Sending a Secure Email: Protect Your Messages with Ease

Let's get one thing straight: your everyday email account is basically a postcard. Anyone who gets their hands on it, from your email provider to a snooping hacker, can read what's on it. If you want to send a truly secure email, you have two proven paths: use a dedicated secure email service or roll up your sleeves and set up your own encryption with tools like PGP or S/MIME.
So, What's Wrong With Regular Email?
Think about that last email you shot off. It felt private, right? Zipping from your screen to theirs in a flash. The reality is quite different. That message journeyed across the open internet as plain text, bouncing between various servers before it landed. At any of those stops, it was vulnerable.
This isn't just paranoid speculation. Unencrypted email is wide open to some very real threats:
- Public Wi-Fi Snooping: A hacker sitting at the next table in a coffee shop can easily capture unencrypted data, including your emails, from a public network.
- Provider Prying: Most big email providers, like Gmail and Outlook, have the technical means to scan the content of your emails. They often do this to target you with ads.
- Massive Data Breaches: When an email provider gets hacked, the entire contents of your inbox and sent messages can be stolen and leaked.
The Postcard Analogy Hits Home
Imagine jotting down your bank account details on the back of a postcard and tossing it into a public mailbox. You’re counting on the postal workers to be honest, but you know anyone handling that card—from the mail carrier to the folks at the sorting center—can take a peek. That's exactly how standard email operates. Your message is an open book as it passes through countless digital checkpoints.
The bottom line is, without encryption, you have zero expectation of real privacy. Sending a secure email is how you turn that open postcard into a locked metal briefcase that only you and your recipient have the key to.
It's no surprise that sophisticated cyberattacks are on the rise, with email being a prime target. This has driven huge growth in the security industry. In fact, the email security solutions market was valued at an estimated US$18.5 billion in 2024 and is expected to hit nearly US$24 billion by 2030. That alone shows you how seriously individuals and businesses are taking this. If you're curious, you can discover more insights on the email security market growth and see what's behind the numbers.
The Two Paths to Truly Secure Email
The good news is you have a couple of solid ways to lock down your communications. Both get you to the same destination—end-to-end encryption—but they take different routes.
- Secure Email Services: Think of platforms like Proton Mail or Tutanota. These services are built from the ground up for privacy, handling all the complex encryption work behind the scenes.
- DIY Encryption (PGP/S-MIME): This is the hands-on approach. You use established encryption standards with your current email client, like Thunderbird or Apple Mail, giving you complete control over your keys and the process.
Which one is right for you? It really comes down to your technical comfort level and what you need to protect.
Before you dive in, it helps to see how these two methods stack up. This table gives a quick overview to help you decide which approach fits you best.
Comparing Secure Email Methods at a Glance
| Feature | PGP/S-MIME (DIY Encryption) | Secure Email Service |
|---|---|---|
| Setup & Ease of Use | High technical skill needed. Requires manual key management. | Very easy. Sign up and go. Encryption is automatic. |
| Control | Full control over your encryption keys and software. | The provider manages the server-side infrastructure for you. |
| Recipient Experience | Your recipient must also use PGP/S-MIME to decrypt messages. | Seamless for users on the same service. May require a password for external recipients. |
| Best For | Tech-savvy users, journalists, activists needing maximum control. | Everyday users, businesses, and anyone wanting a simple "it just works" solution. |
Ultimately, both options are a massive leap forward from standard email. The DIY route offers unparalleled control if you have the know-how, while a secure service provides excellent, hassle-free protection for everyone else.
Choosing a Secure Email Service
When you start looking for a secure email service, it's easy to get lost in a sea of marketing claims. But what really matters? From my experience, it all comes down to two non-negotiable principles: end-to-end encryption (E2EE) and a zero-knowledge architecture. These aren't just fancy terms; they're the bedrock of genuine email privacy.
A provider with a zero-knowledge setup is, by design, incapable of reading your messages. The encryption happens on your device before an email ever leaves your outbox, and it's only decrypted on your recipient's device. This means the provider is just shuffling around scrambled, unreadable data. They don’t hold the keys, so they can’t unlock your content—not even if a government agency shows up with a court order.

This is a world away from mainstream email providers, where your messages might be encrypted on their way to the server, but are often stored in a way that the company can access.
