How to Make Email Secure: Top Tips to Protect Your Account

Securing your email isn't about finding a single magic bullet; it's a discipline built on layers of protection. A lot of people get this wrong. They think one strong password is all it takes. In reality, you need a combination of strong authentication, sharp phishing detection, proper data encryption, and a trustworthy email service.
Think of it like this: your inbox is the command center for your entire digital life. It holds the keys to your bank accounts, social media, and sensitive personal conversations. Leaving it poorly defended is an open invitation for trouble.
Understanding the Pillars of Email Security

When you learn how to make your email secure, what you're really learning is how to defend against specific, predictable threats. The challenge here is the sheer scale of email use. It’s the go-to communication tool for billions of people, and it’s not slowing down.
We’re looking at a jump from roughly 4.83 billion global email users in 2025 to a projected daily email volume of nearly 523 billion by 2030. You can dig into what this growth means for security in cloudHQ's detailed report. This incredible volume makes email a massive, irresistible target for attackers. That's why having a solid security strategy isn't just a recommendation—it's essential.
The Four Core Security Pillars
From my experience, a truly secure email setup always comes down to getting four key areas right. If you neglect even one, you're leaving a gaping hole for attackers to exploit. A comprehensive approach is the only way to genuinely protect your information.
-
Authentication: This is all about proving your identity. It's much more than just a password and serves as your first and most critical line of defense against someone trying to hijack your account.
-
Threat Awareness: You have to become your own security analyst. This means training yourself to spot and sidestep scams, especially the phishing emails designed to trick you into handing over your credentials.
-
Encryption: This pillar is about making your data unreadable. By scrambling your messages, you ensure that even if someone manages to intercept them, the information is completely useless without the decryption key.
-
Provider & Client Security: The foundation of your entire setup is the email host you choose and the apps you use to access your mail. A weak foundation undermines everything else you do.
The biggest mistake I see people make is relying solely on a strong password. True email security is a system where each layer supports the others. If one fails, the rest are there to catch you and prevent a total disaster.
To help you visualize how these components create a comprehensive defense, I've broken them down into a simple table. It summarizes the essential actions needed, the specific threats they counter, and their overall impact.
Core Pillars of Email Security
| Security Pillar | Primary Action | Threat Mitigated | Impact Level |
|---|---|---|---|
| Authentication | Enable Multi-Factor Authentication (MFA) | Unauthorized account access, password theft | High |
| Threat Awareness | Learn to identify phishing emails | Phishing, malware, credential theft | High |
| Encryption | Use end-to-end encrypted services | Data interception, snooping, privacy loss | Very High |
| Provider Security | Choose a secure, private email host | Server-level breaches, data mining | Foundational |
Getting a handle on this framework is your first real step toward building a bulletproof email defense. Each pillar addresses a different vulnerability, and together, they form a resilient shield for your most important digital asset.
Building Your First Line of Defense With Strong Authentication

We’ve all heard the advice to "use a strong password" a million times, but that advice often misses the bigger picture. True digital security isn't just about a password's complexity; it's about building an entire authentication system that's a nightmare for attackers but second nature for you. This is your most critical line of defense.
Let's start by ditching the idea of a traditional password. Forget about those hard-to-remember jumbles of characters like Tr0ub4dor&3. A far better approach is the passphrase—a short sequence of random, unrelated words like correct-horse-battery-staple. It’s surprisingly easy for a human to recall but incredibly difficult for a computer to crack.
Better yet, stop relying on your memory at all. A good password manager is like a digital Fort Knox for your credentials. It generates and securely stores unique, complex passphrases for every single service you use. All you have to remember is one master password. This single step is a game-changer, as it completely walls off the risk of a breach on one site spreading to your email.
The Power of Multi-Factor Authentication
Even with a rock-solid, unique passphrase, you're still vulnerable if that credential gets exposed in a data breach. That's where Multi-Factor Authentication (MFA), sometimes called 2FA, comes in. It’s your account’s secret weapon, adding a second layer of proof that stops attackers cold, even if they have your password.
