What is symmetric and asymmetric key encryption in Email?
At the heart of the matter, the difference between symmetric and asymmetric key encryption is refreshingly straightforward. Symmetric encryption uses a single, shared key for both encrypting and decrypting data. In contrast, asymmetric encryption uses a pair of keys: a public one to lock the data and a private one to unlock it. This core distinction shapes how we protect our communications, especially on hosted email platforms where both security and efficiency are paramount.
Understanding Core Encryption Concepts for Email
Every secure email depends on encryption to shield its contents from prying eyes. This protection is built on two foundational methods—symmetric and asymmetric encryption—and each plays a unique role in keeping your messages private.
You can think of symmetric encryption like a physical key to a safe. To share what's inside, you have to give an identical copy of that key to the other person. It's fast and simple, but you have to find a secure way to get that key to them in the first place.
Asymmetric encryption, also known as public-key cryptography, works more like a personal mailbox. Anyone can drop a letter in through the mail slot using your publicly available address (the public key), but only you have the special key (the private key) to open the box and read the messages. This clever setup solves the challenge of sharing a key without it getting intercepted, which is fundamental to modern email security.
The Role of Keys in Email Security
Getting a handle on these two approaches is the first step to truly understanding modern email privacy. The choice isn't always one or the other; in fact, the best email security systems use them together, creating a hybrid model that balances speed, security, and convenience.
- Symmetric Encryption: Its biggest advantage is speed. The mathematical operations are less complex, making it incredibly efficient for encrypting large volumes of data—think of your entire email archive stored on a hosted email platform's server.
- Asymmetric Encryption: While it's a bit slower, its real power lies in secure key exchange. It lets two people who've never met establish a secure line of communication for their emails without worrying about their shared key being snooped on.
This practical difference explains why symmetric encryption is such a workhorse in cloud security and hosted services. It's actually projected to command a 55% market share in the global cloud data encryption market by 2025. You can dig into these market trends and forecasts on futuremarketinsights.com.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Number of Keys | One shared secret key | A pair of keys (public and private) |
| Primary Strength | Speed and efficiency | Secure key exchange and verification |
| Common Use Case | Encrypting large data volumes (e.g., email archives) | Sharing secret keys and creating digital signatures |
Of course, none of this works if the keys themselves aren't handled properly. Learning about secrets management best practices is a great next step, as those principles are critical for protecting the cryptographic keys we've discussed. These concepts are also the building blocks for the ultimate standard in digital privacy, which you can learn more about in our guide on what end-to-end encryption is and how it works.
A Detailed Comparison of Encryption Methods
Once you get past the basic definitions, the real trick to understanding symmetric and asymmetric key encryption is seeing how they stack up in the real world, especially for things like hosted email. This isn't about one being "better" than the other; it's about picking the right tool for the job. Key differences in speed, security, and how you handle the keys determine where each one shines.
Symmetric encryption, for instance, has one huge advantage: it's incredibly fast. The math behind it is much simpler, so it can chew through massive amounts of data in a fraction of the time its asymmetric cousin would take. This raw speed makes it the go-to choice for encrypting something like an entire email inbox sitting on a server, where you can't afford any performance lag.
On the flip side, asymmetric encryption's genius lies in its ability to create a secure line of communication between two people who've never met or shared a secret before. It neatly sidesteps the problem of how to pass a secret key across an open, untrusted network like the internet. That capability is absolutely essential for kicking off secure email connections and proving you are who you say you are.
Performance and Speed Tradeoffs
When it comes to email, performance is a direct line to user experience. If encryption makes your email client feel sluggish, you've got a problem. This is where symmetric algorithms like AES (Advanced Encryption Standard) are the undisputed champions. They can encrypt and decrypt data hundreds, sometimes even thousands, of times faster than asymmetric algorithms like RSA.
The core tradeoff is simple yet profound: Symmetric encryption offers high-speed data protection for bulk information, while asymmetric encryption provides a slower but highly secure method for exchanging the keys needed to unlock that information.
