How to Protect Personal Information Online: Essential Tips

Protecting your personal information online isn't about one single action; it's about building a series of smart, deliberate habits. Think of it as a layered defense system for your digital life, starting with strong, unique passwords for every account, adding two-factor authentication, and always thinking twice before you share anything.
It really comes down to actively managing your digital footprint and remembering that every click leaves a trace.
Your Digital Footprint And Why It Matters

Let's get practical. In a world where so much of our lives happens online, knowing how to protect personal information isn’t just some tech-savvy skill—it’s a fundamental part of modern life. Every time you log into an app, buy something online, or post on social media, you leave behind a trail of data. This is your digital footprint.
This footprint is much more than just your name and email. It can easily include your location history, what you like to buy, your political leanings, and even the content of private conversations. To companies, this data is a goldmine for targeted advertising. To criminals, it's a treasure map for identity theft, fraud, and worse.
The Growing Concern Over Online Privacy
If you're feeling uneasy about your data privacy, you're not alone. It’s a widespread and completely justified concern. The numbers tell a stark story: a recent survey found that over 92% of Americans are worried about their online privacy.
But here’s the kicker: only 3% of them feel they actually understand the privacy laws meant to protect them. This massive gap highlights a real problem—we're anxious, but we're not always empowered. Globally, the sentiment is the same, with more than 85% of adults wanting to do more to protect their privacy. You can explore more of these eye-opening data privacy statistics to see the full picture.
This gap between wanting to act and actually acting often comes from feeling overwhelmed. Many people just don't know where to begin, or they assume that protecting their data is too complex to even try.
The good news is that you don't need to be a cybersecurity expert to make a significant difference. A few deliberate changes in your habits can drastically reduce your risk exposure and give you back control over your personal information.
Your Quick-Start Online Privacy Checklist
Before we get into the nitty-gritty, let's start with the big wins. Here are the five most impactful actions you can take right now to better protect your personal information online. Think of this as your foundational toolkit for a solid digital defense.
| Action Item | Why It Matters | Time to Implement |
|---|---|---|
| Audit Your Accounts | Deletes sensitive data from old services you no longer use. | 30-60 minutes |
| Strengthen Passwords | Prevents one breach from compromising all your accounts. | 15 minutes (with a manager) |
| Enable 2FA | Adds a crucial second layer of security to your most vital accounts. | 5 minutes per account |
| Review Privacy Settings | Limits what social media and apps can collect and share about you. | 20-30 minutes |
| Browse Securely | Protects your data from being intercepted, especially on public Wi-Fi. | 2 minutes (to install a VPN) |
This table gives you a roadmap. In the rest of this guide, we'll break down the "how" and "why" for each of these steps, moving you from feeling concerned to feeling confident and in control of your digital life.
Building a Fortress Around Your Accounts

Your passwords are the front door to your digital life. For too long, the advice has been a vague, unhelpful "use a strong password." That's not a strategy; it's a suggestion. Let’s build a real, sustainable plan to create a fortress around your most valuable accounts.
The single biggest mistake I see people make is reusing passwords. It’s a habit born from convenience—who can possibly remember dozens of unique, complex passwords? So, we fall back on the same one, or a slight variation, for everything from our email to that random online store we used once.
This is the digital equivalent of using the same key for your house, your car, and your safe deposit box. If a thief gets that one key, they get everything. In the online world, a data breach at some minor website you forgot you even signed up for can give criminals the key to your entire digital life.
Moving Beyond Basic Passwords
To really protect your accounts, you have to shift your thinking from short, jumbled passwords to long, memorable passphrases. A password like Tr0ub4dor&3 feels complex, but it's surprisingly easy for a computer to guess with modern brute-force attacks.
A passphrase, on the other hand, is a game-changer. Think of a simple, random sequence of words like correct horse battery staple. It's way longer, far easier for you to remember, and exponentially harder for a computer to crack.
Here’s why this works so well:
- Length is King: The strength of a password is all about its length. Every character you add dramatically increases the number of combinations an attacker would have to try.
