Data Sovereignty Definition: Key Insights on Data Control
Understanding Data Sovereignty: Beyond the Basic Definition

To really get a handle on data sovereignty, it's helpful to think of it like physical property. Imagine you own a house. The laws that apply to your property—like building codes and taxes—are determined by the country, state, and city where it's located. Your data works in a very similar way; it's subject to the laws of the nation where it is physically stored.
This isn't just a theoretical concept. It's a practical reality that dictates how businesses operate across international borders. In simple terms, data sovereignty is the principle that information is subject to the laws and regulations of the country in which it is located. This means a nation has the final say on how data within its borders is collected, processed, and shared. A single customer email stored in the wrong country could lead to serious legal trouble and fines. For a deeper dive into the concept, the Wikipedia page on data sovereignty is a great resource.
Why This Matters for Your Business
Grasping this idea is as fundamental as understanding your tax obligations. Many large companies are currently overhauling their technology systems just to comply with these rules. This impacts everything from which cloud provider you can use to where your customer support team is allowed to access client files.
There are three essential ideas that work together here:
- Data Residency: This is the specific geographic location where a company decides its data should live. Think of it as choosing the country where you want to build your digital "house."
- Data Localization: This is a much stricter rule. It mandates that data created within a country's borders must never leave those borders.
- Security & Control: This ensures that only authorized people, operating under the correct jurisdictional laws, can access the data.
Getting these elements wrong can open your business up to significant risks. These include hefty non-compliance fines, a breakdown in customer trust, and even having your operations halted if a foreign government suddenly restricts access to your data.
The Legal Landscape: Why Governments Are Drawing Digital Borders
Imagine a country building invisible walls around its digital information. That’s essentially what’s happening globally, and it’s about more than just privacy. We're seeing a tug-of-war between nations trying to protect their digital economies and multinational companies that rely on the free flow of data to operate. These aren't just friendly suggestions; they're legally binding rules with serious financial teeth for any organization that fails to comply.
The Rise of Data-Driven Lawmaking
From Europe’s General Data Protection Regulation (GDPR) to China’s strict data localization laws, the message is clear. Governments are taking control over data for national security, economic protection, and citizen rights. This push for a solid data sovereignty definition within legal systems is a global trend. In fact, as of 2024, an estimated 71% of countries have put their own data protection and privacy legislation in place. You can learn more about how these policies impact business strategy by exploring this guide on data sovereignty.
This chart shows how the importance of data sovereignty is growing from legislative, business, and technology standpoints.
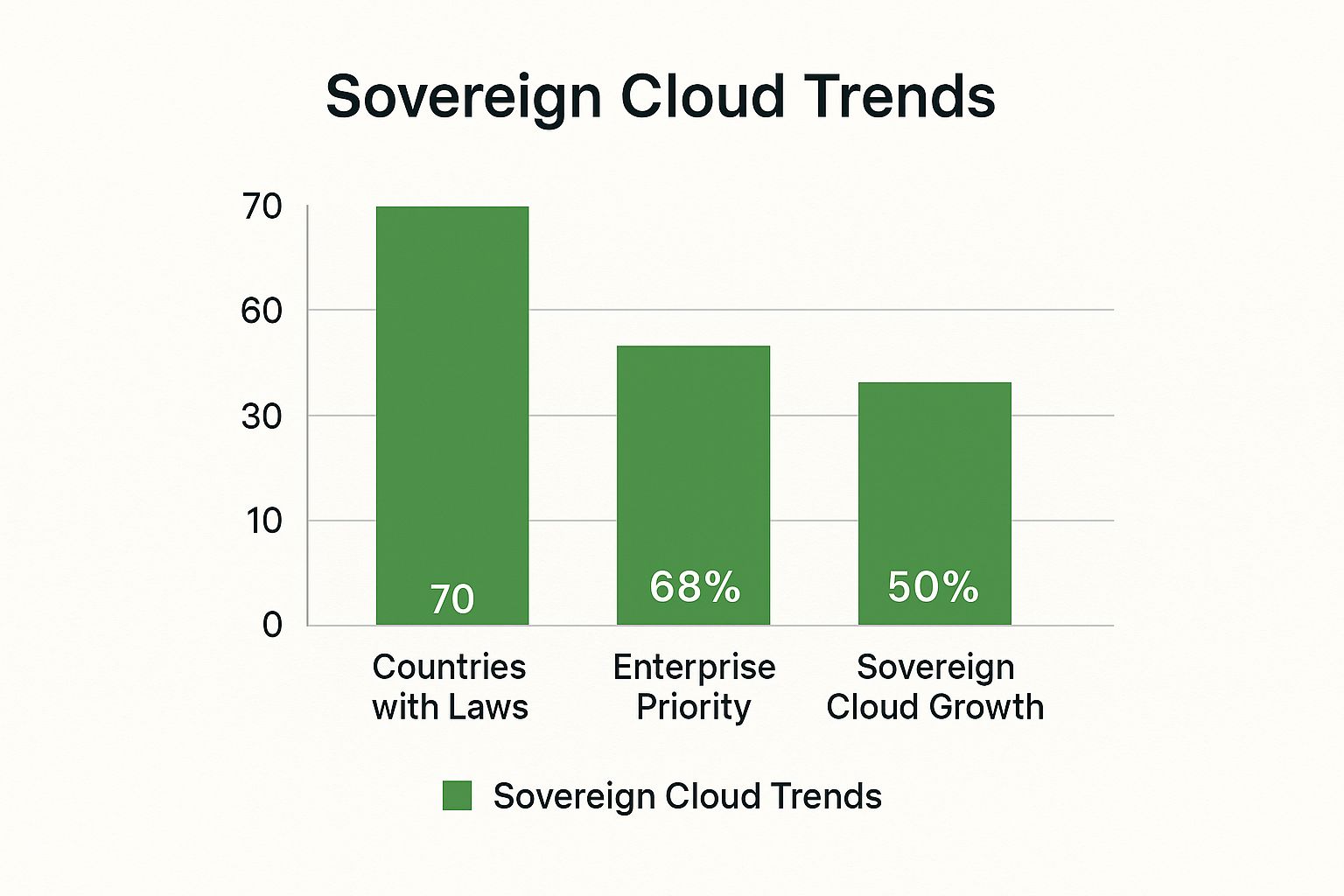
