How To Send Email Securely: Your Complete Protection Guide

Why You Need To Send Email Securely (Before It's Too Late)
Your emails contain a wealth of sensitive information, from personal details and financial records to confidential business communications. This makes them a prime target for cybercriminals. Failing to secure your emails is like leaving your front door unlocked – an open invitation for trouble. Understanding why secure email practices are essential is no longer just a technical issue; it's fundamental to protecting yourself and your business.
The Real-World Consequences of Insecure Email
Imagine a harmless-looking email landing in your inbox. It appears to be from your bank, asking you to update your account information. You click the link, enter your credentials, and minutes later, your account is empty. This is the devastating reality of phishing, a common tactic exploiting insecure email. Malware, disguised as attachments or links, can also infect your devices and compromise your entire system.
Beyond the immediate financial impact, email breaches can severely damage your reputation. For individuals, this could mean identity theft and a tarnished online presence. For businesses, a data breach can lead to lost customer trust, regulatory fines, and legal action. This underscores why prioritizing email security is not just a best practice but a crucial defense against evolving cyber threats.
The Rising Tide of Cyber Threats
Cybercriminals are constantly refining their tactics, becoming more sophisticated and persistent. The increasing importance of secure email practices is directly related to this rise in cyber threats. For example, the global email security solutions market was valued at $18.5 billion in 2024 and is projected to reach $24 billion by 2030, growing at a CAGR of 4.4%. This growth is fueled by the increasing frequency of attacks like phishing and ransomware, pushing organizations to invest in advanced email security solutions. Find more detailed statistics here However, investing in these solutions is only half the battle; knowing how to use them effectively is equally critical.
Compliance and the Future of Email Security
For many industries, sending email securely isn't optional; it's the law. Regulations like HIPAA and GDPR mandate specific security measures to protect sensitive data. Non-compliance can result in significant fines and legal repercussions. Furthermore, as cyber threats become more advanced, email security will only become more vital. Adopting robust security practices now will protect you today and prepare you for the challenges ahead. The future of secure communication depends on understanding and implementing the right measures to safeguard our digital interactions.
Email Encryption Made Simple (No Tech Degree Required)

Sending email securely doesn't have to be complicated. It's simply about selecting the right tools and methods to protect your messages. Think of it as the difference between a postcard and a sealed letter: one is easily read by anyone, while the other maintains privacy. Email encryption performs the same function digitally, encoding your messages so only the intended recipient can understand them.
Understanding the Basics of Encryption
There are two primary types of email encryption: transport layer security (TLS) and end-to-end encryption. TLS protects your message in transit between email servers, like sending a sealed letter through a secure courier. However, once the message reaches the destination server, it's decrypted.
End-to-end encryption, conversely, is like delivering the sealed letter directly to the recipient. Only the recipient possesses the key to open it, maintaining encryption even after arrival.
Choosing the Right Encryption Method
For regular emails, TLS often offers adequate protection. Most major email providers, such as Gmail and Outlook, use TLS by default. However, for highly sensitive information, end-to-end encryption is substantially more secure.
Popular standards like PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions) provide end-to-end encryption. They may require a bit more setup. Selecting the right method depends on your individual security needs and technical skills.
Implementing Encryption in Practice
TLS is generally enabled automatically by your email provider. For end-to-end encryption, you'll need to select a method like PGP or S/MIME and configure it within your email client. There are also user-friendly tools and plugins available to streamline the process.
Some services integrate directly with common email platforms, enabling end-to-end encryption with minimal effort. Learn more about email encryption in our guide to HIPAA compliant email encryption. Regardless of your chosen method, implementing encryption can considerably improve your email security. Even with encryption, remain cautious of phishing attacks and other email threats.
Building Bulletproof Email Access Controls
Strong passwords are no longer enough to protect your email. Think of your password as a single lock on your front door. It might deter the casual intruder, but a determined attacker can find ways to bypass it. That's why multi-factor authentication (MFA) is essential. MFA adds extra layers of security like deadbolts, security cameras, and an alarm system. It keeps unauthorized users out, even if they manage to get your password.
Layering Security with Multi-Factor Authentication
MFA requires users to verify their identity with multiple credentials before granting access. This usually involves something you know (your password), something you have (like a code from your phone), and sometimes something you are (biometrics like fingerprints). The infographic below illustrates the adoption rates of different encryption methods, a critical element in email security.
