Business Email Compromise Prevention: Your Complete Guide

The Hidden Reality Behind Today's BEC Threat Landscape

Business Email Compromise (BEC) attacks are no longer simple phishing scams. They have evolved into complex psychological operations designed to exploit the trust inherent in business relationships. This means traditional security awareness training often isn't enough. Instead of relying on easily detectable fake emails, attackers craft personalized messages that can bypass even expensive security systems.
The Psychology of Deception
These attacks are successful because they exploit human psychology. Attackers skillfully impersonate authority figures, creating a sense of urgency and taking advantage of established trust within organizations and with their vendors.
For example, an attacker might impersonate a CEO requesting an urgent wire transfer. They could also pose as a trusted supplier asking for a change in payment details. This type of manipulation can make even security-conscious employees vulnerable.
Attackers also frequently emphasize confidentiality. They instruct victims to avoid normal verification channels, further isolating them and increasing the likelihood of a successful attack.
The Rising Threat and its Impact
Understanding current trends is crucial for effective BEC prevention. One alarming trend is the increasing volume of these attacks. For more detailed statistics, see: Learn more about BEC Statistics.
As of early 2025, BEC attacks have seen a significant rise. There was a 13% increase in just the first three months of the year, and a staggering 60% increase between January and February 2025 alone. This highlights the urgent need for businesses to implement robust email security measures.
Companies of all sizes are at risk, and the potential financial and reputational damage can be devastating.
Beyond the Technical
While technical defenses like spam filters and antivirus software are important, the human element remains a critical vulnerability. Building a security-first culture is essential. Effective training must go beyond simply identifying phishing emails.
It must equip employees with the skills to recognize and resist the sophisticated psychological tactics employed in BEC attacks. This includes understanding how attackers use authority, urgency, and trust to manipulate their victims.
It also means empowering employees to question suspicious requests, even if they seem to come from a trusted source. By understanding the psychology behind these attacks, organizations can build a stronger defense against this evolving threat.
The True Cost of Getting It Wrong
Beyond the alarming headlines about Business Email Compromise (BEC), the true damage lies in the often-unseen costs that ripple through an organization long after the initial attack. These hidden costs can be far more devastating than the immediate financial loss, impacting everything from customer relationships to business continuity.
Financial Fallout: More Than Just the Stolen Funds
The immediate financial hit of a BEC attack is obvious. Money is transferred to fraudulent accounts, impacting cash flow and potentially jeopardizing projects.
However, the financial ramifications extend beyond the initial transfer. Consider the legal fees incurred investigating the attack, the costs of recovering funds (if possible), and potential regulatory fines for data breaches.
Additionally, factor in the operational downtime as systems are investigated and secured, impacting productivity and potentially revenue. Understanding these hidden costs is crucial for developing a comprehensive security strategy.
Reputational Damage: Eroding Trust
A successful BEC attack can severely damage an organization's reputation. Customers and partners may lose trust, fearing their data or funds are at risk.
This can lead to lost business, difficulty attracting new clients, and strained relationships with key stakeholders.
For example, a company that falls victim to a BEC attack impersonating a vendor might damage its relationship with that vendor, creating future logistical and financial challenges. Rebuilding trust after such an incident can be a long and arduous process.
Operational Disruption: The Ripple Effect
BEC attacks often significantly disrupt daily operations. Beyond the immediate investigation and recovery efforts, organizations may need to overhaul their security systems and processes.
This can be time-consuming and costly, diverting resources from core business activities. This means that even after the initial attack is contained, organizations can face ongoing disruptions to their workflows and projects.
The Impact on Small Businesses: A Disproportionate Threat
Smaller organizations are particularly vulnerable to the devastating effects of BEC. They often lack the resources of larger companies to invest in robust security measures and incident response capabilities.
This can make them easier targets for attackers and leave them with fewer options for recovery. For many small businesses, a single successful BEC attack can threaten their very existence.
Calculating Your Real Exposure
Understanding the full spectrum of potential costs associated with a BEC attack is crucial for effective business email compromise prevention. By calculating your organization's true exposure – encompassing financial, reputational, and operational risks – you can prioritize your prevention investments accordingly.
The average BEC wire transfer request was approximately $24,586 at the start of 2025, emphasizing the financial risk involved. Find more detailed statistics here. Attackers often use services like Gmail to spoof identities.
