Send Secure Email: Tips for Private, Safe Communication

Why You Need To Send Secure Email (And What Happens If You Don't)

Email remains a cornerstone of communication. However, standard email protocols often lack sufficient security, leaving sensitive information exposed to potential threats. This vulnerability presents real dangers, such as phishing attacks. These deceptive emails masquerade as legitimate correspondence, tricking recipients into divulging passwords and financial information. Phishing techniques are constantly evolving, often circumventing conventional spam filters.
Another significant threat is business email compromise (BEC). BEC attacks specifically target organizations, resulting in substantial financial losses. By compromising email accounts, attackers can initiate fraudulent wire transfers or access sensitive company data. The repercussions can be severe, including reputational damage and significant financial setbacks. Sending sensitive information via standard email is like sending a postcard—anyone can potentially read it en route.
The Real Cost of Insecure Email
Standard email's lack of security creates numerous vulnerabilities. One primary weakness is the absence of end-to-end encryption. Without encryption, emails are easily intercepted and read by unauthorized parties. Another vulnerability stems from the susceptibility of email accounts to compromise. Weak passwords, malware, and phishing can give hackers access to your inbox. Once in, they can steal data, impersonate you, or launch further attacks. For a deeper understanding of secure email, check out this Essential Privacy Guide.
The rise in cyberattacks highlights the increasing demand for robust email security solutions. The projected growth of the email security market reflects this trend. Valued at $4.68 billion in 2024, the market is predicted to reach $10.68 billion by 2032, demonstrating a 10.9% CAGR. This growth is driven by the dramatic increase in malicious phishing emails, which saw a 569% surge in 2022, coupled with a 478% increase in reported credential phishing threats. You can find more detailed statistics on the Email Security Market.
Protecting Your Communications: The Need for Secure Email
Safeguarding sensitive information necessitates a transition to secure email. Secure email utilizes encryption and other security measures to protect your messages from unauthorized access. This ensures confidentiality and preserves the integrity of your communications. By adopting secure email practices, you significantly mitigate the risks of data breaches, identity theft, and financial loss. Prioritizing email security is no longer a choice; it's a fundamental requirement for individuals and businesses alike. Learn more about How to Send Secure Email.
Making Sense Of Email Encryption (Without The Technical Jargon)

Sending a secure email involves more than simply clicking "send." It requires a practical understanding of how different encryption methods protect your data. This section clarifies the process, focusing on real-world applications.
Understanding The Basics: Encryption Methods
Encryption transforms readable data into an unreadable format, safeguarding it from unauthorized access. Think of it as sending information in a locked box – only the recipient with the correct key can unlock and view the contents. There are several key encryption methods used to secure emails: end-to-end encryption (E2EE), transport layer security (TLS), and public key infrastructure (PKI).
-
End-to-end encryption (E2EE): With E2EE, only the sender and the intended recipient can read the message. It's like a private conversation where no one else can listen in. This method offers the highest level of privacy.
-
Transport Layer Security (TLS): TLS encrypts the connection between your email provider and the recipient's provider. Think of it as a secure courier service transporting your locked box. While the box is protected in transit, the courier company could potentially access its contents.
-
Public Key Infrastructure (PKI): PKI uses a pair of keys – a public key for encrypting and a private key for decrypting. You can share your public key with anyone, and they can use it to send you encrypted messages. Only you, with your private key, can decrypt these messages. This is like having a secure mailbox where only you have the key.
Choosing The Right Encryption For Your Needs
Different email encryption standards utilize these methods in various ways. PGP (Pretty Good Privacy) is a popular standard for E2EE, providing strong security for individuals. S/MIME (Secure/Multipurpose Internet Mail Extensions) is often used in business and relies on PKI for encryption and digital signatures for authentication. TLS is commonly used by email providers to securely transmit messages between their servers.
The growing emphasis on data privacy and security is fueling the email encryption market. Currently valued at $7.75 billion, this market is projected to reach $40.16 billion by 2033, exhibiting a 20.05% CAGR. This growth underscores the increasing importance of secure email for individuals and businesses alike. You can find more detailed statistics on the email encryption market.
Selecting the appropriate encryption method depends on the sensitivity of your information and your technical resources. Understanding the basics empowers you to send emails confidently and securely.