- Genuinely Memorable: A string of random characters is a nightmare to recall, but a sequence of four or five unrelated words sticks in your brain.
- Resistant to Guesswork: Unlike using your pet's name or your birthday, random word combinations have no personal connection, making them immune to social engineering.
The Non-Negotiable Role of a Password Manager
So, how do you actually manage a unique, strong passphrase for every single account? Simple: you don't. A password manager does it for you. These tools are the absolute cornerstone of modern account security.
A password manager is an encrypted digital vault that stores all your login information. You just have to remember one strong master password to unlock it. From there, it can generate and save incredibly complex, unique passwords for every site you use.
A password manager removes the single greatest point of failure in personal online security: human memory. It automates good password hygiene, making the most secure option the easiest one.
This is a huge step in learning how to protect personal information online. When a data breach inevitably happens at a service you use, the damage is contained. The stolen password is now useless everywhere else.
Putting It All Together: A Practical Strategy
Ready to build your fortress? It’s easier than you think.
First, Choose and Set Up Your Manager:
Start by picking a reputable password manager. Your browser might have one built-in, but dedicated apps often provide better features like secure note storage and data breach alerts.
Next, Tackle Your Critical Accounts:
Don't try to boil the ocean. Begin with your most important accounts: your primary email, banking apps, and main social media profiles. Use the manager's built-in generator to create new, long, and random passwords for each of them.
Finally, Update Others Over Time:
There’s no pressure to change everything at once. From now on, whenever you log into another service, just take a moment to update the password using your new manager. In just a few weeks, you'll have a rock-solid system in place.
Combining the passphrase philosophy with the power of a password manager eliminates the weakest link in your security chain. To truly build a fortress around your online accounts, it's crucial to implement the latest top data security best practices that experts rely on for a comprehensive defense.
Navigating The Web Without Leaving A Trace
Every time you go online, you're leaving behind digital breadcrumbs. If you're not careful, those clicks and connections can expose your personal information to people who shouldn't have it. The good news? Protecting yourself doesn't require a computer science degree. It just takes a few smart habits.
Let's start with the basics. Before you even think about typing a password or credit card number into a website, glance up at the address bar. You’re looking for two things: a little padlock icon and a URL that begins with "https." That 'S' is everything—it stands for secure, meaning the connection between you and the site is encrypted. It’s a simple check that takes a second but can save you a world of trouble.
Your Best Defense on Public Networks
We’ve all done it. You’re at a coffee shop, airport, or hotel, and you hop onto their free Wi-Fi. It’s convenient, but these public networks are notoriously insecure, making them a playground for anyone looking to snoop on your activity. On an open network, a determined attacker can potentially see everything you’re doing.
This is where a Virtual Private Network (VPN) becomes non-negotiable. A VPN creates an encrypted tunnel for all your internet traffic. Think of it as a private, armored car for your data, shielding it from prying eyes, even when you’re on the most insecure public network.
Using a VPN on public Wi-Fi is one of the single most important steps you can take for your online safety. It transforms a dangerously open connection into a private one, effectively making your data invisible to anyone else on that network.
Beyond public spaces, a VPN also masks your real IP address, which is basically your device's home address online. This makes it much harder for websites, advertisers, and even your own Internet Service Provider (ISP) to track your location and what you do online.
Choosing Privacy-First Browsers and Search Engines
Most mainstream web browsers and search engines are built to track you. It's a core part of their business model. They collect data on your searches and the sites you visit to build a detailed profile for targeted ads. But you can opt out of this surveillance.
Consider making a switch to tools that put your privacy first.
- Privacy Browsers: Browsers like Brave or Firefox (with its privacy settings cranked up) are designed to block trackers and intrusive ads right out of the box.
- Private Search Engines: Unlike Google, search engines like DuckDuckGo or Startpage don’t log your search history or tie your queries back to a personal profile. You get the results you need, without the surveillance.
This is a simple change that has a huge impact. You’re taking back control and navigating the web without leaving a trail of personal data for companies to profit from.
