How to Send Secure Email That Stays Private

When you send a secure email, you’re essentially wrapping your message in a digital lockbox using encryption methods like PGP or S/MIME. This scrambles the content, making it gibberish to anyone except the person holding the unique key. Think of it less like a postcard and more like an armored truck delivery.
This guide will show you exactly why this is so important and how to put it into practice.
Why Your Standard Email Is Insecure

Here's a hard truth: most people think their email is private, but it's not. A standard email travels across the internet completely exposed, like a postcard anyone can read. It hops between multiple servers on its way to the recipient, and at any of those stops, it can be intercepted, copied, and stored.
This isn't just a theoretical vulnerability. This lack of built-in privacy opens the door to very real risks, especially since we now share so much sensitive information through email without a second thought.
The Real-World Risks of Unencrypted Communication
Sending an unencrypted email is like leaving your front door unlocked. You're exposing yourself to threats like "man-in-the-middle" attacks, where a cybercriminal slips between you and your recipient to steal data. Even your own email provider or ISP can access and analyze your conversations.
Let’s get specific. Here are a few common situations where unencrypted email is a disaster waiting to happen:
- Business Confidentiality: Imagine sending a draft of a merger agreement, sensitive financial projections, or a new product roadmap in a standard email. That’s a direct invitation for corporate espionage.
- Client Data: If you're a lawyer, accountant, or doctor, sending client information this way can lead to massive trust issues and even legal trouble for violating compliance standards like HIPAA.
- Personal Privacy: Sharing things like your social security number, bank account details, or private health records without encryption is practically handing the keys to an identity thief.
The heart of the problem is that email protocols were never built for the world we live in now. They were designed for simple delivery, not for privacy. Learning how to send secure email isn't just for tech geeks anymore—it's a basic skill everyone needs to protect themselves.
The Growing Need for Email Security
This vulnerability is made worse by the sheer volume of email we all send. Email is still king when it comes to communication. By 2025, the number of global email users is expected to hit 4.83 billion, with a mind-boggling 392 billion messages sent every single day. For hackers, this massive flow of data is a goldmine. You can find more statistics on the future of email at cloudhq.net.
The point isn't to scare you, but to be clear about the stakes. You wouldn’t shout your credit card number across a busy coffee shop, right? Sending it in a regular email is the digital equivalent.
The good news? Powerful and easy-to-use tools are available to lock down your messages. By adopting encryption, you take back control and make sure your private conversations stay private.
Understanding the Building Blocks of Email Encryption

Before you can send a truly secure email, you need to get familiar with the engines running under the hood. Email encryption isn't just one thing; it's a field built on established standards. The two you’ll encounter most are PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions).
From a bird's-eye view, both do the same job: they use a clever system of public and private keys to scramble your messages so only the intended recipient can read them. Your public key is like an open, secure dropbox that anyone can use to send you an encrypted file. But only you have the private key to unlock it.
While they share that core principle, their philosophies and how they operate are worlds apart. The right choice for you really boils down to your specific situation—who you are, who you're emailing, and what kind of security you actually need.
PGP: The Decentralized "Web of Trust"
PGP runs on a decentralized model known as the “web of trust.” In this world, there’s no single, central gatekeeper that issues keys or verifies your identity. Trust is built from the ground up, person by person. You create your own key pair, and its legitimacy grows as other people "sign" your public key, essentially vouching that it really belongs to you.
It's a lot like being new in town. You don't have an official certificate proving you're a trustworthy person. Instead, as you meet your neighbors and they get to know you, they vouch for you to others. This grassroots approach gives PGP incredible flexibility and makes it resistant to control by any single entity.
This model is a favorite among people who prioritize personal autonomy and privacy:
- Journalists use it to protect their sources from surveillance.
- Activists and dissidents depend on it to communicate safely, especially in restrictive environments.
- Privacy-focused individuals love it because it doesn't force them to register with or pay a third-party company.
The biggest hurdle with PGP, honestly, is key management. You're on your own when it comes to generating, storing, and verifying keys, which can feel daunting if you're not particularly tech-savvy.
S/MIME: The Centralized Certificate Authority
S/MIME is the polar opposite. It uses a centralized, top-down trust model. To get started with S/MIME, you need to get a digital certificate from a trusted Certificate Authority (CA). These are commercial companies, like DigiCert or Sectigo, that verify your identity before they issue your certificate, which includes your public key.
Think of it like getting a driver's license. A government body (the CA) confirms you are who you say you are and gives you an official ID (your certificate) that others can easily recognize and trust. When you receive an S/MIME encrypted email, your email client automatically checks the sender’s certificate against a built-in list of trusted CAs.
