What Is Email Authentication? Your Complete Security Guide
What Is Email Authentication? Your Digital Bouncer Explained
Imagine your email inbox is a popular nightclub. Without a bouncer checking IDs, anyone could stroll in, pretend to be someone they're not, and cause all sorts of trouble. Email authentication is like that vigilant bouncer for your inbox. It verifies the sender's identity before an email is allowed "in." This confirmation helps prevent spam, phishing scams, and other nasty digital threats. It's not just about keeping your inbox tidy; it's about protecting your personal information and your business's good name.
Think about it: traditional email, without this authentication, is surprisingly easy to exploit. It's more like a costume party where anyone can forge an email address and impersonate someone else. This makes email a prime target for bad actors looking to steal data or spread harmful software. The fallout from these attacks can be devastating. Between 2015 and 2017, email security breaches exposed a whopping 886.5 million records worldwide—that's more than double the U.S. population! For a deeper dive into this issue, check out this article on email security breaches: https://www.avatier.com/blog/email-security-breaches/. These numbers really highlight how crucial strong email authentication is.
This screenshot from Wikipedia illustrates the different kinds of email authentication, each with a vital role in verifying the sender's identity. The image shows how email authentication involves multiple checks, working together like a team, to make sure the message is genuine and untouched. Understanding what email authentication is and how it works is the first step to protecting yourself and your business from online dangers.
Email authentication isn't just a technicality; it's your frontline defense against online fraud. By implementing proper authentication protocols, you significantly lower the risk of falling victim to these attacks. This safeguards not only your data but also the trust your customers and partners have in you.
From Postcards To Secured Letters: Email's Security Evolution

The screenshot above, taken from the Wikipedia page about the Simple Mail Transfer Protocol (SMTP), shows the basic structure of how email gets delivered. Notice how straightforward it looks. This simplicity, while efficient, made early email very vulnerable to impersonation. Understanding this is the first step to seeing why email authentication is so important.
Imagine the early days of email. Messages were sent almost like postcards—open for anyone to read along the way and easily faked. Sending an email was like shouting across a room. Anyone could hear, and anyone could easily pretend to be you.
This lack of security was a real problem, especially as businesses started using email for important, private conversations.
Something had to change. Email security needed to evolve. A big step forward was the creation of email authentication protocols. Think of these protocols as digital bodyguards, checking the sender's ID and making sure the message hasn't been tampered with. This shift took us from the "postcard" days to something more like sending a sealed, registered letter.
By the late 1990s, the need for better security was obvious. Businesses realized their confidential information was travelling the internet unprotected. This sparked the development of the first authentication methods.
For example, around March 1999, SMTP added a basic authentication feature using EHLO and the 250-AUTH PLAIN LOGIN option. This offered a basic level of protection against unauthorized access. You can explore more about the history of email and SMTP here.
From these early efforts, email authentication has steadily improved, resulting in the strong protocols we use today. Knowing this history helps us understand why modern email authentication exists and how it tackles today's tougher security challenges.
The Security Trio: How SPF, DKIM, and DMARC Work Together
Imagine airport security. Multiple checkpoints work together to ensure only legitimate travelers board the plane. Email authentication is similar. It uses multiple protocols to verify a sender's identity and message integrity, creating layers of protection against spoofing and phishing. Understanding how these protocols work together is key to grasping email authentication.
SPF: The Sender's Flight Manifest
Sender Policy Framework (SPF) is like the airline's passenger manifest. It lists the approved "senders" (mail servers) allowed to send email on behalf of a specific domain. When an email arrives, the recipient's server checks this "manifest." If the sending server isn't listed, the email might be flagged as suspicious. This helps stop unauthorized senders from using your domain for spam or phishing.
Think of it this way: You wouldn't want just anyone claiming to be a pilot for your favorite airline. SPF makes sure only authorized servers are sending emails "for" you.
DKIM: The Tamper-Evident Seal
DomainKeys Identified Mail (DKIM) is like a tamper-evident seal on your luggage. It digitally signs your outgoing messages, verifying that the message hasn't been altered in transit. A broken signature upon arrival suggests tampering, warning the recipient that something might be wrong. This is vital for ensuring the message you send is the message received.
