Send Secure Emails: Master Safe Communication in 5 Steps

Why Your Current Email Isn't As Safe As You Think
Think about how you currently send emails. You compose your message, click send, and it's off, right? But have you ever considered the journey your email takes between those two points? Your message travels across multiple servers, potentially exposed like a postcard, vulnerable to prying eyes. This vulnerability is a significant concern, impacting both businesses and individuals every day.
Many email providers offer basic encryption, protecting your emails in transit between servers. Think of this as locking your front door but leaving your windows open. While this provides some level of security, it's insufficient. Once an email reaches the recipient's server, it might be stored unencrypted, leaving it susceptible to data breaches and unauthorized access.
Standard email also lacks strong authentication measures. This makes it surprisingly easy for cybercriminals to spoof email addresses, making messages appear as if they originate from a trusted source. This is a common tactic in phishing attacks, where attackers deceive recipients into revealing sensitive information such as passwords or credit card details.
This vulnerability fuels the rapid growth of the email security market. The global market, valued at $18.5 billion in 2024, is projected to reach $24 billion by 2030. Explore this topic further. This growth highlights increasing concerns about email security and the growing need for better protection.
The Real Cost of Insecure Email
The repercussions of insecure email can be severe, extending beyond the mere annoyance of spam. For businesses, data breaches can lead to substantial financial losses, regulatory penalties, and lasting reputational damage.
For individuals, compromised personal information can result in identity theft, financial fraud, and significant emotional distress. Relying on standard email for sensitive communication is like leaving valuable possessions unattended in a public space.
It's time to reassess your approach to email security and consider the options available for secure email communication. Protecting your communications and ensuring your privacy should be a priority.
The Foundation: Core Principles That Actually Work

Secure email relies on three core principles: confidentiality, integrity, and authentication. These principles work in concert to shield your messages from unauthorized access, ensure they arrive unaltered, and verify the sender's legitimacy. Understanding these fundamentals is the first step towards mastering secure email practices.
Confidentiality: Keeping Your Secrets Safe
Confidentiality guarantees that only intended recipients can access your email content. This is achieved through encryption, a process that transforms your message into an unreadable format. It's like placing your message in a secure vault, accessible only to those with the correct key. Encryption safeguards your sensitive information both in transit and during storage.
For instance, consider sending sensitive financial data via email. Without encryption, this information would be vulnerable to interception. With encryption, however, the message remains indecipherable to anyone lacking the decryption key. This principle is paramount for protecting sensitive data transmitted via email.
Integrity: Ensuring Your Message Arrives Intact
Integrity ensures that your email reaches its destination exactly as it was sent, free from any unauthorized changes. This is essential for preventing message tampering or alteration. Digital signatures, a form of cryptographic checksum, play a vital role in verifying message integrity.
Digital signatures act like a tamper-proof seal. Any attempt to modify the message will invalidate the signature, alerting the recipient to potential tampering. This safeguard is key for building trust and guaranteeing the reliability of information shared through email.
Authentication: Proving It's Really You
Authentication verifies the sender's identity, confirming that the email originated from the claimed source. This is crucial for preventing spoofing and phishing attacks, where malicious actors impersonate legitimate senders. Digital signatures contribute to authentication by linking the message to the sender's identity.
This digital fingerprint verifies the sender's authenticity, mitigating the risk of impersonation. Imagine receiving an email seemingly from your bank, requesting your password. Authentication helps determine if the message is genuinely from your bank or a fraudulent source. Unfortunately, research on email security trends in 2025 reveals a disparity between security awareness and practical implementation. While many understand the risks, implementing effective security measures isn't always prioritized. Therefore, strong email security demands the integration of all three principles – confidentiality, integrity, and authentication – to effectively safeguard your communications. By understanding these principles, you can make informed decisions about secure email practices and protect your sensitive information.
Business Email Compromise: The Threat Nobody Talks About
Secure email practices are foundational, but it's equally crucial to understand a pervasive threat that often circumvents traditional defenses: Business Email Compromise (BEC). This type of attack poses a significant risk to organizations of all sizes, and understanding its mechanics is paramount for implementing effective security measures. BEC attacks aren't about overpowering security systems; they're about exploiting human psychology.
Anatomy of a BEC Attack
Attackers often invest weeks studying their targets. They carefully analyze communication patterns, identify key personnel, and craft personalized messages designed to leverage trust. These messages often appear remarkably convincing, mirroring the language and style of legitimate business correspondence. This sophistication enables them to bypass spam filters and other conventional security tools.