Here's a real-world scenario I've seen play out too many times: a hacker gets their hands on a list of credentials from an old, forgotten forum you once used. They run that list against major email providers, and your password works. Without MFA, they’re in. With MFA, their login attempt is blocked because they don't have that second factor—the one-time code from your phone.
MFA is the single most effective step you can take to secure your email. It neutralizes the threat of stolen passwords, which is the most common way accounts are compromised.
The good news is that these security measures are making a tangible difference across the board. As adoption grows, our collective digital environment gets safer. Projections show spam is expected to drop from 48% of email traffic in 2025 to 43% by 2030. Even more impressively, the success rate of phishing attacks may plummet from 0.12% to just 0.03%. You can dig deeper into these trends in cloudhq's comprehensive email statistics report.
Choosing Your MFA Method
Not all MFA is created equal. You have a few options, each offering a different mix of security and convenience.
-
SMS Text Messages: Your provider texts a code to your phone. It's convenient, sure, but it's the weakest form of MFA due to the risk of "SIM-swapping," where an attacker tricks your mobile carrier into porting your number to their device.
-
Authenticator Apps: Apps like Google Authenticator, Microsoft Authenticator, or Authy generate time-sensitive codes right on your device. This is far more secure than SMS and should be the baseline for most people.
-
Physical Security Keys: These are small hardware devices, like a YubiKey, that you plug into a USB port or tap on your phone. They offer the highest level of security available and are practically immune to phishing.
For the vast majority of users, an authenticator app hits that sweet spot between robust security and ease of use.
How to Enable MFA on Popular Platforms
Getting MFA set up is a quick win—it usually takes less than five minutes. Here’s how you can get it done on the major email platforms:
-
Gmail: Head to your Google Account settings, click on the "Security" tab, and find the "2-Step Verification" section. From there, you can follow the prompts to add an authenticator app.
-
Outlook/Microsoft: Sign into your Microsoft account, choose "Security," and then "Advanced security options." You can enable two-step verification and add the Microsoft Authenticator app as your method.
-
Apple Mail/iCloud: On your iPhone or Mac, open System Settings, tap your name, then go to "Password & Security." You'll see the option to turn on Two-Factor Authentication right there.
By taking these straightforward actions, you've just erected a formidable barrier around your digital life. Your email account has gone from being an easy target to a well-defended fortress.
How to Spot and Defeat Phishing Scams
Technical setups are only half the battle in securing your email. The other half is purely human—learning to spot the psychological tricks designed to make you act without thinking. Phishing attacks have evolved far beyond the goofy, typo-ridden emails of the past. Today's scams are slick, sophisticated, and built to exploit your trust.
There's a reason phishing is still the number one threat in our inboxes: it works. The sheer volume is staggering. In 2025, an estimated 3.4 billion phishing emails are blasted out every single day. And thanks to new malicious tools, AI-driven phishing attempts have exploded by a mind-boggling 4,000% since 2022. These aren't just spam; they're convincing, personalized attacks that are harder than ever to catch. You can dig into the specifics of this trend by reading the full research on phishing statistics at DeepStrike.io.
With threats getting smarter, our defenses have to get smarter, too.
Deconstructing the Modern Phishing Attack
Modern phishing emails are engineered to slip right past your gut instincts. They do this by faking legitimacy and manufacturing a sense of urgency that forces you into making a snap decision.
Here's a common scenario I see all the time: an email lands in your inbox pretending to be from a service you trust, like Microsoft or your bank. It has all the right logos, the formatting looks professional, and the language is official. The message warns of a problem—a security alert, a billing error, a locked account—that demands you take action right now.
That's the trap. The attacker is counting on that spike of panic to make you click before you think.
The core goal of any phishing email is to make you act on emotion rather than logic. Scammers know that when you're worried or rushed, you're far more likely to miss the subtle red flags that expose their con.
The infographic below really drives home the difference in risk and cost between secure and insecure email, highlighting why stopping these attacks is so crucial.
