A Guide to Secure Email for Business

A secure email solution for your business is all about wrapping your sensitive communications in a layer of strong encryption and other advanced security measures. It’s a world away from standard email, which is often wide open and vulnerable. A proper secure platform keeps your data private, shutting the door on unauthorized access and cyber threats, making email privacy a core business function.
Why Your Standard Email Is a Security Risk
Ever thought of a standard email as a postcard? It's a surprisingly accurate analogy. As it zips across the internet, anyone with the right tools can potentially read its contents. This built-in lack of privacy is the core weakness of most email systems, making them a terrible choice for sending confidential business information.
Every single time you hit "send" on an unencrypted email, you're putting sensitive data at risk. We're talking about everything from financial records and client lists to your company's secret sauce—its strategic plans. This exposure isn't just a problem while the email is in transit; it's also a risk when the data is sitting on a server, a state known as being "at rest."
The Unseen Dangers in Your Inbox
This constant exposure is a goldmine for cybercriminals. Phishing is still the number one way they break into business email, accounting for a staggering 36% of all cybersecurity breaches. The scale is massive, with criminals blasting out an estimated 3.4 billion phishing emails every single day.
These attacks are frighteningly effective, too. A full 94% of malware infections get their start from a phishing attempt. If you want to dive deeper into these trends, the folks at Techmagic have some great insights.
This infographic breaks down the three main weak points in a standard email setup.
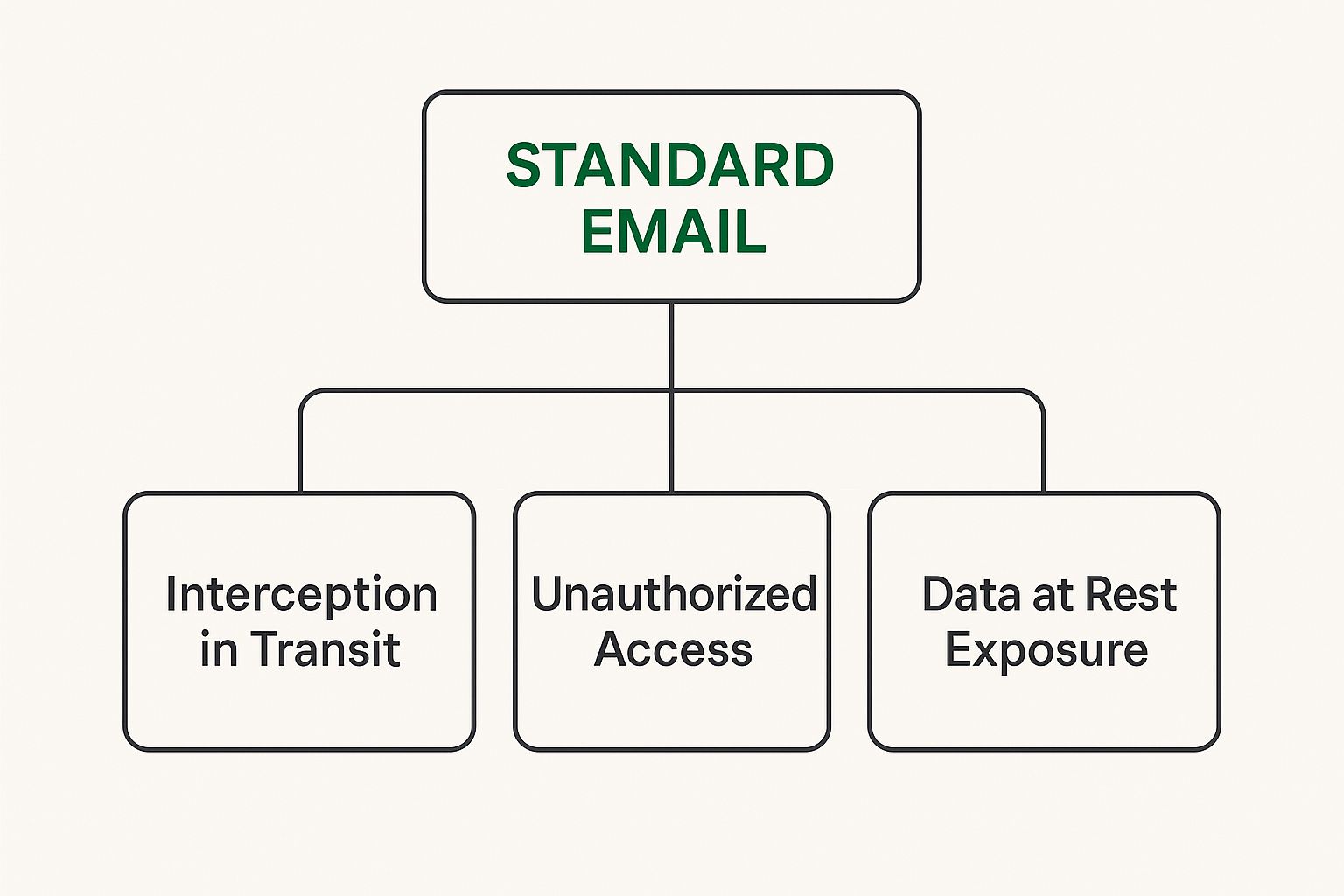
As you can see, data can be snatched right out of the air during transit, accessed on servers where it shouldn't be, or compromised while it's just sitting there. Each of these is a critical failure point that a secure email for business platform is built to eliminate.
Protecting your communications isn't just an IT problem anymore—it's a fundamental business responsibility. A single breach can lead to devastating financial losses, a tarnished reputation, and a complete breakdown of client trust.
Without a solid solution, you're essentially leaving your company's most valuable information out in the open, turning a simple communication tool into your biggest liability.
Understanding the Core of Secure Email
