doesn't hide the metadata. Think of it like a sealed envelope. Anyone who intercepts it can't read the letter inside, but they can still see who sent it, who it's going to, the date it was mailed, and even how much it weighs.
The Metadata Problem
This unencrypted information can reveal a surprising amount about you. For example, even without reading your messages, an outsider could figure out:
- Who you talk to: They know the exact sender and receiver.
- When you talk: The timestamps of your messages are visible.
- How often you talk: They can analyze the frequency and patterns of your conversations.
Over time, this metadata can be pieced together to build a detailed social graph, mapping out your relationships and communication habits even if the conversations themselves remain a secret.
Endpoint Vulnerabilities and Other Risks
The biggest blind spot for E2EE is at the "ends"—the devices themselves. End-to-end encryption protects your data while it's traveling between devices, but it can't do a thing if your device (or your recipient's) has been compromised.
End-to-end encryption secures the journey, not the destination. If the device receiving the message is infected with malware or spyware, your decrypted messages can be easily read, copied, or stolen.
This "endpoint vulnerability" is a major risk. If a hacker gains access to your phone or computer, they can simply wait for messages to be decrypted and read them in plain text. This is why practicing good device security—using strong passwords, keeping software updated, and being cautious about suspicious apps—is just as crucial as using an encrypted service.
Another potential risk is a "man-in-the-middle" (MITM) attack. This is a sneaky attack where a third party intercepts messages between two people who think they're talking directly to each other. To prevent this, many secure apps ask you to verify a contact's security code or key fingerprint. Taking a moment to confirm this code through another channel (like in person or on a trusted phone call) ensures you’re connected to the right person, not an impostor.
Knowing these limits helps you build a much stronger security strategy. You can learn more about layering your defenses by checking out our guide on sending secure emails and your complete protection playbook. Real digital privacy comes from combining strong encryption with smart, cautious habits.
What's Next for Digital Privacy and Encryption?
As we live more of our lives online, the world of digital security is always in flux. End-to-end encryption is a cornerstone of our privacy today, but it’s not a "set it and forget it" solution. It has to evolve to meet the challenges coming our way.
With everything from AI-powered cyberattacks to growing surveillance efforts, truly strong E2EE is no longer a luxury—it’s a necessity for protecting our personal conversations and professional data.
This isn't just about having encryption; it's about having smart, adaptive encryption. As attackers get more creative, our defenses have to stay one step ahead. It’s a constant chess match, and E2EE is right in the middle of it.
The Quantum Threat and AI on Defense
One of the biggest conversations in security circles right now is about quantum computing. It's a bit sci-fi, but the reality is that these incredibly powerful computers could one day break the math that all modern encryption is built on. Because of this, the security community is already racing to develop "quantum-resistant" cryptography to make sure our data stays safe long into the future.
At the very same time, artificial intelligence is stepping up as a powerful ally. While AI can be used by bad actors, we're also putting it to work to build stronger defenses. For instance, AI systems can spot threats in real-time by analyzing network patterns, help manage the complex keys that lock our data, and automate security tasks that used to be too complex for the average person or small business.
The real future here isn’t just about using AI to fight off threats. It's about using it to make powerful privacy tools like end-to-end encryption simpler, more automated, and genuinely accessible to everyone.
We're already seeing this forward-thinking approach pay off. Research shows that when companies blend AI-driven automation with their encryption strategies, they not only boost their security but also see real financial savings.
The stakes are high. A recent survey for 2025 revealed that a staggering 70% of organizations experienced a cybersecurity incident in the last year alone. In response, 65% of critical firms are now turning to AI to help manage their encryption keys and stay compliant. You can dive deeper into these trends in the 2025 encryption trends report.
Ultimately, this combination of AI and encryption isn't just another passing trend. It's the blueprint for the future of our digital privacy.
Common Questions About End-to-End Encryption
Even after you get the basic idea of end-to-end encryption, some questions tend to stick. Let's walk through a few of the most common ones to iron out the details and give you some practical, no-nonsense answers.
Is End-to-End Encryption Really Unbreakable?
The short answer is yes… and no. The mathematical algorithms that power modern E2EE are incredibly strong. In fact, it would take the world's most powerful supercomputers billions of years to guess the right key through brute force. From a purely mathematical standpoint, the encryption is virtually unbreakable.
But that doesn't mean your data is completely invulnerable. The real-world risks aren't about cracking the code itself, but about compromising the "ends" of the conversation—your devices.
- Endpoint Security: E2EE is like an armored car for your message while it's in transit. But if a thief is already inside your house (malware or spyware on your device), the armor on the car doesn't matter. They can just read the message before you send it or after you receive and decrypt it.
- Human Error: Security is often a human problem. Using a weak password, getting tricked by a phishing email, or simply losing your phone can create vulnerabilities that have nothing to do with the strength of the encryption.
So, while the digital safe itself is secure, someone could always try to steal your key or just look over your shoulder when you open it.
Does a VPN Protect Me in the Same Way?
This is a really common mix-up. People often lump VPNs and E2EE together, but they solve two very different problems. They're both essential tools for digital privacy, but they don't overlap.
Here’s a good way to think about it: A VPN is like sending your mail through an unmarked, armored truck that takes a secret, untraceable route. An E2EE is like locking the letter itself inside an unbreakable box before it even gets on the truck.
A VPN encrypts your entire internet connection, masking your IP address and stopping your internet provider from seeing what you do online. But the website or service at the destination can still see your data perfectly clearly. E2EE, on the other hand, protects the content of your message, making sure only the intended recipient can ever decipher it.
For the best possible privacy, using both together is a powerful combination.
How Can I Start Using E2EE in My Daily Life?
Getting started with end-to-end encryption is more straightforward than you might think. The biggest and most effective step is to simply start choosing services that are designed with E2EE from the ground up.
Take a look at the apps you use every day for messaging. Popular choices like Signal and WhatsApp already have it enabled by default. For your email, which often contains your most sensitive information, the next logical step is to find a provider that puts E2EE at the core of its service.
Ready for an email experience where your privacy is the priority? Typewire provides true end-to-end encrypted email hosting, guaranteeing your conversations remain yours and yours alone—no ads, no tracking, no data mining. It’s time to take back your inbox. Explore our features with a free trial.
What Is End-to-End Encryption? Explained Simply
Posted: 2025-08-07
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16