Hosting a Mail Server for Privacy and Control

Deciding to host your own mail server is a massive step toward taking back control of your digital life. It means the hardware, the software, and most importantly, your data, are all yours. This isn't just a technical project; it's a declaration that you're in the driver's seat when it comes to your own email privacy and email security.
Why Bother Hosting Your Own Mail Server?

Let's be blunt: running your own mail server is a choice for digital independence and robust email security. Every time you use a major email provider like Gmail or Outlook, you're handing over your private communications to be stored on their servers. These companies are well-known for scanning email content to build advertising profiles, analyze user behavior, and even train their AI models. Your data effectively becomes their product.
When you host your own server, that entire dynamic flips. You reclaim complete ownership and control over your email privacy. No third party is reading your messages, period. This approach is a direct rejection of data mining and ensures your communications stay truly private. It's a powerful principle, and if you're interested in digging deeper, our guide on data sovereignty and its key insights is a great place to start.
The Big Shift Away From Self-Hosting
Email management has changed dramatically over the years. Back in the late 1990s, it was standard practice for most businesses to run their own mail servers in-house. It was just how things were done.
Fast forward to 2020, and industry surveys revealed a startling shift: less than 20% of organizations worldwide were still managing their own mail servers. The explosion of managed email providers completely reshaped the market, as you can see in these long-term web and mail server trends on Wikipedia.
This move was all about trading control for convenience. But today, the pendulum is swinging back for a growing number of people who are more aware of the privacy and security they've given up.
The core motivation for hosting a mail server is simple: to be in complete control of your data. You decide the rules, you manage the security, and you are the only one with access to your communications.
What You Really Gain By Taking Control
Choosing to go the self-hosted route gives you a few powerful advantages that you simply can't get from a standard provider. These are the real reasons people take on the challenge.
- Absolute Privacy: Your emails live on your server. This means no more third-party scanning for ads, data mining, or surveillance. What's yours stays yours.
- Total Customization: You can fine-tune every single detail. Want unlimited storage for certain accounts? Need to implement a niche security protocol? You can do it all without asking for permission.
- No Random Lockouts: You'll never be at the mercy of a big corporation that can suddenly suspend or delete your account, often with no clear explanation or way to appeal. You own the account and all the data tied to it.
Of course, with great power comes great responsibility. You are now the sysadmin. It's on you to handle email security, maintain uptime, and make sure your emails actually get delivered. It's a real commitment that demands technical skill and ongoing effort.
Let's quickly compare the two paths.
Self-Hosted vs Managed Email At a Glance
The table below breaks down the fundamental differences between running your own server and using a service like Gmail or Outlook. It’s a classic trade-off between control and convenience, with email privacy and security at its core.
| Feature | Self-Hosted Mail Server | Managed Email Provider (e.g., Gmail, Outlook) |
|---|---|---|
| Data Control | Complete ownership and control over all data. | Data is stored on third-party servers under their policies. |
| Privacy | High. No third-party scanning or data mining. | Low. Emails are often scanned for advertising and analytics. |
| Customization | Unlimited. Full control over software, storage, and rules. | Limited. You are restricted to the provider's features. |
| Technical Skill | High. Requires expertise in server management and security. | Low. Minimal technical knowledge is needed. |
| Cost | Varies. Involves server, domain, and time investment. | Often "free" (ad-supported) or a fixed monthly fee. |
| Responsibility | You are responsible for all maintenance, security, and uptime. | The provider handles all maintenance, security, and uptime. |
Ultimately, choosing to self-host is about prioritizing email privacy and control above all else. This guide is here to walk you through exactly how to manage those responsibilities and build a server you can rely on.
Getting Started: The Groundwork for Your Mail Server

Before you even think about installing software, let's talk about planning. Seriously. Diving headfirst into the technical side without a solid plan is a recipe for deliverability nightmares and gaping security holes. Think of this stage as sketching the blueprint for your email infrastructure—a little bit of forethought now will save you a world of hurt down the road.