This proactive approach allows you to allocate resources effectively and focus on the measures that will provide the strongest defense against these costly and disruptive attacks.
Building Your Technical Defense Foundation
Technology is essential for preventing business email compromise (BEC). However, even the most advanced systems need proper configuration. This section explores key technical controls that have successfully thwarted BEC attempts in organizations similar to yours.
Email Authentication: Your First Line of Defense
Email authentication acts as a digital signature, verifying that emails genuinely come from your organization and haven't been altered. This involves three core protocols: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance). SPF specifies authorized mail servers for your domain, acting as a gatekeeper.
DKIM adds a cryptographic signature to outgoing emails, verifying authenticity. DMARC builds on SPF and DKIM, controlling how email providers handle messages that fail authentication. It sets the rules of engagement for your email security. Learn more about email security best practices in our article: How to master email security best practices.
The following infographic illustrates how these measures reduce BEC risk.
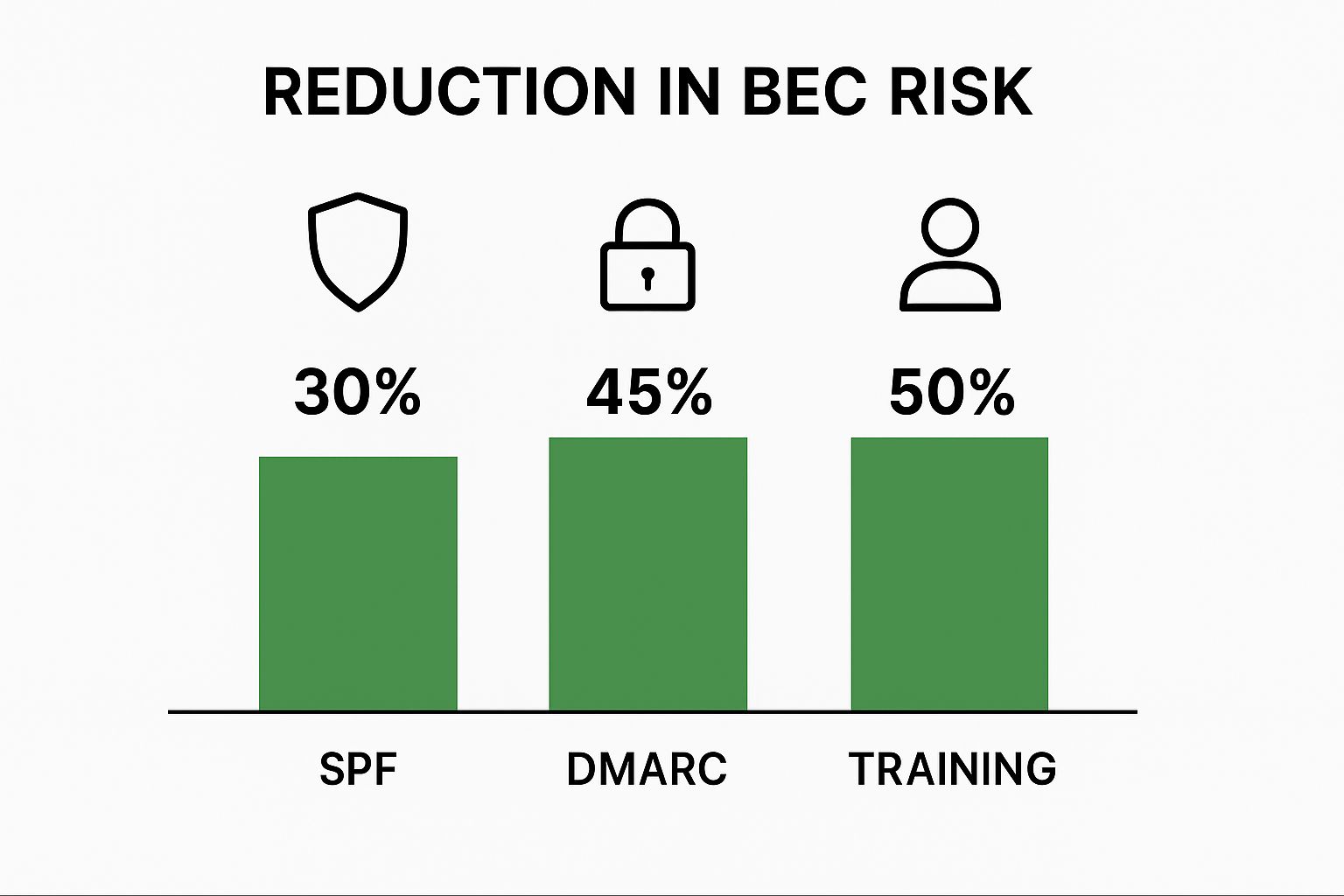
The data shows that while SPF and DMARC offer substantial protection (reducing risk by 30% and 45% respectively), employee training remains the most effective measure, reducing BEC risk by 50%. Combining technical defenses with a security-conscious culture is critical.
