Secure Send Email: Top Tips for Safe & Private Messaging

To really make sure your emails are secure, you need a two-pronged attack: one layer of protection for the message itself, and another for its journey across the internet.
Think of it this way: you’re not just putting your message in a locked box (end-to-end encryption), you’re also sending that box in an armored truck (Transport Layer Security). It’s this combination that truly locks down your communication.
Why You Can't Afford to Ignore Email Security
A lot of us treat our email inbox like it's a vault, but a standard email is actually more like a postcard. Anyone can read it as it hops from server to server. This isn't just a paranoid thought—it's how the system works, and it creates massive problems for people and businesses every single day. The fallout from a single unsecured message can be anything from a little embarrassing to financially devastating.
Real-World Email Threats
Take a classic business email compromise (BEC) scenario. A hacker spoofs the CEO's email and tells the finance department to wire money to a new account. It sounds simple, but this one trick costs companies billions of dollars a year. It's not a super-complex hack; it's just a clever scam that preys on our trust in a fundamentally insecure system.
Or, think about your remote team. An employee grabs a coffee and sends a sensitive client contract over the cafe's public Wi-Fi. That one small action could expose confidential data, violate privacy laws, and completely shatter a client's trust.
These aren't edge cases. We see these vulnerabilities exploited constantly:
- Phishing Attacks: Incredibly convincing emails that look like they're from your bank or a trusted service, designed to steal your logins and financial details.
- Accidental Data Leaks: It happens. Someone sends financial statements or private health records to the wrong "John Smith" in their contact list.
- Man-in-the-Middle Attacks: This is where someone intercepts your email as it travels between servers. It’s surprisingly easy to do on an unsecured network, but proper transport security stops it cold.
Strong email security isn’t just a nice-to-have feature anymore; it’s a basic requirement for doing business. Leaving your email unprotected is like leaving the front door of your office unlocked overnight.
The Growing Importance of Email Security
Protecting your digital conversations is one of the most fundamental things you can do to safeguard your money and your personal information. And it's not just us saying it—the demand for better security tools is exploding. The email security market was valued at around USD 2.781 billion in 2025 and is expected to climb as cyberattacks get more sophisticated. For a deeper dive, check out this email security market analysis.
Whether you’re a freelancer trying to protect a client proposal or a huge company guarding trade secrets, the need to securely send email is the same. It's about making sure your private conversations actually stay private.
The Building Blocks of Secure Email
To truly lock down your email, you need to think about security in two layers. First, you have to protect the email while it’s traveling from your server to the recipient's. Second, you have to scramble the content of the message itself so only the right person can ever read it.
Think of it like sending a sensitive document via a courier. You wouldn't just hand over a stack of loose papers. You’d seal them in an envelope first. The courier protects the envelope on its journey, and the sealed envelope protects the papers inside.
Securing the Journey with TLS
The first layer is Transport Layer Security (TLS). This is the modern standard that replaced SSL, and it’s essentially the armored truck for your email. TLS creates a secure, encrypted tunnel between email servers, which stops anyone from snooping on your message while it's in transit.
Most major email providers, from Gmail to more specialized services like Typewire, have TLS enabled by default. It's a non-negotiable baseline for email security today.
This diagram shows how TLS wraps a protective layer around the communication happening between applications and the internet's transport protocol.

Here's the catch, though: TLS only protects the message while it's moving. Once the email arrives, it sits on the recipient's server exactly as you sent it—unencrypted. Your email provider can still see it.
Locking the Message with End-to-End Encryption
That's where end-to-end encryption (E2EE) steps in. If TLS is the armored truck, E2EE is the locked safe inside that truck. It encrypts the message right on your device before it even leaves, and only the recipient has the key to decrypt it on their end.
With E2EE, no one in the middle can read your message. Not your email provider, not the recipient's provider, not even a hacker who compromises a server. Only you and the person you're writing to hold the keys. This is the gold standard for email privacy. A good primer on fundamental security principles can help put these concepts into a broader context.