The first big decision is where your server will physically (or virtually) live. A home server gives you ultimate hands-on control, but it's a tough path. You'll run into issues with residential ISP restrictions, dynamic IP addresses, and power reliability. For this reason, most people go with a Virtual Private Server (VPS) from a reputable hosting company. This gets you a dedicated slice of a server in a proper data center.
No matter which route you take, one thing is absolutely non-negotiable: a static IP address. This IP is your server's permanent address on the internet. If it keeps changing, other mail servers won't trust you, and your mail will just get bounced. Dynamic IPs, the kind you typically get with a home internet connection, are a complete non-starter here.
Choosing Your Server's Home
When you're shopping for a VPS, the reputation of the IP address they assign you is everything. It's a frustrating truth of the internet that some hosting providers have entire blocks of IP addresses that are blacklisted because of a previous user's spamming habit. You could get a brand-new server that already has a bad reputation before you’ve sent a single email.
You absolutely have to do your homework before you commit:
- Check Provider Reputations: Spend some time on forums and community sites. See what experienced users are saying about a host's IP quality.
- Use Blacklist Checkers: The moment you get your IP, run it through a tool like MXToolbox to see if it’s on any major spam lists.
- Don't Be Afraid to Re-roll: If you get a dirty IP, act fast. Contact support and ask for a new one, or even cancel and sign up again. It’s infinitely easier to get a clean IP at the start than it is to get a tainted one removed from blacklists.
This first step is foundational. A clean IP address is the cornerstone of good email deliverability. It's what gets your messages into the inbox instead of the spam folder.
One of the most common pitfalls for new self-hosters is underestimating the importance of IP reputation. An IP address with a history of sending spam can make deliverability nearly impossible, no matter how perfectly your server is configured.
The Right Operating System and Domain
Once you've secured your server space and a clean IP, you need to pick an operating system (OS). For a mail server, stability and security are the name of the game. The vast majority of self-hosted email runs on a solid Linux distribution.
- Ubuntu Server: This is a hugely popular choice. It's well-documented and has a massive community, which means finding tutorials and support is a breeze.
- Debian: Known for being rock-solid and stable. Its conservative update cycle makes it a great "set it and forget it" option for a critical service like email.
- CentOS/AlmaLinux: Another top-tier choice, often favored in enterprise settings for its long-term support and robust security features.