To really nail down your business's communication security, you need to think beyond just a strong password. A truly secure email for business isn't a single feature; it's a system built with multiple layers of defense. Each layer has a specific job, and they all work together to keep your sensitive data out of the wrong hands.
The absolute heart of this system is End-to-End Encryption (E2EE). Think of it like sending a valuable package in a special, unbreakable lockbox. You snap it shut with a unique key, and only the person you're sending it to has the one-and-only key that can open it. Along the way, no one—not the mail carrier, not a nosy intermediary, not even the email company itself—can see what’s inside.
From the second you click "send" until the moment your recipient opens it, your message is just a jumble of unreadable code to anyone else. This is the gold standard for email privacy, guaranteeing that the conversation remains confidential for its entire trip across the internet.
Beyond Encryption: Your Layered Defenses
While powerful encryption is the foundation, a robust hosted email platform doesn't stop there. Several other critical features work in concert to build a fortress around your inbox, defending you from the most common and damaging cyber threats out there. Think of these as the guards, moats, and reinforced walls that complete your email security setup.
Here are the non-negotiable components you should be looking for:
- Two-Factor Authentication (2FA): This is your second line of defense for logging in. It requires a second piece of proof—usually a code sent to your phone—to verify it’s really you. It’s like having a deadbolt and a key lock on your front door; even if someone steals your key (password), they still can't get in.
- Intelligent Anti-Phishing Filters: Today's phishing scams are incredibly sneaky, perfectly mimicking banks, colleagues, or services you trust. Modern filters are smart, using advanced analysis to spot the tell-tale signs of fraud, automatically catching and isolating these dangerous emails before they ever land in front of an employee.
- Advanced Malware Scanning: Malicious attachments are one of the most common ways that viruses and ransomware cripple businesses. A secure email service acts as a vigilant gatekeeper, scanning every single attachment for known threats and blocking dangerous files before anyone has a chance to click on them.
These features aren't just nice-to-haves; they are essential. Without them, even the best encryption won't matter if an attacker simply tricks an employee into handing over their keys to the kingdom.
A truly secure email solution is about creating a complete defensive system. It's not just about locking the message; it's also about guarding the gates, verifying identities, and neutralizing threats before they reach your team.
