How to Protect Email From Hackers: Security Mastery Guide

Understanding the Email Threats Targeting You Daily

It's an unfortunate truth: your email inbox is under constant assault from various online attackers. Daily, numerous sophisticated threats, much more advanced than basic spam, attempt to get through your security measures. Recognizing these dangers is the essential first step in figuring out how to protect email from hackers and safeguard your online activities.
Why Your Email Is a Prime Target
Attackers don't just see your email as a way to communicate; they view it as a master key to your entire online world. Consider how your email is frequently connected to many other accounts, including banking, social media, cloud services, and online stores. If hackers gain access to your inbox, they can potentially:
- Change passwords for other important accounts.
- Collect personal details for identity fraud.
- Initiate attacks against people in your contact list.
- Access private business or personal files.
This web of connections makes your email account a very attractive prize for cybercriminals, pushing them to create even more clever attack strategies. As a result, the safety of your email is of utmost importance.
The Sophistication of Modern Email Attacks
The malicious emails arriving in your inbox today are often very different from the poorly written scam messages of the past. Phishing continues to be a major threat and is arguably the most common danger. Protecting email from hackers is vital because phishing is the most prevalent type of cybercrime, with an estimated 3.4 billion phishing emails sent every day. This represents about 1.2% of all global email traffic. In 2022, a significant 84% of organizations reported experiencing at least one phishing attempt, which was a 15% increase from the year before. Discover more phishing insights here.
However, phishing is not the only method attackers use. They frequently employ social engineering techniques, which involve manipulating people's psychology to trick them into revealing information or taking actions that weaken their security. These attackers create messages designed to provoke feelings like urgency, fear, curiosity, or even a desire to be helpful, exploiting natural human reactions to get past your logical defenses.
Recognizing the Subtle Signs of Deception
Telling the difference between real communications and cleverly disguised fakes can be difficult, as attackers are skilled at imitating legitimate companies and people. Even individuals who are careful about security can be tricked because these attacks are made to look genuine. Some common warning signs might include:
- Unexpected requests for private information.
- Small differences in sender email addresses or website domain names.
- Grammar or spelling mistakes, although more advanced attacks are often well-written.
- Pressure to take action right away.
- Links that, when you hover over them, show they lead to unfamiliar websites.
Developing a sharp eye for these details is crucial. You should approach every email with a sensible amount of caution. This foundational awareness will change how you see your inbox, helping you make smarter choices that greatly improve your email security. Knowing your adversary's methods is the first step toward defending your digital communications.
Building Your Email Security Foundation That Actually Works

Now that you're familiar with the common methods attackers employ, it's time to build a strong defense. Generic tips often don't provide enough protection, so let's look at practical strategies that genuinely strengthen your security when figuring out how to protect email from hackers. These are the types of solid measures cybersecurity experts use for their own accounts.
Creating Truly Robust Authentication Systems
The primary shield for your email is a solid authentication system, and this journey starts with your password. It's important to sidestep common errors like using easily guessed details or recycling passwords across different services. A strong password is generally lengthy, intricate, and created solely for your email account.
For example, instead of something simple like "Password123," consider a passphrase such as "BlueKitten!Jumped0verYellowMoon#". To handle these distinct credentials without feeling overwhelmed, think about using a reliable password manager. These applications securely keep your passwords and can create powerful, random ones for you, making this vital security step much simpler.
Implementing Multi-Factor Authentication That Works for You
Going beyond a strong password, Multi-Factor Authentication (MFA) introduces an essential additional security step. MFA demands that you supply two or more pieces of evidence to confirm your identity before granting access, which makes it significantly more difficult for unauthorized individuals to breach your account, even if they've obtained your password. Think of it as needing both a physical key and a secret code to unlock a vault; one alone won't suffice.
Many people perceive MFA as inconvenient, but it doesn't need to be. Most email services provide different MFA choices to suit your personal preferences and daily routine:
- Authenticator apps (like Google Authenticator or Authy) produce codes that are valid for a short time.
- Hardware security keys (for instance, a YubiKey) provide physical authentication when inserted into a port or tapped against a device.