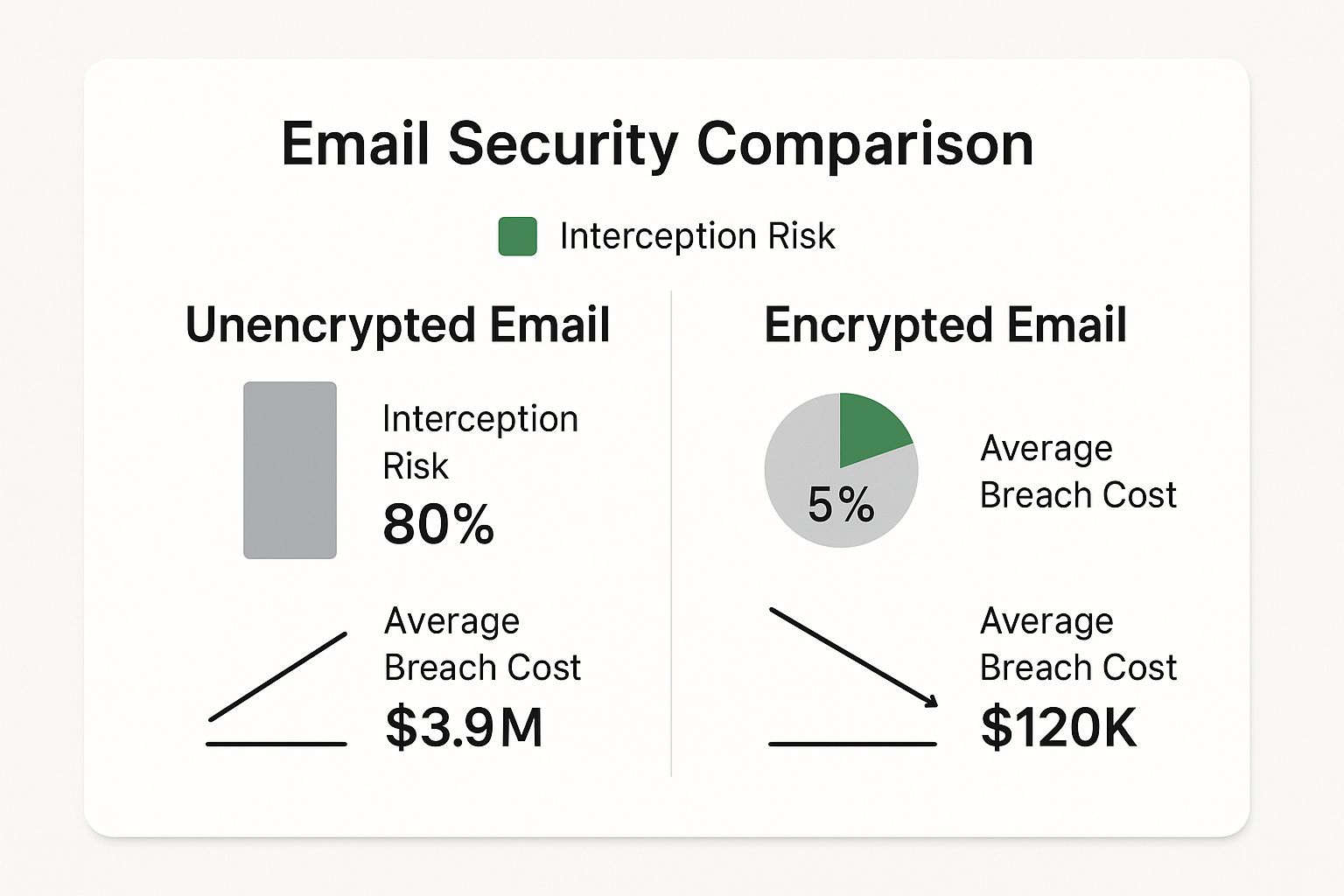
The data is clear. Encrypted, properly secured email dramatically cuts down both the chance of a successful attack and the financial damage if a breach does happen.
To help you distinguish between a genuine message and a malicious one, it’s helpful to know what to look for side-by-side.