Essential Secure Email Features Explained
To help you cut through the noise, here’s a quick-reference guide to the most important security features and what they actually do for your business.
| Security Feature | Primary Function | Why Your Business Needs It |
|---|---|---|
| End-to-End Encryption (E2EE) | Scrambles email content so only the sender and intended recipient can read it. | Protects the confidentiality of sensitive data like contracts, financial records, and client information from being intercepted in transit. |
| Two-Factor Authentication (2FA) | Requires a second verification step (like a phone code) to log in. | Prevents unauthorized access to accounts even if an employee's password is stolen, which happens a lot more than you'd think. |
| Anti-Phishing Filters | Identifies and blocks fraudulent emails designed to steal credentials or data. | Protects your team from costly human error by stopping social engineering attacks before they can cause a breach. |
| Malware & Virus Scanning | Scans all incoming attachments for malicious software. | Prevents ransomware, spyware, and other viruses from infecting your network through email, a very common entry point. |
Having a solid grasp of these core technologies is the first step toward making a smart decision. When you start comparing different hosted email platforms, you’ll be able to see past the marketing jargon and focus on what really matters: whether a service has the fundamental protections your business needs to stay safe.
The Real Cost of Business Email Compromise

It’s easy to think of cybersecurity threats as abstract problems for the IT department. But when an email system isn't secure, the danger becomes very real, and very expensive. This is the world of Business Email Compromise (BEC), a type of attack that turns a simple email into a potential financial disaster.
These scams are particularly brutal for small and mid-sized companies, which often don't have a large security team standing guard.
A typical BEC attack is surprisingly simple. A scammer, convincingly disguised as the company's CEO, shoots a quick email to someone in the finance department. The message is always urgent: "I'm about to close a confidential acquisition and need you to wire funds to this account right away. This is time-sensitive and must be kept quiet."
The Modern BEC Attack
Here’s the scary part: these aren't the clumsy, typo-filled emails of the past. With AI in their toolkit, attackers can now perfectly clone a CEO’s writing style, reference real company projects, and create a sense of urgency that’s hard to ignore. The employee, trying to be responsive and do their job, processes the payment.
Before anyone catches on, the money has vanished. It's usually bounced through a web of international accounts, making it nearly impossible to trace, let alone get back. This isn’t a rare occurrence; it happens to businesses every single day. The damage goes far beyond the lost cash, snowballing into regulatory fines, lawsuits, and a shattered reputation.
The true cost of a BEC attack isn't just the money that disappears from your bank account. It's the trust you lose with customers, partners, and even your own team—and rebuilding that can take years.
The Staggering Financial Impact
BEC scams have exploded into one of the most damaging threats a business can face. The numbers are frankly alarming. Recent data reveals that about 12.9% of employees said their organization lost money directly to a BEC attack. That means nearly one out of every eight companies is getting hit where it hurts.
For businesses that rely on managed service providers, the stats are even worse, with a staggering 21.6% reporting financial losses from these very scams. You can dig deeper into these trends in the State of Email Security Report 2025.
This all highlights a fundamental truth: putting money into a secure email for business solution isn't just another operating cost. It’s an absolutely critical investment to protect your company from attacks that can bring your operations to a halt and ruin the brand you’ve worked so hard to build.
How to Choose the Right Hosted Email Platform
Picking the right secure email for business provider is a big deal. It's a decision that will have a direct ripple effect on your company's email privacy, email security, and day-to-day operations. With so many options on the market, it’s easy to get bogged down by flashy feature lists.
The key is to look past the marketing noise and focus on what really matters. This isn't just about getting a new inbox; it's about entrusting a partner with your most sensitive conversations.
Your first question should be a simple one: where is my data physically stored? The provider's home country, or jurisdiction, determines which government’s laws have authority over your information. A provider based in a country with strong, citizen-first privacy laws gives you a massive advantage over one located in a region known for widespread government surveillance.
Think of this legal framework as the foundation of your email security. Choosing a provider in a privacy-friendly location means your data is protected by law, not just by a company's promises.
Evaluating Security and Privacy Policies
Once you’ve settled on jurisdiction, it's time to get into the technical weeds and really scrutinize the provider's security and privacy commitments. The most important piece of this puzzle is encryption. You need to confirm they use strong, modern encryption standards not just for emails in transit but also for data sitting at rest on their servers.