When it comes to E2EE for email, there are two main players:
- Pretty Good Privacy (PGP): This is a decentralized system built on a "web of trust." You create your own public and private keys and then share your public key with anyone you want to communicate with securely.
- Secure/Multipurpose Internet Mail Extensions (S/MIME): This approach is more centralized. It relies on digital certificates from a trusted Certificate Authority (CA) to verify identities, making it a popular choice in corporate settings.
Key Takeaway: While both PGP and S/MIME deliver powerful end-to-end encryption, they come from different philosophies. Your choice will likely come down to who you're communicating with and how much setup you're willing to do.
To help clarify things, here's a quick look at the core technologies that keep your emails safe.
Comparing Email Security Technologies
| Technology | What It Secures | Level of Protection | Common Use Case |
|---|---|---|---|
| TLS | The connection between email servers | In-Transit: Prevents eavesdropping as email travels the internet. | The default standard for nearly all modern email providers. |
| PGP | The message content itself | End-to-End: Encrypts the message from sender to recipient. | Journalists, activists, and privacy-focused individuals. |
| S/MIME | The message content and sender identity | End-to-End: Encrypts the message and verifies the sender's identity. | Corporate, government, and regulated industries (e.g., healthcare). |
Ultimately, understanding these three components—TLS, PGP, and S/MIME—gives you a complete picture of how to build a truly secure email setup.
How to Choose a Secure Email Provider

Think of your email provider as the bedrock of your digital privacy. Choosing the right one is the single most important decision you can make to secure send email. After all, even the strongest encryption tools won't help much if the platform itself is full of holes.
So many of the big, mainstream providers prioritize convenience over your security, often treating your personal data as a commodity. A genuinely secure provider flips that script, building its entire service around protecting your information, not selling it.
What to Look For in a Provider
It's easy to get bogged down by marketing jargon when you're comparing services. Instead, I've found it's best to cut through the noise and focus on a few non-negotiable features that truly make a difference.
The absolute gold standard is a zero-knowledge architecture. This is just a technical way of saying the provider builds end-to-end encryption into everything and, critically, has no way to access your emails or attachments. If they can't see your data, they can't scan it, sell it, or hand it over. Simple as that.
For example, services like ProtonMail and Tutanota are built on this principle. You'll notice they can't reset your password for you if you lose it—that's because they don't hold the keys to your account. It might seem inconvenient, but it's a fantastic sign that they're serious about zero-knowledge.
Transparency is another huge factor. I always look for providers with open-source applications. This means independent security experts from around the globe can comb through the code, looking for vulnerabilities or hidden backdoors. It’s a powerful way to build trust.
Evaluating Privacy and Jurisdiction
You also have to think about where a provider is physically located. It might seem like a small detail, but it has massive implications for your privacy, as it dictates which government's laws they must follow.
Here’s what I recommend looking for:
- Strong Privacy Laws: Prioritize providers headquartered in countries known for robust data protection, like Switzerland or Germany. These legal frameworks offer a much stronger defense against government prying.
- Data Sovereignty: Does the provider own its own servers, or is it renting space from a cloud giant? Owning their own hardware gives them total control over the security of your data.
The market for cloud-based email security is exploding, valued at USD 5.55 billion in 2025 and expected to reach USD 9.73 billion by 2030. This growth, detailed in a recent cloud-based email security software market report, shows just how critical it is to pick a provider that puts your privacy first.
Making the right call means balancing these technical and legal considerations. To make things easier, we've done some of the legwork for you in our breakdown of the top 7 best email providers for privacy in 2025. At the end of the day, finding a service dedicated to these core principles gives you the strongest possible foundation for keeping your communications private.
