What Is a Digitally Signed Email?

Think of a digitally signed email as the modern equivalent of a letter sealed with a unique, tamper-proof wax seal. It's a method for providing mathematical certainty that a message is authentic and hasn't been altered. In short, it proves you are the real sender and that the content is exactly as you sent it, creating a vital layer of trust and enhancing your overall email privacy and email security.
Why Digital Signatures Are a Must-Have for Email Security
Imagine you’ve just sent a crucial contract or a high-value invoice from your company's hosted email platform. What if your recipient has no way of knowing it’s actually from you? In an environment rife with business email compromise and incredibly convincing phishing scams, that kind of uncertainty is a massive risk to your email security.
A digitally signed email cuts through that doubt. It provides two non-negotiable security guarantees for your messages, whether you're using a major hosted email platform like Google Workspace or Microsoft 365, or a privacy-focused provider.
This isn't a niche concern. As of 2025, an estimated 4.6 billion people are using email, a jump from 4.37 billion just two years earlier. That huge user base makes email a goldmine for fraudsters, turning verifiable security measures from a "nice-to-have" into an absolute necessity for protecting your digital privacy.
Getting Clear on Authenticity and Integrity
It's easy to mix up digital signatures with encryption, but they do very different jobs for your email security. Encryption is all about confidentiality—it scrambles a message so only the intended recipient can read it. Digital signatures, on the other hand, are focused on two other critical principles that are fundamental to email privacy:
- Authenticity: This is all about proving the sender's identity. A signature cryptographically confirms the email came from who it says it came from, helping people instantly spot fakes. It's a powerful way to https://typewire.com/blog/read/2025-10-29-how-to-prevent-email-spoofing-and-fortify-your-email-security.
- Integrity: This guarantees the message and its attachments are untouched. If anyone alters anything in transit—even changing a single comma—the recipient's email client will immediately flag the signature as invalid, protecting the message's content.
A digital signature doesn’t hide the contents of your message; it seals it. It’s a public declaration that the message is genuinely yours and exactly as you wrote it, building a foundation of trust that encryption alone cannot provide and is essential for secure communication.
Of course, digital signatures are just one piece of a much larger security puzzle. A truly comprehensive defense strategy should also include robust endpoint security solutions to protect devices where emails are actually read and written. When you combine these technologies, you create a powerful barrier against the daily threats aimed at your inbox.
How Digital Signatures Actually Work
To really get what’s happening under the hood of a digitally signed email, we need to look at a brilliant system called public key infrastructure (PKI). It sounds a bit intimidating, but the concept is actually quite straightforward. The whole thing hinges on a matched pair of digital keys that create an unbreakable mathematical bond between you and your message, ensuring your email security.
Imagine you have a special lockbox with two unique keys. One is your public key, which is like the slot on the lockbox. You can give copies of this slot to anyone and everyone. They can’t open the box with it, but they can use it to confirm that a package genuinely came from you.
The other key is your private key. This one you keep to yourself, always. It’s the only key that can lock a package in a way that’s unique to you. This is the key you use to "seal" your emails before they go out, a crucial step for maintaining your email privacy.
Creating the Digital Fingerprint
Before your email is sealed, the system first creates a one-of-a-kind identifier for it through a process called hashing. Think of it like a digital fingerprint. A special algorithm scans your entire message—every single word, space, and attachment—and boils it down into a short, fixed-length string of characters called a hash value.
This hash is completely unique to that specific email. If you were to change just a single comma in the original message and run the hash again, the new fingerprint would look completely different. It's this extreme sensitivity that makes hashing the perfect tool for proving a message hasn't been touched.
The diagram below shows how this process works from start to finish to protect your email's authenticity and integrity.
