Register Email Without Phone Number The Ultimate Privacy Guide

Absolutely, you can register an email without a phone number. Several privacy-first email providers have built their services around this very idea, letting you sign up using different recovery methods. It's a smart move that enhances your email security by keeping your personal number out of the equation and putting a stronger lock on your digital identity.
Why You Should Create an Email Without a Phone Number

In today's world, our phone number has become a master key to our digital lives. It's more than just a way for people to call you; it's a unique identifier that links your accounts, activities, and real-world identity. Handing it over every time a service asks for it is a habit that introduces some serious, often overlooked, risks to your email privacy and overall digital security.
This isn't just about dodging annoying spam calls, either. The real issues run much deeper, touching on your personal security and privacy in ways you might not expect.
The Real Threats of a Phone-Linked Account
One of the most chilling vulnerabilities is the SIM swapping attack. It’s a terrifyingly simple scam where a fraudster tricks your mobile provider into switching your phone number over to a SIM card in their possession. The moment they succeed, they control your number.
From there, they can intercept any two-factor authentication codes or password reset links sent via text. Suddenly, your email, bank accounts, and social media are wide open for the taking, compromising your entire email security framework.
Your phone number is often the weakest link in your digital security chain. An attacker doesn't need to hack your password if they can simply take control of your number to reset it.
Then there's the constant threat of data breaches. When a company you’ve trusted with your number gets hacked, that information—your name, email, and phone number—often lands on the dark web. This gives criminals a neat little package to use for targeted phishing attacks or outright identity theft.
Protecting Your Digital Footprint
Beyond the threat of direct attacks, your phone number is a goldmine for data brokers and advertisers. They use it as a persistent identifier to connect the dots between your activities on different websites and apps. This helps them build an incredibly detailed and invasive profile of your habits, interests, and even your physical location. Creating an email without that phone link is a crucial step for maintaining email privacy and throwing a wrench in their tracking machine.
Here’s a quick breakdown of why this matters:
- Enhanced Privacy: It decouples your email from your real-world identity, making you less of an open book.
- Stronger Security: It completely nullifies the threat of SIM swapping and minimizes the damage from data breaches.
- Reduced Tracking: It makes it much harder for advertisers and data brokers to follow you across the web.
Ultimately, the choice to create an email without a phone number is a proactive step toward regaining control. This mindset often extends to other areas, like using anonymous payment options for enhanced privacy to further reduce your digital trail. It’s a practical, powerful way to safeguard your identity online.
Choosing the Right Private Email Provider

When you make the decision to register an email without a phone number, you’re taking a big step away from the mainstream providers who often treat your personal data like a commodity. You're entering a world of privacy-first services, platforms built from the ground up to shield your identity, not exploit it.
These providers operate on a completely different philosophy. Unlike the giants that require personal details to fuel their ad engines, private email services put your email privacy and security first. They get that real privacy starts the moment you sign up, which is why they've become the trusted choice for journalists, activists, and anyone who simply wants to take back control of their digital footprint.
Understanding Key Privacy Features
As you start exploring your options, you'll run into some technical terms that are crucial for email security. Two of the most important ones you'll see are end-to-end encryption (E2EE) and zero-access architecture.
Think of end-to-end encryption as a digital sealed envelope. Your message gets scrambled the second you hit "send" and can only be unscrambled by the person you sent it to. No one in between—not even the email provider itself—can peek inside.
Zero-access architecture takes this protection even further. It guarantees that the provider has absolutely no way to access your stored emails because they are encrypted with a key that only you hold. This is a massive safeguard for your email privacy. It means your data stays unreadable even if the company's servers are compromised or if they receive a legal order to hand over data. This is really the bedrock of any truly private email service.
Comparing Privacy-Focused Email Providers
Let’s take a look at some of the leading platforms that let you create an email account without handing over your phone number. The market for secure email has definitely matured, and providers like ProtonMail, Tutanota, and Mailfence have seen a huge surge in popularity through 2025. They're meeting a global demand for anonymity and robust email security as people become more aware of data surveillance.