To further illustrate the differences between these email authentication protocols, refer to the table below:
Email Authentication Protocol Comparison: Comparing SPF, DKIM, and DMARC authentication methods with their specific benefits and implementation requirements.
| Protocol | Primary Function | Protection Level | Implementation Complexity |
|---|---|---|---|
| SPF | Designates authorized mail servers | Moderate (Reduces risk by ~30%) | Relatively simple |
| DKIM | Cryptographically signs emails | Moderate (Provides authentication beyond SPF) | Moderate |
| DMARC | Controls actions on unauthenticated emails | High (Reduces risk by ~45% when combined with SPF and DKIM) | More complex, requires careful planning |
This table summarizes the core functions and benefits of each protocol, highlighting the increasing complexity and protection offered as you move from SPF to DMARC. Implementing all three provides a layered defense, significantly reducing the risk of BEC.
Advanced Threat Detection: Beyond Basic Filtering
Standard spam filters often overlook the subtle cues of BEC attacks, which rely on social engineering rather than malicious content. Advanced threat detection systems using artificial intelligence and machine learning analyze email content, identify patterns, and flag potential BEC attempts.
These systems detect unusual sender behavior, requests for sensitive information, and language indicating urgency or pressure. This helps to identify and prevent BEC attacks before they succeed.
Automated Alerts and Secure Communication: Strengthening Your Response
Rapid response is crucial in addressing potential BEC attacks. Automated alerts can instantly notify your security team of suspicious activity, enabling swift action. This may involve blocking the sender, quarantining the email, or initiating manual review.
For sensitive transactions, consider secure communication channels like encrypted messaging or dedicated phone lines for extra protection. This helps ensure confidential information remains secure.
Monitoring and Continuous Improvement: Staying Ahead of the Curve
BEC tactics constantly evolve, requiring adaptable defenses. Monitoring systems tracking email traffic, flagging suspicious activities, and generating insightful reports on potential vulnerabilities are vital.
Use this information to refine security policies, enhance employee training, and stay ahead of threats. Regular security audits and vulnerability assessments help identify weaknesses and maintain effective defenses.
Creating A Security-First Culture That Actually Works

Your employees are your first line of defense against Business Email Compromise (BEC). They can be your strongest asset or your weakest link. This section explains how to build a security-conscious culture that empowers your workforce to become human firewalls.
Training That Transforms: Beyond the Basics
Generic security awareness training isn't enough to combat today's complex BEC attacks. Instead, focus on training that goes beyond simply identifying phishing emails.
Incorporate real-world examples and simulations that mirror actual BEC scenarios. This practical approach helps employees develop stronger threat recognition skills and reinforces best practices.
For example, use simulated phishing emails that incorporate authority impersonation, urgent requests, and requests for confidential information. This allows employees to practice identifying these tactics in a safe environment.
Training should also emphasize the psychological manipulation often used in BEC attacks. Teach employees to recognize how authority, urgency, and trust can be used as tools of manipulation. Empower them to question suspicious requests, even if they appear to come from a trusted source.
Escalation and Verification: Clear Procedures, Effective Action
Establish clear escalation procedures that are easy for employees to understand and follow. This ensures suspicious emails are reported promptly to the right people.
Implement verification protocols for financial transactions and sensitive information requests. These protocols should be practical for day-to-day operations, yet strong enough to stop fraudulent requests.
Multi-factor authentication, dual authorization for high-value transfers, and out-of-band verification are crucial components of a robust defense. For more information on protecting your business, check out this resource: Email security for small businesses.
Maintaining Momentum: Engagement and Adaptation
Security awareness isn't a one-time event; it's an ongoing process requiring continuous reinforcement. Keep employees engaged by regularly updating training content to address new and emerging threats.