Phishing Red Flags vs. Legitimate Communication
| Characteristic | Phishing Attempt Sign | Legitimate Email Sign |
|---|---|---|
| Sender's Address | A mismatched or complex email address that mimics a real one (e.g., paypal-support@mailru.com). |
The official domain of the company (e.g., support@paypal.com). |
| Greeting | A generic salutation like "Dear Valued Customer" or "Hello user." | Your actual name or username. |
| Urgency | Creates panic with threats of account closure, legal action, or immediate loss of funds. | Provides information and clear, non-threatening instructions with reasonable deadlines. |
| Links and URLs | Hovering over the link reveals a strange URL that doesn't match the company's official website. | The link destination clearly matches the company's domain. |
| Attachments | Unexpected attachments, especially ZIP files or documents that ask you to enable macros. | Attachments are expected, or the email explains exactly what the attachment is and why it's there. |
| Grammar/Spelling | Awkward phrasing, typos, or grammatical errors, though AI is making these less common. | Professionally written and proofread content. |
Seeing these signs in context is the key to building a strong defense against these manipulative tactics.
Evolving Threats: Quishing and Spear Phishing
Scammers never stand still. Two of the craftiest tactics gaining traction are "quishing" and AI-powered spear phishing. You need to have these on your radar.
- Quishing (QR Code Phishing): Instead of a sketchy link, the email contains a QR code. Many security scanners are built to inspect text and links, not images, so these can sneak past automated defenses. You scan the code with your phone, and it takes you straight to a fake login page.
- AI-Powered Spear Phishing: This is where it gets personal. Scammers use AI to scrape your public data from LinkedIn, company websites, and social media. They then build a highly targeted email that might reference your boss, a recent project, or even a conference you attended, making it incredibly believable.
These hyper-personalized attacks are tough to spot. For a deeper dive into real-world examples and what to do, check out our guide on how to identify phishing emails with expert tips.
Your Practical Phishing Detection Checklist
When an email lands and something just feels off, stop. Trust that feeling. It's your built-in alarm system. Run through this quick mental checklist before you do anything else.
-
Examine the full sender address. Don't just glance at the name. Hover your mouse over the "From" field to see the real email address behind it. An official alert from Microsoft is never going to come from
microsoft.security@notice-123.net. -
Inspect links before you click. Let your mouse hover over any button or hyperlink. The true destination URL will pop up in the corner of your screen. If that URL looks weird or doesn't match the supposed sender, don't go there.
-
Analyze the tone. Is the message trying to scare you? Is it demanding immediate action? Does it use a generic greeting like "Dear Sir/Madam" when the company usually uses your name? Those are classic phishing tells.
-
Question every unexpected attachment. Never open an attachment you didn't ask for, even if it looks like it's from someone you know. Their account could have been hacked.
-
Verify through a separate channel. If you get an email asking you to act on an account, don't use its links. Open a new browser tab, go directly to the company's official website by typing it in yourself, and log in there. Any real notifications will be waiting for you.
Making this checklist a habit is how you go from being a potential target to being an active defender of your own inbox.
Using Email Encryption for True Privacy
Think about the last email you sent. Did you imagine it as a sealed letter or more like an open postcard? It’s a useful analogy. Most standard email security today works a lot like a postcard. The message is protected while traveling between postal hubs (email servers), but anyone working at the hub could theoretically take a peek. This is what Transport Layer Security (TLS) does, and it’s the default for services like Gmail and Outlook.
TLS is crucial, don’t get me wrong. It stops bad actors from snatching your email out of thin air as it flies across the internet. But the protection stops the moment your message lands on your provider's server. Your email host—be it Google or Microsoft—still has the technical ability to access and scan the contents of your messages.
The Shift to End-to-End Encryption
For genuine, undeniable privacy, you need to upgrade that postcard to a sealed letter written in a secret code that only your recipient can decipher. That's the essence of End-to-End Encryption (E2EE). With E2EE, your message gets locked up on your device before you hit send, and it can only be unlocked by the person it's intended for. Not even your email provider can read what’s inside.
A few years ago, this level of security felt out of reach for most people, reserved for spies and tech wizards. Thankfully, that's changed. E2EE is becoming much more user-friendly, putting real privacy within reach for anyone who needs to keep their communications under wraps.