Finding The Right Secure Email Platform That Actually Works
Finding the right platform for secure email can be overwhelming with the multitude of options available. It's essential to look beyond marketing and focus on features that genuinely enhance security. This involves balancing essential features like zero-knowledge architecture (meaning only you hold the decryption keys) and multi-factor authentication with practical aspects like ease of use and integration with your current tools.
Essential Security Features
When selecting a secure email provider, prioritize these key features:
-
End-to-End Encryption (E2EE): This ensures only you and the intended recipient can read the message. Look for platforms that offer true E2EE, not just encryption while the message is in transit.
-
Zero-Knowledge Architecture: Verify the provider cannot access your encrypted data. This safeguards your privacy and maintains the confidentiality of your information.
-
Multi-Factor Authentication (MFA): Add another layer of security to your account by requiring multiple forms of authentication for login. This protects against unauthorized access, even if your password is compromised.
-
Secure Attachment Handling: Make sure the platform securely handles attachments, encrypting them just like the message itself.
-
User-Friendly Interface: A complicated interface can discourage use. Opt for platforms that prioritize ease of use without sacrificing security.
Evaluating Encryption Methods and Adoption Rates
The effectiveness of secure email heavily depends on the encryption methods used. The following infographic illustrates the adoption rates of various encryption methods:
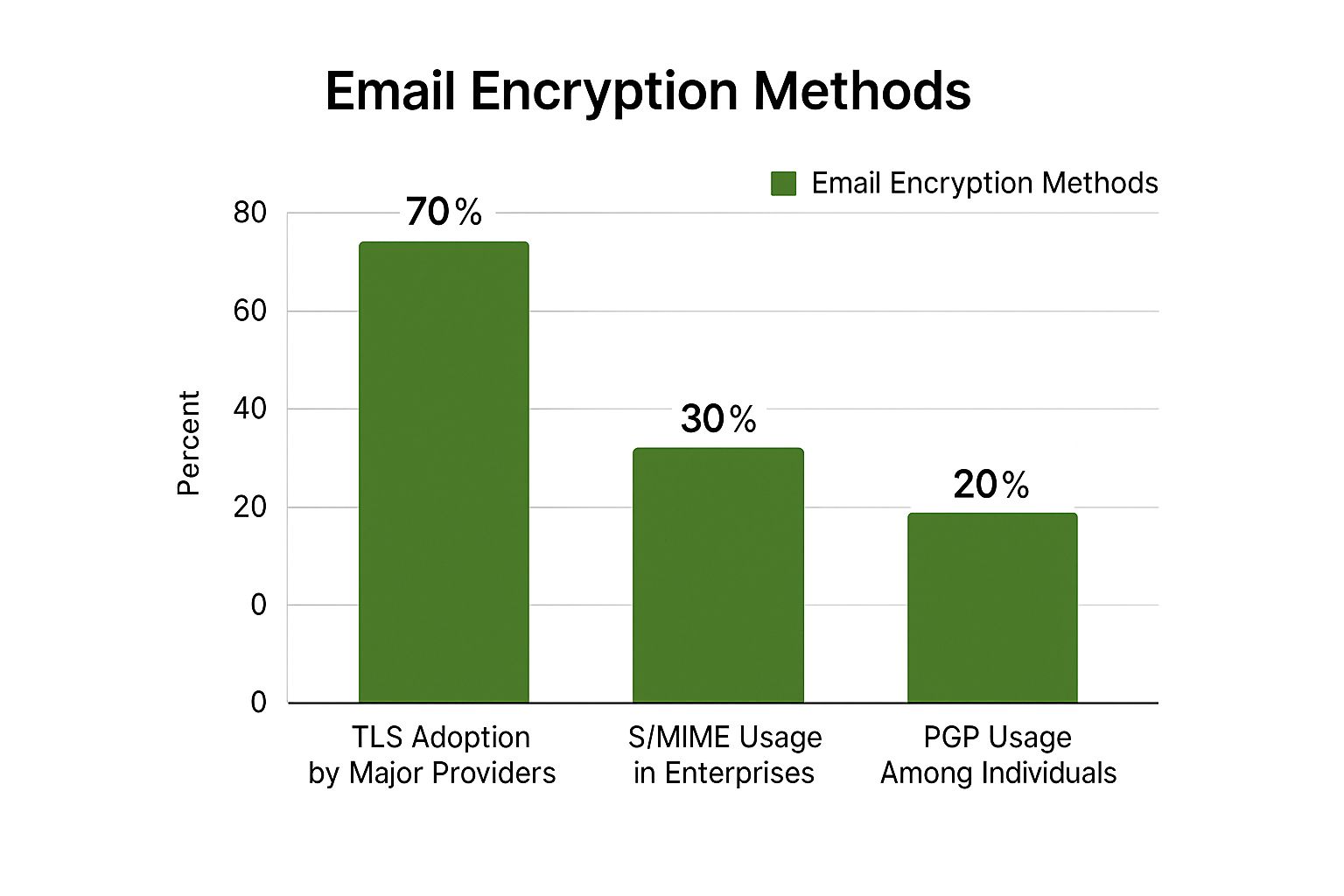
As the infographic shows, while TLS is widely adopted by major email providers like Gmail and Outlook, offering a baseline level of security during transmission, its 70% adoption rate still leaves a significant portion of email traffic potentially vulnerable. S/MIME and PGP offer more robust encryption, but their lower usage rates – 30% in enterprises and 20% among individuals, respectively – underscore the need for user-friendly and accessible secure email solutions. This highlights the importance of choosing a platform that prioritizes strong, easily implemented encryption.
To help you make an informed decision, we've compiled a comparison of popular secure email platforms:
Secure Email Platform Comparison: A detailed comparison of popular secure email platforms showing encryption methods, key features, compliance standards, and pricing structures.
| Platform | Encryption Type | Key Features | Compliance | Starting Price |
|---|---|---|---|---|
| ProtonMail | End-to-End Encryption | Zero-access architecture, mobile apps, custom domains | GDPR | Free |
| Tutanota | End-to-End Encryption | Open source, two-factor authentication, encrypted calendar | GDPR | Free |
| Mailfence | End-to-End Encryption | Digital signatures, document storage, integrated calendar | GDPR | Free |