Beyond the tech, a provider's privacy policy reveals its true business model. Hunt for clear, unambiguous language confirming they do not scan your emails for advertising and that they have a strict zero-tracking policy.
A provider that respects your privacy will treat your data like a sealed vault, not a resource to be monetized. Their commitment should be explicitly stated, leaving no room for ambiguity about how your information is handled.
The screenshot below from Wikipedia gives you a sense of the principles behind GDPR, a regulation that has set a global standard for data protection.
These principles—lawful, fair, and transparent data processing—are exactly what you should demand from any secure email provider.
Assessing Usability and Essential Features
Let's be realistic: the most secure platform in the world is useless if your team hates using it. A clunky, confusing interface will kill adoption faster than anything else. Before you sign any contracts, make sure you take advantage of free trials. See how the platform actually feels to use. Can your team get their work done without a massive learning curve?
While security is the priority, productivity features still matter. For example, some people rely on tools to speed up their workflow and would want to explore dictation features for Gmail if they were considering that ecosystem.
Finally, you need to make sure the platform gives you the administrative muscle to manage your organization. Here are the non-negotiables:
- Custom Domain Support: You absolutely need to use your own domain name (like
you@yourcompany.com) to look professional. - User Management Controls: How easy is it to add or remove users, set permissions, or manage team aliases? It should be simple.
- Compliance Certifications: If you're in a regulated industry like healthcare (HIPAA) or finance, you need a provider that can show proof of compliance.
- Integration Capabilities: Your email platform needs to play nicely with your other essential tools, like calendars and contact managers.
By thinking through these critical factors—from the laws that protect you to the features your team uses every day—you can confidently select a hosted email platform that truly has your back. For a head-to-head comparison, take a look at our guide on the top 7 best hosted email platforms for business security in 2025.
Implementing Email Security Best Practices

While a top-tier hosted email platform gives you a powerful technological shield, that’s only half the story. Your team is your first, and most important, line of defense. Building a culture where everyone is security-minded isn't just a bonus—it's a core strategy for creating a truly secure email for business environment.
Let's be realistic: even the most advanced software can't stop every threat if your team's actions open the door. The hard truth is that human error is the single biggest factor in most email security breaches. In fact, a recent poll of IT security pros found that roughly 95% of all data breaches involve some type of human mistake, from accidentally emailing sensitive files to the wrong person to simply mishandling information. You can dig deeper into these numbers in the State of Human Risk 2025 report.
Cultivating Everyday Security Habits
A strong defense is built on simple, powerful habits woven into your team's daily routine. We're not talking about complex technical configurations, but practical, everyday behaviors that massively cut down on risk. When these actions become second nature, your entire organization becomes a much tougher target.
Here are a few fundamental habits to get started with:
- Strong, Unique Passwords: Push for long passphrases that are easy for a person to remember but tough for a computer to guess. Better yet, require a password manager. It takes the guesswork out of it and ensures every login is protected with a unique, rock-solid credential.
- Vigilance Against Phishing: Train everyone to have a healthy dose of suspicion for unexpected emails, especially those demanding urgent action, information, or money. Teach them to spot the red flags: a strange sender address, sloppy grammar, or a tone that just feels off.
- Verifying Unusual Requests: This one is non-negotiable. If an email requests a wire transfer, asks to change payment details, or wants sensitive data, that request must be verified through another channel. A quick phone call can prevent a devastating financial mistake.
The goal is to shift your team's mindset from passive email users to active defenders of company data. Security is not someone else’s job; it's a shared responsibility that everyone owns.
Reinforcing Security Through Ongoing Training
A one-and-done training session just won't cut it. Cyber threats are always evolving, and your team’s awareness needs to keep pace. Regular, engaging training keeps security at the front of everyone's mind and helps people recognize the newest tricks and scams.