S/MIME shines in settings where verifiable identity is just as crucial as confidentiality. It offers a formal, structured approach to trust that plugs directly into existing corporate security policies.
This makes S/MIME the go-to standard for many organizations:
- Corporations often mandate it to comply with data protection regulations like GDPR or HIPAA.
- Government agencies use it to ensure the authenticity of official communications.
- Regulated fields like finance and healthcare frequently require it to meet strict compliance rules.
While S/MIME makes trust verification almost invisible to the end-user, it does mean you're dependent on CAs and often have to pay for a certificate. For a deeper dive into how these standards work, check out our essential guide to secure email protocols.
Choosing the Right Standard for You
So, which one is it? The choice between PGP and S/MIME really comes down to your context. An investigative journalist has fundamentally different security needs than a corporate lawyer. To help you figure out which path makes sense, I’ve put together a quick comparison.
PGP vs. S/MIME: A Quick Comparison
| Feature | PGP (Pretty Good Privacy) | S/MIME (Secure/Multipurpose Internet Mail Extensions) |
|---|---|---|
| Trust Model | Decentralized (Web of Trust) | Centralized (Certificate Authorities) |
| Key Generation | User-generated | Issued by a trusted CA after identity verification |
| Cost | Typically free (software is open-source) | Often requires purchasing a certificate from a CA |
| Ease of Use | Higher learning curve; manual key management | Simpler for end-users; often integrated into clients |
| Ideal User | Journalists, activists, privacy advocates | Corporations, government, regulated industries |
Ultimately, understanding these differences is the first real step in learning how to send secure email effectively. Once you know which system fits your world, you can move on to getting it set up.
A Hands-On Guide to Setting Up PGP Encryption
Getting started with PGP encryption can seem daunting, but I promise it's more straightforward than it sounds. We're going to skip the dense cryptographic theory and jump right into what you actually need to do to send truly secure emails.
For this walkthrough, we'll be using a popular and completely free combination: the Thunderbird email client and its built-in OpenPGP features. I often recommend this setup for beginners because it wraps powerful encryption tools into a familiar email interface, making the whole process far less intimidating.
Choosing Your PGP Tools
Your first real decision is picking the software to handle your encryption. There are quite a few options out there, but consistency is your friend. The smoothest path, especially when you're just starting, is to use an email client that either has PGP built-in or a well-supported plugin.
Here are a few trusted choices I've seen work well for people:
- Thunderbird with OpenPGP: A free, open-source email client that works on Windows, macOS, and Linux. Its native PGP support is hard to beat for ease of use.
- Gpg4win (Windows): This is a full encryption package for Windows users. It comes with Kleopatra for managing your keys and an Outlook plugin called GpgOL.
- GPG Suite (macOS): The go-to for many Mac users, this suite integrates nicely with Apple Mail for a seamless experience.
Since Thunderbird offers a consistent experience no matter your operating system, all the steps from here on out will be based on that.
Generating Your First Key Pair
Okay, you've got Thunderbird installed and your email account is set up. Now for the exciting part—creating your unique encryption keys. This is the moment you forge the digital "lock and key" for your private communications.
Inside Thunderbird, head over to your Account Settings and look for the "End-to-End Encryption" tab. You should see an option to add a new key. The client will guide you through the process, but you'll need to confirm a few things:
- Identity: Make sure the correct email address is selected for this key.
- Key Type: Just stick with the recommended defaults here. That usually means an RSA key of at least 3072 or 4096 bits. A bigger number means it's exponentially harder for anyone to crack.
- Expiration Date: Setting your key to expire in a year or two is just good security hygiene. It's a built-in reminder to cycle your keys, which limits your risk if a key ever gets compromised. You can always push this date back later.
Don't worry, Thunderbird handles all the complex math behind the scenes.
The single most important part of this whole process is creating a strong passphrase. This is not your email password. Think of it as a separate, ultra-strong password that protects your private key file itself. If someone gets on your computer, this passphrase is the last line of defense stopping them from impersonating you.
The infographic below really helps visualize the basic flow of what you do with your new keys.