Imagine receiving a letter with a broken seal. You'd be suspicious, right? DKIM provides that same peace of mind in the digital world.
DMARC: The Airport Security Chief
Domain-based Message Authentication, Reporting & Conformance (DMARC) is the security coordinator, the one in charge. It tells the recipient's server what to do if SPF or DKIM checks fail. You can instruct the server to reject suspicious emails, quarantine them (like holding a suspicious passenger), or simply monitor them. DMARC also sends valuable reports back to you, showing who is sending emails on behalf of your domain—both legitimate and not.
DMARC is like the head of security, making the final call on who gets through and who doesn’t. It provides crucial oversight and control.
To help illustrate the relationship between these protocols, let’s look at the table below:
Email Authentication Protocols Comparison: A detailed comparison of SPF, DKIM, and DMARC protocols showing their functions, strengths, and limitations
| Protocol | Primary Function | What It Validates | Protection Level | Implementation Complexity |
|---|---|---|---|---|
| SPF | Authorizes sending mail servers | Envelope sender (Return-Path) | Prevents sender address spoofing | Relatively simple |
| DKIM | Verifies message integrity | Message content and some headers | Detects message tampering | Moderate |
| DMARC | Sets policies based on SPF and DKIM results | Alignment between sender addresses | Provides comprehensive control over email delivery | Most complex |
This table summarizes the core functions of each protocol, showing how they build upon each other. While each has its strengths, they are most effective when combined.
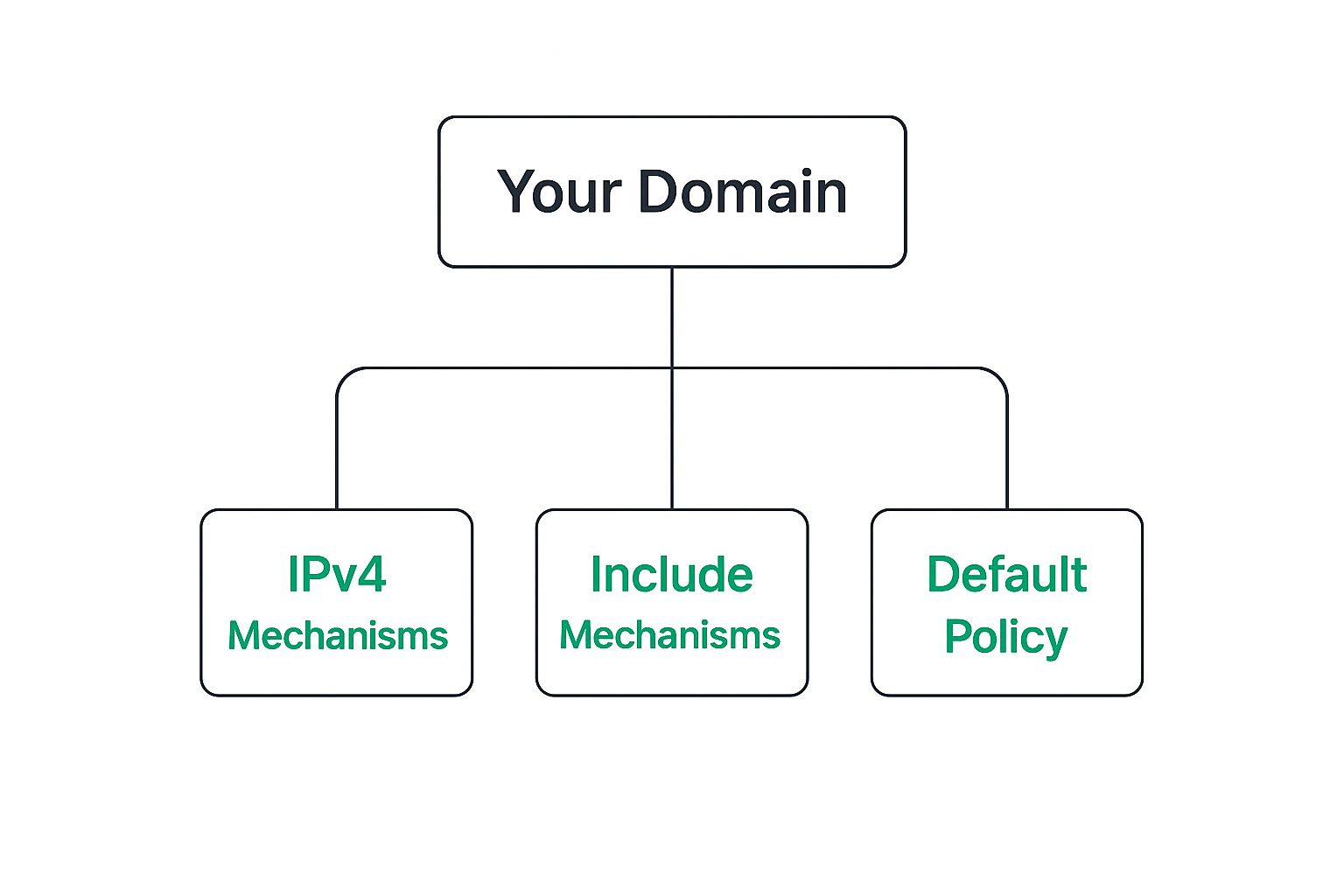
As this infographic shows, these protocols interact within your domain like a well-coordinated team. This hierarchical structure allows for fine-tuned control over authentication, ensuring that only authorized senders use your domain.

This screenshot from Dmarcian further visualizes DMARC's role as the ultimate decision-maker. It reinforces the importance of this final layer of control for a secure email environment. These tools aren't just technical details; they protect your brand and build customer trust. Implementing all three—SPF, DKIM, and DMARC—creates a strong, unified defense against email threats. Don't settle for partial protection when you can have the full security team working for you.
Battle Stories: When Authentication Saves The Day (And When It Doesn't)
Email authentication isn't just a technical box to tick. Think of it as a frontline defense for your business, one that can determine success or failure in the fight against online threats. Let's explore some real-world scenarios where these protocols proved their mettle—and others where their absence had dire consequences.