This continuous education turns email security from a dusty policy document into a living, collective effort. For more concrete steps, take a look at our guide on the 8 email security best practices to implement now. When you empower your team with knowledge and reinforce good habits, you're building a human firewall that works hand-in-hand with your technology, making your business safer from the inside out.
Meeting Compliance and Data Privacy Rules

For a lot of businesses, using a secure email for business platform isn’t just a good idea—it’s a legal necessity. If you’re in an industry like healthcare or finance, or if you handle the personal data of anyone in Europe, email privacy stops being optional. It becomes the law.
Regulations like the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) have incredibly strict rules about protecting sensitive information. Getting it wrong doesn't just expose your customers; it can land you with crippling fines that could jeopardize your entire company. This is where a secure email solution becomes an essential piece of your risk management puzzle.
Bridging Security Features with Legal Duties
So how does a hosted email platform actually help you navigate these complex legal waters? It all boils down to specific features that give you verifiable proof that you're doing your due diligence. They turn abstract legal requirements into concrete actions you can stand behind.
- End-to-End Encryption (E2EE): This is the foundation. By making sure only the intended sender and recipient can ever read a message, E2EE directly addresses the core data protection principles of regulations like GDPR.
- Data Residency Controls: Many laws dictate that a citizen's data must stay within a specific country or region. A good hosted email provider lets you choose where your servers are located, giving you direct control over data residency and simplifying compliance.
- Detailed Access Logs: If the worst happens and a breach occurs, you need a clear record of who accessed what and when. Detailed logs create an undeniable audit trail, which is crucial for any investigation and for proving your compliance to regulators.
Choosing a hosted email platform is a critical compliance decision. It serves as tangible proof that you are actively taking steps to safeguard customer data, protecting both their privacy and your business from legal jeopardy.
These features shift your email from being a potential weak spot to a documented strength. For a closer look at what's required, our GDPR compliance checklist is a great resource for understanding your responsibilities with European customer data.
Ultimately, by making email privacy and security a priority, you’re not just following the rules. You’re protecting your customers, your reputation, and your bottom line.
Got Questions About Secure Email? We've Got Answers.
Jumping into a secure email for business platform is a smart move, but it's completely normal to have a few practical questions before you commit. Let's clear up some of the most common ones so you can feel confident about making the switch.
Can I Still Use My Own Domain Name?
Of course. In fact, that's one of the main points. A professional, secure email host is designed to work with your existing domain name (like contact@yourcompany.com).
This is a standard feature, not a special request. It lets you keep your brand front and center while adding powerful security and privacy layers underneath. The setup process is usually quite simple.
Will This Be a Huge Hassle for My Team to Learn?
Not at all. The best secure email providers know that if it isn't easy, people won't use it. They've designed their platforms to look and feel just like the email services everyone is already used to.
All the heavy lifting—the encryption, the security checks, the complex stuff—happens completely in the background. Your team just logs in and gets to work. No confusing extra steps are needed.
The real mark of a great secure email platform is that the security is practically invisible. It should feel completely normal for the user, even while it's providing ironclad protection behind the scenes.
How Is This Different From Regular Email That Uses SSL/TLS?
This is a fantastic question and it highlights a crucial difference. Think of SSL/TLS as a secure tunnel. It encrypts the connection between your computer and the email server, but it doesn't do anything to protect the message itself once it's sitting on that server or traveling between servers.
A true secure email service uses end-to-end encryption. This scrambles the actual content of the message from the moment you hit "send" until your recipient opens it. Only the sender and the intended recipient have the key to unscramble it, providing a much higher, more fundamental level of email privacy.
What's This Going to Cost My Small Business?
Enterprise-grade email security is more accessible than you might think. Most providers offer flexible pricing that scales with your needs, usually based on the number of users and how much storage you require.
For a small team, you can often find a great plan for just a few dollars per user per month. It's a small investment for a massive upgrade in security and peace of mind.
Ready to take control of your business communications? Typewire offers secure, private email hosting that puts your privacy first. With custom domains, advanced security, and a simple interface, you get peace of mind without the hassle. Explore our plans and start your free trial today at https://typewire.com.
A Guide to Secure Email for Business
Posted: 2025-10-11
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31