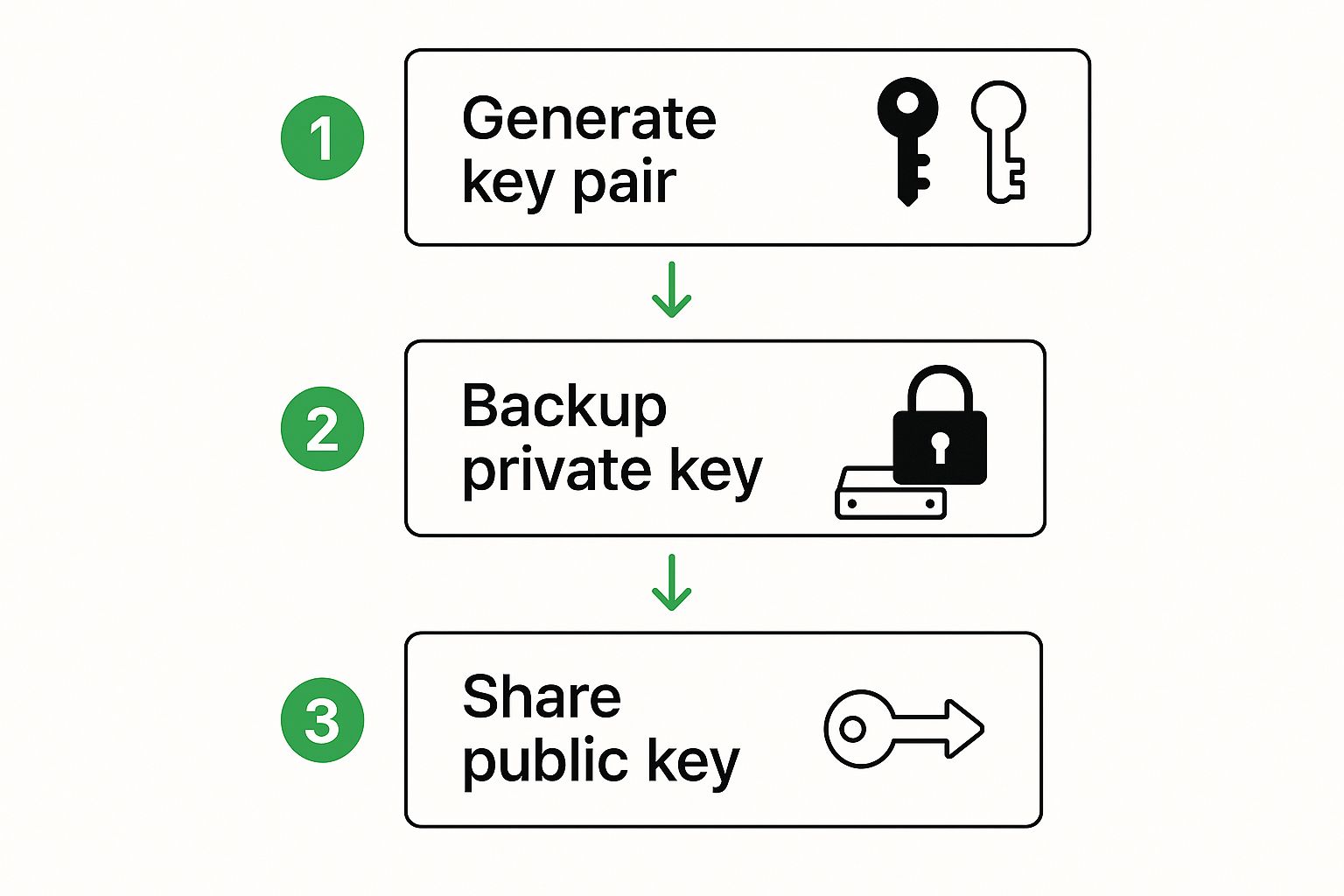
As you can see, once the keys are generated, your job boils down to two things: protecting your private key and sharing your public one.
Sharing and Managing Your Keys
Here's a core concept to remember: encryption is a team sport. For you to send someone a secure email, you need their public key. And for them to reply securely, they need yours. This is where key management becomes a simple, everyday habit.
Getting Your Public Key Out There
You need to make it easy for people to find your public key. Inside Thunderbird's key manager, you can export your public key into a small text file (it'll have a name like my-key.asc). You can then attach this file to an email, send it to your contacts, or even post it on your website.
Importing Your Contact's Public Key
When someone sends you their public key file, you need to add it to your keychain. It's usually as simple as opening the file and letting Thunderbird import it. Once you do, the client automatically links that key to your contact's email address.
From that moment on, whenever you start writing a new email to that person, Thunderbird will find their key and give you an option to encrypt the message with a single click. Watching it all come together is what really drives home the top benefits of encrypted email; it turns an abstract security idea into a real, practical tool you can use every day.
Implementing S/MIME for Professional Security

While PGP is a powerful tool for decentralized security, the professional world often marches to a different beat. For anyone working in corporate, government, or regulated fields like finance and healthcare, S/MIME (Secure/Multipurpose Internet Mail Extensions) is the gold standard.