- Biometric verification employs your fingerprint or facial scan for swift entry.
Select the method that gives you the best mix of security and ease of use. The small amount of time spent setting up MFA initially offers substantial protective benefits, acting as a strong barrier against intruders.
Cultivating Essential Security Habits
Technology by itself is not a complete solution; your personal practices are very important for your email security. People who maintain secure accounts often establish particular routines that become automatic:
- Regularly review account activity: Make it a habit to check for any logins from unfamiliar locations or unexpected modifications to your account settings.
- Be skeptical of unexpected attachments or links: Even if an email seems to be from someone you know, if anything seems unusual, confirm its legitimacy before clicking.
- Keep software updated: This applies to your computer's operating system, your web browser, and any email client software you use, ensuring that known security weaknesses are fixed.
- Log out of unused sessions: This is particularly vital when you access your email on computers that are shared or in public places.
These habits, when applied consistently, establish a proactive approach to security. For more detailed actions, you might find this resource useful: 8 Email Security Best Practices to Implement Now.
Evaluating Your Email Provider's Security
Not every email service gives you the same degree of defense. Spend some time looking into the security measures your current provider has in place. Do they have effective spam filters, encryption methods (like TLS for emails during transit), and transparent policies regarding data privacy and their response to security breaches? Understanding how to protect email from hackers well often begins with selecting a provider that genuinely puts your security and privacy first.
If your provider is missing key features, or if their business operations depend heavily on collecting user data (which can pose inherent privacy concerns), it could be time to look at other options. Seek out services that focus on privacy by design, open security measures, and give users strong control over their data. This forward-thinking stance is crucial; in fact, studies indicate that individuals who use thorough email security tactics, including strong authentication and frequent security checks, lower their risk of successful cyberattacks by 87% compared to those who only use the default protections from their provider. You can Explore this topic further in an email security effectiveness study.
Optimizing Overlooked Security Settings
Lastly, many email platforms include security settings that are frequently ignored but can greatly improve your protection with very little effort. Taking a few minutes to adjust these can create a significant improvement:
- Turning off automatic image loading in emails can stop tracking pixels and certain kinds of malicious code.
- Checking and removing access for third-party applications linked to your email account reduces possible weak points.
- Setting up account recovery options with care, making sure those recovery channels are also secure.
By methodically dealing with authentication, using MFA, developing good habits, choosing your provider carefully, and adjusting settings, you construct a layered defense system that is truly effective. This strategy is fundamental to keeping your email correspondence safe from increasingly skilled hackers.
Advanced Protection Strategies for Serious Security
While basic security steps are fundamental, achieving serious email protection means adding more developed tactics to your approach. For those dedicated to understanding how to protect email from hackers, these advanced strategies offer several strong layers of defense for your private communications, taking you beyond simple measures into professional-level security.
Implementing Robust Encryption for True Privacy
One of the most effective advanced methods is End-to-End Encryption (E2EE). Think of it like sending a physical letter in a unique envelope that only your intended recipient can unlock; E2EE functions in a similar way for your digital messages. This ensures that from the moment an email is sent until the recipient opens it, the content is scrambled and unreadable to anyone else, including email service providers or potential intruders. Putting E2EE into practice greatly improves the confidentiality of your communications. Services supporting E2EE often employ protocols like PGP (Pretty Good Privacy), with tools such as GnuPG (The GNU Privacy Guard) offering widely-used implementations, or they provide E2EE capabilities directly, turning your email into a secure repository.
Choosing Genuinely Secure Email Providers
When assessing email services for advanced security, it's important to look beyond advertising and concentrate on actual performance and verifiable security commitments. A truly secure provider will be open about its data handling procedures, encryption techniques, and how it protects against security breaches. For example, services like Typewire construct their platforms with privacy by design, meaning security is a foundational element, not an add-on. They often avoid third-party cloud services to maintain better control over data security. Look for providers that offer features such as E2EE support, operate on privately owned infrastructure, and clearly state they do not conduct data mining or ad tracking. This careful approach ensures your selected platform actively supports your goal of learning how to protect email from hackers.