To help you get a clearer picture, here’s a quick comparison of some of the top contenders.
Comparing Privacy-Focused Email Providers
The table below breaks down the key differences between some of the most respected privacy-focused email services available today.
| Provider | Phone Number Required | Encryption Model | Key Privacy Features |
|---|---|---|---|
| ProtonMail | Optional | E2EE & Zero-Access | Based in Switzerland with famously strong privacy laws. Uses open-source cryptography. |
| Tutanota | No | E2EE & Zero-Access | Encrypts the entire mailbox, going beyond just the message body to include subject lines and contacts. |
| Mailfence | No | E2EE with OpenPGP | Based in Belgium. Offers an integrated suite with a calendar and document storage. |
| Typewire | Optional | E2EE & Zero-Access | A hosted email platform in Canada on privately owned infrastructure, with a strong emphasis on user control. |
This comparison gives you a solid starting point. Each service has its own unique strengths, and what's best for you will depend on your specific needs.
For a deeper dive, you can explore our full analysis of the 7 best private email providers for security in 2025 to get a more detailed breakdown.
The Advantage of Private Hosted Email
For those who want the absolute maximum level of control and security, a private hosted email platform like Typewire offers a very compelling alternative. Instead of sharing space on a massive public service, you get a dedicated environment that you and your team manage directly.
With hosted email, you are not just a user—you are the owner. This fundamentally shifts the balance of power, ensuring your data, domain, and communications remain exclusively yours.
This model is a fantastic fit for businesses and individuals who need to manage several accounts under their own custom domain while enforcing strict security standards. Because these platforms run on their own infrastructure, they aren't tied to the policies of big cloud providers, which adds another powerful layer of data sovereignty and genuine peace of mind. Hosted email platforms deliver superior email security and email privacy by giving you full administrative control.
Your Walkthrough for Creating a Private Email Account
Alright, you’ve picked a provider that puts privacy first. Now for the fun part: setting up your account. The great news is that the process to register an email without a phone number is often much simpler than with the big tech giants. It just requires a different mindset—you're focusing on securing your own access instead of just handing over your data.
I'll walk you through the process using Tutanota as the main example, mostly because their sign-up is a perfect illustration of a privacy-first approach. The core concepts are pretty much the same whether you choose Tutanota, Proton Mail, or Mailfence. The real key is paying close attention to the recovery options. This is where you set yourself up for long-term email security.
Navigating the Sign-Up Process
When you land on Tutanota's sign-up page, your first task is to pick your new email address and create a strong, unique password. Think of this password as the only key to your digital front door. Because of Tutanota's zero-access architecture, they can't see your password, which means they can't reset it for you if you lose it.
- Craft a serious password: I'm talking a combination of uppercase letters, lowercase letters, numbers, and symbols. Aim for at least 16 characters. Don't use your dog's name or your birthday. If you're not great at creating them, let a password manager generate and store a super complex one for you.
- Accept the terms (and the responsibility): You'll have to check a box confirming you understand that if you lose your password and your recovery code, your account is gone forever. This isn't a scare tactic; it's the reality of taking full ownership of your data to ensure email privacy.
Right after this, you'll be given the most critical piece of information for your new account: the recovery code.
Securing Your Lifeline: The Recovery Code
Pay attention here, because this is the most important step for your email security. Tutanota, for instance, will give you a unique, 64-character recovery code. This string of characters is the only way you can get back into your account if your password ever slips your mind. There's no "Forgot Password?" link that texts a code to your phone.
Your recovery code is the master key to your digital safe. Treat it with the same level of security as you would the deed to your house or your physical passport. Once it's lost, there's no backup plan.
You absolutely must store this code somewhere safe, secure, and completely separate from your password. Keeping them in the same digital note or on the same piece of paper completely defeats the purpose.