Spotting and Sidestepping Phishing Scams
One of the most common threats you’ll face is phishing. These are crafty emails, texts, or messages designed to trick you into giving away sensitive info like passwords or credit card details. The fallout from these attacks is massive; the global average cost of a data breach has soared to $4.88 million per incident. Human error plays a part in 68% of these cases, with phishing and stolen credentials leading the charge. You can find more details on the rising costs of data breaches on deepstrike.io.
Phishing attacks almost always create a sense of urgency to get you to act before you think. You might see a message claiming your account has been hacked or that you've won a prize that needs to be claimed right now.
Learning to spot the red flags is your best defense. Be suspicious of generic greetings like "Dear Customer," look for obvious typos and grammatical errors, and always check the sender's email address to see if it matches the company's actual domain.
Before you click any link in an email, hover your cursor over it. Your browser will show you the real destination URL at the bottom of the screen. If it looks fishy, don't click it. By training yourself to spot these deceptions, you stop being an easy target and become a much harder one to fool.
Adding Your Digital Deadbolt With 2FA
Think of your password as the lock on your front door. It’s a decent first line of defense. But Two-Factor Authentication (2FA) is the steel deadbolt you add for real security. It’s one of the single most effective ways to protect your personal information, stopping intruders cold even if they manage to steal your password.
Without 2FA, a leaked password gives an attacker the keys to the kingdom. But with 2FA active, that same stolen password becomes nearly worthless. The would-be hacker is stuck on the login page, unable to provide the second piece of proof that only you possess.
Understanding Your 2FA Options
Not all 2FA is created equal. The methods range from convenient to fortress-like, and the right choice really depends on how critical the account is. Thankfully, setting it up is usually straightforward—most services guide you through a simple process, often just scanning a QR code with your phone.
Here’s a quick rundown of the most common types you'll encounter:
- SMS Text Codes: The service texts a one-time code to your phone. While it’s certainly better than nothing, this is the least secure option because it's vulnerable to "SIM-swapping," a technique where scammers trick your mobile carrier into porting your number to their phone.
- Authenticator Apps: Apps like Google Authenticator, Microsoft Authenticator, or Authy generate a fresh, time-sensitive code on your device every 30 seconds. This is a major security step up from SMS and a fantastic baseline for most accounts.
- Physical Security Keys: These are small hardware devices, often resembling a USB stick, that you physically plug in or tap to approve a login. This method offers the highest level of security available to consumers and is nearly immune to phishing attacks.
For anyone looking to really button up their security, it's worth reading about enhancing security with new two-factor authentication options to see what's on the horizon.
Why Passwords Alone Just Don't Cut It Anymore
Let's walk through a real-world scenario. A hacker buys your email and password from a data breach on the dark web. They head over to your banking website, plug in your credentials, and feel that rush of imminent victory.
But then, the site asks for a six-digit code from your authenticator app. The hacker doesn't have your phone. They're stopped dead in their tracks. Access denied.
Two-Factor Authentication completely changes the game by neutralizing the threat of a compromised password. It transforms security from being about something you know (a password) to something you know and something you have (your phone or a security key).
This simple action can block over 99.9% of automated attacks on your accounts. In an age where data breaches are a weekly occurrence, relying on just a password is a gamble you can't afford to take.