Consider incorporating gamification and rewards to incentivize participation and knowledge retention. This can make learning more interactive and fun.
Regularly assess the effectiveness of your security awareness programs. Track reporting rates for suspicious emails and conduct periodic simulated phishing campaigns to measure employee vigilance. This provides valuable data on the program's impact.
Fostering a Culture of Security: Questioning Is Key
Create a work environment where questioning suspicious communications is encouraged and rewarded, not seen as paranoia or inefficiency. Encourage employees to speak up without fear of reprisal. This fosters a culture of shared responsibility for security.
By emphasizing open communication and proactive questioning, you transform your workforce into a powerful defense against BEC. This human firewall, combined with strong technical controls, creates a formidable barrier against even the most sophisticated BEC attacks. This proactive approach minimizes risk and protects your organization's valuable assets.
Verification Processes That Stop Fraud Dead

When technology and awareness training fall short, robust verification processes are your last line of defense against business email compromise (BEC). These processes act like a safety net, catching fraudulent requests before they impact your finances. This section explores proven verification methods used by organizations that have successfully thwarted BEC attacks.
Multi-Step Authorization: Adding Layers of Security
Multi-step authorization is similar to a combination lock. One number won't open it; you need the full sequence. Likewise, multi-step authorization requires multiple approvals for sensitive transactions, significantly hindering attackers. Even if one step is compromised, the others remain a barrier.
-
Dual Authorization: For high-value transactions, mandate approval from two separate individuals. This provides essential oversight.
-
Separation of Duties: The individual requesting a transaction shouldn't be the one who approves it. This avoids conflicts of interest and reinforces internal controls.
-
Tiered Approvals: Implement different approval levels based on the transaction amount. Smaller transactions may need one approval, while larger ones require multiple approvals from higher-level staff.
Out-of-Band Verification: Breaking the Attack Chain
Out-of-band verification confirms requests using a different communication channel than the initial request, vital for BEC prevention. Suppose you receive an email requesting a wire transfer. Instead of replying, call the sender directly using a known phone number to verify the request.
This tactic breaks the attack chain. Even if the attacker controls the email account, they likely don't control the phone line, significantly bolstering security.
-
Phone Calls: Use established phone numbers, never numbers provided in the email.
-
Text Messages: Verify requests through SMS messages to designated personnel.
-
Secure Messaging Apps: Utilize encrypted messaging platforms like Signal for sensitive information.
You may also find this helpful: Top 8 Anti-Phishing Programs to Protect Your Business for additional security tools.
Automated Workflows: Flagging Suspicious Activity
Automated workflows can streamline verifications and flag potentially fraudulent requests, efficiently processing legitimate transactions while maintaining robust fraud prevention.
-
Transaction Monitoring: Implement systems that automatically flag unusual transaction amounts, destinations, or frequencies.
-
Behavioral Analysis: Consider AI-powered tools that learn your organization's communication patterns and flag anomalies, which can help detect subtle BEC attack indicators.
-
Automated Alerts: Set up real-time alerts to notify security personnel of suspicious activity.
To understand the differences between verification methods, review the following table:
Introduction: The table below compares various transaction verification methods, highlighting their security levels, implementation time, and user impact.
| Verification Method | Security Level | Implementation Time | User Impact |
|---|---|---|---|
| Manual Review | Low | Short | Low |
| Dual Authorization | Medium | Short | Medium |
| Out-of-Band Verification | High | Medium | High |
| AI-Powered Behavioral Analysis | High | Long | Low |
Conclusion: While manual review offers a quick implementation, it lacks the robust security of other methods. AI-powered solutions provide high security with minimal user impact but require a longer implementation time. Out-of-band verification, although highly secure, can impact user experience due to additional steps. Choose the method that best balances security and operational efficiency for your organization.
Balancing Security and Efficiency: The Importance of Flexibility
Security should not impede legitimate business. Establish clear escalation procedures for urgent requests needing expedited processing, ensuring critical transactions aren't delayed.
Develop emergency procedures for overriding standard verification processes in exceptional circumstances, like natural disasters or system outages. These should be documented and monitored to prevent misuse. Maintain comprehensive audit trails of all transactions and approvals to support security investigations and meet compliance requirements. By balancing robust verification with practical flexibility, you can effectively mitigate BEC risks without disrupting operations.