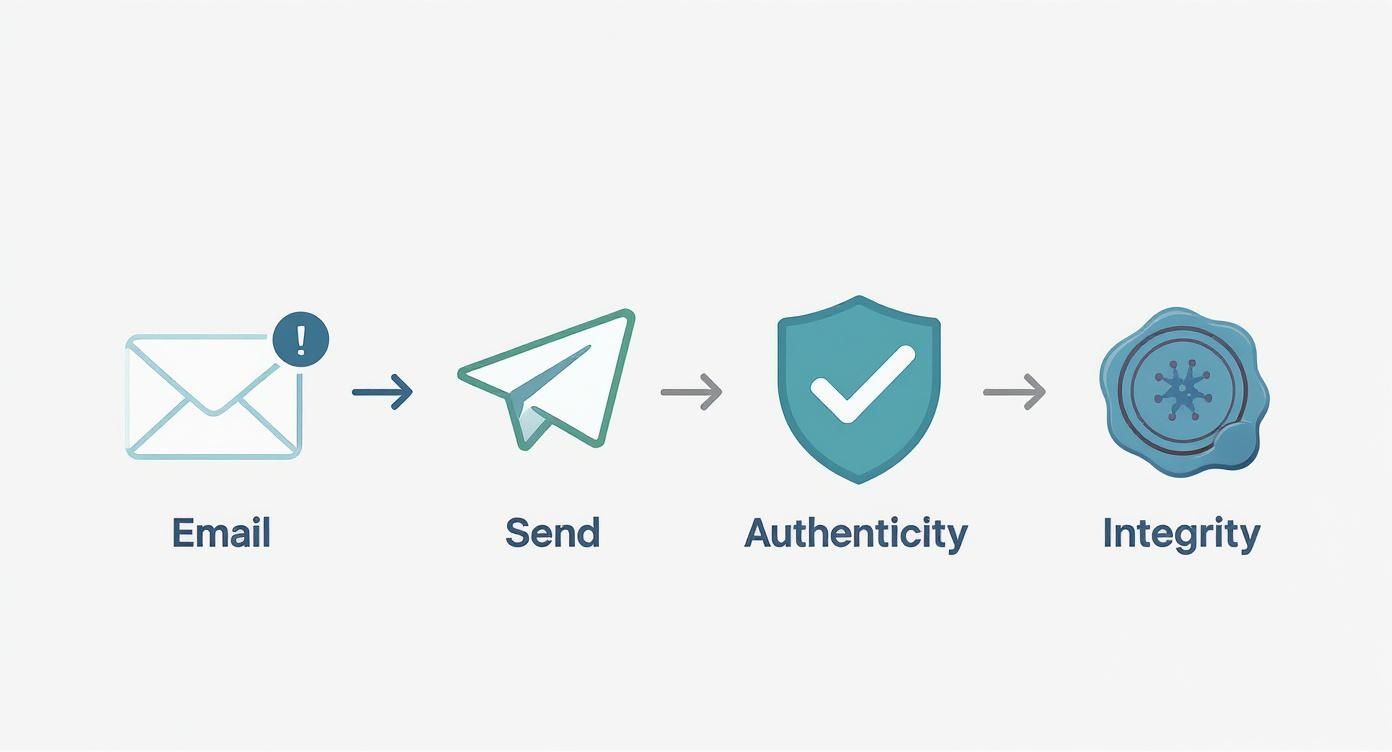
As you can see, a digital signature nails down the two most critical parts of email security: who sent the message and whether it arrived exactly as it was sent.
Locking the Fingerprint with Your Private Key
Once that unique hash is created, it's time to sign it. Your email client takes your closely guarded private key and uses it to encrypt only the hash. This encrypted hash is the digital signature.
It’s a common misconception that the whole email gets encrypted. It doesn't. The message itself stays perfectly readable, but it now travels with this locked-up fingerprint attached. It’s ready to be verified by anyone who has your public key. To see the bigger picture, it helps to understand the role of encryption in information security and how these concepts secure more than just email.
A digital signature is where the uniqueness of the message content (the hash) meets the uniqueness of the sender's identity (the private key). The result is a verifiable seal that's mathematically tied to both the email and its author.
This lock-and-unlock mechanism is a perfect example of asymmetric cryptography, where different keys are used for different jobs. We dive deeper into this in our guide on what is symmetric and asymmetric key encryption in email. It’s a core concept in modern cybersecurity.
How the Recipient Verifies Your Signature
When your email lands in someone's inbox, their email client kicks off a verification process automatically. It all happens in the background in a split second.
Here’s a breakdown of what their system does:
- Generate a New Fingerprint: First, the recipient's email client takes your message and runs it through the exact same hashing algorithm you used. This creates a fresh hash value on their end.
- Unlock Your Original Fingerprint: Next, the client uses your public key (which it can find easily) to decrypt the digital signature that was attached to your email. This reveals the original hash you created before you hit send.
- Compare the Two Fingerprints: Finally, it’s showtime. The client compares the new hash it just made with the original one it unlocked.
If the two fingerprints are identical, the signature is valid. Their email client will display a little badge of trust—like a checkmark or a ribbon—to show the message is authentic and untampered with. If the hashes don't match, it's a red flag that something was changed in transit, and the client will display a prominent warning that the signature is invalid.
Comparing Digital Signature Technologies
When it comes to digitally signing emails, you've got a few different tools for the job. Think of them as different types of ID cards—each one is valid, but they work in different systems and are trusted for different reasons.