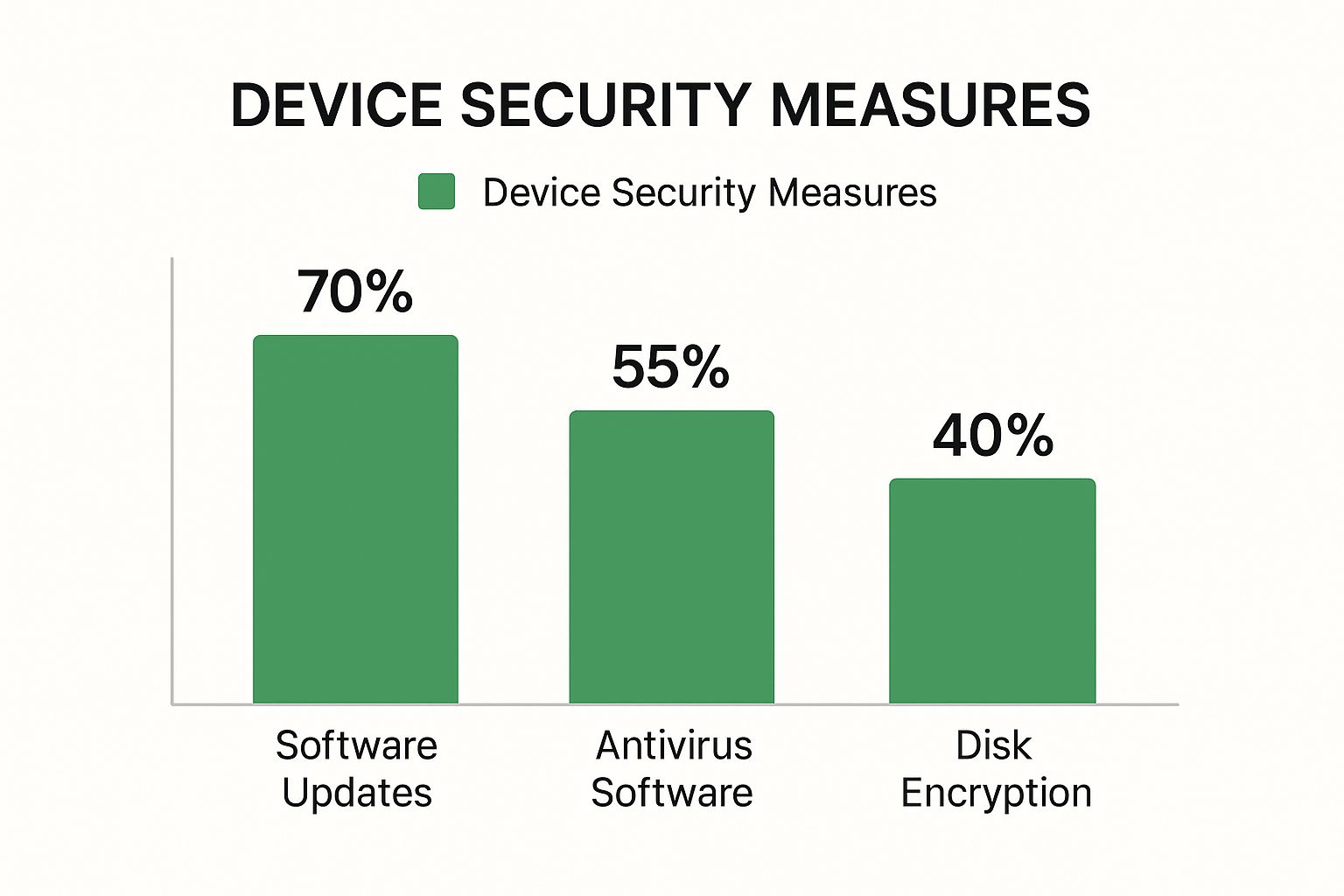
The chart above shows that while many people are good about software updates, other critical protections like disk encryption lag behind. This highlights a common pattern: people often overlook some of the most powerful security tools at their disposal, like 2FA.
To help you decide which method fits your needs, let's compare the options side-by-side.
Comparing Two-Factor Authentication (2FA) Methods
| 2FA Method | Security Level | How It Works | Best For |
|---|---|---|---|
| SMS/Text Message | Low | A code is sent to your phone via text. | Basic accounts where you have no other option. It's better than nothing. |
| Authenticator App | High | An app on your phone generates a constantly changing 6-digit code. | Most online accounts, including email, social media, and banking. |
| Physical Security Key | Highest | A hardware device (USB/NFC) that you tap or insert to verify your login. | Critical accounts like your primary email, password manager, and financial platforms. |
Ultimately, the best 2FA method is the one you'll actually use, but I strongly recommend pushing for an authenticator app or a physical key wherever possible.
Your Action Plan: Where to Enable 2FA First
Feeling overwhelmed? Don't be. You don't need to enable 2FA on every single account overnight. Instead, focus on your "high-value targets"—the accounts that would cause the most chaos if compromised.