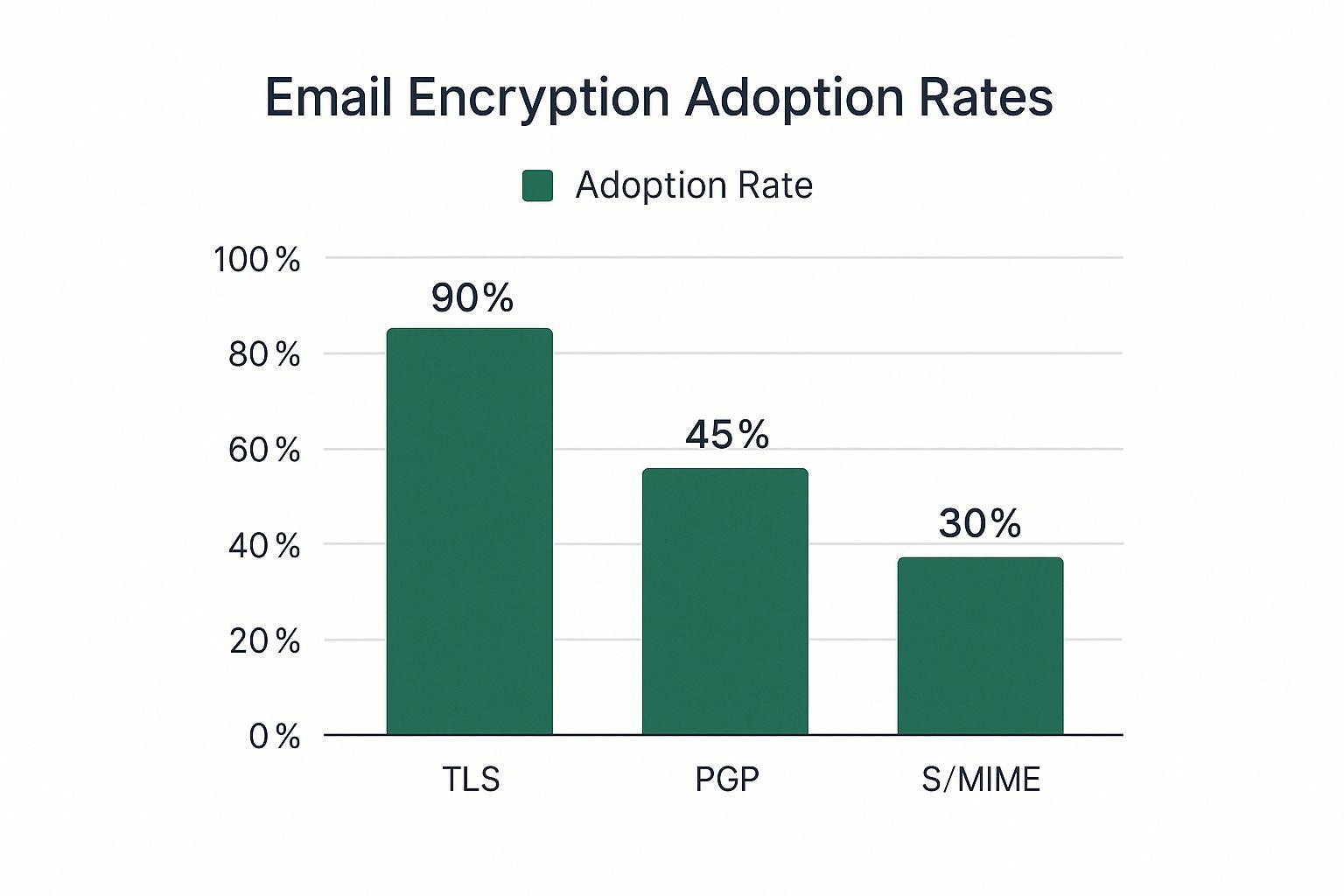
The data shows a significant difference in adoption rates between TLS and more robust methods like PGP and S/MIME. While TLS is widely used, fewer people take advantage of the stronger security offered by PGP and S/MIME. This underscores the need for greater awareness and adoption of these more secure encryption methods.