A Walkthrough of PGP Encryption Setup
Diving into PGP (Pretty Good Privacy) encryption might sound like a job for a cybersecurity pro, but modern tools have brought it within everyone's reach. You really don't need a background in coding to secure send email using this powerful, end-to-end encryption method.
Let's walk through a common scenario. Imagine you're a designer sending confidential product mockups to a new client. You can't risk a leak, so a standard email just won't cut it. This is a perfect use case for PGP. A fantastic, free tool for this is Mailvelope, a browser extension that works right inside webmail clients like Gmail and Outlook.com.
This handy infographic shows the basic PGP workflow in three simple stages.
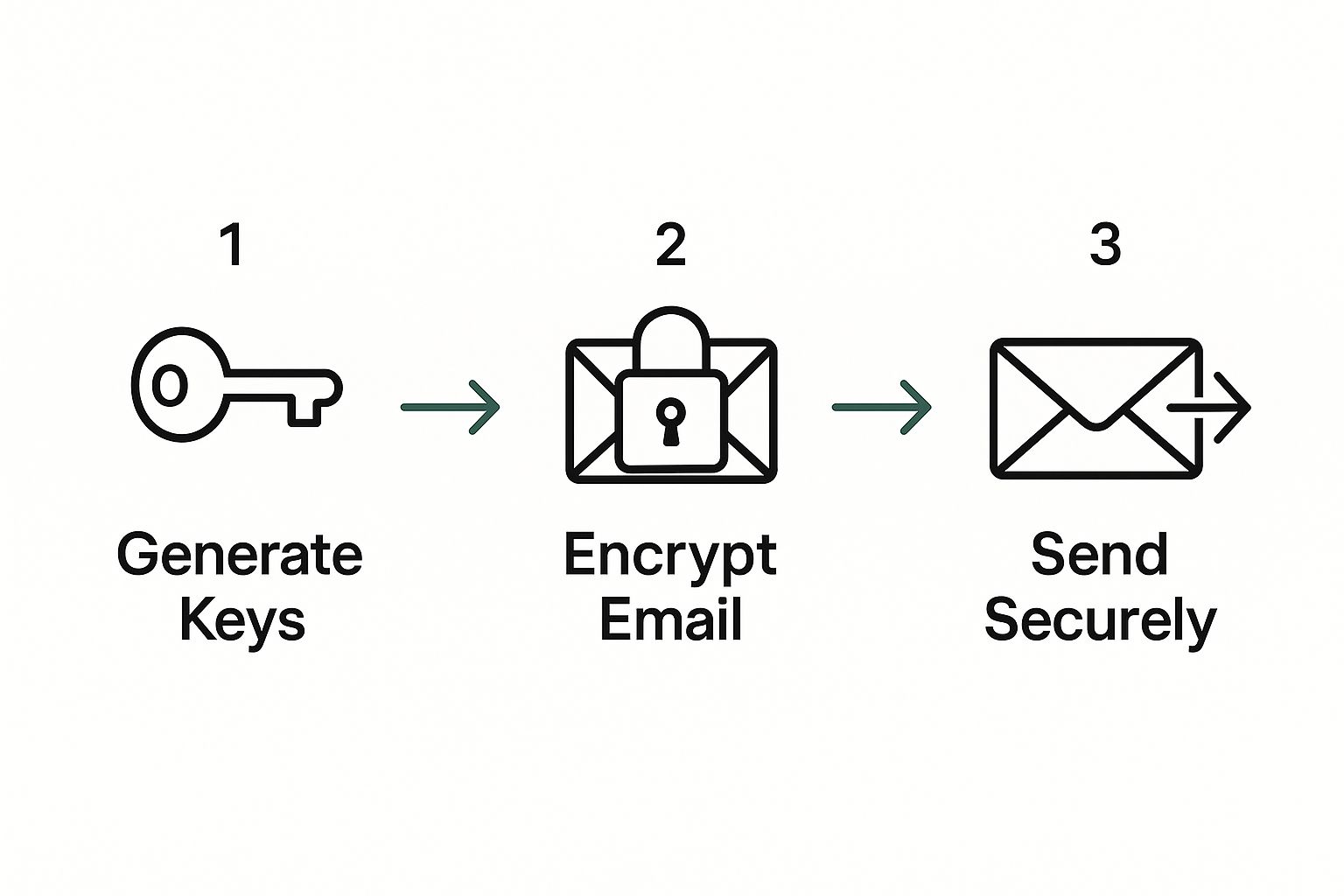
As you can see, it all starts with creating your keys. From there, you encrypt your message, and finally, you send it securely, knowing only the right person can ever read it.