For instance, an attacker might impersonate a CEO requesting an urgent wire transfer. The message might appear to originate from the CEO's actual email address, even referencing recent company events to enhance credibility. The request might seem perfectly reasonable within the context of regular business operations, making it difficult for employees to detect the deception. For more insights into identifying suspicious emails, check out this resource: How to Avoid Phishing Emails – Essential Security Tips.
Beyond the Financial Impact
The repercussions of BEC attacks extend beyond immediate financial losses. These attacks erode trust, tarnish reputations, and disrupt business operations. The recovery process can be protracted and complex, often requiring extensive investigations and remediation efforts. Furthermore, the psychological impact on victims can be significant, leading to feelings of guilt, anxiety, and reduced productivity.
The importance of secure email practices is underscored by the alarming prevalence of BEC attacks. In 2024, BEC accounted for 73% of all reported cyber incidents, emphasizing the critical need for robust security measures. Hoxhunt provides more detailed statistics on BEC. This stark reality necessitates a proactive approach to email security that transcends basic spam filtering and incorporates comprehensive strategies for defending against social engineering tactics.
Building Organizational Immunity
Protecting your organization from BEC requires a multi-pronged approach. Implementing strong authentication protocols, educating employees about social engineering techniques, and establishing clear procedures for verifying financial requests are vital first steps.
Additionally, fostering a culture of security awareness, where employees feel empowered to question suspicious emails, is essential for building organizational immunity. This proactive approach, coupled with robust technical safeguards, helps create a strong defense against the ever-evolving threat of BEC.

Encryption Made Simple: Finding What Works For You
So, you’re ready to send secure emails. But navigating the world of email encryption can feel daunting. This section simplifies the process, helping you choose the right encryption method for your needs. We'll cut through the technical jargon and focus on practical application, guiding you toward a solution that balances robust security with ease of use.
Understanding Your Encryption Options
There are several approaches to email encryption, each offering varying levels of protection and implementation complexity. Transport Layer Security (TLS) is a common method that protects your messages in transit. Think of it like sealing a letter in an envelope. It safeguards the message as it travels but doesn't guarantee privacy once it reaches the recipient's server. This is often sufficient for everyday communication but may not be enough for highly sensitive information.
End-to-end encryption (E2EE), on the other hand, provides the highest level of security. Imagine placing your message in a locked box that only the recipient has the key to open. Even your email provider cannot access the content. E2EE is essential when sharing confidential data. Popular E2EE options include PGP and S/MIME, as well as modern cloud-based solutions that offer user-friendly implementation.
Comparing Popular Secure Email Providers