How to Vet a Provider's Security Claims
So, as you compare popular services like Proton Mail or Tutanota, you need to look past the promises on their homepage. A trustworthy service is transparent about how it protects you. You’re looking for technical proof, not just pretty marketing copy.
Here’s a practical checklist I use when evaluating any service:
- End-to-End Encryption: Is it automatic for messages sent between users on the same platform? This should be the default setting, not a feature you have to hunt for.
- Zero-Knowledge Proof: Do they explicitly state they operate a zero-knowledge or zero-access system? This is their promise that they can’t decrypt your stored emails or contacts.
- Open-Source Code: Are their apps open source? This is a huge sign of confidence. It lets security experts from around the world poke and prod the code for weaknesses, which adds a powerful layer of public trust.
- Jurisdiction: Where is the company based? You'll want a provider headquartered in a country with strong privacy laws, like Switzerland or Germany, which offer much better legal protection.
- Custom Domain Support: To look professional, you'll want to use your own domain. If you're new to this, we have a complete guide on how to set up a custom email domain that walks you through it.
One of the biggest giveaways is the provider's business model. If the service is free and runs on ads, your data is the product. A genuinely secure service is almost always funded by subscriptions, which means their financial success is tied directly to protecting your privacy.
Matching a Service to Your Real-World Needs
The best service for you really depends on what you’re trying to protect. Shielding personal chats from prying eyes is one thing; meeting strict professional compliance standards is another entirely.
Think about these real-world situations:
- A journalist talking to a sensitive source: Here, anonymity and a proven track record are everything. The ideal choice is a service based in a privacy-first country with fully open-source code.
- A healthcare provider sending patient records: This falls under HIPAA regulations. The provider must be willing to sign a Business Associate Agreement (BAA) and offer features built for compliance.
- A small business discussing client strategy: A secure email service with custom domain support is perfect. It ensures all your strategic conversations are locked down while you maintain a professional brand.
Focus on the underlying tech and match the features to your specific use case. When you do that, you can pick a service with confidence, knowing it’s truly built to keep your communications private.
Taking Control with PGP Encryption
If you're someone who wants the final say over your digital privacy, relying on even the most secure email service can feel like a compromise. You're still using someone else's server, after all. For those who prefer a more hands-on approach where you hold all the keys, Pretty Good Privacy (PGP) has long been the gold standard.
While PGP has a reputation for being a bit intimidating, modern tools have made it far more approachable than it used to be.
The magic behind PGP is a concept called asymmetric encryption. It sounds complex, but the idea is simple: you create a "key pair" that works as a team.
- Public Key: You can share this key with anyone. Think of it as a public drop-box with a special slot. People can drop messages in, but only you have the key to open it.
- Private Key: This one is yours and yours alone. It's the secret key that unlocks any message that was locked using your public key. You need to guard this with your life.
This two-key system means that even if an email is intercepted, it's just a garbled mess of text to anyone without your private key. It’s like sending a locked briefcase—only the person you sent it to has the combination. If you want to get into the nitty-gritty of how it all works, our essential guide to secure email protocols breaks down the technical details of PGP and its cousin, S/MIME.
Getting Started with Thunderbird and OpenPGP
So, what’s the easiest way to jump in? I almost always recommend starting with the free email client Mozilla Thunderbird. A few years ago, you had to mess around with clunky third-party plugins, but now Thunderbird has OpenPGP functionality built right in. This is a game-changer.
The process is surprisingly straightforward. After installing Thunderbird and linking your regular email account, you just head into the settings. There, you'll find an "End-to-End Encryption" section where you can generate your first key pair.
The software will walk you through creating a strong passphrase (this is a password that protects your private key itself) and setting an expiration date for your key, which is just good security hygiene.
