A Practical Guide to Sending Secure Mail

Think about standard email for a second. Sending one is basically like mailing a postcard. Anyone who gets their hands on it along the way—from your internet provider to a hacker sniffing the network—can read it. In a world where we're constantly sharing sensitive information, just hoping for the best isn't a strategy.
When we talk about sending secure mail, we're talking about using encryption to put that postcard inside a locked metal box. Only the person with the right key can open it. This isn't just for spies and corporations anymore; it’s a fundamental practice for protecting everything from personal details to confidential business plans.
Why You Can't Afford to Ignore Email Security
The strange thing about email is that its default state is wide open. Without encryption, your messages are just plain text hopping across servers. That makes them easy targets at multiple points along their journey. This isn't just a big-company problem, either. Freelancers, small businesses, and individuals are all handling information that needs to be protected.
The fallout from an email breach can be brutal. We’re talking about everything from financial theft and identity fraud to serious damage to your reputation. A single hacked account can act as a skeleton key, giving an attacker access to your entire network of contacts and a trove of sensitive data.

This diagram gives you a clear picture of how encryption works. Your message gets "locked" with a public key before it's sent, and only the recipient's matching private key can "unlock" it. If someone intercepts it mid-transit, all they see is scrambled, unreadable code.
The Real-World Risks of Unsecured Email
It’s easy to tune out security warnings, but the real-world examples hit hard. Imagine a freelance designer sending project mockups and contracts to a new client. If that email is intercepted, their intellectual property could be stolen. Or think of a therapist emailing a patient about their session—a standard, unencrypted email could lead to a major privacy violation and crippling fines. These aren't just hypotheticals; they happen all the time.
We are often the weakest link in our own security. Even the experts can get fooled by a clever phishing email, which is why having strong technical safeguards in place is so important—they protect us from our own momentary mistakes.
Where Standard Email Services Falter
Sure, popular email providers have beefed up their security over the years, but they are far from foolproof. The threat is real even in major corporate environments. Take Microsoft 365, for example. A shocking 79% of its users have been hit by at least one email-based cyber incident. That statistic alone shows that standard defenses just aren't enough to stop determined attackers.
This is exactly why you need to be proactive about sending secure mail. Understanding the top benefits of encrypted email you need to know is the first step toward truly protecting your digital communications.
Cracking the Code of Email Encryption
You don't need a cryptography degree to send a secure email, but knowing the basics will help you pick the right tools with confidence. It's like understanding the difference between a simple door latch and a deadbolt—both secure a door, but one offers a whole lot more protection. The same idea applies here.
At the heart of it all, you'll constantly run into two main technologies: Transport Layer Security (TLS) and End-to-End Encryption (E2EE).

What Happens When You Hit 'Send'
Think of TLS as an armored truck. When you send an email using a modern service like Gmail or Outlook, TLS encrypts the connection between your computer and their server. It then does the same between their server and your recipient's server. Your message is safe while it’s in transit—inside that armored truck.
The catch? When the truck gets to the email provider's sorting facility (their server), the message is temporarily "unpacked" and can be seen by the provider.
This is where E2EE changes the game. If TLS is the armored truck, E2EE is a locked box inside that truck. With true E2EE, the message is encrypted on your device and can only be decrypted by the person you sent it to. Nobody in the middle can peek inside—not your internet provider, not a snooping hacker, and not even the email company itself.
TLS protects the journey, while E2EE protects the message itself from everyone except the recipient. For truly sensitive communication, E2EE is what you need.
This distinction is more important than ever. The average person gets over 80 emails a day, with nearly half being spam. That sheer volume creates a huge playground for phishing and other attacks, making solid encryption a must-have. You can learn more about what end-to-end encryption is in our detailed guide.
PGP vs. S/MIME: The Two Big Players
As you dig deeper into setting up encrypted email, you’ll find two main standards leading the charge: PGP and S/MIME. Both get the job done, but they work on fundamentally different systems of trust.
- PGP (Pretty Good Privacy) is built on a "web of trust." It’s a decentralized approach where you and your contacts exchange public keys directly. This makes it a favorite among journalists, activists, and anyone who values privacy without a central authority.
- S/MIME (Secure/Multipurpose Internet Mail Extensions) uses a centralized model. It depends on digital certificates from a trusted Certificate Authority (CA), much like the SSL/TLS certificates that secure websites. This structure makes it a natural fit for corporate and government settings.
Deciding which to use often comes down to your technical comfort and, more importantly, what the people you're emailing use.