The core idea behind E2EE is simple: only the sender and the recipient hold the keys to unlock the message. It effectively removes the email provider from your circle of trust, ensuring your conversations remain completely private.
This isn't just a "nice-to-have" in certain fields; it's an absolute necessity. For professionals in healthcare, finance, or law, handling sensitive client data without this level of protection is a major risk. For a deep dive into specific industry requirements, our guide on HIPAA compliant email encryption explains what's at stake.
Built-in Encryption Tools and Their Limits
The big email providers have noticed the growing demand for privacy and have rolled out their own "confidential" or "encrypted" modes. They're a step in the right direction, but it's vital to understand their limitations.
Gmail's Confidential Mode
This feature is pretty handy. It lets you set expiration dates on emails and blocks recipients from forwarding, copying, or printing your message. The catch? It is not true E2EE. Google still has access to the content. It’s more of a rights management tool that only works as long as the email stays within Google's system.
Outlook's Encrypt-Only
Microsoft's "Encrypt" option, powered by Office 365 Message Encryption, is a bit more robust. It restricts access to authenticated users, which is a good security layer. But just like Gmail's tool, it's not truly end-to-end. Microsoft manages the encryption keys, which means they maintain the technical ability to access the content.
These built-in options are great for preventing casual snooping or stopping someone from accidentally sharing sensitive info. But they don't deliver the absolute, verifiable privacy that some situations demand.
| Feature | Best For | Key Limitation |
|---|---|---|
| TLS Encryption | Everyday, non-sensitive emails | Provider can access message content on their servers. |
| Gmail Confidential Mode | Preventing forwarding/printing | Not true E2EE; Google retains access to content. |
| Outlook Encrypt-Only | Restricting access to authenticated users | Not true E2EE; Microsoft manages the encryption keys. |
| True E2EE | Highly sensitive data (legal, financial, health) | Requires a dedicated service or tool for absolute privacy. |
When to Demand Absolute Privacy with E2EE
So, how do you decide what’s good enough? The answer comes down to the sensitivity of the information you’re sending.
Let’s get practical. Think about these real-world scenarios:
- Financial Records: You're sending tax documents to your accountant, complete with your social security number and detailed financial history.
- Legal Matters: You're discussing a confidential case with your attorney, where maintaining attorney-client privilege is non-negotiable.
- Business Strategy: You're sharing proprietary trade secrets or M&A plans with fellow executives.
In any of these cases, the risk of a breach—whether from an outside attacker or unauthorized server-level access—is simply too high to ignore. This is where dedicated E2EE providers like Typewire or ProtonMail shine. These services are built on a "zero-access" architecture, meaning they are structurally incapable of accessing your data. Your privacy is guaranteed by design.
Another path is to add E2EE to your existing email client with tools that implement PGP (Pretty Good Privacy). It can be a bit more technical to set up, but PGP has been the gold standard for email encryption for decades. By taking this step, you're moving beyond basic security and embracing a framework of true digital confidentiality.
Securing the Devices and Apps You Use for Email

Let's be blunt: your email security is only as strong as its weakest link. More often than not, that weak link is the very device you’re using right now.
You can have the most complex password and the tightest encryption, but if your computer or phone is compromised, it's all for nothing. Attackers can simply bypass your defenses. This is why any real strategy for securing email must include hardening the hardware and software you rely on every day.
Think of it this way: a compromised device gives an attacker a front-row seat to your entire digital life. They can install a keylogger to steal your passwords, rifle through your files, and read your emails right off the screen. Your encryption becomes useless. It’s like having an unbreakable safe in your house but leaving the front door wide open so a burglar can walk in and watch you dial the combination.
This is a far more common attack vector than people realize. The moment you check your inbox on an out-of-date laptop or over sketchy public Wi-Fi, you’re rolling the dice with your most sensitive information.
Perform a Full Device Security Sweep
One of the most impactful things you can do right now is to run a full security sweep on your primary devices. This isn't a one-time fix; it's a critical habit that closes common security gaps before they can be exploited.