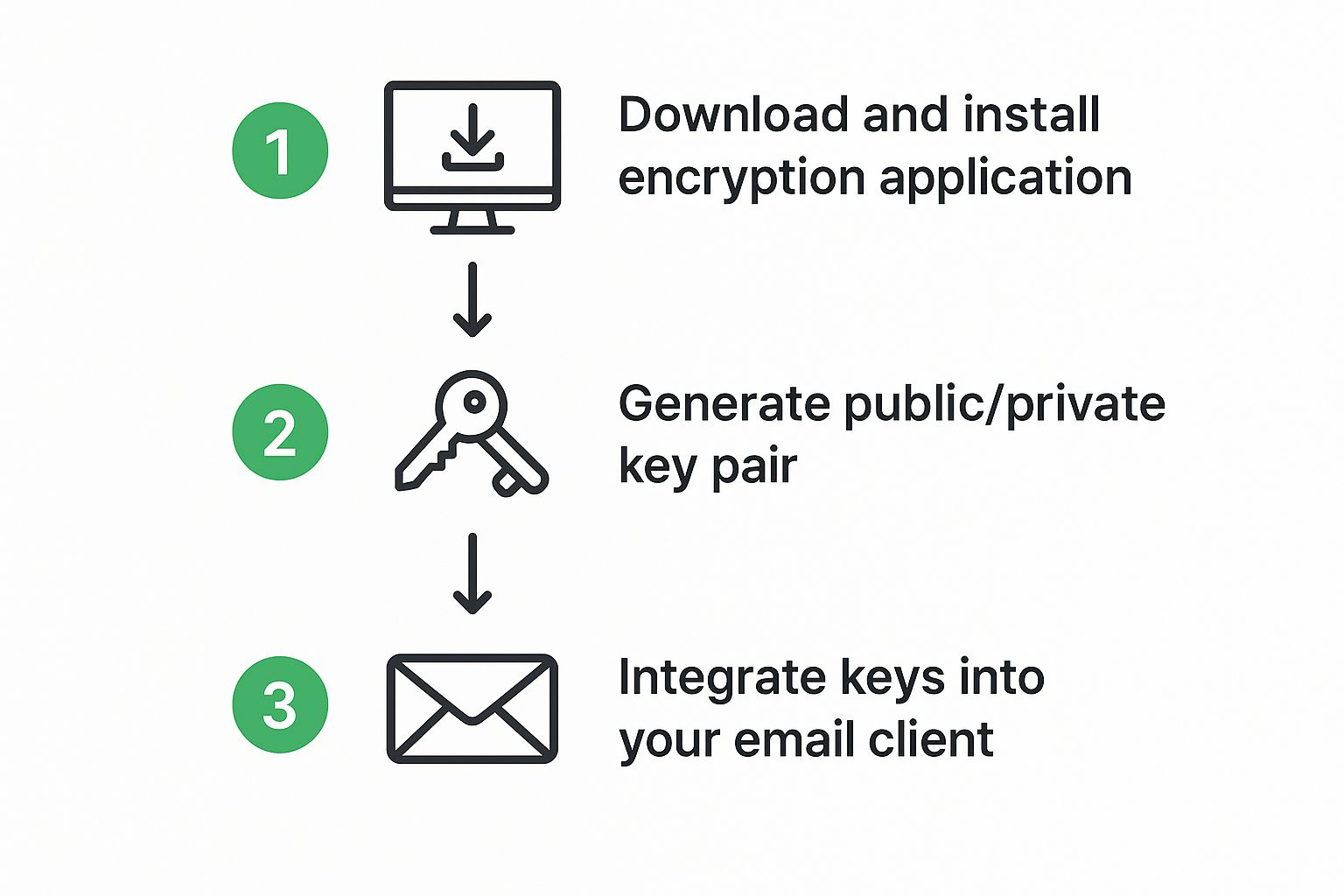
Once your keys are ready, you can export your public key as a small file and email it to your contacts. They'll need to import that key into their own PGP-enabled client. From then on, whenever they write an email to you, they can select your key to encrypt the message before it even leaves their outbox.
When the email arrives in your inbox, Thunderbird sees that it's encrypted. It will prompt you for your passphrase, use your private key to unlock the message, and display it as plain, readable text. It feels almost seamless once it's set up.
Essential Habits for PGP Users
Getting the software configured is just the first step. To use PGP effectively, you need to build a few key security habits. Simply having the keys isn't enough to guarantee you're communicating securely with the right person.
I've seen many newcomers make a critical mistake here: they don't verify key fingerprints. A "fingerprint" is a unique string of characters that acts like a serial number for a public key. After you get someone's public key, you absolutely must verify its fingerprint with them over a different channel—a phone call, a text, a video chat—to make sure a "man-in-the-middle" attacker didn't secretly swap their key with a fake one.
Here are two other habits you need to adopt from day one:
- Backup Your Private Key Securely. This is non-negotiable. If you lose your private key, you lose access to every single email encrypted for you with its public key. Forever. There is no "forgot my password" link. Make a backup and store it on an encrypted USB drive or in a secure password manager, completely separate from your main computer.