Success Stories: Authentication As A Shield
Many organizations have seen a dramatic improvement in their security posture by implementing strong email authentication. They've witnessed a significant decrease in successful phishing attacks and a boost in overall email security. These aren't hypothetical wins, but tangible victories achieved by prioritizing authentication.
For instance, companies constantly bombarded by phishing emails found that, after implementing DMARC, the number of fraudulent emails reaching their employees plummeted. This meant fewer security breaches, reduced financial losses, and increased employee productivity.
These success stories demonstrate the real benefits of a well-configured email authentication system. By actively blocking fraudulent emails, businesses safeguard their reputation, earn customer trust, and create a safer online environment. This proactive approach translates into long-term savings of time, money, and resources.
Failures: The Cost of Neglect
Unfortunately, not every story has a happy ending. The lack of, or weak implementation of, email authentication has given attackers an open door to exploit vulnerabilities and inflict significant damage.
This screenshot from Krebs on Security highlights the kind of headlines that emerge when email security is neglected. It shows that even prominent organizations aren’t immune to attack, emphasizing the critical need for proactive defenses. KrebsOnSecurity offers valuable insights, revealing that even large, established companies can be vulnerable without proper email authentication.
One particularly striking example is the 2004 AOL security breach. An employee stole approximately 92 million customer accounts, including email addresses and credit card information. This stolen data was then sold to spammers, who unleashed billions of unsolicited emails, costing AOL dearly. To understand the impact of this and other email security breaches, you can delve deeper here: Learn more about email security breaches. This incident vividly illustrates the devastating repercussions of inadequate security measures.
These cases demonstrate how neglecting email authentication can have severe consequences, ranging from financial loss to reputational damage. They underscore the vital need for proactive steps to protect sensitive data and preserve customer trust. These real-world examples prove that robust email authentication isn't just a best practice; it's an absolute necessity.
Beyond Security: The Hidden Business Benefits You’re Missing
Let's talk about email authentication. It's more than just a security measure; it's a powerful tool that can transform your email system into a valuable business asset. Surprisingly, many businesses overlook the significant advantages that make email authentication a worthwhile investment.