Keeping software current is an essential, yet frequently overlooked, advanced security measure. The data presented below emphasizes the role of software updates in reducing security vulnerabilities.
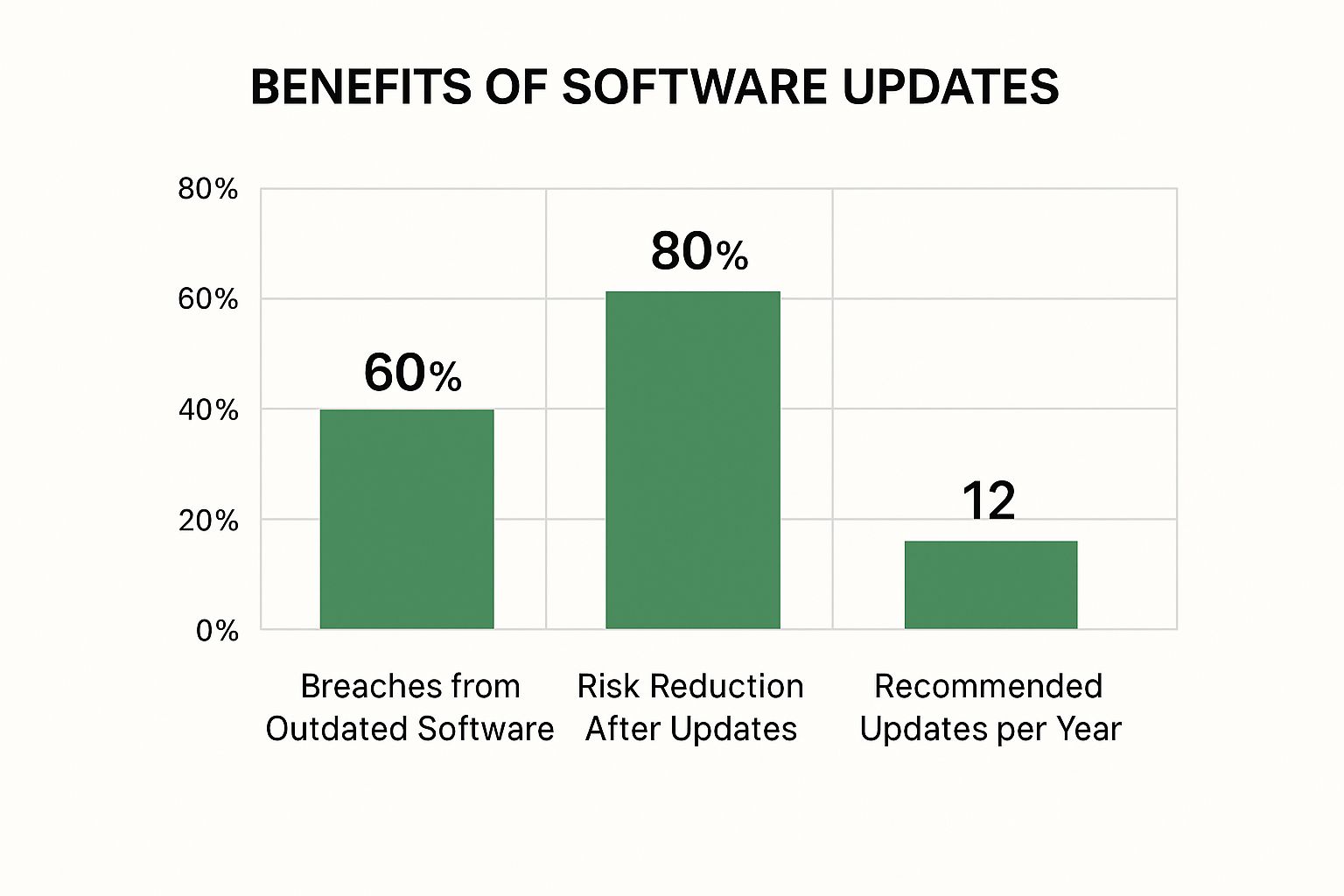
This graphic highlights a critical fact: a substantial 60% of security breaches originate from outdated software. However, merely keeping systems updated can decrease this risk by as much as 80%. The advice for at least 12 updates per year shows that staying alert in this area is a continuous, active defense strategy. This directly affects email security, as weaknesses in your operating system, browser, or email application can be targeted by attackers.