Comparing Email Encryption Methods
Here's a quick breakdown of the two main encryption standards to help you figure out which one might be right for your situation.
| Feature | PGP (Pretty Good Privacy) | S/MIME (Secure/Multipurpose Internet Mail Extensions) |
|---|---|---|
| Trust Model | Decentralized (Web of Trust) | Centralized (Certificate Authorities) |
| Common Users | Individuals, journalists, tech community | Corporations, government agencies |
| Setup | Often requires manual key management | Integrated into many enterprise clients (e.g., Outlook) |
| Cost | Generally free (open-source tools) | Often requires purchasing a certificate |
Ultimately, S/MIME is often easier to manage in a large organization where an IT department can handle the certificates. For individual users or small teams prioritizing privacy and low cost, PGP is usually the go-to choice.
Choosing the Right Secure Email Tool for You

When it comes to sending secure mail, the sheer number of options can feel like a maze. The secret isn't finding the one "best" tool, but finding the right tool for you. It all comes down to your daily workflow, how comfortable you are with technology, and just how much security you really need.
Let’s break down the three main paths you can take. A freelance designer swapping sensitive project files with a client has completely different needs than a large healthcare provider that must comply with strict regulations.
Path 1: Dedicated Secure Email Services
The simplest, most direct route is signing up for a dedicated secure email provider. These services were built from the ground up with end-to-end encryption and user privacy as the main event, not a feature tacked on later. Think of them as a complete, private ecosystem for your communications.
- Who are they for? Privacy-conscious individuals, journalists, lawyers, and any small business that regularly handles sensitive client information.
- What’s the upside? They are incredibly easy to get started with. The setup is minimal, and encryption is often automatic when you email other users on the same service.
- Any downsides? You’ll get a brand new email address. This means you have to let all your contacts know about the change, which can be a bit of a hassle for some.
Providers like ProtonMail and Tutanota are the big names here. They make security the default setting. For a more detailed comparison, our guide on the top 7 best secure mail service providers for 2025 is a great place to start.
Path 2: Plugins for Your Current Email Client
Maybe you're perfectly happy with your Gmail or Outlook account and don't want to start over. I get it. In that case, adding a security plugin or browser extension is your best bet. These tools basically bolt PGP encryption capabilities onto your existing inbox.
This approach is like giving your familiar email client a major security upgrade. It’s a fantastic middle ground for anyone who wants serious encryption without leaving their current setup behind.
Here's the crucial part: For a plugin to work, both you and your recipient need to have a compatible system. It requires a bit more coordination but gives you the flexibility to stay put.
Tools like Mailvelope or FlowCrypt are popular choices that integrate right into your compose window, adding an "Encrypt" button. The main hurdle is getting comfortable with managing your encryption keys and making sure your contacts are set up to read your messages.
Path 3: Built-in Enterprise Solutions
For larger companies, email security has to be manageable across hundreds or thousands of employees. This is where enterprise-grade tools like Microsoft 365 Message Encryption or Google Workspace Client-side Encryption shine. They're designed to plug directly into the corporate IT environment.
- Who are they for? Medium-to-large businesses, especially those in finance, healthcare, or any other field with strict compliance rules.
- What’s the upside? Everything is managed centrally by the IT team, which makes rolling it out and enforcing security policies much easier. It all works within the company's existing tech stack.
- Any downsides? These solutions can be expensive. They also might not offer true "zero-knowledge" privacy, as the company itself often holds a master key to decrypt messages if needed.
For any business, protecting email is non-negotiable. When you consider that email marketing can bring in around $36 for every $1 spent, securing this communication channel is more than just a good practice—it's a critical business function.
Your Walkthrough for Sending Encrypted Email
Alright, let's move from theory to action. Understanding how encryption works is one thing, but sending your first secure email can feel a little daunting. Don't worry, it's easier than it sounds.
I’ll walk you through two of the most common and practical ways to get this done. We'll look at using an all-in-one secure service and then explore how to add encryption to the email client you already use every day.
Option 1: Use a Dedicated Secure Email Service
The simplest way to start sending end-to-end encrypted email is to sign up for a service built specifically for it. Think of platforms like ProtonMail or our own service, Typewire. Security isn't just a feature for them; it's the entire point.
Let's use ProtonMail as our example, since the process is pretty similar across the board for these types of providers.
Getting Set Up Is Surprisingly Fast
First, you’ll create an account. This usually just means picking a username, creating a strong password, and maybe adding a recovery email. Here's the cool part: as you do this, the service is already generating your public and private encryption keys for you, completely behind the scenes. You never have to mess with them, which is a massive plus.
Once you’re in, the interface looks just like any webmail you've used before. No steep learning curve.
Sending Your First Encrypted Message
When you go to compose a new message, this is where the security kicks in.