Here’s your priority list:
- Your Primary Email Account: This is the master key to your digital life. If a hacker gets in, they can hit "forgot password" on almost every other service you use. Lock this down first.
- Financial and Banking Apps: This one's a no-brainer. Protect your money. Go into the security settings of your bank, investment apps, and services like PayPal, and enable the strongest 2FA they offer.
- Your Password Manager: This is the vault containing all your other digital keys. It absolutely must have 2FA enabled, preferably with an authenticator app or, even better, a physical key.
- Key Social Media Accounts: Your social profiles are goldmines of personal data and are prime targets for impersonation scams and takeovers.
Spending just 15 minutes adding this digital deadbolt to your most important accounts is one of the smartest security investments you can make. For a deeper look at protecting your most vital online asset, check out our guide: https://typewire.com/blog/read/2025-08-06-a-guide-to-multi-factor-authentication-email-security.
Conducting Your Personal Privacy Audit
Most apps and social media platforms are designed to collect as much of your data as they can right out of the box. It’s time to flip the script. A personal privacy audit is your chance to go on the offensive, methodically reviewing what your accounts and devices are sharing about you and locking things down.
This isn’t about going off the grid. It's about consciously shifting from being a passive data point to an active manager of your own digital identity.
Think of it like this: you wouldn't leave your front door wide open for anyone to wander in. Your digital life deserves the same care. Regularly auditing your privacy settings is the digital equivalent of checking the locks, ensuring you’re the one deciding what to share and with whom.
Taking Control of Your App Permissions
Your smartphone is a goldmine of personal data, and every app you install wants a piece of it. Many request access to your contacts, camera, microphone, and location history—often for reasons that have nothing to do with their actual function. This is where you can make a huge, immediate impact.
Start by digging into your phone's settings. Look for a menu labeled "Privacy" or "Permissions." Inside, you'll find a list of data types like "Location Services," "Contacts," and "Microphone." Tap into each one to see a list of every app that has requested access.
You’ll probably be surprised by what you find. Does that simple photo editing app really need to see your entire contact list? Does that puzzle game need to know your precise location 24/7? The answer is almost always a hard no.
- Be ruthless. Go through each category and revoke access for any app that doesn't absolutely need it to function.
- Limit location tracking. For apps that genuinely need your location (like maps or ride-sharing), switch the permission from "Always" to "While Using the App." This simple change stops them from tracking your every move.
- Make it a habit. Set a calendar reminder to do this once a quarter. App updates can quietly reset these permissions, so it pays to stay vigilant.
Auditing Your Social Media and Google Accounts
If your phone is a data goldmine, then social media and Google are the epicenters. Their default settings are geared for maximum data sharing, not maximum privacy. It’s time to dive in and adjust them to a level you're comfortable with.
Fortunately, platforms like Facebook, Instagram, and Google have made this a bit easier. Look for a feature often called a "Privacy Checkup" or "Security Checkup." These tools are designed to walk you through the most critical settings one by one.
Here’s what to look for:
- Ad Settings: Find the ad personalization options and turn them off. You'll still see ads, but they won't be targeted based on your personal activity and data.
- Off-Platform Activity: This is a big one. Many services track your activity on other websites and apps. You can view this surprising history and, more importantly, disconnect it from your account.
- Third-Party Connections: Review the list of apps and websites you've connected to your account over the years. Remove anything you no longer use or don't recognize.
A personal privacy audit is an act of digital hygiene. By methodically reviewing your settings, you are actively reducing your attack surface and taking back control over how your information is used and shared.
Finding and Deleting Old, Unused Accounts
Over the years, you've probably signed up for countless websites and services you've completely forgotten about. These dormant accounts are a serious liability. They sit there, often containing sensitive personal information, just waiting for that service to suffer a data breach.
As part of your audit, it's also smart to keep an eye out for unauthorized activity by accessing your free credit reports regularly. This is a great way to spot fraudulent accounts that might have been opened in your name. For a deeper dive into managing your data rights, especially under regulations like the GDPR, our GDPR compliance checklist offers some great, practical guidance.
