Hosting a Mail Server: A Practical Guide to Email Privacy and Security

Running your own mail server is a powerful move, putting you in complete control of your digital communications. It's about setting up and managing your own email system on a server you control, giving you the final say on everything from email privacy to email security protocols. This guide will walk you through the process, but also explore when a dedicated, secure hosted email platform might be a better choice.
Why Bother Hosting Your Own Mail Server?
In an age of slick, convenient cloud email services, the idea of hosting your own mail server can feel like a throwback. But that convenience from major platforms often comes with a steep, hidden price: your privacy. When you use a third-party service, you're handing over your most private conversations to a corporation whose business model often involves mining your data.
Self-hosting turns that arrangement on its head. It is a conscious decision to prioritize digital sovereignty over plug-and-play simplicity, making you the master of your own communication infrastructure. It's not for everyone—it demands technical expertise and a commitment to maintenance—but the payoff in privacy and control is immense.
Take Back Full Ownership of Your Data
The single biggest reason for hosting a mail server is unquestionable data ownership. Your emails are an intimate log of your personal and professional life. When that data sits on someone else's server, it’s subject to their privacy policies, their terms of service, and their potential legal obligations to hand it over.
When you self-host, your emails live on your hardware, governed by your rules. Period.
- No Data Mining: Your messages won't be scanned to build an advertising profile or train an AI.
- True Deletion: When you delete an email, it's actually gone, not archived for future analysis.
- No Lockouts: You can't be kicked off your own server for violating an obscure term of service.
Build Genuine Email Privacy and Security
While standard email providers offer a baseline of security, self-hosting lets you construct a security fortress tailored to your exact needs. You decide on encryption standards, authentication methods, and how server logs are handled. For a much deeper look, we've covered how setting up an email server boosts privacy and security in another guide.
Choosing to self-host is a statement. It declares that your digital privacy isn't a negotiable feature but a fundamental right you intend to protect. You become the architect of your own secure communication channel, free from the prying eyes of corporations.
This level of control is becoming more critical. Daily email volume exceeded 319 billion in 2021 and is projected to hit 376 billion by 2025 as more people move to the cloud. You can learn more about these email market trends from The Radicati Group's report.
Hosting your own server is your way of opting out of this massive data consolidation. It’s more than a technical project; it's a powerful education in how one of the internet's most essential protocols works and how to protect it.
Building Your Technical Foundation
Before installing software, you must get your foundation right. This is the most important part of hosting a mail server. Your pre-flight checklist will determine whether your emails land in the inbox or vanish into a spam filter.
Your first decision is where your server will live. A Virtual Private Server (VPS) often hits the sweet spot between cost and control. But don't just shop for the lowest price. The real value is in a provider with a reputation for clean IP address ranges. Starting with a tainted IP is a fight you don't want to have.
You’ll also need a static IP address. This is non-negotiable. Unlike the dynamic IP from your home internet, a static one never changes, giving your server a stable identity that other mail servers can learn to trust.
This image shows how the core pillars of self-hosting—ownership, privacy, and control—work together to form a secure system.
Each element reinforces the others, creating a foundation for true email privacy.
Securing Your Digital Identity
With your server infrastructure chosen, it's time for your digital address: the domain name. Best practice is to register a new domain exclusively for sending email. This isolates its reputation, which is a smart long-term play for deliverability and email security.
If you can find a domain that has been registered for a while, even better. Major email providers are often suspicious of brand-new domains, sometimes blocking them entirely for the first few months. An established domain helps you skip that painful "probationary period."
Pro Tip: Before committing to a VPS, run the IP address through several blacklist-checking tools. A previously blacklisted IP can be a deliverability nightmare. It's far easier to ask for a new IP at the start than to repair a damaged reputation later.
Once the domain is yours, you need to configure its DNS records. These are the internet's sorting instructions for your email and your most powerful tool for proving you aren't a spammer.
Understanding Core DNS Records for Email
Setting up DNS can feel arcane, but it boils down to a few key records working together to build trust. Skipping any of them will severely damage your ability to send email reliably.
Here are the absolute essentials:
- MX (Mail Exchanger): This record points to the server responsible for receiving email for your domain. It’s the mailing address for your server.