One of the most immediate benefits is the dramatic improvement in email deliverability. Think of it like sending a crucial business letter: you wouldn’t want it getting lost in the mail. Email authentication ensures your important messages land directly in your customers' inboxes, not their spam folders.
Another critical advantage is reputation protection. If cybercriminals can't impersonate your domain, they can't damage your brand by sending fraudulent emails. This safeguards your relationships with customers and partners, maintaining their trust and confidence.
This SpamTitan screenshot illustrates various email security threats. It highlights the vital role of comprehensive email security, including strong authentication, in protecting businesses from diverse online risks. Implementing proper authentication protocols drastically lowers these risks.
More Than Just Security
Beyond security and deliverability, email authentication offers significant compliance advantages, particularly in regulated sectors like finance and healthcare. Demonstrating robust email security is often a prerequisite for meeting industry standards and regulations. This can be a deciding factor for clients who prioritize secure communication channels.
Furthermore, email authentication provides a competitive edge. In today's world, businesses that prioritize security are increasingly attractive to clients aware of cyberattack risks. Implementing email authentication signals to potential clients that you value their security, differentiating you in a competitive marketplace.
The Financial Advantage
Finally, let's talk about the bottom line. Email authentication is a smart financial move. The cost of implementing these protocols is typically far less than the potential damage from a security breach or reputational harm.
To illustrate the business impact, let's look at some data:
Business Benefits of Email Authentication
Quantitative analysis of business improvements after implementing email authentication protocols
| Benefit Category | Average Improvement | Time to See Results | Cost Impact |
|---|---|---|---|
| Deliverability | 20-30% | 1-2 weeks | Low |
| Open Rates | 10-15% | 2-4 weeks | Low |
| Click-Through Rates | 5-10% | 2-4 weeks | Low |
| Spam Complaints | Decrease by 50-75% | 1-2 months | Low |
| Brand Reputation | Significant positive impact | Ongoing | Low |
This table demonstrates that improvements can be seen across key metrics, often within a relatively short timeframe. The cost impact of implementing authentication is generally low, making it a highly cost-effective strategy.
Through enhanced communication, fewer security incidents, and improved business credibility, email authentication delivers a strong return on investment. It’s not just an expense; it's an investment in the future of your business.
Your Authentication Action Plan: From Setup To Success

This screenshot shows the MXToolbox SPF record lookup tool. It’s a helpful resource for checking your SPF record setup. The results tell you which mail servers are authorized to send emails on behalf of your domain, a key step in preventing email spoofing. Getting your SPF record right is the crucial first step in email authentication.
Implementing email authentication might sound complicated, but it's a straightforward process. Think of it like building a house: you wouldn't start with the roof. You need a solid foundation first. That begins with assessing your current email setup.
Assessing Your Current Email Setup
Before jumping into implementation, take a moment to understand your current email environment. This assessment helps you spot potential weaknesses and focus your efforts.
-
Identify your email sending sources: Where are your emails coming from? Knowing this helps pinpoint which systems need authentication configured.
-
Analyze your email volume: How many emails do you send daily? This helps determine the right authentication approach and anticipate any resource needs.
-
Check existing authentication: Do you already have any authentication protocols in place? This assessment creates a baseline and guides your next steps.
Implementing Your Authentication Protocols
Once you have a clear picture of your email landscape, you can begin implementing the key protocols: SPF, DKIM, and DMARC. These protocols are like adding layers of security to your house.
-
Start with SPF: Think of SPF as your first line of defense. It’s relatively simple to set up and provides immediate benefits.
-
Add DKIM: DKIM strengthens your authentication by verifying message integrity. It's like adding a lock to your front door.
-
Implement DMARC: DMARC acts as the control center for your email authentication. It instructs receiving servers on what to do with emails that fail SPF and DKIM checks.
Interestingly, the evolution of email authentication mirrors the broader history of authentication. Think about it: we’ve gone from basic passwords in the 1960s to the multi-factor authentication we use today. Similarly, email authentication protocols build on one another. To delve deeper into the history of authentication, check out this resource: Discover more insights.