Finally, you need a domain name that you control. This will form the basis of your email addresses (e.g., you@yourdomain.com). Through your domain registrar, you'll set up the critical DNS records that tell the internet how to find your mail server. These records act like signposts, directing email traffic and building trust with other mail systems. We'll get into the nitty-gritty of configuring them later on, but for now, just make sure you have full administrative access to your domain's DNS settings.
Choosing and Configuring Your Mail Software
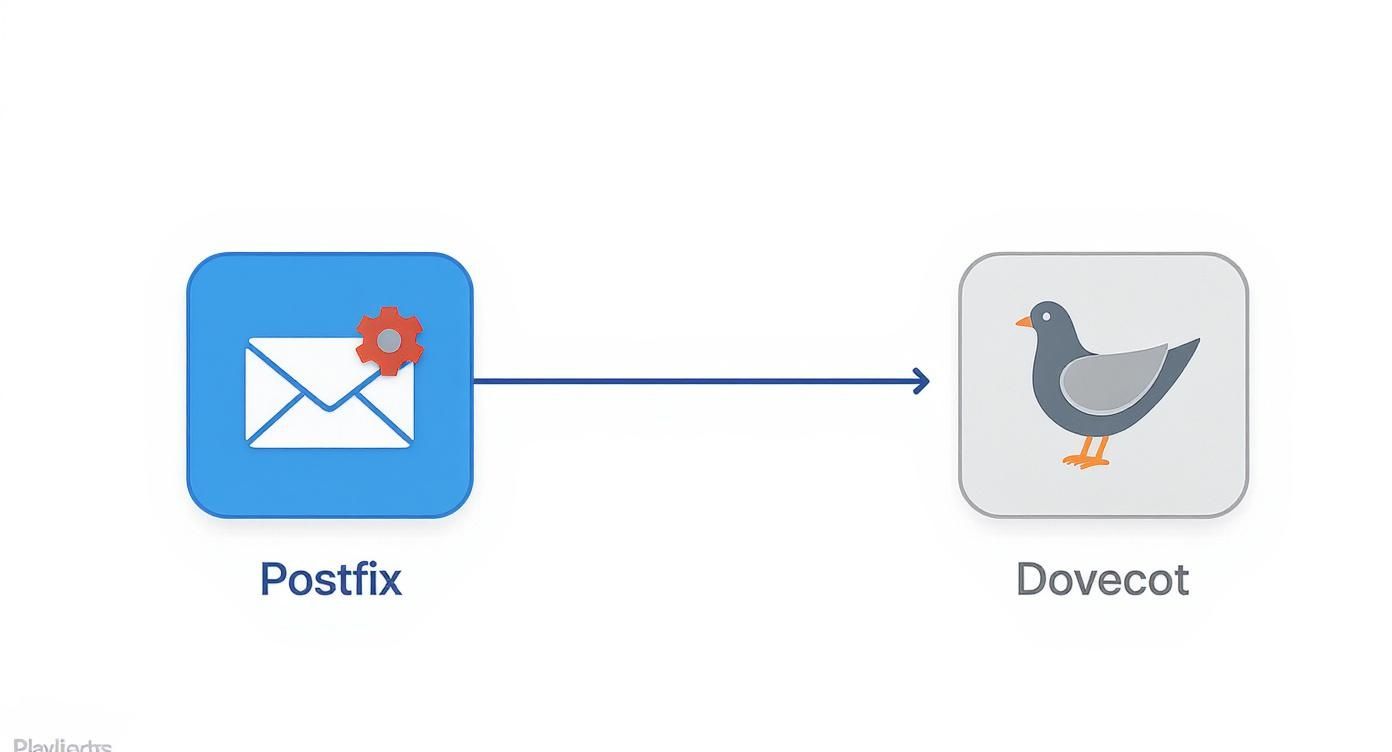
Alright, your server is up and your domain is ready. Now comes the fun part: picking the software that will actually run your email operation. A mail server really has two core jobs: one is to talk to the rest of the internet to send and receive mail, and the other is to let your users securely access their inboxes. These two jobs are almost always handled by separate, specialized pieces of software that work in tandem.
When it comes to self-hosting email, the combination of Postfix and Dovecot is the undisputed champion. This isn't just a popular choice; it's a battle-tested, industry-standard setup for a reason. Both are open-source, have fantastic documentation, and carry a rock-solid reputation for security and stability.
The email world has changed a lot. Back in the early 2000s, Sendmail was king, running on roughly 30% of mail servers. By 2010, Postfix had taken the crown, capturing about 35% of the market thanks to its modern, security-first design. While massive providers like Google Workspace and Microsoft 365 now handle over 80% of business email, Postfix remains the cornerstone for those of us who run our own show. You can get a better sense of these trends in email server technology to see the bigger picture.
The A-Team: Understanding Postfix and Dovecot
It’s crucial to know what each piece of this puzzle does.
Postfix is your Mail Transfer Agent (MTA). Think of it as the public-facing post office for your server. It uses the SMTP protocol to talk to every other mail server on the internet. When someone sends an email to you, their server connects to your Postfix. When you send an email out, your Postfix connects to their server. It handles all the public transit.
Dovecot, on the other hand, is your Mail Delivery Agent (MDA)—or more precisely, your IMAP and POP3 server. It handles the private side of your setup. After Postfix accepts an incoming email, it passes it off to Dovecot. Dovecot then securely files it away in the correct user’s mailbox. When you open your email app (like Thunderbird or Apple Mail), you're connecting directly to Dovecot to read your mail.
Postfix is the mail carrier, handling the pickup and delivery of letters between different post offices across the country. Dovecot is the locked mailbox at your house where you retrieve your personal mail. One manages the public network, the other provides private access.
This "separation of duties" is a fundamental security principle. Postfix is designed to be a fortress because it’s exposed to the wild internet. Dovecot, which deals with authenticated users and their private data, can be tucked away behind the scenes, adding another layer of protection.