- SPF (Sender Policy Framework): This record is a public list of servers authorized to send email from your domain. It's a critical tool for preventing scammers from spoofing your address.
- DKIM (DomainKeys Identified Mail): DKIM adds a unique digital signature to every email you send. The receiving server checks this signature against a public key in your DNS, proving the message hasn't been altered in transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC ties SPF and DKIM together. It tells other servers what to do if an email fails those checks—reject it, quarantine it, or report back to you.
Getting these authentication methods right is the foundation of your email security and deliverability. For a deeper dive, our complete guide to email authentication breaks down exactly how they work.
Assembling Your Mail Server Software Stack
With your server prepped, it's time to choose the software that will run your mail server. Think of it less like installing a single app and more like assembling custom components—the engine, the transmission, the security system—that must work in perfect harmony.
The software you pick will define your server's security, performance, and day-to-day user experience.
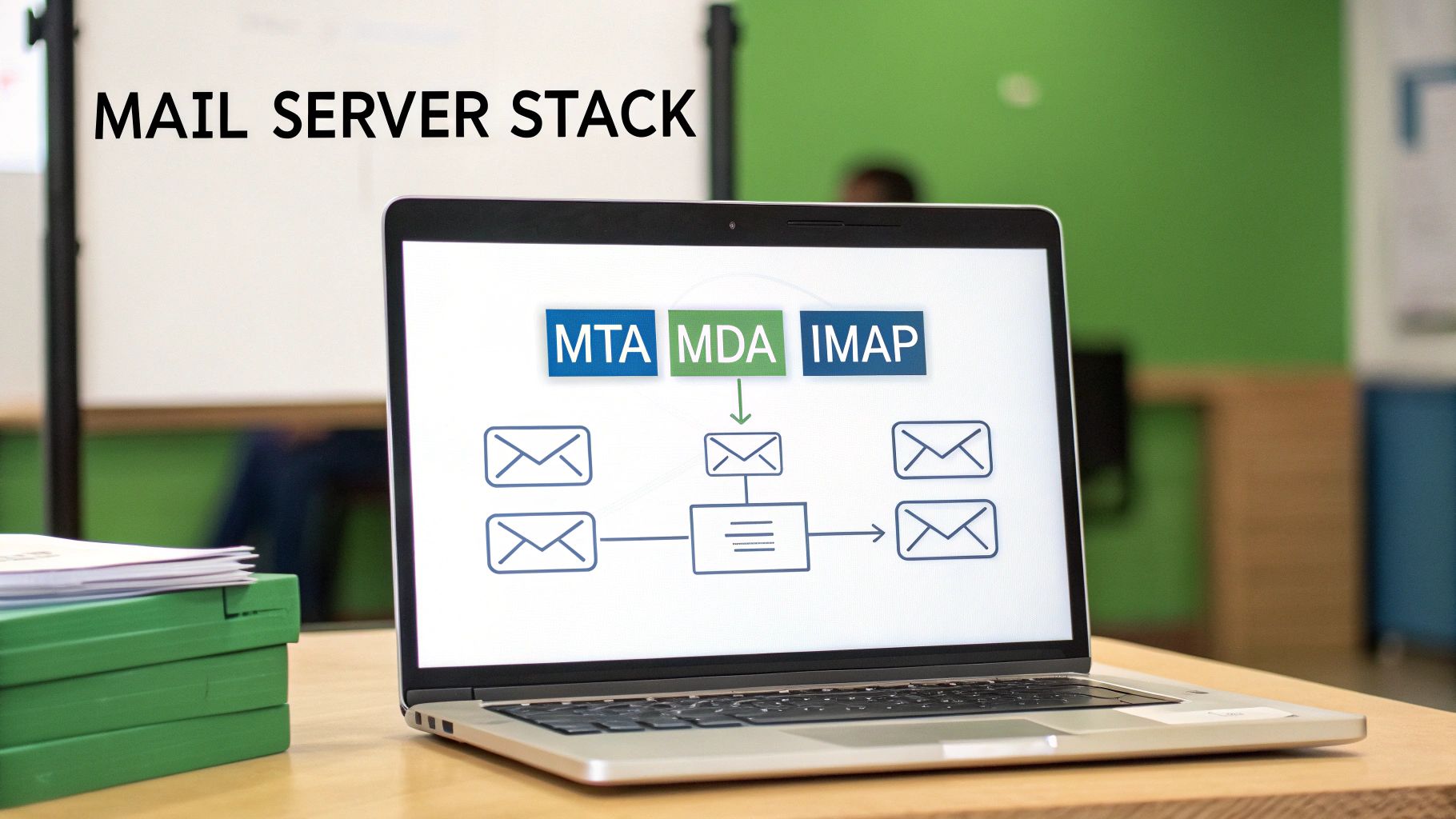
This isn't just a technical decision; it's a strategic one. Your choices here directly impact your control over your data and email privacy.