Exploring MFA Methods: From SMS to Biometrics
Different MFA methods provide varying levels of security and convenience. SMS codes are common, but vulnerable to SIM swapping attacks. Hardware tokens, such as physical key fobs, offer stronger security but can be less convenient. Biometric authentication, like fingerprint or facial recognition, combines security and convenience but can raise privacy concerns. The right balance depends on your individual security needs and risk tolerance.
To help you choose the best method for your needs, let's compare the most common MFA options.
Authentication Methods Comparison
This table compares different multi-factor authentication options based on their security level, user convenience, implementation complexity, and best use cases.
| Authentication Method | Security Level | User Convenience | Setup Complexity | Best Use Case |
|---|---|---|---|---|
| SMS Codes | Low | High | Low | Low-risk accounts |
| Hardware Tokens | High | Medium | Medium | High-security environments |
| Biometric Authentication | High | High | Medium | Mobile devices and personal accounts |
| Software Tokens (Authenticator Apps) | High | High | Low | Everyday use and diverse accounts |
As this table illustrates, there's no one-size-fits-all solution. While SMS codes are easy to use, Authenticator apps and hardware tokens offer robust security. Biometrics provides a convenient high-security option, but consider the privacy implications.
Implementing and Managing MFA Effectively
Setting up MFA is usually straightforward with most email providers. It typically involves enabling the feature in your account settings and connecting a secondary authentication method, such as a mobile app or security key. However, effectively managing MFA across multiple devices and having backup plans for lost or malfunctioning devices is crucial for uninterrupted access and avoiding lockouts. Plan ahead and ensure you have recovery options in place.
Spotting Modern Phishing Attacks (They're Getting Scary Good)
Gone are the days of easily spotted phishing emails riddled with obvious typos and suspicious links. Today's phishing attacks are far more sophisticated. They use artificial intelligence (AI), meticulous social engineering, and advanced spoofing techniques to create convincing impersonations. These tactics can fool even the most cautious users. This means relying solely on your spam filter isn't enough to send email securely.
Deceptive Tactics: How Attackers Mimic Legitimate Sources
Modern phishing attacks frequently utilize AI to create highly personalized messages. These messages resonate with the recipient by mimicking the tone, style, and even branding of legitimate organizations. Imagine a fake login page nearly indistinguishable from your bank's website. Or an email seemingly from your boss requesting urgent action. These deceptive tactics are designed to bypass traditional security filters and exploit human psychology.
Subtle Warning Signs: Beyond the Obvious Red Flags
Even though modern phishing attacks are cleverly disguised, there are still subtle clues you can look for. Scrutinize the sender's email address. Look for slight variations or misspellings in the domain name. Before clicking, hover over any links to see their true destination. If the URL appears suspicious, don’t click it. Be wary of emails creating a sense of urgency or demanding immediate action. These are often pressure tactics designed to make you slip up.
Verification Techniques: Taking Control of Your Security
If you’re uncertain about an email's authenticity, take steps to verify it independently. Contact the supposed sender directly. Use a known phone number or website, not the information provided in the email itself. For more detailed guidance, you might find this resource helpful: How to identify phishing emails—expert tips to stay safe. Attackers often research their targets on social media and other online sources. This allows them to tailor phishing attempts with personalized lures that exploit your interests and connections. Phishing attack success rates have been a significant concern. In 2025, these rates were around 0.12%. With improvements in AI-powered filters and user education, this rate is projected to decrease to 0.03% by 2030. Reports also indicate that 92% of polymorphic attacks use AI, significantly changing the threat landscape. You can explore this topic further here. Developing strong security habits and a healthy dose of skepticism can protect you from even the most sophisticated phishing attacks and help ensure you send email securely.
Beyond Technology: Cultivating a Security Mindset
Protecting yourself against these evolving phishing tactics requires a proactive security mindset. It goes beyond just technology. By staying informed about the latest threats and practicing vigilance, you can significantly reduce your risk. This means questioning everything, verifying information independently, and trusting your instincts.
Choosing Email Providers That Actually Protect You
Finding the right email provider can be tricky. Marketing promises often obscure the reality of a service's security. How can you tell which providers truly prioritize protecting your data? This section provides practical advice on how to select an email service that keeps your communications confidential.