Getting the Configuration Right
The real art is in teaching Postfix and Dovecot how to work together. You'll be defining your users, your domains, and your security rules. While we won't get into the nitty-gritty of command-line editing here, understanding the core concepts is what will make or break your setup.
Here’s what you’ll be configuring at a high level:
- Virtual Mailboxes: This is the modern way to manage users. Instead of creating a full system account for every email address, you create "virtual users." Their details (
user@yourdomain.com, password, etc.) are stored safely in a database or a simple text file. This is far more secure and infinitely easier to manage. - Domain Handling: You need to tell Postfix which domains it's responsible for. This is how it knows to accept mail for
you@yourdomain.combut reject mail intended forsomeone@gmail.com. You can easily list multiple domains for Postfix to handle on a single server. - The Authentication Handshake: Postfix needs to know that the person trying to send an email is a legitimate user. This is where Dovecot comes back in. Using a protocol called SASL, your email client authenticates with Dovecot, which then vouches for you, telling Postfix, "Yep, this person is one of ours. You can send their message."
What This Looks Like in Practice
Let's make this less abstract. Imagine you're setting up email for two domains, example.com and another-domain.net.
-
Telling Postfix What Domains to Handle: Deep in your Postfix configuration, there’s a parameter often called
virtual_mailbox_domains. This would point to a simple text file that contains nothing more than your domains:example.comanother-domain.net -
Mapping Users to Their Mailboxes: Next, you need to tell Postfix where to put the mail for each user. You'll create a "virtual mailbox map," which is another simple file. It connects an email address to a storage path on your server.
contact@example.com example.com/contact/sales@example.com example.com/sales/info@another-domain.net another-domain.net/info/
This map tells Postfix, "When a message for contact@example.com arrives, deliver it to this specific folder." This keeps everything organized and prevents one user's mail from getting mixed up with another's.
By building your mail server on this modular Postfix and Dovecot foundation, you create a system that’s not just powerful, but also much easier to secure and maintain for years to come. This is how you gain true control over your email.
Ensuring Your Emails Actually Get Delivered
Getting Postfix and Dovecot up and running is a huge milestone, but it's really only half the job. What good is a perfectly tuned mail server if every single email it sends lands in the recipient's spam folder? This brings us to the most delicate and often frustrating part of the whole process: email deliverability.
Deliverability isn’t a switch you can flip. It’s a reputation you have to build from the ground up, one email at a time. The big players like Google and Microsoft are extremely wary of mail coming from new, unknown servers. Your primary goal is to prove to them that you're a legitimate sender, not just another spammer firing up a fresh IP.
This is where a few critical DNS records come into play. Think of these as public declarations about your server's identity. They create a chain of trust that other mail systems can follow to verify you are who you say you are. Without them, you’re just an anonymous stranger knocking on their digital door—and they'll almost certainly turn you away.
The Holy Trinity of Email Authentication
To get past the internet's gatekeepers, you absolutely must implement three core email authentication standards. Each one tackles a different piece of the trust puzzle, and they work together to verify your identity and protect your domain's reputation from being hijacked by phishers and spammers.
Sender Policy Framework (SPF)
SPF is the foundational layer. At its core, it's a simple TXT record in your DNS that publishes a list of all the IP addresses authorized to send email for your domain. It’s like a bouncer’s guest list for email servers.
When a server receives a message from you@yourdomain.com, it quickly checks your domain's SPF record. If the email originated from an IP on your list, it passes. If not, the receiving server can be pretty sure it’s a forgery and will likely reject it. This is your first and most basic line of defense against email spoofing.
DomainKeys Identified Mail (DKIM)
While SPF verifies the server, DKIM authenticates the message itself. It uses public-key cryptography to attach a unique digital signature to the headers of every outgoing email. This signature confirms two critical things: that the email truly originated from your domain and that its contents haven't been messed with along the way.
Think of it as putting a custom wax seal on an envelope. If the seal is intact, the recipient trusts its origin. If it’s broken, they know something’s wrong. Getting DKIM right is a massive step toward building trust, especially with providers like Gmail who place a lot of weight on it.