- Create a Revocation Certificate. When you first generate your key pair, you'll also have the option to create this special file. If your private key is ever lost or stolen, you can publish this certificate. It’s a public announcement telling everyone that your old key is compromised and should no longer be trusted.
By making these practices second nature, you move beyond just using a tool. You start taking true ownership of your communications, turning PGP into a powerful system for protecting what matters most.
How to Send Your First Encrypted Email
Alright, you've done the setup work by picking your tools. Now for the fun part: actually sending a secure message. Whether you opted for a dedicated service like Proton Mail or decided to go the PGP route with your own email client, the goal is the same—a message that only your recipient can read.
The process has a few subtle differences depending on the path you chose, so let's walk through what this looks like in practice.

This isn't just a technical drill. Think about it: global email use is expected to hit 4.83 billion users in 2025 and climb to a staggering 5.61 billion by 2030. That’s an unbelievable volume of digital conversations. Locking down your messages is a small step that contributes to a much safer digital world for everyone. If you're curious about the scale of it all, these email statistics and projections are genuinely eye-opening.
Composing on a Secure Email Service
If you signed up for a secure-by-design platform like Proton Mail or our own Typewire, the experience is incredibly smooth. Honestly, it's designed to be that way.
When you send a message to someone else on the same service, end-to-end encryption is almost always on by default. You just write your email, attach files, and hit send. The service handles all the complex encryption and decryption behind the scenes. It just works.
But what if your recipient uses a standard service like Gmail or Outlook? This is where these platforms get clever.
- First, you compose your message like usual, but this time you'll click an "Encrypt" or "Lock" icon.
- The system will then ask you to create a shared password for that specific message.
- You’ll need to send this password to your recipient through a completely separate channel—a quick text from a secure app or even a phone call works great.
Your contact will get an email with a link. When they click it, they’ll land on a secure web page where they can pop in the password to read your message. Simple.
Sending with PGP in Your Email Client
For those who went with PGP in a client like Thunderbird, the process is just as seamless once you're set up, though it does require you to be a bit more deliberate. You've already done the hard part: exchanging public keys with your contact and making sure their key is legitimate.
Now, when you write an email to them, you’ll notice some new security options in the compose window—usually a little lock icon or a dropdown menu. Before sending, all you have to do is make sure the "Encrypt" option is enabled. That’s it. Your email client grabs their public key, scrambles the message, and sends it on its way. On their end, their client uses their private key to unlock it automatically.
A Real-World Scenario: Imagine a journalist needing to share sensitive research with an anonymous source. Using PGP, the journalist encrypts the draft and attaches a protected document. The source receives it, decrypts it with their private key, and can reply securely, confident that the entire exchange is shielded from prying eyes.
What the Recipient Sees
A common question I get is, "What does the other person actually see?" Making it easy for them is half the battle.
| Your Method | Recipient's Experience | What You Need to Do |
|---|---|---|
| Secure Service (to non-user) | Gets an email with a secure link to view the message. | Share the message password with them out-of-band. |
| PGP/S-MIME | The message might look like a jumble of random text or an attachment called encrypted.asc. |
Make sure they have PGP software and your public key. |
| Secure Service (to user) | The message looks like any other email because it decrypts automatically. | Nothing! It's seamless. |
A little guidance goes a long way. I always recommend sending your contact a quick heads-up before you send your first encrypted message. Just letting them know what to expect can prevent any confusion and helps build their confidence in the process.
It's More Than Just Sending One Secure Email
You've done the hard part: setting up encryption and sending your first secure message. That’s a huge win. But real security isn’t a one-and-done deal. It’s a habit, a mindset you build over time to keep your private conversations truly private.
Think of it less as a technical chore and more as developing a new sense of awareness for your digital life. The tools are important, but your vigilance is what truly keeps you safe, especially when attackers get creative.

Ultimately, no amount of software can protect you from clever social engineering. That's where you, the human in the loop, become the most important part of the defense.
First, Double-Check Your Foundation
Before we get into the advanced stuff, let’s make sure the basics are locked down. These are the absolute non-negotiables for any secure email setup.