Evaluating Key Security Features
Before committing to an email provider, consider these essential security features:
- Encryption Standards: Look for providers that offer Transport Layer Security (TLS). This encrypts data in transit, protecting your emails from eavesdropping. Support for end-to-end encryption, such as PGP or S/MIME, offers even stronger protection.
- Data Retention Policies: How long does the provider keep your data? Shorter retention periods limit the potential damage from data breaches.
- Server Locations: The physical location of the provider's servers impacts data privacy and legal jurisdiction. Be sure to understand where your data is stored.
- Transparency Reporting: Transparency reports detail government data requests and security incidents. Providers who publish these reports demonstrate a commitment to accountability and user trust.
Mainstream Providers vs. Specialized Secure Services
Mainstream email providers like Gmail and Outlook have improved their security in recent years. For example, Gmail now provides accessible end-to-end encryption. This simplifies secure communication, eliminating the complexity of older methods like S/MIME. However, specialized secure email services exist to serve the needs of privacy-focused users. These services frequently offer advanced features and stronger privacy protections.
For further reading on secure email providers, see: Top Private Email Providers for Security in 2025
Hidden Security Features and the Convenience-Protection Trade-Off
Many email providers offer security features that often go unused, simply because they are not enabled by default. These features, such as two-factor authentication (2FA), can significantly improve your security but may require some configuration. There’s a constant balance between convenience and protection. Stronger security measures might involve extra steps. Maximum convenience can sometimes create security vulnerabilities. Finding the right balance for your needs is crucial.
To illustrate the features available, see the table below:
Secure Email Provider Features: Comprehensive comparison of security features offered by leading email providers including encryption, privacy controls, and compliance certifications.
| Provider | Encryption Type | Zero-Access | 2FA Options | Compliance | Pricing |
|---|---|---|---|---|---|
| ProtonMail | End-to-end, TLS | Yes | App-based, Security Key | GDPR, Swiss privacy laws | Free, Paid plans |
| Tutanota | End-to-end, TLS | Yes | App-based, U2F | GDPR, German privacy laws | Free, Paid plans |
| Mailfence | End-to-end, TLS | Yes | App-based, SMS | GDPR, Belgian privacy laws | Free, Paid plans |
| Gmail | TLS, Optional end-to-end | No | App-based, SMS, Security Key | GDPR, US privacy laws | Free, Paid plans (Workspace) |
| Outlook | TLS, Optional S/MIME | No | App-based, SMS, Security Key | GDPR, US privacy laws | Free, Paid plans (Microsoft 365) |
This table offers a snapshot of the different security and privacy features available. Remember to research each provider thoroughly to understand their specific offerings.
Cost vs. Security Value
Free email services sometimes monetize user data for targeted advertising. Paid secure email providers prioritize privacy but come with a subscription cost. Carefully weigh your security needs against your budget. Investing in enhanced privacy and security can be a wise decision.
Migration Strategies and Complementary Tools
Switching email providers doesn't have to be a headache. Several migration strategies can ensure a smooth transition without losing important emails. Tools like password managers and VPNs further enhance your overall email security by adding extra layers of protection for your credentials and online activities. Choosing the right email provider is a fundamental step in securing your digital life. By carefully evaluating your needs and the available options, you can choose a provider that fits your security requirements.
Daily Habits That Keep Your Email Secure

Sending email securely isn't a one-time event. It's an ongoing process, much like brushing your teeth or locking your door. Incorporating security habits into your daily routine can dramatically improve your defenses. This consistent approach cultivates a security-first mindset, protecting you across all your digital interactions.
Smart Password Management: Your First Line of Defense
Your password is the gateway to your online life. Use a strong, unique password for your email, keeping it separate from any other online accounts. This helps limit the damage if one of your accounts is ever compromised. Using a password manager is a great way to generate and securely store these complex passwords, eliminating the need to memorize them all.
Regular Security Audits: Staying One Step Ahead
Just like a regular home security check, periodic reviews of your email settings are essential. Examine connected devices and apps with email access. Revoke access for anything you no longer use or don't recognize. This practice minimizes potential access points for malicious actors.
Staying Informed: Recognizing Evolving Threats
The world of online threats is always evolving. Staying up-to-date on current phishing techniques and best security practices is key to staying protected. Consider it a form of continuing education for your digital well-being. Subscribing to security blogs or newsletters is a great way to remain informed without feeling overwhelmed.