The three main players in this space are S/MIME, PGP/GPG, and DKIM. While they all rely on the same core cryptographic magic, they're built for very different purposes. A large corporation using a hosted email platform will lean one way, while a privacy-minded individual will prefer another. Let's dig into what makes each one tick.

S/MIME: The Corporate Standard
If you work in a business environment, you've likely encountered S/MIME (Secure/Multipurpose Internet Mail Extensions). It’s the go-to standard for most companies because it relies on a centralized, hierarchical trust model that businesses understand well.
To use S/MIME, you need a digital certificate issued by a recognized Certificate Authority (CA), like GlobalSign or DigiCert. This CA acts as a trusted third party, a bit like a digital passport office, that verifies your identity before handing you a certificate. This is why major hosted email platforms like Microsoft 365 and Google Workspace have built-in support for it. It just works, right out of the box in clients like Outlook and Apple Mail, which makes IT administrators happy.
PGP/GPG: The People's Choice for Privacy
On the other end of the spectrum is PGP (Pretty Good Privacy) and its popular open-source implementation, GPG (GNU Privacy Guard). Instead of a central authority, PGP operates on a decentralized model called the "web of trust." This model is a cornerstone for users prioritizing absolute email privacy.
Here, trust isn't bought from a CA; it's earned. You establish your identity's validity when other people you know and trust digitally sign your public key, essentially vouching for you. This peer-to-peer system is a favorite among journalists, activists, and anyone who prefers not to rely on a corporate or government entity for their email security. The trade-off is that it’s more hands-on. Setting it up and verifying keys requires a bit more effort and often means installing plugins or specialized software.
DKIM: The Silent Guardian of Domains
Then there's DKIM (DomainKeys Identified Mail), which operates on a completely different level. It's not concerned with proving who sent an email, but rather with proving where it came from. DKIM adds an invisible, domain-level signature to every outgoing message from a hosted email platform.
DKIM’s job is to stop domain spoofing. It allows receiving email servers to verify that a message claiming to be from
yourcompany.comwas actually sent from a server authorized by that domain.
This process is completely transparent to the end-user. An administrator sets it up once, and it protects the entire organization's email traffic from then on. It’s a foundational piece of modern email security, working behind the scenes with SPF and DMARC to protect a company’s reputation and prevent phishing attacks.
Comparison of Digital Signature Technologies
Choosing the right technology depends entirely on your goals—are you a business trying to secure internal communications, an individual protecting sensitive sources, or a system administrator fighting phishing? This table breaks down the key distinctions.
| Feature | S/MIME (Secure/Multipurpose Internet Mail Extensions) | PGP/GPG (Pretty Good Privacy / GNU Privacy Guard) | DKIM (DomainKeys Identified Mail) |
|---|---|---|---|
| Trust Model | Centralized. Trust is granted by a formal Certificate Authority (CA). | Decentralized. Trust is built peer-to-peer through a "web of trust." | Domain-Level. Trust is verified via public keys in a domain's DNS records. |
| Primary Use Case | Signing and encrypting individual emails, mostly in corporate or government settings. | Securing person-to-person communication for privacy-focused individuals and communities. | Authenticating the sending domain to prevent email spoofing and phishing at scale. |
| Setup & Management | Individuals get certificates from a CA; often deployed and managed by an IT department. | Users generate and manage their own key pairs and must manually verify others' keys. | Configured once at the domain level by an administrator; completely invisible to users. |
| Integration | Native support in most major email clients (Outlook, Apple Mail) and platforms. | Typically requires third-party plugins or dedicated software for email clients. | Handled automatically by email servers and service providers; no user action needed. |
In short, S/MIME is for structured, top-down trust. PGP/GPG is for grassroots, decentralized trust. And DKIM is for automated, domain-wide trust. Many organizations will actually use both S/MIME for user-level security and DKIM for domain-level protection, as they solve different problems.
The Business Case for Digital Signatures
Beyond the technical wizardry, adopting digitally signed email is a smart business move, especially if you're using a hosted email platform. It takes email security out of the abstract IT department and turns it into a real asset that protects your revenue, builds stronger client relationships, and makes your business more resilient. Think of it less as an IT upgrade and more as a business upgrade.
Investing in digital signatures is one of the most direct ways to fight back against financially devastating cyber threats. Scams like invoice fraud and business email compromise (BEC)—where a criminal poses as an executive to reroute a payment—cost companies billions every year. A digitally signed email makes these cons incredibly difficult to execute.
When your finance team gets a signed payment request, they can confirm its origin and that it hasn't been messed with in a matter of seconds. That simple check closes the door on the main attack vector for invoice fraud, transforming a major vulnerability into a secure, verifiable process.