This table provides a starting point for your research. Remember to delve deeper into each platform's specifics to find the best fit for your needs.
Key Questions to Ask and Red Flags to Avoid
Don't hesitate to ask potential vendors tough questions about their security practices, data storage policies, and compliance certifications. Be wary of vague security claims, a lack of transparent privacy policies, or consistently negative user reviews. Migrating to a new email platform can seem like a big undertaking, but a well-planned transition can greatly improve your email security. Look for providers that offer migration assistance and resources to minimize disruption to your workflow. By prioritizing these factors, you can confidently select a secure email platform that truly delivers on its security promises, protecting your sensitive communications now and into the future.
Your Step-By-Step Guide To Send Secure Email Like A Pro

Sending secure email isn't just about the platform you choose. It's about adopting the right practices to keep your messages confidential. This guide provides a practical, step-by-step approach to sending secure emails, from initial setup to more advanced configurations.
Setting Up Your Secure Email
The first step is choosing a secure email provider. Look for one that offers end-to-end encryption and a zero-knowledge architecture. These features ensure that only you and your recipient can decrypt and read your emails. Providers like ProtonMail, Tutanota, and Mailfence are well-regarded for their robust security.
Once you've chosen a provider, enable multi-factor authentication (MFA). This adds another layer of security to your account, significantly reducing the risk of unauthorized access.
Sending a Secure Message
With your account secure, let's look at how to send an encrypted email:
-
Compose your message: Write your email as usual, paying close attention to the recipient's address.
-
Encrypt your message: Depending on your email platform, you might click an "Encrypt" button or select an encryption option from a menu. Some platforms encrypt all messages by default.
-
Attach files securely: If you're sending attachments, make sure they are encrypted too. Many secure email platforms automatically encrypt attachments along with the message.
-
Verify the recipient: Double-check the recipient’s email address. This crucial step prevents accidentally sending sensitive data to the wrong person.
-
Send: Click send, and your securely encrypted email is on its way.
For further information, check out this helpful resource: How to master encrypted email.
Key Management and Troubleshooting
Effective key management is essential for maintaining long-term security. Safeguard your private key and never share it. Create a secure backup of your key in case of device loss, but store this backup very carefully to prevent unauthorized access.