The reality is that we're often forced to make a difficult trade-off. Research shows a staggering 72.6% of iOS apps track user data, and free apps are four times more likely to do so than paid ones. At the same time, 37% of consumers admit they share personal data simply because there’s no other way to get the service.
You can learn more about these trends in consumer data privacy on explodingtopics.com. By taking the time to conduct an audit, you put yourself back in the driver's seat, allowing you to consciously decide which services are truly worth that exchange.
Common Online Privacy Questions Answered
Even when you've got the basics down, certain situations pop up that can make you second-guess your choices. The world of online privacy is filled with gray areas, so it's only natural to have questions. Here are some clear, straightforward answers to the dilemmas I see people run into most often.
Getting a handle on these specific scenarios is just as important as building good day-to-day habits. Once you understand the "why" behind the advice, you can start making smarter, more confident decisions on your own. Let's dig into some of the most common questions.
Do I Really Need A VPN At Home?
This is a great question, and the answer is yes, if you truly value your privacy. A VPN is an absolute must-have on public Wi-Fi, but using one at home adds a critical layer of protection that most people overlook.
Your Internet Service Provider (ISP) can see every single website you visit, every app you use, and how long you spend on them. In many countries, they are legally allowed to bundle up that browsing data and sell it to advertisers. A VPN encrypts your connection, essentially scrambling it so your ISP can no longer read it. They can see you're online, but they can't see what you're doing.
A VPN effectively draws a digital curtain between you and your ISP. It’s a powerful tool for keeping your online activity private, even on a network you own and trust.
How Do I Know If My Data Was In A Breach?
It’s a horrible feeling—hearing about a massive data breach on the news and wondering if your account was one of the millions swept up in it. The good news is, you don't have to live in suspense.
The best-known tool for this is a free service called Have I Been Pwned?. It’s a massive, searchable database of information collected from hundreds of data breaches. Just pop in your email address, and it will tell you if it has appeared in any known compromises.
Here’s how I recommend using it:
- Check all your emails. Don't forget old ones you barely use.
- Sign up for alerts. The service can automatically notify you if your email shows up in a future breach.
- Use your password manager's tools. Many password managers now have built-in breach monitoring that alerts you if one of your saved accounts is compromised.
Checking this regularly is a crucial, proactive step. It gives you a head start to change your password and lock down an account before a thief gets a chance to use your stolen info.
What Is The Single Most Important Account To Secure?
Your primary email account. No question. Think of it as the master key to your entire digital life.
Almost everything you do online is tied to that one email address—banking, social media, shopping, you name it. It's where password reset links are sent, where security notifications land, and where verification codes arrive. If a criminal gets into your inbox, they can systematically pivot to take over almost every other account you own.
Because it's the digital linchpin, you need to protect it with the highest level of security available.
- Use a long, unique passphrase that isn’t used anywhere else.
- Keep that passphrase locked away safely in your password manager.
- Enable the strongest Two-Factor Authentication (2FA) offered—preferably an authenticator app or a physical security key.
Securing this one account is the most impactful thing you can do to protect yourself online. To go deeper, our guide to the most common email security threats offers a complete defense strategy you can put into action.
Is Incognito Mode Actually Private?
Not really, and definitely not in the way most people assume. "Incognito" or "private browsing" mode has a very narrow function: it stops your browser from saving your history, cookies, and site data on your computer.
That's helpful if you're on a shared device and don't want the next user to see your search history. But it does not make you anonymous online.
Your online activity is still completely visible to:
- Your Internet Service Provider (ISP)
- Your employer or school (if you're on their network)
- The websites you visit
They can all still see your IP address and track what you're doing. For true privacy that shields your activity from your ISP and other outside observers, you need a VPN. Think of Incognito mode as tidying up your room—a VPN is more like locking the door.
Ready to take back control of your most important online asset? At Typewire, we believe your email should be private, secure, and free from surveillance. Explore our secure email hosting and experience a better way to communicate. Learn more at Typewire.
How to Protect Personal Information Online: Essential Tips
Posted: 2025-08-25
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31