This massive speed difference is precisely why nearly all modern email security systems use a hybrid approach. Asymmetric encryption handles the initial "handshake" to securely agree on a temporary symmetric key. Once that's done, the much faster symmetric key takes over to encrypt the actual email content.
The infographic below really drives home the fundamental difference in how their keys are structured.
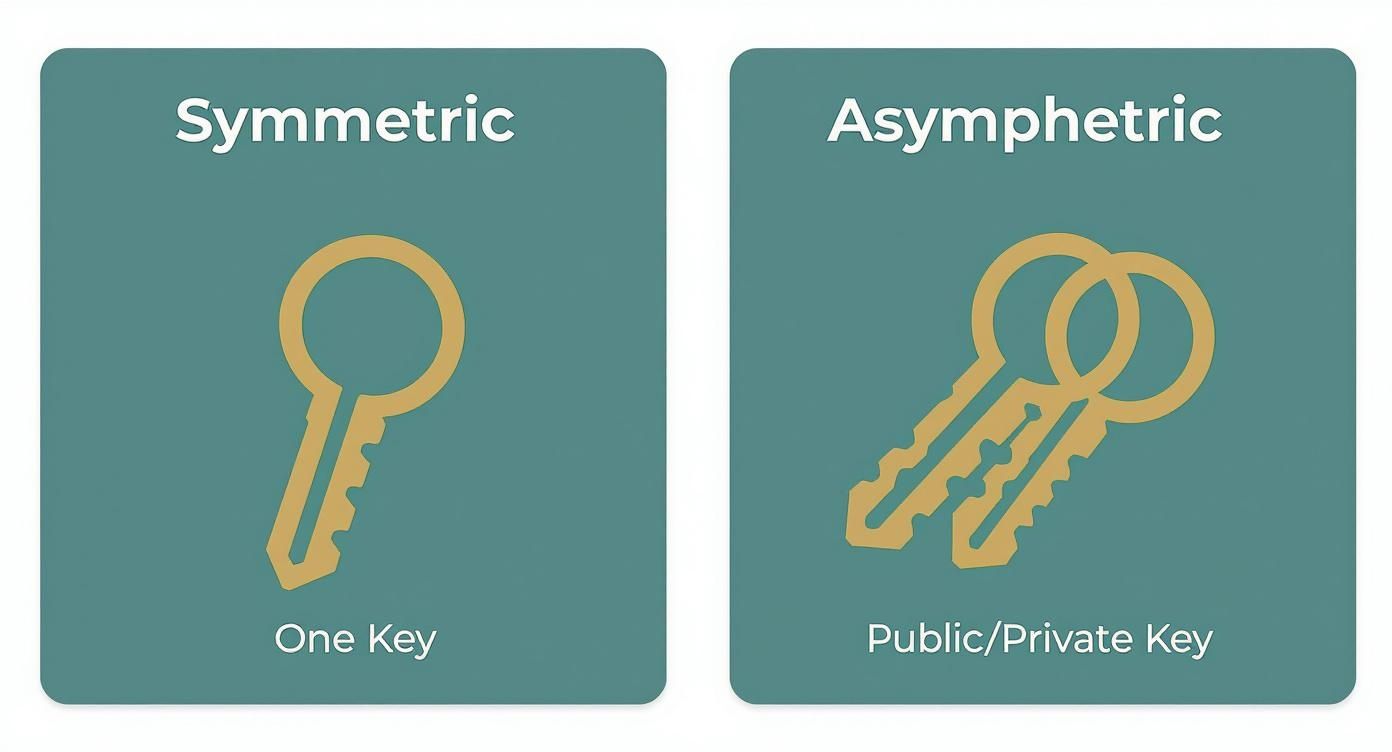
As you can see, the architecture is completely different. Symmetric encryption hinges on one shared secret, while asymmetric encryption splits the locking and unlocking functions between a public and a private key.