The Core Components of an Email System
A mail server is a collection of specialized tools. The two most important are the Mail Transfer Agent (MTA) and the Mail Delivery Agent (MDA).
-
Mail Transfer Agent (MTA): This is your server's public-facing post office. The MTA uses the SMTP protocol to talk to other mail servers, sending your outgoing mail and receiving incoming mail. Popular, battle-hardened choices are Postfix and Exim.
-
Mail Delivery Agent (MDA): Once the MTA accepts an incoming email, it hands it to the MDA. The MDA files the email into the correct user's mailbox. The most common tool for this is Dovecot, which also provides the IMAP and POP3 services your email clients use to retrieve messages.
The combination of Postfix and Dovecot is a classic for a reason—it's incredibly stable, secure, and well-documented.
By picking and configuring these components yourself, you gain total control. You decide which encryption standards to enforce, how users authenticate, and what gets logged. That's a level of granular control you'll never find with a standard hosted email platform.
Building Out a Modern, Secure Stack
A simple MTA/MDA setup isn't enough. To protect your server from the constant flood of junk and malicious attacks, you need dedicated spam and virus filtering. This is where a layered security approach is critical.
You’ll want to add a couple more components:
-
Spam Filter: SpamAssassin is a must. It inspects every incoming email and scores it based on thousands of rules, allowing you to automatically reject or flag spam.
-
Antivirus Scanner: An antivirus engine like ClamAV is essential. It scans all attachments for malware, viruses, and phishing attempts before they can land in a user's inbox. This is a non-negotiable step for email security.
The scale of email today makes this essential. The global user base is expected to reach 4.6 billion by 2025, with daily email volume projected to hit nearly 392.5 billion by 2026. As you can see from these email marketing statistics, that massive volume is a huge attack surface. Robust filtering isn't a luxury; it's a core requirement.
Mail Server Software Stack Comparison
Here’s a high-level look at the most common open-source components to help you decide on a stack.
| Component Type | Popular Software | Primary Function | Best For |
|---|---|---|---|
| Mail Transfer Agent (MTA) | Postfix, Exim | Sends and receives email from other servers (SMTP). | Postfix: Security and simplicity. Exim: Extreme flexibility and customization. |
| Mail Delivery Agent (MDA) | Dovecot, Procmail | Delivers email to user mailboxes; provides IMAP/POP3 access. | Dovecot: The modern standard for performance, security, and features. |
| Spam Filter | SpamAssassin, Rspamd | Analyzes and scores emails to identify and block spam. | SpamAssassin: Highly configurable and widely used. Rspamd: Faster, modern alternative. |
| Antivirus Scanner | ClamAV | Scans email attachments for viruses, malware, and other threats. | ClamAV: The open-source standard for email antivirus scanning. |
The classic Postfix, Dovecot, SpamAssassin, and ClamAV stack remains an excellent and well-documented choice for anyone starting out.
What About All-in-One Solutions?
If assembling this stack piece by piece sounds daunting, you have another option. All-in-one mail server suites are designed to simplify this entire process.
Projects like Mail-in-a-Box or Mailcow bundle all the necessary software into a single, cohesive package. They come with automated installation scripts that handle the most complex parts of the configuration for you.
- The DIY Stack: This path is for those who want absolute control and a deep understanding of how everything works. It’s more work but offers unmatched flexibility.
- The All-in-One Suite: This is for someone whose main goal is a private, self-hosted email server without spending weeks on configuration. It offers a much faster path to a secure system.
A DIY server is an incredible learning experience. But an all-in-one suite gets you 90% of the benefits with only 10% of the setup headache, making it a fantastic and practical choice for many.