Building a good reputation is a slow process. Some providers will even limit how many emails you can send per day from a new IP, gradually increasing the limit as you prove to be a responsible sender. Patience is a key part of hosting a mail server successfully.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
DMARC is the enforcer that ties SPF and DKIM together. Once you have those two in place, a DMARC record tells receiving mail servers what to do if an email fails either check. You can instruct them to quarantine the message (move it to spam) or reject it entirely.
Even better, DMARC gives you invaluable feedback. It tells servers to send you reports detailing which emails are passing or failing authentication. These reports are your eyes and ears, helping you spot configuration issues or catch fraudsters trying to spoof your domain. A solid DMARC policy gives you visibility and control.
Don't Forget Reverse DNS
Beyond the big three, one more DNS record is an absolute must-have: the Reverse DNS (PTR) record. A normal DNS 'A' record points a domain name to an IP address. A PTR record does the exact opposite—it maps an IP address back to a domain name.
Many corporate and government mail servers have a strict policy: if they receive an email from an IP that doesn't have a matching PTR record, they'll reject it on the spot. It's a simple yet surprisingly effective anti-spam measure. You'll typically need to contact your server provider to get this set up, but it's completely non-negotiable.
For a deeper dive into these authentication methods, you might be interested in our real-world email setup guide that works, which provides detailed insights into making these systems work.
Finally, keep a close eye on your server's IP reputation. Use tools like MXToolbox to check regularly if your IP has shown up on any blacklists. Getting blacklisted can happen for all sorts of reasons, and you'll need to act fast to resolve the underlying issue and request removal to keep your emails flowing.
Hardening Your Server Against Email Threats

Alright, your server is officially online and handling email. Now comes the real work: email security. Running a mail server isn't something you can "set and forget." It’s an ongoing commitment to protecting your system and, more importantly, the email privacy of everyone who uses it.
Hardening your server means building layers of defense to create a private, resilient email fortress.
The process starts with tackling the internet's biggest nuisance—spam and malicious attachments. The amount of email flying around is mind-boggling. Back in 2020, daily email volume blew past 300 billion messages. Forecasts show it will likely hit 376 billion per day by 2025. That explosion in traffic makes robust filtering non-negotiable for anyone serious about hosting their own mail. You can get a better sense of the scale of modern email traffic and see why these defenses are so critical.
Building Your First Line of Defense Against Spam
Your first move should be installing a powerful spam filter. For self-hosted setups, SpamAssassin is the industry standard for a reason. It’s an incredibly smart, rule-based system that inspects every single email for hundreds of spammy red flags. It checks everything from headers and body content to sender reputation, assigning a score to each message. You just set a threshold—if a message scores too high, it gets flagged and can be automatically quarantined or rejected outright.
But spam is only half the battle. An antivirus scanner is just as vital. ClamAV is a fantastic open-source option designed to sniff out trojans, viruses, and other malware hiding in email attachments. Integrating ClamAV with your mail server ensures attachments get scanned before they ever land in a user's inbox, shutting down a huge vector for security breaches.
Encrypting Communications with SSL and TLS
Sending unencrypted email is like mailing a postcard. Anyone who gets their hands on it can read it. For genuine email privacy, you have to enforce encrypted connections at every single step of an email's journey. This is where SSL/TLS certificates come in—the very same tech that powers HTTPS on secure websites.
Getting a certificate used to be a pain, but now it’s free and fully automated thanks to Let's Encrypt. You install a small client on your server, and it handles getting, installing, and even renewing your SSL/TLS certificates for you. Once you have them, you'll configure both Postfix and Dovecot to use them. This does two critical things:
- Encrypting Transit (SMTP): It secures the connection when your server talks to other mail servers, protecting emails as they zip across the internet.
- Encrypting Access (IMAP/POP3): It encrypts the connection between your users' email clients (like Outlook or Apple Mail) and your server, protecting their passwords and email content.
Enforcing TLS encryption isn't just a "nice-to-have" feature; it's a fundamental requirement for modern email privacy. Without it, you're leaving your users' private communications wide open to snoopers.