Generating Your First Key Pair
Your first move is creating your public and private keys. It's helpful to think of them this way:
- Your public key is like a PO box address. You can share it freely with anyone who needs to send you something securely.
- Your private key is the key to that PO box. You guard it with your life and never, ever share it.
With a tool like Mailvelope installed, it will prompt you to generate a new key. You'll just need to enter your name, the email you're securing, and a very strong password. This password is the final line of defense for your private key.
Once you hit 'generate', your key pair is stored locally inside the extension. Now you're ready to share your public key.
Exchanging Keys and Sending Your First Encrypted Email
To send those encrypted mockups, you need your client's public key, and they need yours. This is the "key exchange." You can export your public key as a simple text file and email it to them, and they'll do the same for you.
Once you have their key file, you simply import it into Mailvelope. Now, your system knows exactly how to encrypt messages for your client.
Actually sending the email is surprisingly simple:
- Open your webmail (like Gmail) and compose a new message like you always do.
- Attach your confidential mockup files.
- Look for the new Mailvelope icon in the composition window and click it.
- Choose your client from the list of recipients you have keys for.
- Click "Encrypt."
That's it. Mailvelope instantly scrambles the entire email—body and attachments—into unreadable ciphertext. The only person who can decrypt it is your client, using their private key.
This key exchange is the most critical part of the entire process. You have to be sure the public key you received actually belongs to your client. A quick phone call or video chat to confirm is a small step that adds a massive layer of security.
While tools like Mailvelope make PGP far more approachable, some people prefer a service where this functionality is already baked in. If that sounds like you, check out our guide to the top 7 best secure mail service providers for 2025. It's an in-depth look at providers that make this even easier.
Building Your Daily Email Security Habits

Even with the best encryption tools in your arsenal, the human element is what makes or breaks your security. To truly secure send email, you need to combine that powerful technology with smart, consistent habits. It’s all about weaving security into the fabric of your daily routine so it becomes second nature.
These practices don't have to be complex or time-consuming. In fact, it's the simple, conscious actions you take every day that separate a secure communicator from an easy target. Adopting these habits is the single most effective way to protect your sensitive information, day in and day out.
Make Two-Factor Authentication Non-Negotiable
If you only take one piece of advice from this entire guide, let it be this. Two-factor authentication (2FA) is your single greatest defense against someone hijacking your account. Even if a thief manages to steal your password, they're stopped dead in their tracks without that second verification step—usually a code sent to your phone.
Think of it like adding a heavy-duty deadbolt to your front door. A password is the standard lock, which can be picked. But 2FA is that extra, much tougher layer of security that thwarts the overwhelming majority of break-in attempts.
A compromised email account isn't just an inconvenience; it's a skeleton key that can give an attacker access to every other service connected to that address. Making 2FA mandatory for your email should be your absolute number one priority.
Scrutinize Every Link and Attachment
Phishing attacks have gotten frighteningly sophisticated. Emails can look identical to ones from brands you trust, all designed to create a sense of panic or urgency that makes you click before you think. You need to train your brain to pause and check before acting.
Develop these quick reflexes:
- Hover, Don't Click: Before your cursor ever clicks a link, just hover over it. Your browser or email client will show you the real destination URL. If the text says "amazon.com" but the preview shows a bizarre, misspelled web address, you've spotted a phish.