Hardening Your Server for Email Security
Getting your mail server software running is just the start. An unconfigured server is a welcome mat for spammers and attackers. The next critical phase is to turn that basic setup into a digital fortress. This layered defense protects your data and ensures genuine email privacy.
A properly hardened server also tells other mail servers you're a responsible operator, which is a massive factor in getting your emails delivered.

Implementing Robust Spam and Virus Filtering
Your first line of defense is dealing with the relentless flood of incoming junk. Without powerful filtering, your inbox will become a nightmare and your server will be exposed to attacks.
- SpamAssassin: This is the champion of spam identification. It puts every email through a gauntlet of tests to generate a spam score. You can set rules to reject emails above a certain score or tag them for user-side filtering.
- ClamAV: A solid antivirus engine is non-negotiable. ClamAV scans every attachment for malware. Integrating it into your mail flow ensures malicious files are stopped on arrival, protecting users from phishing and ransomware.
This proactive filtering is a fundamental part of responsible server management when hosting a mail server. It keeps your users safe and prevents your server from being used to spread junk, which is the fastest way to get your IP blacklisted.
Enforcing Encrypted Connections with TLS
Sending an email without encryption is like mailing a postcard. For true email security, you must enforce encrypted connections for every step of an email's journey using Transport Layer Security (TLS) certificates.
Forcing TLS encryption isn't optional anymore. It's the bare-minimum expectation for any legitimate mail server. Without it, you expose user credentials and message content, and other servers will rightly refuse to trust you.
Let's Encrypt is a free, automated certificate authority that provides the TLS/SSL certificates you need. A tool like Certbot can automate the entire process of getting and renewing them.
You’ll need to configure your server to use these certificates for:
- SMTP (Sending/Receiving): Encrypts the conversation between your mail server and others.
- IMAP/POP3 (Client Access): Encrypts the connection between an email app and your server, protecting logins and content.
Locking Down Your Server's Perimeter
You also have to secure the underlying operating system. Your server is being scanned for weaknesses 24/7.
A well-configured firewall is your most critical perimeter defense. Using ufw or iptables, you should set a "deny by default" policy, blocking all incoming traffic and then poking specific holes only for the services you need.
To fend off automated login attempts, Fail2Ban is an absolute must-have. It watches server logs for brute-force attacks and automatically updates your firewall to block the attacker's IP.
Finally, get into a strict routine of applying security patches for your OS and all installed software. This closes security holes as soon as they're discovered, keeping your fortress walls strong.
Self-Hosted vs. Hosted Email Platforms: When to Hand Over the Reins
So you've hardened your server and have it humming along. Now what? You've reached a fork in the road. One path is continued self-management—a commitment to being a permanent, on-call sysadmin. The other leads to a managed, privacy-focused hosted email platform.
This isn't about giving up. It's about making a smart decision based on your time, expertise, and what you ultimately want to achieve with your email security and privacy.
The truth about self-hosting is that the job is never done. You are now responsible for monitoring IP blacklists, troubleshooting deliverability issues, and patching vulnerabilities at a moment's notice. For many, the initial thrill of control eventually gives way to the practical need for reliability.
The True Cost of Total Control
The siren song of self-hosting is digital sovereignty. You own the server, control the software, and set every rule. This gives you the pinnacle of email privacy. But that control comes with an equally absolute level of responsibility.
Every security patch, every software update, every configuration tweak—it's all on you. When a major provider randomly blacklists your IP, you're the one navigating their delisting process. This constant, ongoing effort is the hidden tax of self-hosting, paid not in dollars, but in hours.
When Hosted Email Platforms Just Make Sense
A privacy-focused hosted email platform offers a powerful middle ground. You offload the immense technical headache of server management while keeping the core benefits you wanted: email security and data privacy.
Unlike big-name free providers, specialized services are built to protect user data, not sell it. Companies like Typewire operate on a simple principle: your email is your own. They provide expertly managed infrastructure, robust security, and stellar deliverability that are incredibly difficult for one person to achieve alone. And they do it all without mining your messages for ad revenue.
The question isn't "Can I run my own server?" It's "Is running my own server the best use of my time?" For a growing number of people and businesses, a privacy-first hosted email platform is the smarter choice.