Employing Advanced Filtering and Monitoring Tools
Beyond typical spam filters, advanced protection includes using more refined filtering systems. These systems can detect and isolate complex threats such as spear phishing emails or messages carrying new types of malware that basic filters might overlook. Some email services provide options for custom filter rules or work with specialized security tools that examine email headers, sender credibility, and content more thoroughly.
Moreover, strong security monitoring tools offer vital insight into potential threats before they become major problems. These tools may include:
- Alerts for unusual login attempts or access from unfamiliar locations.
- Activity logs for accounts that can be checked for irregularities.
- Notifications if important account settings are changed.
Such features provide early warnings, enabling quick responses to secure your account. Regularly checking these logs and alerts is an important habit for maintaining a high standard of email security.
To help you understand how these different security methods stack up, here's a comparative overview.
Email Security Methods Comparison
A detailed comparison of different email security approaches, their effectiveness levels, implementation difficulty, and cost considerations.
| Security Method | Protection Level | Ease of Use | Cost | Best For |
|---|---|---|---|---|
| End-to-End Encryption (E2EE) | Very High (for content privacy) | Moderate (setup, recipient compatibility) | Varies (free tools to paid services) | Highly sensitive communications, privacy-focused individuals/organizations |
| Secure Email Providers | High | Varies (user-friendly to more complex E2EE) | Often subscription-based | Users prioritizing overall privacy and avoiding data mining |
| Regular Software Updates | Medium to High | Easy (often automated) | Free (included with software) | All users; fundamental security practice |
| Advanced Filtering & Monitoring | High | Moderate (setup, requires alert attention) | Varies (built-in or dedicated paid tools) | Businesses, individuals at higher risk of targeted attacks |
This table shows that while each method offers distinct benefits, a combination usually provides the strongest defense. E2EE offers top-tier content privacy, while secure providers offer a foundation of trust. Regular updates are a non-negotiable basic, and advanced filtering helps catch sophisticated attacks.
By integrating these advanced strategies—strong encryption, careful provider selection, consistent software updates, and refined filtering and monitoring—you establish a powerful defense system. This multi-layered tactic is key to effectively protecting your email from hackers in an environment of constantly changing threats.
Mastering Phishing Detection and Prevention

Phishing attacks are not merely frequent; they are constantly changing, often moving faster than our ability to spot them. These misleading efforts target human psychology, using clever manipulation that can fool even individuals who are typically careful about security. Understanding these approaches is key to learning how to protect email from hackers.
The Evolving Face of Phishing Attacks
Hackers are always improving their tactics, which makes phishing emails increasingly difficult to tell apart from genuine communications. Standard security awareness training, while helpful, often doesn't provide people with the specific skills needed to identify these more advanced deceptions. In fact, studies of successful phishing attacks indicate that 73% of victims had participated in security awareness training within the previous year. This highlights a clear need for more advanced detection methods beyond simple awareness. Explore this topic further to understand its implications for email security effectiveness. This striking statistic demonstrates that a more profound understanding and a more alert stance are vital.
Spotting The Subtle Red Flags
Telling a cleverly designed phishing email from a real one demands careful observation. Attackers try to take advantage of trust and create a sense of urgency, hoping you'll react before you consider the details. Here are common signs to watch for:
- Mismatched Sender Information: Closely examine the sender's email address. Phishers frequently use addresses that are slightly altered from legitimate ones (e.g.,
support@company-notice.cominstead ofsupport@company.com). - Suspicious Links and Attachments: Always hover your mouse over links before clicking to reveal the actual destination URL. Be cautious with unexpected attachments, especially if they come from unknown senders or if the context seems unusual.
- Urgent or Threatening Language: Phishing emails often aim to create a sense of panic, insisting on immediate action to prevent supposed negative outcomes.