As you can see, when governments pass more laws, data sovereignty becomes a bigger deal for company leaders and drives the need for compliant cloud solutions.
To help make sense of this complex global puzzle, here’s a look at some of the major data protection laws around the world.
Major Data Sovereignty Laws by Region
A comprehensive comparison of key data protection regulations across different countries and regions
| Region/Country | Law Name | Year Enacted | Key Requirements | Maximum Penalties |
|---|---|---|---|---|
| European Union | General Data Protection Regulation (GDPR) | 2018 | Strict consent rules, data breach notifications, right to be forgotten, data processing agreements. | Up to 4% of annual global turnover or €20 million, whichever is higher. |
| United States | California Consumer Privacy Act (CCPA) | 2020 | Grants consumers rights to know, delete, and opt-out of the sale of their personal information. | $2,500 per unintentional violation; $7,500 per intentional violation. |
| China | Cybersecurity Law (CSL) & Personal Information Protection Law (PIPL) | 2017 & 2021 | Requires personal information and important business data to be stored locally. Cross-border transfers are heavily regulated. | Up to 5% of annual turnover or ¥50 million, plus business suspension. |
| Brazil | Lei Geral de Proteção de Dados (LGPD) | 2020 | Modeled after GDPR, it establishes rights for data subjects and rules for data processing and transfers. | Up to 2% of the company's revenue in Brazil, limited to R$50 million per violation. |
| India | Digital Personal Data Protection Act (DPDPA) | 2023 | Focuses on consent-based data processing, defines data fiduciaries' obligations, and sets up a Data Protection Board. | Up to ₹250 crore (approx. $30 million) per incident. |
| Canada | Personal Information Protection and Electronic Documents Act (PIPEDA) | 2000 | Governs how private-sector organizations collect, use, and disclose personal information in commercial activities. | Fines up to $100,000 per violation for certain offenses. |
This table shows that while the goals are similar—protecting data—the rules and penalties vary greatly from one place to another. This makes a one-size-fits-all approach to data management nearly impossible for global businesses.
High-Stakes Enforcement and Compliance
Ignoring these rules comes with a massive price tag. Major tech companies have been hit with penalties in the hundreds of millions for data sovereignty violations. For example, a major social media platform was fined $1.3 billion for improperly moving user data from the EU to the US, which was a clear violation of GDPR.
These actions send a powerful signal: regulators are done with warnings and are now taking firm action. This pressure is forcing companies to rethink their entire data infrastructure. Forward-thinking organizations are turning these compliance hurdles into a competitive edge. They are proactively designing their operations around data sovereignty, staying ahead of a trend that shows no sign of stopping.
Real Business Impact: How Data Rules Are Reshaping Operations
The idea of data sovereignty isn't just for lawyers and legal briefs; it's actively changing how companies function every single day. The basic data sovereignty definition—that data must follow the laws of the country where it is physically stored—is compelling businesses to make major, and often expensive, adjustments to their infrastructure and processes. This isn't a distant concern; it's a current reality showing up in quarterly budgets and long-term strategic plans.