To put the challenge in perspective, Gmail controls roughly 27.76% of the email client market, serving over 2.5 billion users. That operation requires massive data centers and entire teams dedicated to security. This breakdown of Gmail's scale on clean.email underscores the mountain a solo admin has to climb.
Decision Matrix: Self-Hosted vs. Privacy-Focused Hosted Email
Choosing your path boils down to a trade-off analysis. This table can help you weigh the key factors.
If you're leaning toward a hosted solution, it's worth checking out this guide on the top 7 best hosted email platforms for business security in 2025.
| Factor | Self-Hosted Mail Server | Privacy-Focused Hosted Service (e.g., Typewire) |
|---|---|---|
| Time Commitment | High: Requires constant monitoring, maintenance, and troubleshooting. | Low: The provider handles all technical management and security. |
| Technical Expertise | Expert Level: Deep knowledge of Linux, DNS, and mail protocols is essential. | Minimal: Requires basic user setup and domain configuration. |
| Control & Privacy | Absolute: You have full control over all data, logs, and policies. | High: Strong privacy policies, no data mining, but you trust the provider. |
| Deliverability | Variable: Dependent on your skill in managing IP reputation and DNS. | High & Consistent: Managed by experts who specialize in deliverability. |
| Initial Cost | Moderate: VPS hosting fees and potential software licenses. | Predictable: Fixed monthly or annual subscription fee. |
| Security | Your Responsibility: Effectiveness depends entirely on your configuration. | Expert-Managed: Handled by a dedicated team using advanced tools. |
Ultimately, both paths can lead to a more private and secure email experience. The real question is which one honors your most valuable resource: your time.
Frequently Asked Questions
Even the best-laid plans run into questions. Before you dive into hosting a mail server, let’s tackle the most common concerns.
What Are the Real Costs Involved?
Financially, getting started can be cheap. A Virtual Private Server (VPS) costs just a few dollars a month, and the core software is open-source and free.
The real currency you'll spend is time. The setup, constant security monitoring, and troubleshooting—that's the investment. When an email gets flagged as spam or a security patch needs to be deployed now, you're on call.
The biggest investment in self-hosting isn't money; it's your time. The ongoing commitment to maintenance, email security, and deliverability is a very real operational cost.
How Does Self-Hosting Compare to Gmail for Privacy?
This gets to the heart of why people self-host. With a free service like Gmail, you are the product. Your messages are scanned to build advertising profiles and feed AI models. It's a trade-off: convenience for a lack of true email privacy.
When you're hosting a mail server yourself, that dynamic vanishes. There's no third party scanning your messages and no data mining. You control the logs and encryption policies. The privacy is absolute because you are the gatekeeper of your own data.
Is Maintaining Email Deliverability Really That Hard?
Honestly? Yes. It's the single most frustrating and ongoing challenge. Big players like Google and Microsoft are inherently suspicious of mail from small, independent servers.
You can do everything right—flawless DNS, top-notch encryption, a clean IP—and still see your emails land in spam. Building a good sender reputation takes a lot of patience.
- IP Reputation: Your server's IP is everything. If it has a bad history, you've inherited a problem.
- Domain Age: New domains are often treated with suspicion for months.
- Sending Volume: Inconsistent sending patterns can look spam-like to automated filters.
Once your mail server is running smoothly, using effective email management tips can help you manage your inbox and improve your day-to-day productivity.
What Happens If My IP Address Gets Blacklisted?
Getting blacklisted happens. The immediate effect is that other servers will refuse to accept your email. First, use an online tool to find out which blacklist you're on.
Then, you have to diagnose the cause. Was your server compromised? Is there a mistake in your SPF records? Once fixed, you must follow each blacklist's specific delisting process. This can be a slow, painful process that leaves your email out of commission for days. It’s a stark reminder of the difference between having a dedicated team managing your email security on a hosted email platform and doing it all yourself.
Ready for secure, private email without the technical headaches? Typewire offers expertly managed hosting that puts your privacy first. Get the control you want and the reliability you need. Explore our plans and start your free 7-day trial today at typewire.com.
Hosting a Mail Server: A Practical Guide to Email Privacy and Security
Posted: 2025-11-22
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31