Key Management and Security Implications
Managing cryptographic keys is, without a doubt, one of the toughest parts of email security. With symmetric encryption, the biggest headache is getting that single, shared key to the right people without it being intercepted. If an attacker grabs that key, every piece of data it protects is instantly compromised. As more people join an email thread, this becomes a logistical nightmare.
Asymmetric encryption solves this distribution problem beautifully. You can share your public key with anyone who needs to send you a secure email. Since it can only be used to encrypt data meant for you, there's no risk. Only your private key, which you guard carefully, can decrypt those messages. This model makes secure communication possible on a global scale, which is non-negotiable for modern email privacy.
Symmetric vs Asymmetric Encryption Key Differences
To make these distinctions even clearer, here's a simple table that breaks down the key differences between the two methods. It’s a handy cheat sheet for understanding why one is used over the other in different email security scenarios.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Structure | A single, shared key for encryption and decryption | A pair of keys: one public (to encrypt), one private (to decrypt) |
| Speed | Extremely fast, with low computational overhead. | Much slower, computationally intensive. |
| Key Management | Distributing the shared key securely is a major challenge. | Simple distribution—the public key can be shared openly. |
| Primary Use in Email | Encrypting the actual email content and attachments. | Securing the initial connection and exchanging session keys. |
| Best For | Encrypting large volumes of data (data at rest). | Digital signatures and secure key exchange. |
Ultimately, this table reinforces the idea that symmetric and asymmetric encryption aren't competitors. They are partners, each playing a critical role in building a comprehensive email security system.
How Hybrid Encryption Secures Modern Email
When it comes to modern email security, you don't have to pick a side between symmetric and asymmetric encryption. The reality is, the best systems use both, combining their strengths into a powerful hybrid model. Protocols you've probably heard of, like PGP (Pretty Good Privacy) and TLS (Transport Layer Security), are built on this very idea, delivering both rock-solid security and speed.
This "best-of-both-worlds" approach is what makes privacy on hosted email platforms actually work. Asymmetric encryption is great for establishing a secure connection, but it's slow. Symmetric encryption is lightning-fast, making it perfect for encrypting the actual message. They truly complement each other. For a closer look at where these methods shine, check out these top encryption use cases on encryptionconsulting.com.
The Hybrid Handshake in Action
So, what does this look like when you send a secure email? It's a clever process that neatly sidesteps the weaknesses of each encryption type. Let's say you're sending a confidential file to a coworker.
- Key Exchange (Asymmetric): First, your email client generates a brand-new symmetric key just for this one message—this is often called a "session key." It then uses your coworker's public key to encrypt that session key. Since only their private key can unlock it, this initial exchange is safe, even if someone is snooping on the network.
- Message Encryption (Symmetric): With the session key securely delivered, your email client gets to work. It uses this fast and efficient symmetric key to encrypt the entire email—the text, the attachments, everything. This is where the speed comes in; trying to do this with asymmetric encryption would be painfully slow, especially for large files.
- Decryption: When your coworker receives the message, their email client uses their private key to decrypt the small, encrypted package containing the session key. Once the session key is revealed, it's used to quickly decrypt the actual email, turning it back into plain, readable text.
This whole sequence ensures the slow, processor-intensive asymmetric encryption is only used for one tiny, critical task: protecting the session key. The much faster symmetric encryption does all the heavy lifting for the message itself.
This hybrid method has become the undisputed industry standard for a reason. It masterfully balances the high-security key exchange of asymmetric methods with the high-performance data protection of symmetric ciphers.

It’s this precise combination of symmetric and asymmetric key encryption that allows services like Typewire to provide strong email privacy without bogging down your inbox. If you want to put this kind of protection to work for yourself, our guide on how to encrypt an email to ensure total privacy is a great place to start. Understanding what happens under the hood gives you a real appreciation for the sophisticated security that keeps your daily communications safe.
How Encryption Protects Your Email in the Real World
It's one thing to understand the theory of symmetric and asymmetric key encryption, but it's another to see how it actively shields your data on a hosted email platform. All the major email providers use these principles to lock down your messages at two critical points: while your email is flying across the internet and while it's sitting on their servers.