For many businesses, the first step is a complete rethinking of where their data is kept. Some have had to move away from centralized, cost-efficient cloud services to more expensive, localized hosting solutions. This change can easily cost millions, as seen with major tech companies building new data centers in specific countries just to comply with local laws. As a clear example, Microsoft announced it would more than double its data center capacity in Europe between 2023 and 2027, a direct reaction to demand from customers and governments for data to stay within European borders.
Industry-Specific Adjustments
The consequences of these rules differ across industries, but the impact is felt everywhere. Think about these real-world scenarios:
- Healthcare: A German medical clinic is not allowed to store patient files on a server based in the United States because it would violate GDPR. To stay compliant, it must go through the complex and costly process of moving all sensitive health data to servers located within the EU.
- Finance: A global investment bank needs to redesign its IT systems to guarantee that data belonging to its European clients never crosses outside of the EU. This could mean creating entirely separate, walled-off IT environments for its offices in London, Paris, and Frankfurt.
- E-commerce: A Canadian online store with a growing base of European shoppers faces a choice: invest heavily in a European data center or face the risk of massive fines for non-compliance.
These examples show that following data sovereignty rules is no longer a choice but a necessity. It demands smart investment and a new approach to operations. Businesses that get ahead of these changes can build greater trust with their customers and gain an edge over competitors who are slower to adapt.
The Technology That Makes Data Sovereignty Possible

Achieving data sovereignty isn't a matter of policy alone; it's built on a foundation of specific technological choices. Behind every compliant organization is an infrastructure strategy designed to create and enforce digital borders. This technology is what translates the legal data sovereignty definition into real, practical controls over where your information lives and who can touch it. At its heart, this means using architectures that lock data within certain geographic areas and applying strong encryption that meets strict regulatory rules.
Cloud providers like AWS and Microsoft are key players in this space, developing services with sovereignty in mind. For example, AWS is launching a European Sovereign Cloud by the end of 2025. This will be a separate cloud environment operated entirely by EU residents within the EU, directly addressing demands for data residency and control in sensitive industries.
Key Technological Pillars
Several core technologies work in concert to make data sovereignty a reality without complicating business operations.
- Data Residency Architecture: This is the bedrock. It involves setting up cloud services to store data exclusively in data centers located within a specific country or region. For instance, a company can use an AWS region in Frankfurt to guarantee that German customer data never leaves Germany.
- Confidential Computing: Think of this as a digital vault for your data while it's in use. This advanced technology creates secure, encrypted spaces where data remains protected even during processing. Not even the cloud provider can peer inside, giving you an exceptionally high degree of control.
- Zero-Trust Architectures: This security model follows a simple but powerful rule: "never trust, always verify." It demands strict identity confirmation for every person and device attempting to access information, no matter where they are. This is essential for enforcing access rules based on jurisdiction.
These technical building blocks, when paired with automated compliance tools, give organizations the power to manage data sovereignty effectively.
Overcoming Common Implementation Challenges
While the logic behind a clear data sovereignty definition is sound, translating theory into practice is where the real work begins. Putting a solid data sovereignty strategy in place is rarely a simple task. It can be a complex, costly, and disruptive process for established workflows. IT leaders consistently report a few common pitfalls that can stop these projects before they gain any momentum.
One of the biggest obstacles is getting new, compliant systems to work with older, legacy technology. Most older software and databases were built without jurisdictional boundaries in mind. This creates significant compatibility headaches and unexpected problems with data synchronization across borders, often draining unplanned time and resources.
Phased Strategies and Budgeting
A phased implementation is often the most sensible approach to avoid overwhelming your teams and your budget. Instead of a complete, simultaneous overhaul, successful organizations prioritize their data and address compliance in manageable stages. This method keeps operational disruption to a minimum while ensuring consistent progress toward your goals.
- Start with High-Risk Data: Begin by identifying and securing your most sensitive information, such as personal customer details or valuable intellectual property. This tackles the biggest compliance risks first.
- Leverage Sovereign Cloud Solutions: Look into services like the upcoming AWS European Sovereign Cloud, which is designed from the ground up to meet strict data residency and control requirements.
- Balance Global and Local Needs: Aim for a practical middle ground that allows for efficient global operations while adhering to strict local regulations. This requires choosing technology that supports, rather than complicates, your compliance efforts.
Effective planning for timelines and budgets requires an honest assessment of the work involved. Teams that have gone through these transitions often find that their initial estimates were too optimistic. Building in a buffer for unforeseen integration challenges is crucial for keeping the project on schedule and within its financial plan. With careful planning, the path to full compliance becomes much more manageable.