- Generic Greetings: Although some phishing is highly personalized (spear phishing), many bulk phishing emails use general salutations like "Dear Customer."
- Poor Grammar and Spelling: While attackers are getting better, errors in language can still be a clue in less polished attempts.
For a more comprehensive guide on recognizing these deceptive messages, take a look at our article on How to Identify Phishing Emails: Expert Tips to Stay Safe.
To help clarify, here’s a comparison:
| Feature | Legitimate Email Clue | Phishing Email Warning Sign |
|---|---|---|
| Sender Address | Matches the official, recognized domain. | Subtle misspellings, or public domains (e.g., @gmail.com) for official communications. |
| Links | Lead to official websites; HTTPS is typically present. | Masked URLs, domains that don't match, non-HTTPS for login pages. |
| Tone & Language | Professional and appropriate for the context. | Urgent, threatening, overly emotional, or offers that seem too good to be true. |
| Requests | General information, expected types of interactions. | Direct requests for passwords, one-time passcodes (OTPs), or financial details. |
| Attachments | Expected, relevant file types from known senders. | Unexpected, unusual file types (like .exe, .scr) that could be harmful. |
Advanced Verification Without Alerting Attackers
Sometimes, an email might appear genuine enough to make you pause. In these situations, independent verification is your most effective protection. Instead of clicking links or calling numbers found in a suspicious email, go directly to the company's official website by typing the address into your browser or using a bookmark you've previously saved. Similarly, if you get an unexpected request from a colleague, confirm it through a different communication channel, such as a phone call or a direct message on a company-approved platform. This ensures you are interacting with the real entity, not an imposter, and doesn't alert a potential attacker that you are suspicious of their email.
What To Do When You Suspect an Attack
If you think you've received a phishing email, taking the correct actions is vital for your safety and the security of others. Knowing how to protect email from hackers involves having a proper response plan:
- Do not click any links or download attachments. This is the main method attackers use to deploy malware or steal your login information.
- Do not reply to the email. Responding can confirm that your email address is active and might lead to more focused attacks.
- Report the email. Use your email client’s reporting feature (often labeled "Report Phishing" or "Report Spam"). If it's a work-related email, follow your organization's specific reporting procedures.
- Delete the email from your inbox and then from your trash or deleted items folder after you've reported it.
Reporting phishing attempts helps email providers and security companies enhance their filters and safeguard others from similar attacks. Your alertness contributes to a more secure online environment for everyone. Continuous learning and a healthy degree of caution are your most powerful tools against the ongoing threat of phishing.
Conquering Spam and Malicious Content Effectively
The character of unwanted email has changed quite a bit. What used to be a simple nuisance in the form of spam has grown into a complex pathway for significant cyber threats. To effectively protect email from hackers, it's necessary for defense strategies to adjust to these new tactics. Current malicious efforts are quite skilled at hiding their dangerous purposes, which makes them more challenging to spot.
These efforts often involve creating emails that look authentic, allowing them to bypass standard, older filters. The massive amount of unwanted messages highlights this problem. For example, email spam continues to be a major risk to email security. In 2022, almost 48.63% of all emails sent worldwide were identified as spam. Although this number decreased from 51.02% in the first quarter to 46.16% by the fourth quarter of that year, it still shows the urgent need for strong spam filters and careful observation of email activity.
The rise in remote work has also worsened cybersecurity problems, with security breaches related to remote work costing companies an average of $173,074 more. You can find more detailed statistics about phishing and email threats. This continuous flood of messages means that sophisticated filtering systems are now a fundamental requirement.
Configuring Advanced Spam Filters
Basic email filters can catch plain spam, but they often miss more cleverly hidden malicious content. Advanced filtering systems provide a more detailed method, employing complex algorithms and current threat information to find and isolate harmful emails. Setting up these systems correctly is very important; the aim is to strongly block threats while avoiding the accidental capture of legitimate, essential messages.