Sometimes, you might encounter issues sending or receiving secure emails. These issues can arise from compatibility problems with the recipient's email provider or incorrect encryption settings.
If problems occur, consult your email provider's documentation or support resources. Most providers offer troubleshooting guides and dedicated support channels. By following these steps and understanding the importance of key management, you can confidently send secure emails, protecting the confidentiality and integrity of your communications.
Advanced Security Features That Take Your Email Protection Further
Secure email communication involves much more than just basic encryption. A variety of advanced security features can significantly enhance your email protection. These features include digital signatures, multi-factor authentication (MFA), and message control options such as setting expiration times and recalling messages.
Ensuring Authenticity With Digital Signatures
A digital signature acts like a tamper-proof seal for your emails. It verifies the sender's identity and ensures the message hasn't been altered in transit. This is particularly important in combating email spoofing, where attackers forge sender addresses to appear legitimate. Digital signatures provide an important layer of trust, especially when handling sensitive information.
Strengthening Access With Multi-Factor Authentication
Multi-factor authentication (MFA) provides a crucial extra layer of security for your email account. MFA requires multiple authentication factors – something you know (like a password), something you have (like a security token), or something you are (like a biometric scan). This combined approach makes it significantly harder for unauthorized access, even if someone obtains your password.
Controlling Your Messages: Expiration and Recall
Message control features offer greater security and flexibility. You can set expiration dates for sensitive emails or recall messages sent in error. This allows for more control over your communication flow and minimizes the risk of unintended access. For more information on secure email practices, you might find this resource helpful: How to master HIPAA Compliant Email Encryption.
Beyond the Hype: Assessing Advanced Features
It's important to understand that not all advanced security features offer the same practical value. While certificate-based authentication provides strong identity verification, implementation can be complex. Similarly, biometric verification offers increased security, but its effectiveness hinges on the specific technology and user adoption.
Backup and Recovery Planning
Robust backup and recovery planning is crucial for maintaining access to your encrypted emails. Key escrow and backup strategies are essential in case of device loss or private key compromise. However, careful implementation of these strategies is vital to avoid creating security vulnerabilities. Maintaining the integrity of your secure communication requires thorough planning and secure procedures.
The following table provides a comparison of various email security features:
Email Security Features Comparison
Overview of advanced security features available across different email security solutions, showing capabilities and implementation complexity
| Security Feature | Protection Level | Implementation Difficulty | Best Use Cases |
|---|---|---|---|
| Digital Signatures | High | Moderate | Protecting sensitive information, ensuring authenticity |
| Multi-Factor Authentication | High | Moderate | Protecting against unauthorized access |
| Message Expiration | Moderate | Low | Limiting access to time-sensitive information |
| Message Recall | Moderate | Low | Correcting accidental disclosures |
| Certificate-Based Authentication | High | High | Highly regulated industries, high-security environments |
| Biometric Verification | High | Moderate to High | Environments requiring strong user authentication |
This table highlights the trade-offs between security levels, implementation complexity, and best use cases for different email security features. Choosing the right combination of features depends on your specific security needs and resources.
The Market Reality Behind Secure Email Solutions
The need for secure email has become a fundamental business requirement. This shift is driven by a combination of increasing cyber threats, more stringent data privacy regulations, and a growing awareness of the importance of protecting sensitive information. This demand has led to significant investment in secure email solutions, creating a dynamic market filled with innovative technologies and constantly evolving security standards.
Market Growth and Driving Forces
The global market for email security solutions is expanding rapidly. This growth highlights the increasing importance of safeguarding sensitive communications. Several key factors are contributing to this expansion:
- Increased Cyber Threats: The rise of sophisticated cyberattacks like phishing, ransomware, and business email compromise makes robust email security essential.
- Regulatory Compliance: Strict data privacy regulations, such as GDPR and HIPAA, require organizations handling sensitive personal information to implement secure communication practices.
- Cloud Adoption: The growing adoption of cloud-based email platforms has fueled the demand for secure cloud email security services.
- AI-Powered Threat Detection: The integration of AI and machine learning in threat detection is driving innovation in email security solutions, enabling them to better identify and neutralize evolving threats.