- Emailing someone on the same service: If your recipient also uses ProtonMail, the encryption is completely automatic. Just type your email and hit send. A little lock icon usually appears, confirming the message is protected with end-to-end encryption. It's seamless.
- Emailing someone on a standard service (like Gmail): This is where these services really prove their worth. You can still send a fully encrypted message by protecting it with a password. Your recipient gets an email with a secure link. They click the link, enter the password (which you've shared with them through another channel, like a text), and they can read and reply to your message within a secure web portal.
This password-protected email feature is a game-changer. It bridges the gap, letting you maintain end-to-end encryption even when the person you're talking to isn't on a secure platform. It solves one of the biggest headaches of encrypted communication.
Option 2: Add PGP Encryption to Your Current Email
What if you love your Gmail or Outlook address and don't want to switch? You can add a powerful layer of security right on top of it using PGP (Pretty Good Privacy). Tools like Mailvelope or FlowCrypt are browser extensions that integrate directly into your existing inbox.
Let's break down how this works.
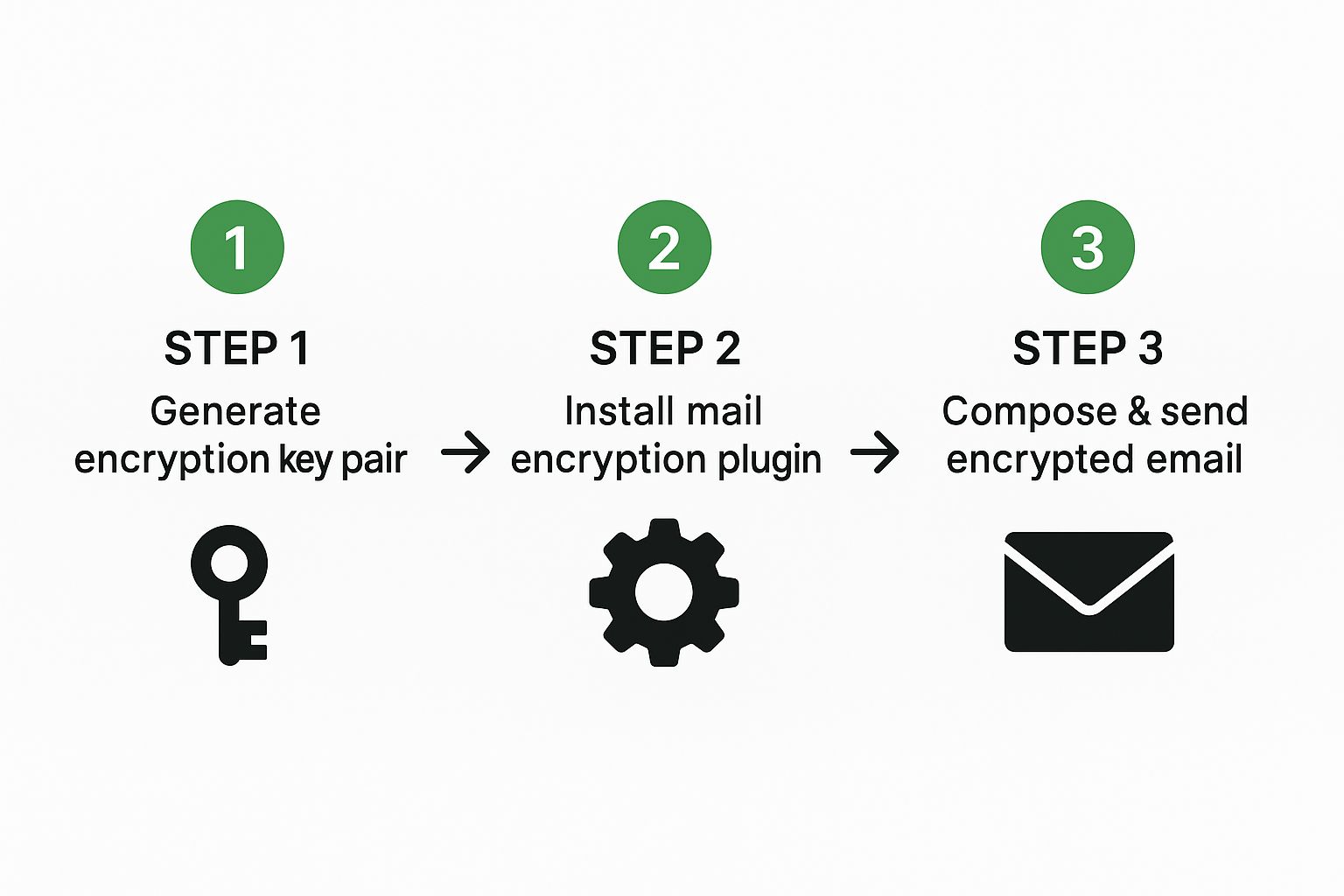
This process really boils down to three main stages: generating your keys, sharing them, and then encrypting your message.