- Strong, Unique Passwords: Your email password needs to be a fortress. Don't reuse it anywhere else. I can't stress this enough—a good password manager is your best friend here. It handles the creation and storage so you don't have to.
- Multi-Factor Authentication (MFA): If you haven't turned this on for your email account, do it now. MFA is the single best thing you can do to protect your account, stopping a thief even if they manage to steal your password.
Getting these fundamentals right makes it exponentially harder for someone to break into your account, which is almost always the first step in a bigger attack.
Keeping Up With Today's Threats
To stay secure, you have to know what you’re up against. One of the most insidious threats out there right now is Business Email Compromise (BEC). It's a shockingly effective tactic where criminals pose as a boss or a trusted vendor to trick someone into sending money or sensitive files.
And it’s not a niche problem—BEC schemes made up a staggering 73% of all reported cyber incidents in 2024. With new rules like the EU's NIS2 Directive that can slap companies with fines up to €10 million for not reporting these attacks, the financial and legal risks are massive. You can see the full research on BEC attack trends to get a sense of the scale.
Here's a pro-tip I always follow: periodic re-verification. If you're using PGP, don't blindly trust a public key you downloaded ages ago. Before sending anything truly critical, re-verify the key’s fingerprint with your contact through another channel, like a quick phone call. It takes 30 seconds and can save you from a disaster.
Attackers are also getting smarter with their phishing emails. They'll send fake notifications from secure email providers, claiming your "encrypted message is waiting" and linking to a credential-stealing site. Knowing what these social engineering tricks look like is half the battle. To learn more, take a look at our guide on the complete defense against modern email security threats.
Common Questions About Secure Email
Once you’ve got a secure email system set up, you’ll probably find a few practical questions popping up. Answering these is key to using your tools with confidence and sidestepping common mistakes that could leave you exposed. Let's walk through some of the things people often ask after they start sending secure email.
A lot of the initial confusion comes from features offered by big email providers. It's easy to see something like Gmail's "Confidential Mode" and assume it’s the same thing as true end-to-end encryption.
Is Gmail's Confidential Mode Truly Secure?
In short, no—not in the way a privacy expert would define it. While Gmail's Confidential Mode is a handy tool to stop people from forwarding, copying, or printing a message, it does not use end-to-end encryption.
This is a critical distinction. It means Google can technically still access the content of those emails. For genuine privacy, you need a system where the email is encrypted on your device and can only be decrypted on your recipient's device. This is the entire point behind services like Proton Mail or a manual PGP setup.
Think of it this way: Confidential Mode is like adding a lock to a door but giving the building manager a master key. True end-to-end encryption means only you and your recipient have keys. No one else—not even the building manager—can get in.
What Is the Difference Between PGP and S/MIME?
Both PGP (Pretty Good Privacy) and S/MIME are long-standing protocols for email encryption, but they're built on completely different foundations of trust.
- PGP: This works on a decentralized model called the "web of trust." You and other users vouch for each other's identities by signing public keys. It's incredibly flexible and a favorite among journalists, activists, and privacy advocates.
- S/MIME: This relies on a top-down, centralized system of Certificate Authorities (CAs). It’s the same basic model that secures websites with SSL/TLS certificates and is more commonly found in corporate or government environments.
You'll often find S/MIME support built right into mail clients like Microsoft Outlook and Apple Mail. PGP, on the other hand, usually requires a plugin, though it's now seamlessly integrated into clients like Thunderbird.
If I Use a Secure Service, Does My Recipient Need One Too?
This is a classic question, and the answer is nuanced: it's best if they do, but it's not always required.
For the simplest, most secure communication, you and your recipient should ideally use the same end-to-end encrypted email service. The encryption happens automatically behind the scenes, ensuring total privacy.
But what if they don't? Most top-tier secure providers have a workaround. You can send a secure message to someone using a standard service like Gmail or Yahoo. Your recipient will get a notification with a link. When they click it, they’ll be prompted to enter a password (which you need to share with them separately, maybe over a Signal message or phone call) to view and reply to your message in a secure web portal.
Ready to take back control of your inbox with true end-to-end encryption and a zero-knowledge architecture? Typewire offers secure, private email hosting that puts you in charge. Say goodbye to ads, tracking, and data mining. Start your 7-day free trial of Typewire today and experience what real email privacy feels like.
Sending a Secure Email: Protect Your Messages with Ease
Posted: 2025-07-13
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31