- Question Unexpected Files: Get an invoice you weren't expecting? A "shared document" out of the blue? Even if it seems to be from a colleague, don't open it. Their account might have been hacked. Shoot them a quick text or call them to verify they actually sent it.
Know When Encryption Is Necessary
Let's be realistic—not every email needs the full end-to-end encryption treatment. You don't need to fire up PGP to send a lunch invitation. What you do need is a clear mental checklist for when it's time to secure send email with an extra layer of protection.
Flip that switch to "encrypt" any time a message contains:
- Personally Identifiable Information (PII): Things like Social Security numbers, home addresses, or dates of birth.
- Financial Data: Bank account details, credit card info, or financial statements.
- Confidential Business Information: Trade secrets, sensitive client data, or internal strategy documents.
Turning these checks into automatic habits is what ultimately transforms your email from a potential vulnerability into a genuinely secure channel for communication.
Answering Your Questions About Sending Secure Email
Even with the best tools, putting email security into practice can bring up some tricky real-world questions. Let's walk through some of the most common ones I hear from people just starting to secure send email.
Getting these details right is what separates theory from effective, everyday security.
Is My Standard Gmail or Outlook Account Secure Enough?
For casual, non-sensitive chats, sure. Services like Gmail and Outlook use Transport Layer Security (TLS), which is great for protecting your email as it travels from one server to another. Think of it as putting your letter in a secure mail truck.
The problem is, the post office (the email provider) can still open and read your mail. These services don't offer end-to-end encryption by default, meaning they can access and scan your emails. When you're dealing with financial records, legal contracts, or anything you wouldn't want exposed, you need a higher level of security.
For a deeper dive, check out our guide on how to send secure email that stays private.
What Happens if I Send an Encrypted Email to Someone Without Encryption Tools?
This is a classic "what if" and a fantastic question. If you send a PGP-encrypted email to someone who isn’t set up for it, they’ll just see a jumbled mess of characters. The email will be completely unreadable to them.
This is why you can't just flip a switch and start sending encrypted messages to everyone. You need to coordinate with your recipient first, usually by exchanging public keys so they can decrypt what you send.
Thankfully, many secure email providers have figured this out. Their platforms often provide a workaround, like sending the recipient a secure link. When they click it, they can verify their identity and view the message in a secure web portal—no complex setup required on their end.
Key Takeaway: You can't just send an encrypted email into the void and hope for the best. Communication and coordination with your recipient are essential for end-to-end encryption to work as intended.
The demand for these smoother, more user-friendly solutions is why the email encryption market is booming. It's projected to jump from USD 9.30 billion in 2025 to a massive USD 23.33 billion by 2030, largely because of the ever-present threat of data breaches and cyberattacks. You can learn more about this expanding market and its drivers.
Do I Need to Encrypt Every Single Email I Send?
Definitely not. Encrypting every single message would be overkill and create a lot of unnecessary hassle for both you and your recipients. The key is to be selective and smart about it.
You don't need to encrypt an email about grabbing lunch, but you absolutely should encrypt one with a new business proposal or your personal tax documents.
A simple gut check works wonders here. Just ask yourself, "Would I be in serious trouble if this information was made public?" If the answer is yes, encrypt it.
Here’s a simple way to think about it:
- Public-level info: Scheduling, quick questions, sharing articles. No encryption needed.
- Private-level info: Business strategy, financial data, client lists, personal records. Encryption is a must.
This approach keeps your high-stakes communication locked down without bogging down your daily workflow.
Ready to take control of your email privacy? Typewire offers a secure, private email hosting platform designed from the ground up to protect your communications. With zero tracking, no ads, and powerful security features, you can communicate with total peace of mind. Start your 7-day free trial and experience a truly private inbox at https://typewire.com.
Secure Send Email: Top Tips for Safe & Private Messaging
Posted: 2025-08-31
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27