Here are a few battle-tested ways to store it:
- In a Password Manager: Use a trusted manager like Bitwarden or 1Password to save the code as a secure note. This keeps it encrypted but still accessible when you need it.
- Good Old-Fashioned Paper: Print it out or write it down—very carefully. Then, stick that physical copy in a fireproof safe, a bank's safe deposit box, or another truly secure location.
- On an Encrypted Drive: Save the code in a simple text file on an encrypted USB stick. Keep that drive offline and tucked away somewhere safe.
Once you’ve safely stashed your recovery code and confirmed you've done so, your new private email is ready to go. You’ve just created a secure communication channel without tying it to your phone number—a huge step toward digital independence.
For those who want to push their privacy even further, our guide on how to create an anonymous email for total privacy is the perfect next step.
How to Properly Secure Your New Email Account
Alright, you've created your private email. That's a huge step. But the real work starts now. Securing that account is what turns it from a good idea into a genuine fortress for your digital life. The whole point of strong email security is to build up measures that don't rely on easily intercepted SMS messages—a favorite target for hackers.
This requires a mental shift. Instead of reflexively typing in a phone number, we're going to lean on far more robust methods to keep your account safe.
The setup for a truly private email is surprisingly simple, focusing on what actually matters for security.
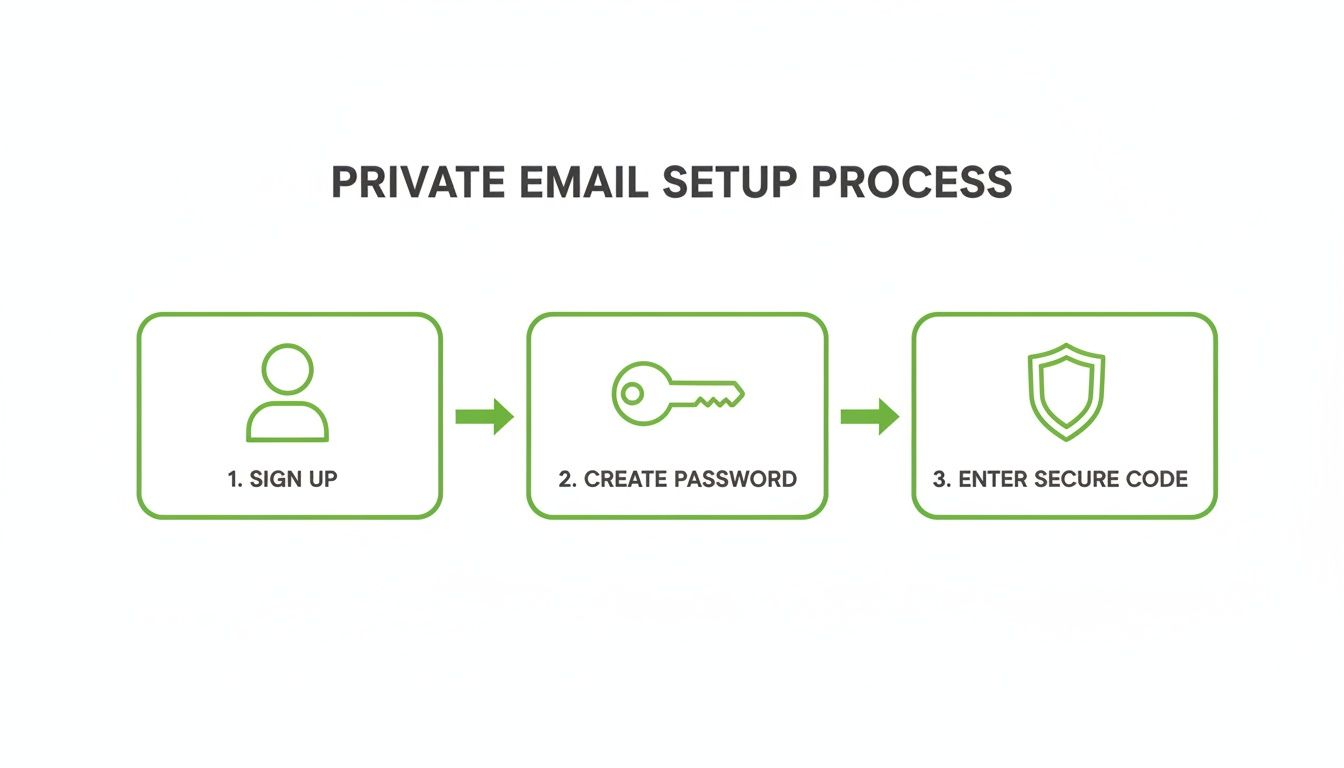
As you can see, the process is built around a strong password and a unique secure code, taking your phone number completely out of the equation for maximum email privacy.