Think of it as a two-part security strategy. When you hit "send," your email travels through a series of servers to reach its destination, and each hop is a potential weak point for interception. Then, once it's stored in your inbox, it becomes a static, valuable target for anyone trying to break in. This is why email hosts apply different encryption tactics for each threat.

Locking Down Data in Transit with TLS
When your email is on the move, it’s protected by encryption-in-transit. The standard for this is Transport Layer Security (TLS), a protocol that masterfully blends both encryption types into a hybrid model. As soon as your email client connects to your provider’s server, TLS kicks off a secure “handshake.”
During that initial handshake, asymmetric encryption comes into play to securely negotiate and exchange a temporary, single-use symmetric key. Once your client and the server have that shared secret key, the rest of the conversation—including the entire email and its attachments—is scrambled using that much faster symmetric key. It's a clever system that ensures even if someone snoops on the connection, all they'll see is gibberish.
This hybrid approach is the cornerstone of modern internet security. It combines the bulletproof key exchange of asymmetric encryption with the raw speed of symmetric encryption to protect everything from your banking sessions to your daily emails.
Securing Data at Rest on Servers
Once an email safely lands in the recipient's inbox, it’s stored on the provider's servers. At this point, encryption-at-rest takes over. The data isn't moving anymore, so the main goal shifts to protecting huge volumes of stored information as efficiently as possible. This is where symmetric encryption truly shines.
Providers use powerful symmetric algorithms like AES-256 to encrypt entire mailboxes. This method is incredibly fast and efficient, putting very little strain on the servers. The result? You can search and access your entire email history instantly, all while it remains securely encrypted. The provider, of course, has to manage the keys for this process, keeping them tucked away in highly secure storage systems. For companies using platforms like Microsoft Exchange Server, understanding how these encryption protocols are managed is a core part of their security posture.
End-to-End Encryption: The Ultimate Privacy Shield
While standard transit and at-rest encryption are fantastic, they share one potential vulnerability: the email provider holds the keys. In theory, they could access your messages. To close this gap, some platforms offer end-to-end encryption (E2EE). E2EE is built squarely on asymmetric principles to guarantee that only the sender and the intended recipient can ever read the message.
Here’s how it works: anyone who wants to send you a secure message uses your public key to encrypt it. The only thing that can unlock that message is your private key, which lives exclusively on your device. This means no one in the middle—not even the email provider—can decipher your conversations. Getting this level of privacy hinges on picking the right service, which is why our guide on the top hosted email platforms for business security is a great place to start your research.
Making the Right Email Security Choices
Navigating the world of symmetric and asymmetric key encryption isn't just an academic exercise. When it comes to your email security, making an informed choice boils down to what you really need. Are you an individual who values absolute privacy above all else, or a business manager responsible for protecting company data on a hosted email platform?
Your goals will dictate the right approach.
For individuals, the main driver is usually confidentiality. You want a guarantee that no one can read your messages—not even your email provider. This is exactly where end-to-end encrypted (E2EE) email services shine.
These platforms are built to handle the tricky parts of asymmetric key encryption behind the scenes. When you sign up, the service guides you through generating a public and private key pair. Your public key gets shared so people can send you encrypted messages, but your private key stays locked down on your device. Only you can decrypt what you receive. The best part? These tools make it easy, automating key management so you get top-tier email privacy without needing a degree in cryptography.
Evaluating Hosted Email Solutions for Business
Business managers, on the other hand, have a much broader set of concerns. Individual privacy still matters, but it’s part of a bigger picture that includes compliance, data governance, and protecting the entire organization. When you’re evaluating a hosted email provider, you have to dig deeper than the marketing claims and really understand their security architecture.
First, mandatory Transport Layer Security (TLS) is non-negotiable. This is your baseline, ensuring all emails are encrypted as they travel across the internet, shielding them from prying eyes in transit. But that's just the start. You also have to ask how the provider handles encryption-at-rest.