Building a Culture of Security for Teams
For businesses, fostering a security-conscious environment is vital for secure email practices. Establish clear security policies, provide consistent training, and create an atmosphere where employees feel comfortable discussing potential threats. This builds a collective defense, where every individual contributes to overall security.
- Implement practical security policies: Steer clear of overly complicated rules that employees are likely to ignore. Instead, focus on practical steps that easily fit into their existing workflow.
- Conduct regular security awareness training: Use engaging training sessions to keep employees informed about the latest threats and best practices. Techniques like gamification and real-world scenarios can increase effectiveness.
- Encourage prompt threat reporting: Set up a system where employees can easily and confidentially report suspicious emails or activities without fear of repercussions. This facilitates a quick response and containment of potential breaches.
Monitoring and Backups: Protecting Against the Unexpected
Implementing multi-factor authentication (MFA) adds an extra layer of security, significantly hindering unauthorized access. Regular email backups provide a safety net for data recovery in the event of system failures or successful attacks. This ensures your information remains protected, even in worst-case scenarios.
Future-Proofing Your Email Security Strategy
The email security landscape is constantly shifting. New threats appear, and existing ones grow more complex. Staying ahead requires a proactive and adaptable strategy. This means looking beyond current threats and anticipating the challenges of the future.
Emerging Threats and Defense Technologies
Cybersecurity is a dynamic field. New threats are continuously emerging. Understanding these trends is key to future-proofing your email security.
-
Quantum-Resistant Encryption: The rise of quantum computing may threaten current encryption methods. Quantum-resistant encryption algorithms are being developed to address these future attacks, ensuring your encrypted messages remain secure even in a post-quantum world.
-
AI-Powered Threat Detection: Artificial intelligence (AI) plays a growing role in cybersecurity. AI-powered threat detection systems analyze large datasets to identify and neutralize threats faster and more accurately than traditional methods, including sophisticated phishing attacks and malicious attachments that could bypass human detection.
-
Zero-Trust Security Models: Traditional security models often assume trust within a network's perimeter. Zero-trust changes this, requiring verification for every access request, regardless of its origin. This approach limits the damage of successful breaches by restricting lateral movement within a network.
Adapting to Changing Regulations and Compliance
Privacy regulations and compliance requirements are not static. They change with technological advancements and emerging threats. Staying informed about these changes and adapting your email practices is vital for avoiding legal issues and maintaining customer trust.
Evaluating New Security Technologies
The cybersecurity market is full of new products and technologies. It's important to critically evaluate these offerings. Look beyond marketing and focus on the technology itself. Does it address a specific threat? Does it integrate with your current systems? How difficult is implementation and maintenance?
Building an Adaptable Security Framework
A static security strategy is inadequate in today's dynamic threat environment. An adaptable security framework allows you to respond effectively to new challenges. This means establishing a foundation of core security practices, including encryption, multi-factor authentication, and regular security audits, while maintaining the flexibility to integrate new technologies and adapt to evolving threats. Regularly review and update your security strategy to keep it aligned with current needs and best practices.
Maintaining Robust and Sustainable Protection
Security isn't just about technology; it's also about cultivating a security-conscious culture. Educate yourself and your team about potential threats and best practices. Encourage vigilance and establish clear reporting procedures for suspicious activity. An informed and proactive user is your strongest security asset.
Start securing your email communications today with Typewire's robust and privacy-focused platform. Explore Typewire's secure email hosting solutions.
How To Send Email Securely: Your Complete Protection Guide
Posted: 2025-06-02
Your Guide to Finding the Right IMAP Port Number for Secure Email
Posted: 2025-12-20
How to Securely Set Up Emails on iPhone
Posted: 2025-12-19
Professional Email Writing Tips: Secure, Private Communication for Crisp Comms
Posted: 2025-12-18
How to Get Spam Emails to Stop Your Ultimate Inbox Defense Guide
Posted: 2025-12-17
How to Get Spam Emails to Stop and Reclaim Your Inbox
Posted: 2025-12-17
Register Email Without Phone Number The Ultimate Privacy Guide
Posted: 2025-12-16
What Is Domain Name Registration A Guide to Your Digital Address
Posted: 2025-12-15
Choosing an Encrypted Email Solution for Your Business
Posted: 2025-12-14