Embrace App-Based Two-Factor Authentication
The single best email security upgrade you can make is switching to app-based two-factor authentication (2FA). This method uses a Time-based One-Time Password (TOTP), which sounds technical but just means an app on your phone or computer generates a new code every 30-60 seconds.
This one change completely shuts down the risk of SIM-swapping attacks. Since the code is created on your device—not sent over the insecure SMS network—a thief who takes over your phone number gets absolutely nothing.
Getting it running is pretty simple:
- Get an authenticator app. I personally recommend Authy or Aegis Authenticator for Android. Many password managers like Bitwarden also have this feature built-in.
- Scan the QR code. Go into your email account’s security settings, find the option to enable 2FA, and your provider will show you a QR code. Just scan it with your authenticator app.
- Save your backup codes! This is critical. Your email provider will give you a list of one-time-use codes. Treat these like gold. Store them somewhere incredibly safe, just like your main recovery code. If you lose your phone, these codes are your only way back in.
For a deeper dive into how this all works, check out this guide: https://typewire.com/blog/read/2025-08-06-a-guide-to-multi-factor-authentication-email-security.
Use Another Private Email for Recovery
Here's another pro-level strategy: set up a second private email account and use it only as the recovery address for your main one.
This creates a self-contained security loop that you control entirely. If you get locked out of your primary account, the password reset link goes to another secure account you own, not to a vulnerable phone number.
By combining an authenticator app with a secondary private email for recovery, you're building layers of defense. An attacker would have to steal your password, get their hands on your physical device, and break into your separate recovery email. That's a whole lot harder than just tricking a mobile carrier.
Securing your email is a fantastic start, but don't stop there. Think about your other communications, too. For broader digital privacy, learn how to encrypt your phone calls and apply the same privacy-first mindset across the board.
The Hidden Dangers of Disposable Email Services
When you're looking to register an email without a phone number, you'll inevitably run into disposable email services. They’re tempting, I get it. They offer an instant, no-fuss inbox that seems perfect for a one-off sign-up. But that convenience is a trap, and it comes with some serious hidden costs to your email privacy and long-term security.
Think of these services as a quick fix that often creates much bigger headaches down the road. They’re built for fleeting interactions, not for actually protecting your digital life.
Why Temporary Is a Terrible Idea
The most glaring problem with disposable emails is their total lack of security. Seriously, there's often none. Many of these services use public or easily guessable inboxes, meaning anyone who figures out your temporary address can potentially see your messages—including sensitive things like password reset links or account confirmations. This makes them a disaster for email security.
And their name says it all: they are temporary. That’s not just a marketing term; it's a hard limit. Most of these inboxes are designed to self-destruct in a few hours or days, and when they go, so does your access to whatever account you signed up for. Forget your password? You have absolutely zero chance of getting it back.
A disposable email is like building your digital home on a foundation of sand. The first time a wave of trouble hits—like a forgotten password or a security check—the entire structure washes away, leaving you with nothing.
This makes them fundamentally useless for anything more important than a throwaway coupon code.