Selecting the right secure email provider depends on your individual needs and priorities. Some providers prioritize ease of use, while others focus on advanced security features. The market is growing, with several strong contenders offering varying levels of service.
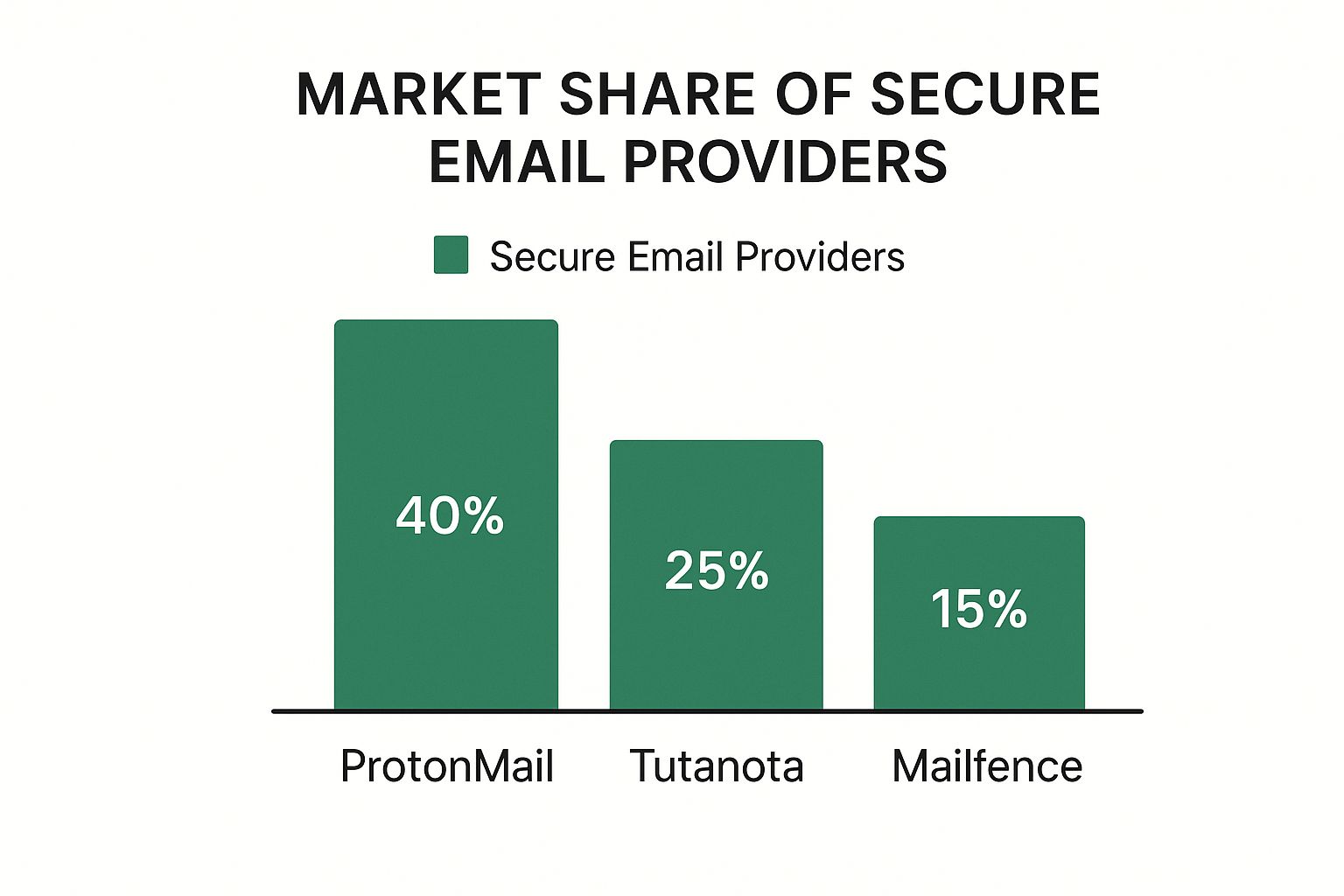
The infographic above shows the market share distribution among leading secure email providers. ProtonMail holds the largest share at 40%, followed by Tutanota at 25% and Mailfence at 15%. This data illustrates the increasing demand for secure email solutions and the diverse range of options available.
To help you understand the differences between common encryption methods, we've compiled the following comparison table.
Email Encryption Methods Comparison: A detailed comparison of different email encryption technologies, their security levels, ease of implementation, and best use cases.
| Encryption Method | Security Level | Implementation Complexity | Best Use Case | Key Management |
|---|---|---|---|---|
| TLS | Moderate | Simple | Everyday communication, newsletters | Automatic |
| E2EE (PGP) | High | Complex | Highly sensitive data, confidential communications | Manual |
| E2EE (S/MIME) | High | Complex | Business communications, legal documents | Manual, often centralized |
| Cloud-based E2EE | High | Simple | Secure file sharing, sensitive data storage | Automatic, managed by provider |
This table highlights the key differences in security levels and implementation complexity, helping you choose the method that best suits your technical skills and security needs. Cloud-based E2EE solutions offer a compelling balance of strong security and ease of use.
Finding The Right Balance
Choosing an email encryption method often involves balancing security with convenience. E2EE provides the strongest protection, but it can be more complex to set up than TLS. For casual business correspondence, TLS might be sufficient. However, when sharing sensitive documents or dealing with regulations like HIPAA, E2EE is essential.
Your technical expertise and available resources also play a role. Cloud-based E2EE solutions generally offer a simpler implementation than traditional methods like PGP and S/MIME, which require more technical configuration and manual key management. Ultimately, selecting the right encryption method involves understanding your specific needs, assessing the associated risks, and choosing a solution that balances security, usability, and implementation complexity. By carefully considering these factors, you can ensure your emails remain confidential and protected.
Choosing Your Secure Email Solution Without The Headaches
Tired of sifting through countless vendor claims and complex technical terms? Let's focus on the practical aspects of selecting a secure email solution that truly meets your needs. We'll concentrate on the most important criteria: seamless integration with your current systems, user-friendliness for your team, and the appropriate level of security for your specific circumstances.
Key Considerations For Secure Email
Selecting the right secure email platform requires careful consideration. Here are the key factors to evaluate:
-
Integration: How smoothly does the solution integrate with your current email system and workflow? A difficult integration can result in user frustration and reduced efficiency.