Start with the absolute basics: updates. Software updates aren't just for shiny new features. They are packed with security patches that fix vulnerabilities developers have found. In fact, one study found that nearly 60% of data breaches were linked to a known but unpatched vulnerability. Procrastinating on updates is like knowing your front door has a broken lock and just hoping for the best.
Here’s a straightforward checklist to get you started:
- Operating System: Make sure your Windows, macOS, Android, or iOS is set to update automatically. This is your device’s foundational defense.
- Browser and Extensions: Your browser is your main gateway to the web. Keep it updated and be ruthless—remove any extensions you don’t actively use or trust.
- Email Client: Whether you use the Outlook desktop app, Apple Mail, or something else, confirm it’s the latest version.
- Antivirus/Anti-Malware: Run a full scan with a reputable security program. Just as important, make sure its threat definitions are updated daily.
A common mistake I see is people focusing only on the operating system. Your browser and its extensions are just as critical. A forgotten, outdated browser extension can become a backdoor for an attacker to slip right through, completely bypassing all your other security efforts.
Audit and Revoke App Permissions
Over the years, you’ve probably granted dozens of apps and online services access to your email account. That old calendar app you tried once? That marketing tool you no longer use? They might still have full permission to read, and even send, email from your account.
Each one of those connections is a potential security risk—a dormant digital key just waiting to be misused.
It's time for an audit. Go into your Google, Microsoft, or Apple account's security settings and find the section labeled something like "Apps with access to your account." You will probably be surprised, and maybe a little alarmed, by what you find there.
As you go through the list, ask yourself these simple questions:
- Do I still actively use this service?
- Does this app really need access to my email?
- Do I even recognize this company?
If the answer to any of these is "no," revoke its access immediately. It only takes a few seconds per app, and it’s one of the most effective ways to shrink your attack surface.
Secure Your Network Connection
Finally, let's talk about the network you're using. Connecting to an unsecured public Wi-Fi at a café or airport can expose your traffic to anyone else on that network. While most email traffic is now encrypted in transit with TLS, a poorly configured network can still present serious risks.
At home, your Wi-Fi needs to be locked down. Use a strong, unique password—not the default one that came printed on the router. You also need to ensure you’re using WPA3 or WPA2 encryption, which are modern security standards.
This simple step prevents unauthorized users from hopping onto your network and snooping on your activity, adding another vital layer to your email security fortress.
Building Better Habits for Real-World Email Security
All the best security tech in the world can't save you from a single bad click. It’s a hard truth, but the person sitting at the keyboard—you—is the final line of defense. The most sophisticated encryption and authentication protocols are useless if your habits are weak.
This isn't just a hunch; it's a well-documented reality. Human error is consistently the weakest link in the chain. In fact, a 2025 analysis of over 1,100 security professionals found that a stunning 95% of all data breaches were caused by simple human mistakes, like sending an email to the wrong person. If you're curious about the details, Mimecast’s State of Human Risk report is an eye-opening read.
What this really means is that your mindset and daily actions are your most powerful security tools. Let's talk about how to sharpen them.
Shrink Your Digital Footprint
Think of every bit of personal information you share online as a breadcrumb for a potential attacker. Your birthday on Facebook, your job title on LinkedIn, your city on Twitter—scammers collect these details to craft spear-phishing emails that look frighteningly real.
Imagine an attacker knows your boss's name, the project you’re currently leading, and that you're on vacation next week. It becomes incredibly easy for them to write a convincing "urgent" request that tricks you into taking action.
An attacker's best weapon is information you give them for free. The less they know about you, the harder it is for them to build a believable scam. Treat your personal information like cash, because to a scammer, that's exactly what it is.
A little digital spring cleaning can make a huge difference. Go through your social media privacy settings and ask yourself, "Does this really need to be public?" The goal isn't to vanish from the internet, but to be deliberate about what you broadcast to the world.
Compartmentalize Your Email Addresses
Here’s one of the most effective habits I've ever adopted: stop using one email address for everything. I can't tell you how many times this simple strategy, known as email segmentation, has saved me from a major headache.
The logic is simple: if one account gets compromised, the damage is contained.