What makes it so different? Its strength is its centralized, verifiable trust model—something that’s absolutely essential for meeting strict compliance rules and organizational security policies.
Unlike PGP's web of trust between individuals, S/MIME uses a top-down system built on Certificate Authorities (CAs). These are trusted third-party companies that formally verify your identity before issuing you a digital certificate. This certificate is your email's passport, proving to every recipient that you are who you claim to be.
This formal verification is precisely why businesses rely on it. It takes the guesswork out of authentication, which is critical when you're handling sensitive client data, intellectual property, or legally binding agreements. For professionals, understanding how to send secure email with S/MIME isn’t just a good idea; it's often a requirement.
Obtaining Your S/MIME Certificate
Your first step is getting an S/MIME certificate from a recognized Certificate Authority. This isn't a file you generate yourself—you have to apply for it, much like getting an official ID. You'll find plenty of providers out there, from big names to smaller specialists.
When you start looking, you'll see two main tiers of certificates:
-
Free Certificates: Some CAs offer free, basic certificates that are perfect for personal use or just trying things out. They typically provide encryption and last for a shorter period (like 90 days), with verification usually limited to confirming you own the email address.
-
Paid Certificates: For any serious business use, a paid certificate is the way to go. These involve a much more thorough validation process where the CA confirms your personal or organizational identity. They also last longer (usually one to three years) and are widely trusted by email clients, which means fewer compatibility headaches.
From my experience, investing in a paid certificate for business is a no-brainer. The cost is negligible compared to the assurance it provides, and it sends a clear message to clients and partners that you take their security seriously.
Installing and Configuring Your Certificate
Once the CA has verified your identity and sent you the certificate—usually as a .p12 or .pfx file—it's time to install it. The good news is that most major email clients, including Microsoft Outlook and Apple Mail, have great built-in support for S/MIME.
Installation is usually a breeze. In most cases, you just double-click the certificate file, and your operating system's keychain or certificate manager will walk you through the process. You'll need to enter the password you set up when you first exported the certificate from the CA's website.
With the certificate installed, the final move is telling your email client to actually use it. This involves a quick trip to your email account's security settings.
For example, in Microsoft Outlook, the steps look like this:
- Navigate to
File > Options > Trust Center > Trust Center Settings. - Select
Email Securityfrom the left-hand menu. - Under the
Encrypted emailsection, you can select your new certificate for signing and encrypting messages.
Here, you can set your client to automatically digitally sign all outgoing messages. A digital signature doesn't hide your message content; instead, it acts like a tamper-proof seal, proving the email came from you and wasn’t altered along the way.
You can also set a default to encrypt all outgoing mail. But just remember, you can only send an encrypted email to someone if you have their public key. The magic of S/MIME is that this key exchange happens seamlessly. The very first time you get a signed email from a new contact, your email client automatically saves their certificate. From that point on, you can send them encrypted messages. It all happens in the background, making S/MIME surprisingly easy to use day-to-day once it's set up.
Easier Ways to Send Secure Email Every Day
While PGP and S/MIME are the gold standard for bulletproof security, let's be realistic—they can be a nightmare to set up. For most people, figuring out how to generate, manage, and share keys is a major roadblock. This complexity often leads to mistakes or, worse, just giving up on encryption entirely.
But what if you could have that same high-level security without all the technical headaches?
Thankfully, a new wave of secure email services has stepped up to solve this exact problem. These platforms are designed with a "security by default" philosophy, meaning all the heavy lifting of encryption happens behind the scenes. You get to send a truly secure email with the same simplicity as using any popular webmail service.
The New Breed of Simplified Secure Email
Modern platforms like Typewire present a fantastic alternative. They deliver end-to-end encryption without forcing you to become a cryptography whiz. The whole experience is built for real people, hiding the complicated mechanics so you can focus on what you’re writing, not how it’s being secured.
The secret sauce is automated key management. When you sign up, the service generates and handles your cryptographic keys for you. When you send a message to another user on the platform, encryption and decryption just happen. It’s seamless.
This approach offers some huge advantages for daily use:
- No Setup Required: Forget installing plugins, tweaking settings, or messing with key files. Just create an account and you're ready to go.
- Use It Anywhere: These services usually have clean web interfaces and dedicated mobile apps, so your secure email is always accessible, no matter the device.
- Modern Features: Many go beyond simple encryption, adding things like self-destructing messages, secure file transfers, and even the ability to recall an email after it’s been sent.
The point of these platforms isn’t to kill off PGP or S/MIME. It's to make powerful encryption available to everyone. After all, the most secure system in the world is useless if nobody can figure out how to use it.