This market growth represents a fundamental change in how organizations and individuals approach email security. The focus is not only on protecting against current threats but also on proactively anticipating and mitigating future risks. For instance, the global market for email security solutions, valued at approximately $18.5 billion in 2024, is projected to reach $24 billion by 2030, with a CAGR of 4.4%. This expansion is largely driven by the increasing prevalence of sophisticated cyber threats. You can learn more by reading more on the Email Security Solutions Market.
The Impact of Compliance and Emerging Technologies
Compliance with regulations is a major driver of secure email adoption. Industries like healthcare, finance, and government face strict regulations regarding data privacy and security. These regulations often mandate the use of secure email for protecting sensitive data such as patient records or financial information. This has led to the development of specialized secure email solutions designed to meet these specific requirements.
Emerging technologies are also reshaping the secure email landscape. AI-powered threat detection systems analyze massive datasets to identify and block sophisticated phishing attacks and malware. Cloud-based solutions offer scalability and flexibility, making secure email accessible to businesses of all sizes. These advancements improve email security while making it more user-friendly and cost-effective.
Implications for Your Email Security Strategy
Understanding these market dynamics is crucial for developing a robust and adaptable email security strategy. Choose solutions that meet your present needs and can adapt to future threats and regulatory changes. Invest in platforms that offer robust encryption, advanced threat detection, and relevant compliance certifications. Staying informed about market trends and technological advancements will ensure your email communications remain secure in the face of evolving cyber risks. Investing in secure email is not an expense, but rather an investment in protecting your valuable data and reputation.
Key Takeaways For Your Secure Email Success
This section offers practical strategies for establishing and maintaining robust email security. We'll explore user training, policy development, and the importance of ongoing maintenance. This roadmap will provide you with the tools and knowledge you need to effectively protect your communications.
Building a Secure Email Culture: User Training and Policy Development
Effective user training is paramount. Many security breaches originate from human error, not technical vulnerabilities. Regular training should address key areas like recognizing phishing emails, creating strong passwords, and understanding the importance of secure email practices. Consistent training reinforces these crucial skills.
A well-defined email security policy is also essential. This policy should clearly outline acceptable email usage, password requirements, encryption protocols, and data handling procedures. Easy access to this policy for all employees is key. Consistent enforcement underscores the organization's commitment to email security.
Implementing Effective Training Methods
User training should be engaging and practical. Instead of lengthy lectures, prioritize interactive sessions, real-world examples, and simulated phishing exercises. These simulations can effectively assess employee awareness and uncover vulnerabilities.
Integrating security policies into onboarding processes and performance reviews promotes accountability. This reinforces the importance of these policies and demonstrates organizational commitment. A well-implemented policy is not static; it should adapt to evolving threats and organizational needs.
Maintaining a Secure Email Environment: Ongoing Monitoring and Adaptation
Email security is an ongoing process, not a one-time fix. Regular security audits are crucial for identifying vulnerabilities and ensuring compliance. These audits should examine email configurations, encryption protocols, and user access controls. This proactive approach allows you to address weaknesses before they're exploited.
Because the threat landscape is constantly changing, your security strategy must also adapt. Stay informed about emerging threats and update your policies and training accordingly. This vigilance ensures your email security remains effective against the latest attack methods. Regular updates to security procedures are essential for long-term protection.
Actionable Steps for Immediate Implementation
-
Conduct a security assessment: Evaluate your current email security practices and pinpoint areas for improvement.
-
Develop or revise your email security policy: Create a clear and comprehensive policy outlining secure email procedures.
-
Implement a user training program: Train employees to recognize phishing attacks, create strong passwords, and adhere to security protocols.
-
Regularly monitor and audit your systems: Conduct periodic security audits to identify and address vulnerabilities.
-
Stay informed about emerging threats: Keep abreast of the latest security threats and adapt your strategy accordingly.
By following these guidelines, you can build a robust email security framework that protects your communications, safeguards your data, and strengthens your overall cybersecurity posture.
Ready to enhance your email security? Start a free trial with Typewire today and experience the peace of mind that comes with secure email hosting. Explore Typewire's Secure Email Platform
Send Secure Email: Tips for Private, Safe Communication
Posted: 2025-06-03
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31