This includes adjusting sensitivity settings and frequently checking quarantined emails. If you're looking to explore more options, check out our guide on The Top 8 Best Email Spam Filters to Protect Your Inbox in 2025. These tools frequently offer custom rules, whitelists, and blacklists, providing better management over your incoming mail.
Understanding Business Email Compromise (BEC)
A very sneaky type of malicious content comes through Business Email Compromise (BEC) attacks. These aren't your usual mass spam messages; BEC attacks are specifically aimed social engineering tactics. Attackers pretend to be executives or reliable vendors, writing believable emails that push employees to make fake wire transfers or share private company details.
Their success comes from their quiet approach and how they take advantage of human trust and feelings of urgency. Ways to detect BEC include:
- Verifying payment requests using a different communication method (like a phone call to a familiar number).
- Carefully checking email addresses for small changes that suggest someone is faking an identity.
- Teaching employees to spot the psychological tricks being used.
Putting strict internal rules in place for financial dealings can greatly reduce the danger of BEC.
Staying Ahead of Malicious Content Trends
The world of malicious email content is always shifting as attackers come up with new strategies. Keeping up with the latest developments, like new forms of malware or changing phishing methods, is vital for anyone wanting to understand how to protect email from hackers.
Luckily, high-quality tools and features are now more accessible to individual users, not just big companies. Many secure email services, such as Typewire, build advanced anti-spam and anti-virus protection right into their offerings. These often feature real-time threat assessment and automatic updates to their threat information, offering an active defense against new threats. This forward-thinking method for filtering and spotting threats is a key part of current email security.
Securing Mobile Email Access Without Sacrificing Convenience
Your smartphone is a key channel for email on the go, but it’s also a focus for attackers. You don’t have to choose between security and speed. Focusing on a few core features and habits shows you how to protect email from hackers without slowing your day.
Evaluating Mobile Email Apps For Real Security
Before you settle on an email app, check the actual safeguards it provides:
- End-to-End Encryption (E2EE): Only sender and recipient can read your messages.
- Local Data Encryption: Keeps cached emails scrambled on your device.
- Regular Security Updates: Patches emerging threats with each release.
A comparison of three popular options helps highlight the differences:
| App | E2EE Support | Biometric Unlock | Data Tracking |
|---|---|---|---|
| Typewire Mobile | Yes | Yes | No |
| Gmail Mobile | No | Yes | Yes |
| Outlook Mobile | No | Yes | Yes |
This table shows which clients match your security needs and privacy goals.
Implementing Device-Level Protections
Protecting your inbox starts on the device itself. Try these steps:
- Strong Screen Lock: Pick a longer PIN or passphrase over a 4-digit code.
- Automatic OS Updates: Allow patches to install as soon as they’re available.
- App Permissions Audit: Limit access to your email app to what’s essential.
Adopting these habits makes it harder for threats to reach your messages.
Securing Public Network Connections
Public Wi-Fi is a common attack vector. To stay safe:
- Always connect through a trusted VPN.
- Turn off auto-join for open hotspots to avoid unintentional connections.
These actions protect your credentials and content when you’re on the move.
Leveraging Remote Wipe And Secure Sync Features
If your phone is lost or stolen, you need quick response tools:
- Selective Remote Wipe: Erase only corporate or email data, not personal files.
- Encrypted Cloud Sync: Store your emails on zero-knowledge servers.
- Device Inventory Dashboard: View and revoke active sessions in one place.
With these features, you can lock down your account even if you can’t retrieve the device.
VPN Strategies That Work On The Go
A mobile VPN is more than an app—it’s your secure tunnel:
- Always-On Mode: Stops any network traffic outside the VPN.
- Split Tunneling: Routes only email traffic through the secure service.
- Kill Switch: Cuts the connection if the VPN fails.
Pair these VPN settings with a reliable client and device safeguards for a balanced setup that supports both security and convenience.
Studies show that 68% of successful email-based attacks start on mobile, and users are 3.2× more likely to fall for phishing on their phones than on desktops. Read the full research here.
These measures deliver a practical approach to protecting your email from hackers—strong enough to lock down your data yet flexible enough to keep your inbox at your fingertips.