-
Usability: Can your team easily use the solution without extensive training or constant support from IT? Secure email shouldn't be overly complicated.
-
Security Level: Does the solution provide the right level of protection for your data and communications? Think about the kinds of information you handle regularly and the possible consequences of a security breach.
-
Budget: What's the overall cost, including licensing fees, implementation expenses, and ongoing maintenance? The priciest option isn't always the most suitable.
By carefully considering these factors, you can narrow your choices and select a solution that best aligns with your organization's specific requirements. This thoughtful approach ensures you're not merely purchasing software, but making a strategic investment in a solution that genuinely strengthens your security. You might be interested in: How to Send Email Securely: Your Complete Protection Guide.
Evaluating Popular Platforms
Many secure email platforms are available, each with its advantages and disadvantages. Instead of getting bogged down in a feature-by-feature comparison, concentrate on how effectively each platform fulfills your primary needs.
For instance, some solutions are exceptionally user-friendly, with intuitive interfaces and easy setup. Others emphasize advanced security features, such as end-to-end encryption and detailed access controls. The table below provides a concise comparison of how various providers might address your key considerations.
To help you make an informed decision, we've compiled a comparison table of leading secure email providers. This table highlights key features, allowing you to quickly compare and contrast different options.
Secure Email Solution Features Matrix
Comprehensive comparison of key features offered by leading secure email providers, including encryption standards, compliance support, and integration capabilities
| Provider | Encryption Standards | Compliance Features | Integration Options | Pricing Model |
|---|---|---|---|---|
| Provider A | Basic Encryption (e.g., TLS) | Limited Compliance (e.g., GDPR-ready) | Seamless with popular email clients (e.g., Outlook, Gmail) | Freemium/Subscription |
| Provider B | Advanced Encryption (e.g., End-to-End, PGP) | Extensive Compliance (e.g., HIPAA, GDPR, CCPA) | Requires dedicated client software or API integration | Subscription/Enterprise |
| Provider C | Strong Encryption (e.g., End-to-End, two-factor authentication) | Strong Compliance (e.g., GDPR, HIPAA compliant) | Cloud-based, accessible from anywhere | Subscription based on storage and user count |
This matrix reveals the potential trade-offs you might face. Provider A offers convenience but may have limited security features. Provider B offers robust security but might be challenging for non-technical users. Provider C aims to balance strong security with ease of use. The optimal choice hinges on your specific needs and technical resources.
Avoiding Implementation Pitfalls
Even the best secure email solution can fall short if not implemented effectively. Common issues include insufficient training, lack of user acceptance, and inadequate technical support. To prevent these problems, prioritize thorough user training and consistent communication. Clearly explain the reasons behind secure email practices, address user concerns, and foster a culture of security awareness.
Ensure your chosen solution integrates seamlessly with your current workflows. A complex implementation can hinder adoption and weaken your security efforts. Offer readily available technical assistance to resolve user problems quickly. By proactively addressing these challenges, you can guarantee a successful implementation that enhances your overall security. This forward-thinking approach sets you up for long-term success and helps you maximize the value of your chosen solution.
Making It Stick: Implementation That Actually Works

Implementing secure email practices isn't simply about selecting the right technology. It's about ensuring your team actively uses it. This involves a strategic approach that considers the human element of security. This section offers a practical roadmap for implementing changes that last, based on proven organizational successes.
Training That Caters to All
Generic, one-size-fits-all training rarely yields positive results. Your team members likely possess varying levels of technical proficiency. Some may be highly adept with technology, while others might require assistance with fundamental computer operations. Design training programs that accommodate these different comfort levels.
This means providing extra support for those less familiar with technology. This could involve hands-on workshops or individualized guidance. For example, a readily available quick reference guide or a series of short instructional videos on sending secure emails can greatly improve adoption rates.
Furthermore, consider offering a variety of learning formats. This allows individuals to choose the method that best suits their learning style. Some may prefer online tutorials, while others might find in-person sessions more beneficial. Offering these options ensures everyone can access effective training, promoting wider adoption and bolstering overall security.
Building Buy-In Across the Organization
Implementing change often encounters resistance. To address this, clearly communicate the reason for the change. Explain the risks associated with insecure email and the advantages of adopting secure practices. This fosters genuine buy-in and motivates employees to embrace new procedures.
Sharing real-world examples of security breaches can be highly impactful. Highlighting the potential consequences of a phishing attack, for example, resonates more powerfully than abstract security concepts. This approach encourages active participation in the security initiative.