Data Sovereignty Implementation Challenges and Solutions
To help you anticipate these issues, here is a look at common challenges and potential solutions for businesses of different sizes.
| Challenge | Impact Level | Solution Approach | Estimated Cost | Implementation Time |
|---|---|---|---|---|
| Integrating with Legacy Systems | High | Use a phased migration. Employ middleware or APIs to bridge the gap between old and new systems. Prioritize migrating high-risk data first. | $50,000 – $250,000+ | 12 – 24 months |
| Lack of In-House Expertise | Medium | Partner with a specialized consultant or managed service provider. Invest in training and certification for key IT staff. | $20,000 – $100,000 | 3 – 9 months |
| High Implementation Costs | High | Adopt a cloud-native strategy to reduce hardware expenses. Start with a smaller, focused pilot project to demonstrate ROI before a full-scale rollout. | $15,000 – $75,000 (initial) | 4 – 8 months |
| Complex Legal Requirements | High | Engage legal counsel specializing in data privacy for the target jurisdictions. Use compliance-as-a-service platforms to automate monitoring. | $10,000 – $50,000 (legal) | Ongoing |
| Operational Disruption | Medium | Implement changes during off-peak hours. Communicate clearly with all stakeholders about the timeline and potential impact on their work. | Varies (Internal cost) | 6 – 18 months |
This table shows that while challenges like legacy system integration have a high impact, structured and phased solutions can make them manageable. The key takeaway is that proactive planning, strategic partnerships, and a realistic budget are essential for a successful data sovereignty implementation.
Email Hosting: Your Hidden Data Sovereignty Risk
Most companies are careful about where they store customer databases and important files, but they often overlook one of the biggest data sovereignty risks: their email. Every single message your team sends or receives is a piece of data. It can contain sensitive information, contracts, and private internal discussions. All this communication is governed by the laws of the country where the email servers are physically located—a detail a surprising number of businesses don't even know. This oversight can quickly turn your email provider into a major compliance blind spot.
Your choice of email provider directly affects your ability to meet legal standards. A vague data sovereignty definition in a service agreement is not enough. You must know the physical jurisdiction where your data lives.
Why Your Mailbox Location Matters
Picture a healthcare organization that uses an email service hosted in a different country. Without clear controls, private patient information within those emails could be subject to that nation’s data access laws. This could easily violate local privacy regulations like HIPAA in the U.S. or PIPEDA in Canada. In the same way, financial data shared in emails could be exposed to foreign government surveillance if it's stored on servers outside your legal territory.
This isn't just a theoretical problem. Real organizations have faced serious regulatory trouble because of email hosting choices they barely thought about. To protect your business, you need to look at email providers through a data sovereignty lens. This means asking some direct questions:
- Where are your servers physically located?
- What legal jurisdiction governs my data?
- Do you use third-party cloud providers for hosting?
Solutions like Typewire are built to solve these problems directly. They operate using privately owned data centers in a single, transparent location—Vancouver, Canada. This approach ensures your email data stays under Canadian privacy laws, giving you clear control and helping you avoid the hidden risks of global hosting. Making an informed choice about your email infrastructure is a fundamental part of a solid data sovereignty strategy.
Your Strategic Action Plan for Data Sovereignty Success
Are you ready to manage data sovereignty with confidence? Shifting from understanding the data sovereignty definition to building a practical strategy calls for a clear, organized roadmap. A successful plan doesn't have to be complicated or expensive if you break it into smaller, more direct steps. This action plan offers a framework to guide you through compliance without disrupting your daily work.
Conduct a Thorough Data Audit
The first and most important step is to figure out exactly what data you have and where it’s stored. After all, you can't protect what you don't know you have.
- Map Your Data: Start by identifying every type of data your organization handles, from customer PII and financial records to intellectual property.
- Locate Your Data: Pinpoint the physical locations where your data lives. This includes cloud servers, on-site hardware, and any third-party services you use. A recent study revealed that 58% of organizations find this particular step challenging, which shows both its difficulty and its importance.
- Classify by Risk: Sort your data based on its sensitivity and the specific laws tied to its location. Focus on high-risk information for immediate attention.
Choose the Right Partners and Technology
With a clear map of your data, the next step is to pick the right tools and partners to enforce your data sovereignty rules. This is about working with vendors who value transparency and give you control.
- Evaluate Your Vendors: Take a close look at the data sovereignty policies of your current cloud and software providers. Don't hesitate to ask them directly where your data is stored and who can access it.
- Establish Compliance Monitoring: Put tools in place that give you a continuous view of your data's location and who is accessing it. This proactive monitoring helps you stay compliant as regulations change and your business grows.
By taking this organized approach—auditing your data, classifying it, and choosing your partners carefully—your organization can develop a strong and compliant data strategy.
For any business where email is a central tool for communication, securing that correspondence is a vital part of a sovereignty plan. See how Typewire delivers secure, private email hosting on Canadian-based servers, which gives you total control over your data’s physical location and the laws that govern it. Learn more about Typewire's commitment to your data privacy.
Data Sovereignty Definition: Key Insights on Data Control
Posted: 2025-06-19
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16