Building Unbreakable Client Trust
In business, trust is everything. Each email you send is a tiny billboard for your brand's professionalism and how seriously you take email security. Using a digitally signed email sends a clear message to your clients: "We care about the security of our communication, and by extension, we care about protecting you."
This has a surprisingly powerful effect on people. When clients see that little verification badge on your emails, it's an instant dose of reassurance.
- Contracts and Agreements: They know the legal documents they just received are the real deal and haven't been altered.
- Financial Reports: They can be confident that sensitive financial data is exactly as you sent it.
- Sensitive Data: It assures them that confidential information stays that way from your outbox to their inbox, respecting their email privacy.
Consistently showing up with this level of security builds a reputation for being reliable and careful, which can easily set you apart from competitors who might be cutting corners.
Meeting Stringent Regulatory Compliance
If you're in an industry with heavy regulation, proving your data is protected isn't just a good idea—it's the law. Regulations like GDPR in Europe and HIPAA in the U.S. require organizations to have the right technical measures in place to guarantee the integrity and authenticity of sensitive information, a core tenet of email privacy and email security.
A digitally signed email creates an auditable, cryptographic record that proves where a message came from and that it remains untouched. This becomes an indispensable tool for proving compliance during an audit and sidestepping the massive fines that come with mishandling data.
By implementing digital signatures, you aren't just locking down your data; you're creating a clear, defensible paper trail that keeps regulators happy.
The market is already signaling a major shift in this direction. The global e-signature market was valued at over $3 billion as of 2025, which shows just how much companies are investing in digital authentication. As we all move away from paper, the demand for tamper-proof digital documents is exploding for both efficiency and security. You can find more data on the growing adoption of these technologies on Exploding Topics. This trend really highlights that adopting digital signatures isn't just about keeping up; it's about getting ahead and aligning your business with modern standards.
A Practical Guide to Using Signed Emails
Putting digitally signed emails into practice is much easier than it sounds. Most modern hosted email platforms and apps have streamlined the whole process, so both individuals and entire organizations can add this critical layer of email security. Let’s walk through the steps for getting started.
Setup for Individual Users
If you're setting this up for yourself on something like Outlook or Apple Mail, you'll most likely be using S/MIME. The first thing you need is a digital certificate from a trusted Certificate Authority (CA). Think of it as your official digital ID card.
Once you have your certificate file, it's usually just a simple three-step process:
- Get a Certificate: You can obtain an S/MIME certificate from a well-known CA like GlobalSign or DigiCert. They'll need to verify your identity to make sure the certificate is really tied to you.
- Install the Certificate: Most CAs give you an installer or a file you just double-click. Your operating system then securely stores it in its keychain or certificate manager.
- Configure Your Email App: Dive into your email client’s settings—for instance, Outlook's Trust Center or Apple Mail's account settings. There, you'll find an option to link the new certificate to your email address for signing.
After that's done, you should see a "Sign" button or icon pop up when you compose a new email. Just click it, and your digital signature gets attached before you hit send. Simple as that.
How to Recognize a Signed Email
Once you start sending and receiving signed messages, spotting them is easy. Email clients use clear visual cues to show you that a signature has been checked and verified.
Keep an eye out for these common signs:
- A Checkmark Icon: Many apps display a small, colored checkmark right next to the sender's name.
- A Ribbon or Seal Badge: A little ribbon or seal icon is another popular symbol that says "this email is legitimately signed."
- An Informational Banner: Some platforms put a banner right at the top of the email, stating something like, "This message is signed and the signature is valid."
These little symbols give you instant confidence that the sender is who they say they are and that the message hasn't been messed with.
Setup for System Administrators
For admins managing email for a whole company on a hosted email platform, the game changes. You’re not thinking about one person, but about organization-wide deployment. Here, two key technologies are in play: S/MIME for individual user emails and DKIM for authenticating the entire domain.
Deploying S/MIME Across an Organization
Trying to manually install certificates on every employee's computer would be a nightmare. Instead, administrators typically use certificate management tools to automate the rollout. This ensures everyone gets a valid certificate without having to do anything technical themselves.
Publishing DKIM Records
In today's world, DKIM is non-negotiable for business email security. It works by adding a hidden signature to every single outgoing email. Receiving servers then check that signature against a public key you publish in your domain's DNS records. Setting up DKIM is a one-time task that protects your entire domain from being spoofed.
For system administrators, DKIM is the foundation. It protects your brand's reputation at scale, while S/MIME provides granular, user-level proof of identity for high-stakes communications. Both are essential components of a robust email security posture.