Your Complete Email Security Implementation Plan
Moving from knowing about email threats to actively protecting against them means you need a clear, step-by-step strategy. This plan is designed to help you organize your approach, transforming information on how to protect email from hackers into a working security program that fits your specific situation. By systematically tackling important areas, you can develop and sustain strong email defenses.
Assessing Your Current Security Posture
Before you put new security measures in place, it's a good idea to figure out where you stand right now. Think about your specific risk profile: Are you often a target because of your job? Do you regularly work with very sensitive data? It's also important to assess your technical comfort level so you can pick solutions you're confident managing.
A straightforward self-check can tell you a lot. Ask yourself these questions:
- Is the password for my main email account unique and strong?
- Do I use Multi-Factor Authentication (MFA) whenever it's an option?
- When did I last look at my email account's connected applications and security settings?
- Am I sure I can identify clever phishing attempts?
Answering these questions truthfully will quickly show you where you need to make improvements. This first check-up is the foundation of your personal plan for how to protect email from hackers.
Prioritizing Your Security Measures
Once you have a better understanding of your current security, the next step is to decide which actions to take first. Not all security steps are equally effective, and some offer much better protection against common threats than others. Start with the basics that counter the most frequent risks, like making your login details stronger and turning on MFA. These are essential first lines of defense.
After that, focus on addressing the specific weak spots you found in your self-assessment. For example, if you often check your email using public Wi-Fi, getting a dependable VPN becomes more important. This focused method ensures you're tackling the areas with the biggest impact first.
Creating Your Implementation Timeline
To keep the process from becoming too much, it helps to divide your security upgrades into weekly objectives. A well-organized timeline can help you keep up the pace without feeling swamped. The following is a sample 4-week plan to help you get started. Remember to modify the time estimates based on how familiar you are with these actions.
To help you organize these steps, here's a detailed plan.
Email Security Implementation Timeline
A structured 30-day plan showing when to implement each security measure, priority levels, and expected time investment for each step.
| Week | Security Task | Priority Level | Time Required | Expected Outcome |
|---|---|---|---|---|
| 1 | Create unique, strong passwords for email; set up a password manager. | High | 1-2 hours | Improved account access security. |
| Enable Multi-Factor Authentication (MFA) on your email account. | High | 30 mins | Greatly lowered risk of unauthorized logins. | |
| 2 | Review and adjust advanced spam filter settings; learn to report phishing. | Medium | 1 hour | Fewer unwanted/malicious emails; better threat awareness. |
| Conduct a thorough review of your email provider's security and privacy features. | Medium | 1 hour | Informed decision about provider suitability. | |
| 3 | Secure mobile email: review app permissions, set strong device lock. | High | 1-2 hours | Protected email access on mobile devices. |
| Review connected third-party applications and remove unnecessary access. | Medium | 30 mins | Reduced potential attack vectors. | |
| 4 | Schedule bi-annual security audits (password changes, settings review). | Medium | 30 mins | Proactive security maintenance habit established. |
| Ensure all software (OS, browser, email client) is up-to-date. | High | 30 mins | Known vulnerabilities patched. |
This timeline serves as a guide; you should adjust it to fit your own circumstances. The main objective is consistent progress, making security an ongoing part of your routine.
Establishing Ongoing Monitoring and Maintenance
Good email security isn't something you set up once and forget; it's an ongoing activity. Regular security audits, perhaps conducted every six months, are very important. During these check-ups, update your passwords, look through your account activity for any unusual logins, and verify your security settings.
It's also important to know when your defenses need an update. Keep up with information on new types of threats and the latest security advice. If your email service introduces new security tools, find out about them and use them if they're right for your needs. Staying alert this way is vital for lasting protection and truly understanding how to protect email from hackers well.
If you're looking to set up a genuinely secure email system that gives you full control, choosing a provider that builds security in from the start, such as Typewire, can make your implementation much simpler by including many of these protections automatically. Discover Typewire's secure email hosting and begin your 7-day free trial today.
How to Protect Email From Hackers: Security Mastery Guide
Posted: 2025-05-26
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27