The Data Proves the Risk
This isn't just a hypothetical problem. The numbers paint a pretty clear picture of how unreliable these services are. A 2025 analysis of over 500,000 online sign-ups found that a surprising 12% came from temporary email addresses. That figure shot up to 18% for sites offering free trials or special deals, showing just how often people use them for hit-and-run registrations.
What's really alarming is that the data also showed 60% of those temporary emails were gone—deactivated—within just 24 hours. That makes any kind of follow-up, let alone critical account recovery, completely impossible. You can dive deeper into these trends and what they mean by reading the full findings on invalid email addresses.
At the end of the day, a dedicated, private email provider is the only smart, sustainable choice. While disposable services offer a shortcut, a secure and permanent email address from a provider focused on email privacy provides a safe, reliable path for your online life.
Answering Your Questions About Phone-Free Email
Even when you know the steps, it's normal to have a few questions. Deciding to register an email without a phone number means taking a different path than most, so let's clear up some of the common uncertainties.
The great thing is, this whole approach is built on solid principles of email privacy and genuine security—not on trying to find some sneaky loophole.
Is It Actually Legal to Create an Email Without a Phone Number?
Yes, it’s 100% legal. There’s absolutely no law that says you have to hand over your phone number to create an email account. When a provider asks for your number, it’s just their corporate policy for verifying users and collecting data, not a legal requirement.
In fact, privacy-first providers—especially those in places with strong data protection laws like Switzerland or Germany—go out of their way to collect as little information as possible. It's a core part of their philosophy and aligns with regulations like GDPR. For them, phone-free registration is a feature that promotes email privacy, not a flaw.
What Happens If I Forget My Password? Can I Still Recover My Account?
You absolutely can, but your recovery options will look different. Instead of getting a text message with a reset link, you'll be relying on the alternative methods you set up during registration to ensure your email security.
This usually means one of two things:
- A secondary recovery email: A separate, trusted email address where the provider can send password reset instructions.
- A one-time recovery code: That unique, long string of characters you were prompted to save when you created the account.
I can't stress this enough: that recovery code is your lifeline. Treat it like gold. Store it somewhere safe and offline—a secure note in a password manager or even printed out in a physical safe. If you lose your password and don't have a recovery email, it's the only key you have to get back in.
Are Emails Without Phone Verification Less Secure?
Quite the opposite—they're often much more secure. Real email security doesn't come from a phone number, which can be hijacked through SIM-swapping attacks. It comes from a strong, unique password paired with a modern two-factor authentication (2FA) method, like a TOTP authenticator app.
This approach completely removes your mobile carrier as a potential weak link in your security chain. The growing demand for phone-free options is part of a larger shift toward user privacy. Data shows that 67% of users are already creating secondary accounts just to avoid spam, which has driven more people toward secure providers that respect their privacy. You can discover more insights about email privacy trends and see firsthand how user priorities are evolving.
Ready to take full control of your digital communications? With a hosted email platform like Typewire, you get secure, private email hosting that puts you in the driver's seat. No ads, no tracking, just a powerful platform built to protect your email privacy. Start your 7-day free trial today!
Register Email Without Phone Number The Ultimate Privacy Guide
Posted: 2025-12-16
What Is Domain Name Registration A Guide to Your Digital Address
Posted: 2025-12-15
Choosing an Encrypted Email Solution for Your Business
Posted: 2025-12-14
What is email deliverability: Your guide to inbox success
Posted: 2025-12-13
What Is SMTP Authentication? A Guide to Email Security and Privacy
Posted: 2025-12-12
How to Create Email Templates Securely and Effectively
Posted: 2025-12-11
Unlock Inbox Peace: How Can I Stop Receiving Spam Emails and Reclaim Control
Posted: 2025-12-10
Discover how to send encrypted emails: A practical guide to secure messaging
Posted: 2025-12-09
How to Host an Email Server: A Guide to Privacy and Security
Posted: 2025-12-08