Securing User Access and Server Ports
Beyond encryption, you have to make sure only authorized users can send email from your server. This is done with the Simple Authentication and Security Layer (SASL). It works with your mail software to demand a valid username and password before anyone can send an outgoing message. This is what stops spammers from hijacking your server to blast out junk, which would absolutely tank your IP reputation overnight.
Finally, you need a basic firewall. It’s an essential layer of security. The best approach is to block all incoming connections by default and then poke very specific holes for only the ports your mail server needs. This "deny by default" strategy dramatically shrinks your server's attack surface.
Essential Mail Server Ports to Allow:
- Port 25 (SMTP): Used for server-to-server email delivery.
- Port 587 (Submission): The one your authenticated users will use to send outgoing mail.
- Port 993 (IMAPS): For secure IMAP access to inboxes.
- Port 995 (POP3S): For secure POP3 access, if you decide to support it.
This mix of filtering, encryption, and access control is the heart of a well-hardened mail server. But the security landscape is always shifting. For a deeper dive into protecting your server from new and evolving dangers, our complete defense guide to email security threats will help you stay ahead of the game.
When to Choose a Privacy-Focused Hosted Service
Let's be honest. After everything we've walked through, it's pretty clear that running your own mail server is a serious commitment. The rewards are huge, but so is the workload. The constant need to stay on top of email security, uptime, and deliverability is basically a full-time job. And for many people, that's just not practical.
This is exactly where privacy-focused hosted email platforms come into play. They offer a fantastic middle ground, giving you the data control and email privacy you're after without the monumental headache of managing every single piece of the infrastructure yourself.
The Best of Both Worlds
Choosing a dedicated privacy service isn't like signing up for one of the big, free email providers. Those services often treat your personal data as a product to be sold to advertisers. Privacy-first hosted email platforms operate on a completely different business model: your privacy is their product.
This simple shift in philosophy brings some massive benefits to the table:
- Expert Security: You're not just one person trying to keep up. You get an entire team of professionals whose only job is to secure servers, watch for threats, and patch vulnerabilities before they become a problem.
- Guaranteed Uptime: These services run on redundant, professional-grade infrastructure. No more worrying about a power outage at home taking your email offline. It’s just always on.
- Solved Deliverability: Forget the nightmare of getting your IP address off a blocklist. They handle IP reputation, manage all the authentication protocols, and maintain relationships with other providers to make sure your emails actually land in the inbox.
You essentially get to hand off all the frustrating, time-sucking maintenance work while keeping the very things—email privacy and control—that made you consider self-hosting in the first place.
"Many people will tell you not to [self-host], and it definitely gets harder. While still possible, you will have to have a lot of patience and time on your hands. If I had to choose again, I am not sure if I would go that path again." – Timo Reymann, experienced self-hoster.
What Truly Sets Them Apart
The real difference comes down to philosophy and how that translates into practice. A privacy-focused hosted email platform is built from the ground up to serve you, not advertisers.
- Zero Data Mining: Their business model is built on subscriptions, not ads. This means they have absolutely no financial reason to scan your emails for keywords or build an advertising profile on you. Your inbox is yours, period.
- Commitment to Encryption: Strong TLS and end-to-end encryption aren't just buzzwords or optional extras; they're baked into the core of the service. They ensure your communications are locked down, both on the wire and on their servers.
- Transparent Business Practices: You know exactly where your data is stored and how it's being protected. Many of these services, for instance, run on their own hardware to avoid relying on third-party cloud giants and can truly guarantee data sovereignty.
This gives you a clear choice. Is your goal of email privacy best served by building it all from scratch, or by partnering with a dedicated expert who shares your values? For a lot of people and businesses, the latter is the most realistic and sustainable way to achieve digital independence without having to become a full-time sysadmin.
If you're looking for the control of a self-hosted solution without the management headaches, Typewire provides a secure, private email hosting platform built from the ground up to protect your communications. We offer zero tracking, no data mining, and a commitment to your privacy on our privately owned infrastructure. Explore our features with a 7-day free trial and take back control of your inbox.
Hosting a Mail Server for Privacy and Control
Posted: 2025-11-22
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31