Measuring Success Beyond Installation
Simply installing secure email software isn't enough. True success lies in consistent use. Measure adoption by monitoring key metrics. Track active users, the frequency of secure email usage, and the number of reported phishing attempts. This data offers valuable insights into how effectively your team utilizes the new tools.
Go beyond simple installation metrics. Focus on actual usage patterns. Regularly review these metrics to pinpoint areas for improvement. Adjust your approach as needed. This continuous evaluation ensures your security initiative remains effective and adapts to evolving requirements.
Practical Policies and Procedures
Develop clear, user-friendly policies and procedures for sending secure emails. These should encompass everything from selecting the right encryption method to reporting suspicious emails. Include practical templates for employees to use as a reference.
These documents should be more than just theoretical guidelines. They should be actionable resources that seamlessly integrate into daily workflows. By providing accessible and user-friendly resources, you foster a proactive security culture where best practices are consistently reinforced. This not only enhances security, but empowers employees to contribute actively to protecting the organization. By combining these efforts, your organization can go beyond simply installing security measures. It can cultivate a robust email security culture that effectively safeguards valuable information and mitigates risks.
Key Takeaways
Sending secure emails isn't a luxury anymore; it's a necessity. This section boils down essential strategies into actionable steps you can use right away. These takeaways concentrate on practical improvements that boost your security without getting in the way of your work. They offer a roadmap for building consistent, security-conscious email habits.
Prioritize End-to-End Encryption
The foundation of secure email is end-to-end encryption (E2EE). This method makes sure that only you and your recipient can read your messages. Unlike simpler encryption that only protects messages while they're being sent, E2EE protects your data even after it arrives in the recipient's inbox. This is vital for keeping sensitive information safe from data breaches and unauthorized access.
-
Choose the Right Method: Pick an E2EE method that balances security with ease of use. Cloud-based E2EE solutions can be more user-friendly than complex options like PGP and S/MIME.
-
Implementation Timeline: Start by using E2EE for your most sensitive communications. Gradually increase its use as your team becomes more comfortable.
-
Success Metric: Keep track of the percentage of sensitive emails sent using E2EE. The goal should be 100% encryption for all confidential correspondence.
Recognize and Avoid BEC Attacks
Business Email Compromise (BEC) attacks pose a serious threat, often getting around traditional security. These attacks rely on social engineering, tricking people into giving up sensitive information or authorizing fraudulent transactions.
-
Education is Key: Train your team to spot the red flags of BEC attacks. These include unusual requests, urgent demands, or anything that doesn't look right about the sender's information.
-
Implementation Timeline: Make security awareness training mandatory for all employees. Regular refreshers will keep security top-of-mind.
-
Success Metric: Monitor the number of phishing and suspicious email reports. Fewer reports can indicate better awareness and training effectiveness.
Choose the Right Secure Email Provider
Picking the right secure email provider is key for long-term success. Think about these factors:
-
Seamless Integration: The solution should integrate easily with your current email setup and workflows.
-
User-Friendliness: Choose a provider that is easy for your team to use effectively without constant IT help.
-
Appropriate Security: The solution's security level needs to match the sensitivity of your data and communication needs.
-
Implementation Timeline: Research different providers. Run a pilot test with a small group before rolling it out company-wide.
-
Success Metric: Keep an eye on user feedback and adoption rates. High adoption and positive feedback point to a successful rollout.
Foster a Culture of Security
Technology isn't enough on its own. A strong security culture requires everyone in your organization to actively participate.
-
Empower Your Team: Encourage employees to question suspicious emails and report anything that seems like a potential threat.
-
Provide Clear Guidelines: Set up clear, easy-to-follow rules for sending secure emails and handling sensitive information.
-
Implementation Timeline: Start by explaining the importance of email security to everyone. Regular security awareness campaigns and reminders will reinforce best practices.
-
Success Metric: Check how engaged employees are with security protocols and track how many security incidents are proactively reported. More reports suggest increased awareness and a stronger security culture.
By putting these key takeaways into practice, you can change email security from a major challenge into a real advantage. Remember, effective security is an ongoing process. Start small, gain momentum, and focus on steady, thoughtful improvements.
Looking for a secure and private email platform that gives you control? Typewire offers robust security, custom domain hosting, and a user-friendly design, helping individuals and businesses protect their communications. Start your 7-day free trial today and see the difference: Typewire
Send Secure Emails: Master Safe Communication in 5 Steps
Posted: 2025-06-07
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16