For a deeper dive, check out this guide on how to authenticate email with a real-world setup that works. It provides detailed instructions to help you lock down your domain's defenses.
Troubleshooting Common Issues
Even with a perfect setup, things can go wrong. The good news is that most problems with digitally signed emails fall into a few common buckets and are usually pretty easy to fix.
- Certificate Validation Errors: This usually happens when the recipient's email client doesn't trust the CA that issued your certificate. Make sure you're using a certificate from a major, widely recognized CA to avoid this.
- "Signature is Invalid" Warnings: If you see this, it’s a red flag. It means the message was altered in some way after it was sent. Don't trust the email's contents. Contact the sender through another channel, like a phone call, to confirm they sent it.
- Misconfigured Email Clients: Honestly, this is the most common problem. It's often just a setting that's off. Double-check that the S/MIME certificate is correctly associated with the sending email address in your client's settings.
By following these steps, both individuals and administrators can get digital signatures working smoothly, seriously boosting the email privacy and email security of their communication.
Frequently Asked Questions

As you start working with digitally signed email, you're bound to have some questions. It's a powerful tool, but some of the concepts can be tricky at first. This section tackles the most common questions we hear, with straightforward answers to help you see how this technology really works to protect your communications.
Our aim here is to clear up any confusion and solidify the core ideas, so you can feel confident every time you send or receive a signed message.
Signed vs. Encrypted Emails Explained
What's the real difference between a signed email and an encrypted one? This is a great question because people mix them up all the time, but they solve two very different email security problems.
Think of it this way. A digitally signed email is like sending a letter in an envelope sealed with your personal, official wax seal. Anyone can see the envelope, but that seal guarantees two things: it proves the letter really came from you (authenticity) and shows it hasn't been opened or messed with along the way (integrity).
An encrypted email is entirely different. It’s like putting that same letter inside a virtually unbreakable lockbox. Only the person with the one-of-a-kind key can open it and see what's inside. This gives you confidentiality, a key component of email privacy. For the highest level of security, you can actually do both—send an encrypted message inside a digitally signed envelope.
Software Needs for Recipients
Does the other person need special software to read my signed email? For the vast majority of business emails today, the answer is usually no.
Modern email clients like Outlook, Apple Mail, and even Gmail have built-in support for verifying S/MIME signatures, which is the standard in the corporate world. When someone using one of these hosted email platforms gets your signed email, their software handles the verification automatically in the background.
If the signature checks out, they’ll see a small trust icon—like a checkmark or a ribbon—letting them know the message is legit. It’s a seamless experience. While PGP users might need a plugin, the S/MIME process is mostly invisible for anyone on major platforms like Microsoft 365 or Google Workspace.
The beauty of standards like S/MIME is their integration into the email ecosystem. The security check happens without requiring the recipient to take any extra steps, making it a practical solution for enhancing trust in everyday business communications.
The Risk of Phishing Attacks
Can a digitally signed email still be a phishing attack? This is a critical point to understand for your email security. While a valid signature makes phishing much, much harder, it’s not entirely impossible.
A digital signature proves two key facts: the email truly came from the sender’s address (like support@yourbank.com) and its contents weren't changed in transit. This immediately shuts down attackers who are just "spoofing" the 'From' address, which is one of the most common phishing tricks.
But what if a skilled attacker compromises a legitimate account first? If a scammer hacks a real employee's email, they could send a phishing message that is correctly signed from that account. The signature would be technically valid because it came from the authentic source.
So, you should always view a digitally signed email as a strong layer of verification, but not a free pass to let your guard down. Stay vigilant about suspicious links, weird attachments, or out-of-character requests, even if the message has a valid signature.
What If a Signed Email Is Altered
What happens if someone modifies a signed email in transit? This is where digital signatures truly shine, showcasing their core function: the integrity check that is vital for email security.
When an email is signed, that signature is created from a unique "digital fingerprint" (a hash) of the original message. If an attacker intercepts that email and changes anything—even a single comma—the fingerprint of the now-altered message will no longer match the fingerprint locked into the signature.
When the recipient's email client runs its verification check, it will spot this mismatch instantly and the validation will fail. The client will then display a big, hard-to-miss warning that the signature is invalid and the message may have been tampered with. This tells the recipient not to trust what they’re reading, neutralizing the threat.
Ready to take control of your email privacy and security? At Typewire, we provide secure, private email hosting built on our own infrastructure, free from tracking and ads. Explore our plans and start your 7-day free trial to experience a truly private inbox. Learn more at Typewire.
What Is a Digitally Signed Email?
Posted: 2025-11-26
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31