Keeping Pace with the Modern Cloud Office
This trend toward user-friendly security isn't just for personal use. Businesses are also ditching clunky, old-school solutions. The email security market is changing fast, thanks to the massive shift to cloud services and the constant threat of sophisticated cyberattacks. With so many companies relying on cloud-native platforms like Microsoft 365 and Google Workspace, there's a clear demand for security tools that are just as flexible and easy to manage. You can read more about these market shifts and challenges.
This brings up a critical point: for a security tool to be successful, it has to fit into how people already work. Integrated solutions let companies enforce strong security policies without slowing everyone down—a balance that’s absolutely essential today. If you're looking to bring this kind of streamlined security into your own workflow, our guide can help you master safe communication in five steps.
At the end of the day, whether it’s for protecting your personal privacy or meeting professional compliance standards, you shouldn’t have to sacrifice convenience for security. By breaking down the technical barriers, these simpler tools empower more people to protect their conversations. The best way to learn how to send secure email is with a tool that makes it feel completely natural.
Common Questions About Sending Secure Email
Even with the best guides, jumping into email encryption for the first time can feel a bit daunting. It’s only natural to have questions when you’re dealing with things like PGP keys and S/MIME certificates.
Think of this section as a quick chat to clear up some of the most common things people wonder about. We’ll tackle the practical, "what-if" scenarios so you can get started with confidence.
What Happens If I Lose My Private Key?
Losing your private key is like losing the only key to a bank vault. It's a serious problem because you instantly lose the ability to read any email—past, present, or future—encrypted for you. This is why having a solid backup plan isn't just a suggestion; it's absolutely essential.
Here’s what you need to do before disaster strikes:
- Make a Secure Backup: As soon as you create your key pair, back up your private key. Don't just toss it in a cloud folder. Save it to an offline device, like a dedicated USB drive, and store that drive somewhere physically safe.
- Create a Revocation Certificate: When you first generate your PGP keys, your software will give you the option to create a revocation certificate. Do it. This is your emergency "kill switch."
- Know When to Use It: If you ever lose your private key or even suspect it's been compromised, you publish this certificate. It’s like putting out a public notice telling everyone, "Don't use my old key anymore!" This stops people from sending you emails you can no longer open and prevents a thief from using your key to impersonate you.
Can I Send an Encrypted Email to Someone Without Encryption?
The short answer is no, you can't send a fully end-to-end encrypted message to someone who isn’t set up for it. The whole system relies on you having their public key to "lock" the email. If they don't have one, you have no lockbox to put your message in.
But that doesn't mean you can't add a layer of security. You can still digitally sign the email.
A digital signature doesn’t hide the content of your email. Think of it more like a tamper-proof seal on an envelope. It provides cryptographic proof that the message genuinely came from you and hasn't been altered along the way. For true privacy where the message itself is unreadable, both you and your recipient need to be using encryption.
Is a Service Like Typewire Better Than a Manual PGP Setup?
This is a great question, and the honest answer is that it really depends on what you need and how hands-on you want to be. One isn't inherently "better" than the other; they're just built for different people.
Setting up PGP manually with tools like Thunderbird or GPG Suite gives you complete and total control. You manage everything yourself, you aren't tied to a third-party service, and you can even inspect the open-source code. This is often the path for journalists, activists, or anyone who requires maximum autonomy. The trade-off? It comes with a much steeper learning curve.
On the flip side, secure email services like Typewire are designed for ease of use. They handle all the complicated key management behind the scenes, making powerful encryption accessible to anyone. For most individuals and businesses, a dedicated service is simply the more practical and sustainable option. You get the robust security without all the manual work.
Does the Browser Lock Icon Mean My Email Is Secure?
That little lock icon you see in your browser's address bar next to Gmail or Outlook.com is important, but it doesn't mean your email message is secure.
The lock indicates an HTTPS connection. All it means is that the data traveling between your computer and that one email server (e.g., Google's) is encrypted. This is crucial for protecting your password when you log in, but that’s where the protection ends.
Once your email arrives at their server, it's typically stored unencrypted. When it's sent to your recipient, it travels across the internet to their provider's server, often in the clear. True email security—where only you and your recipient can read the message—requires end-to-end encryption like PGP, S/MIME, or a service that builds it in by default.
Ready to skip the complexity and start sending truly private emails today? Typewire offers end-to-end encryption with no complicated setup, no ads, and no data mining. Protect your communications with a platform designed for privacy from the ground up. Start your free 7-day trial of Typewire and take back control of your inbox.
How to Send Secure Email That Stays Private
Posted: 2025-07-11
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27