Here’s a practical setup I recommend to everyone:
- Primary Personal Email: Keep this one pristine. It's for close friends, family, and no one else. Never use it to sign up for a newsletter or an online account.
- Financial & Admin Email: Create a separate, secure address exclusively for banking, bills, taxes, and other sensitive correspondence. This one should be guarded just as closely.
- Public-Facing Email: This is your digital junk drawer. Use it for online shopping, forum sign-ups, newsletters, and any site that asks for an email but isn't critical to your life.
Now, if your public email gets spammed or shows up in a data breach notification, it's just a minor annoyance. Your truly important inboxes—the ones with your financial and personal data—are safe and sound.
Adopt a "Zero-Trust" Mindset
Finally, the most important habit is to cultivate a healthy sense of suspicion. "Zero-trust" sounds technical, but it just means you should treat every single email, link, and attachment as potentially hostile, no matter who it seems to be from.
Even an email from your closest colleague or family member could be a threat. Their account might have been hacked, with an attacker now using it to send malware to everyone in their address book.
I once got an email from a coworker with a familiar-looking invoice. The message was short and the tone felt just a little off. Instead of opening the attachment, I shot them a quick message on our company chat. Sure enough, their account had been compromised, and that "invoice" was ransomware. A two-second check prevented a disaster.
This is the mindset that acts as your ultimate shield. Before you click, always pause and ask yourself:
- Was I expecting this?
- Does this request seem normal?
- Can I verify this through another channel (like a text or phone call)?
Developing this instinct is one of the 8 email security best practices to implement now. When you start limiting what you share, segmenting your digital life, and approaching your inbox with a zero-trust attitude, you shift from being a target to being an active defender.
Frequently Asked Questions About Email Security
Diving into email security can feel a little overwhelming, and it's natural for questions to pop up as you start exploring the tools and concepts. I get asked about this stuff all the time, so let's clear up some of the most common points of confusion.
Is a VPN Enough to Secure My Email?
A Virtual Private Network (VPN) is a fantastic tool for privacy, but it doesn't actually secure your email messages. What a VPN does is encrypt your entire internet connection, which is great for hiding your online activity from your internet provider or protecting you from anyone snooping on a public Wi-Fi network.
But here’s the catch: it offers zero protection if your email provider itself gets hacked, or if you accidentally click on a phishing link.
I like to think of a VPN as an armored truck. It protects the journey from point A to point B, but it does nothing to protect the contents of the package once it’s been delivered. A VPN is a valuable layer in your security setup, but it’s not a complete solution on its own.
Can I Trust My Email Provider's Built-in Security?
For the most part, yes. Big players like Google and Microsoft have invested heavily in security. They have powerful spam filters and use TLS encryption to protect your emails as they travel between servers. For the average person, this is a solid baseline defense against a lot of common threats.
However, when you're dealing with truly sensitive information—think legal documents, financial details, or confidential business plans—that built-in security might not be enough.
The single most important step you can take to secure your email is to enable Multi-Factor Authentication (MFA or 2FA). Even if a scammer steals your password, they can't get into your account without that second piece of proof from your phone or a physical key. It is the most effective defense against unauthorized access.
If you need absolute confidentiality, you should look into a service that offers end-to-end encryption (E2EE), like Typewire or ProtonMail. With E2EE, not even your email provider can read your messages. Your conversations stay completely private, period.
How Often Should I Change My Password?
The old-school advice on this has completely changed. Forget the rule about changing your password every 90 days. That practice often backfires, leading people to create weak, predictable passwords (like Password123! followed by Password124!).
Modern security wisdom is all about creating a unique, strong passphrase for each important account and keeping them safe in a password manager. The only time you really need to change a password is if you have a specific reason to believe that account was compromised or if a service you use announces a data breach. In the world of passwords, strength and uniqueness always beat frequency.
Ready to take control of your email privacy? Typewire offers secure, private email hosting built on a foundation of zero-access encryption. Say goodbye to ads and data mining, and protect your communications with a platform designed for true security. Explore our plans and start your free 7-day trial.
How to Make Email Secure: Top Tips to Protect Your Account
Posted: 2025-07-20
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16