The best providers are transparent about their methods, typically using strong symmetric algorithms like AES-256 to encrypt all data stored on their servers. This protects your company's email archive from physical theft or unauthorized server access.
The intense focus on these security layers isn't happening in a vacuum; it’s a direct response to escalating cyber threats. This trend is reflected in the global data encryption market, which is projected to grow from USD 18.08 billion in 2024 to an estimated USD 36.02 billion by 2029. You can read more about these data encryption market projections on openpr.com.
In the end, choosing the right email solution means finding a provider whose technical capabilities match your security requirements. For individuals, that usually means finding a service that automates E2EE. For businesses, it means a thorough vetting of a provider’s commitment to comprehensive encryption—both in transit and at rest.
Frequently Asked Questions About Email Encryption
Diving into email security can feel a little overwhelming, and it's easy to get lost in the jargon. Let's clear up some of the most common questions about symmetric and asymmetric key encryption and what they mean for protecting your email.
Which Is Better for Email: Symmetric or Asymmetric?
The truth is, you can't really pick one over the other. The best way to think about them is as a team—each one plays a different, equally vital role in keeping your messages safe.
Symmetric encryption is the heavy lifter. It's incredibly fast because it uses the same key for both locking and unlocking your data. This makes it perfect for encrypting the actual body of your email and any large attachments without bogging down performance.
Asymmetric encryption, on the other hand, is the master of secrets. While it's a bit slower, it brilliantly solves the problem of how to share a key with someone you've never met over the open internet. In the world of email, it's used to securely exchange the symmetric key—not to encrypt the entire message.
The most secure email systems don't make you choose. They combine both in a hybrid model: asymmetric encryption protects a one-time-use symmetric key, and that speedy symmetric key handles the encryption of the actual email content.
How Does My Email Provider Actually Protect My Data?
Your email provider essentially builds a digital fortress around your data using encryption at two key points: when it’s on the move and when it's sitting still.
- Encryption in Transit: As soon as you hit "send," your email is shielded by protocols like Transport Layer Security (TLS). TLS uses that hybrid approach we just mentioned, using asymmetric encryption to create a secure channel and then a temporary symmetric key to encrypt the data flowing through it. This prevents anyone from snooping on your email as it travels from your device to the server.
- Encryption at Rest: Once your email lands on the provider's servers, it’s protected by encryption at rest. This is where powerful symmetric algorithms like AES-256 come into play, scrambling the data on the hard drives so it’s completely unreadable to anyone who might gain unauthorized physical access.
Is Standard Email Encryption (TLS) Enough for Real Privacy?
TLS is absolutely essential for basic email security, but it doesn't guarantee complete privacy by itself. Think of it as creating a secure tunnel between mail servers. The problem is, your message is often decrypted and re-encrypted at each server along its route.
More importantly, your email provider holds the keys for encryption at rest. So, while your data is safe from outside attackers, the provider technically has the ability to access and read your messages. For most day-to-day emails, this level of security is acceptable, but it’s a major limitation if you need true, verifiable confidentiality.
What’s the Main Difference Between Transport and End-to-End Encryption?
It all comes down to one simple question: Who holds the keys?
Transport Layer Encryption (TLS) secures the path your email takes between servers. It’s like sending a letter in a locked armored truck. The truck itself is secure, but the postal service can still open it at the sorting facility. In this scenario, your email provider is the postal service.
End-to-End Encryption (E2EE), however, ensures that only you and your recipient can ever read the message. This is like sealing your letter in a box that can only be unlocked with a key that only the recipient has. The message stays encrypted for its entire journey, and not even your email provider can see what's inside. E2EE is the gold standard for email privacy, built on the principles of asymmetric encryption.
Ready to take control of your email privacy with a platform that puts security first? Typewire offers secure, private email hosting that leverages robust encryption standards to protect your communications without ads, tracking, or data mining. Start your free 7-day trial today!
What is symmetric and asymmetric key encryption in Email?
Posted: 2025-11-18
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23