The Evolution Of BEC Prevention Technology
The cybersecurity world is in constant flux, and Business Email Compromise (BEC) prevention is no different. As BEC attacks become more sophisticated, the demand for advanced security solutions rises. This has spurred the development of new tools specifically designed to combat this growing threat.
AI-Powered Email Analysis: A New Era of Defense
One major advancement in BEC prevention is the use of AI-powered email analysis. These systems use machine learning algorithms to analyze email content, identify suspicious patterns, and flag potential BEC attempts. They can detect unusual sender behavior, language that suggests urgency or pressure, and requests for sensitive information. Going beyond basic spam filtering, these systems analyze the context and content of emails to uncover subtle signs of a compromise.
Behavioral Monitoring: Learning Your Organization's Patterns
Another important innovation is behavioral monitoring. These platforms learn your organization’s typical communication patterns and flag anomalies that deviate from the norm. Because the system understands normal communication within your specific organization, threat detection becomes more accurate. This helps distinguish legitimate requests from potentially fraudulent ones.
This growing market is expected to expand significantly. The global market for Business Email Compromise prevention is projected to increase from $1.9 billion in 2024 to $4.34 billion by 2029. This highlights the increasing need for robust email security measures. You can find more detailed statistics here.
Evaluating and Integrating Security Solutions
When considering BEC prevention technology, carefully evaluate available solutions. Look for features like real-time threat intelligence, integration capabilities with existing systems, and customizable alert settings. Avoid relying solely on marketing and instead focus on honest assessments of effective solutions. Consider speaking directly with security vendors and their current clients for real-world feedback.
Integration is also a critical factor. Choose solutions that seamlessly integrate with your current email infrastructure and security systems. Smooth integration minimizes disruption to daily operations and maximizes efficiency, helping your organization stay ahead of the curve and protect your business against the evolving threat of BEC attacks. Ultimately, select technologies that align with your specific risk profile, budget, and operational needs.
Your Complete BEC Prevention Action Plan
Business Email Compromise (BEC) prevention isn't about single tactics; it's about a coordinated strategy tailored to your organization's specific needs. This means developing a practical, actionable plan that provides effective protection within your budget and resources.
Conducting Realistic Risk Assessments
Before implementing solutions, it's essential to understand your organization's vulnerabilities. This involves identifying key personnel who might be targeted, assessing the potential financial impact of a successful attack, and evaluating your current security measures. A thorough risk assessment forms the foundation of a strong prevention plan. It's like a building inspection: you need to identify weak points before reinforcing them.
Prioritizing Security Investments for Maximum Impact
Not all security investments offer the same return. Prioritize based on your risk assessment, focusing on areas with the highest potential for loss. For example, if your finance department handles large wire transfers, multi-factor authentication and dual authorization protocols become crucial. This targeted approach maximizes protection within your resource constraints.
Creating an Implementation Roadmap
A phased implementation roadmap is essential. Start with the most critical controls and gradually add layers of protection. This minimizes disruption and allows for continuous improvement. For instance, begin by implementing DMARC and then progress to advanced threat detection systems. This staged rollout is similar to building a house: you lay the foundation before adding walls and a roof.
Measuring Effectiveness and Maintaining Stakeholder Support
Regularly measure the effectiveness of your BEC prevention program. Track key metrics such as the number of reported suspicious emails, the success rate of simulated phishing campaigns, and response time to potential threats. Sharing these metrics with stakeholders demonstrates the value of your efforts and ensures continued support.
Adapting to the Evolving Threat Landscape
BEC tactics are constantly changing. Stay informed about emerging threats and adapt your strategy as needed. This might involve updating training materials, refining verification processes, or investing in new security technologies. Adaptability is crucial, like adjusting the sails on a ship as the wind shifts. For example, the increasing use of AI in crafting convincing phishing emails requires enhanced training focused on recognizing these advanced tactics. The rise of Vendor Email Compromise (VEC) attacks also underscores the need for stronger vendor verification procedures.
By adopting this comprehensive approach, you can build robust defenses against BEC, safeguarding your organization from financial loss, reputational damage, and operational disruption. Ready to enhance your email security? Start your free trial with Typewire today and experience private and secure email hosting: Secure Your Email with Typewire
Business Email Compromise Prevention: Your Complete Guide
Posted: 2025-05-29
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27