Ongoing Maintenance and Monitoring
Email authentication isn’t a one-time setup. Ongoing maintenance and monitoring are vital for long-term success. It's like regularly checking your home security system to ensure it’s working properly.
-
Regularly review your SPF record: Keep it updated as your email infrastructure evolves.
-
Monitor DMARC reports: These reports offer valuable data about your email traffic and can help you catch potential problems early.
-
Stay informed about best practices: The world of email authentication is always changing, so stay current with the latest recommendations.
By following this practical action plan, you can successfully implement email authentication, bolstering your email security and protecting your organization from online threats. This is more than just checking off a to-do list; it’s about building a secure and trustworthy email ecosystem.
Staying Ahead: Future-Proofing Your Email Security Strategy

This screenshot from Cloudflare's email security learning resources paints a clear picture: email threats are constantly evolving. Just like a vigilant gardener tending to their plants, we need to continuously adapt and improve our email authentication strategies. Staying informed about emerging threats is no longer a luxury, it’s the bedrock of a robust email security posture.
Email authentication isn't something you set up once and then forget about. It requires ongoing nurturing and adjustments. Think of it like tending a garden. You wouldn't plant your seeds and then walk away, expecting a bountiful harvest without regular weeding, watering, and pruning. Your email authentication strategy needs that same level of care.
Emerging Trends in Email Security
The world of email security is dynamic. New threats pop up regularly, making it crucial to stay informed about the latest trends. This awareness is key to future-proofing your email authentication efforts.
-
Artificial Intelligence: AI is a double-edged sword. Attackers use it to craft increasingly sophisticated phishing emails that are harder to detect. On the flip side, defenders leverage AI to identify and block these evolving threats more effectively. It's a constant arms race.
-
New Authentication Methods: The authentication protocols we use today are constantly being refined. New methods are also being developed to address emerging vulnerabilities. Keeping up with these advancements is like updating your antivirus software – essential for maintaining strong defenses. For example, Microsoft's decision to retire Basic Authentication for SMTP signals the ongoing shift towards more secure options like OAuth.
Maintaining Your Authentication Over Time
Setting up email authentication is just the first step. True security requires ongoing monitoring and adjustments, ensuring your defenses remain effective.
-
Monitoring: Think of your DMARC reports as the health checkups for your email authentication setup. Regularly checking these reports for unusual activity or errors can provide early warning signs of potential issues. They’re like the canary in the coal mine, alerting you to potential problems before they escalate.
-
Upgrades: Just like any software, your authentication protocols need occasional upgrades. Periodically review your setup and consider upgrading to newer versions or adding new methods as they become available. This ensures your system benefits from the latest security best practices and remains a strong deterrent against emerging threats.
Building Flexibility Into Your Strategy
A rigid email authentication strategy is like a house built on sand. It can’t withstand the shifting tides of the threat landscape. Flexibility is the key to long-term success.
-
Stay Informed: The world of email security is constantly changing. Staying up-to-date with industry news and security updates related to email authentication allows you to proactively address potential vulnerabilities. Think of it as continuing education for your email security strategy.
-
Be Proactive: Don't wait for a security breach to expose weaknesses in your system. Regularly assess your email security posture and implement necessary improvements. Being proactive is like getting regular checkups – it helps you stay ahead of potential problems.
By adopting a proactive and adaptable approach, you ensure your email authentication strategy remains effective, not just today, but also in the future. This forward-thinking approach saves you time, money, and resources down the line. Want a truly secure and private email experience? Typewire offers a robust and private email hosting platform that puts you in control. Start your free trial today: https://typewire.com
What Is Email Authentication? Your Complete Security Guide
Posted: 2025-06-10
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16
Why Am I Getting So Many Junk Emails? A Guide to Email Security and Privacy
Posted: 2026-01-13
How to Disable Email Tracking and Protect Your Email Privacy
Posted: 2026-01-09
Secure Email Services: A Guide to True Email Privacy and Security
Posted: 2026-01-06
How to Create a Personal Email Domain for Ultimate Email Security and Privacy
Posted: 2026-01-02