Setting Up the PGP Plugin
Once you’ve installed an extension like Mailvelope, your first job is to generate your key pair. The plugin makes this easy, walking you through a few steps where you'll enter your name, email, and a strong passphrase. This passphrase is the master key to your entire setup—it protects your private key, so make it a good one!
The PGP "Handshake": Exchanging Keys
Here's the most important part of the PGP process. Before you can send a secure message, you need your recipient’s public key, and they need yours. You can export your public key from the plugin (it just looks like a block of text) and send it to your contact in a normal, unencrypted email.
They'll import your key into their PGP tool, and you'll need to do the same with their key. Once you’ve both got each other’s public keys saved, you’re ready to communicate securely.
Composing an Encrypted Email in Gmail
With the plugin running, you’ll notice a new button in your Gmail compose window. Write your message as you normally would, then click the "Encrypt" button. The plugin automatically finds the right public key for your recipient, scrambles the message content, and replaces it with a block of encrypted text.
To anyone else, it looks like gibberish. But to your recipient, all they have to do is enter their passphrase, and the plugin instantly decrypts the message back into its original form. It takes a little more setup, but it gives you incredible security without ever leaving the inbox you know and trust.
Building Habits for Long-Term Email Security
Picking the right tool for sending secure email is a great start, but the technology itself is never the whole story. Real, lasting security comes from building consistent, conscious habits around how you handle sensitive information day in and day out.
Think of it like this: your encryption software is a top-of-the-line deadbolt on your front door. It’s fantastic, but it only works if you actually remember to lock it. Your daily practices are what turn a powerful tool into a genuinely secure workflow. This means getting past the "set it and forget it" mindset and actively participating in your own digital safety.
It all starts with the basics, like creating genuinely strong passphrases and enabling two-factor authentication (2FA) everywhere you can.
Spotting the Phishing Scams That Fool Even the Pros
Listen, even the most security-conscious people can get tricked by a clever phishing scam. It happens. Security expert Troy Hunt once wrote a fascinating breakdown of how a sophisticated phish fooled him into handing over his Mailchimp credentials. The attackers didn't use obvious spelling mistakes; they used social engineering to create a false sense of urgency that made him bypass his usual critical thinking.
Phishing attacks are so effective because they exploit human psychology, not just software vulnerabilities. They create a sense of panic or curiosity that makes us act before we think.
This is exactly why constant vigilance is so important. Get in the habit of questioning any email that demands immediate action or asks for credentials, especially if it feels rushed. One of the most critical habits you can build is to never click login links directly from an email. Instead, always open your browser and manually type in the website's address. That's the only way to be sure you’re on the real site.
Managing Your Keys and Knowing When a Link is Better
Your private encryption keys are, for all intents and purposes, the keys to your digital kingdom. You have to guard them carefully.
Here’s what I always tell people:
- Backup Your Keys: Make a secure backup of your private key and its passphrase. A good password manager or an encrypted external drive are both solid options. If you lose your private key, you lose access to all of your encrypted data.
- Keep Your Passphrase Separate: Whatever you do, don't store your key and its passphrase in the same place. That’s like taping your house key to the front door.
- Revoke a Compromised Key: If you have any reason to believe your key has been compromised, you need to revoke it immediately. This prevents anyone from using it to impersonate you.
When it comes to large or extremely sensitive files, attaching them to an email—even an encrypted one—isn't always the smartest move. It's wise to think beyond just email and develop a broader strategy for secure document sharing to protect all your important data. Sending a secure link from a trusted cloud service often gives you far more control, like setting download limits or revoking access later on. That's a huge security advantage.
Common Questions About Sending Secure Email
Once you start using encrypted email, a few real-world questions almost always pop up. It's one thing to understand the theory, but it's another to navigate the practical side of things. Let's tackle some of the most common points of confusion I hear from people.
Can Someone Read My Secure Email in Their Regular Gmail Inbox?
Yes, they absolutely can, but it's not going to look like a normal email. When you send a message with end-to-end encryption to a standard inbox like Gmail or Outlook, your recipient gets a notification email instead of the message itself.
That notification contains a secure link. When they click it, they're taken to a private web portal where they can view your message. To get in, they'll need a password that you've shared with them through a separate channel (a quick text message is perfect for this). This little extra step is what keeps the message truly secure from start to finish, even if their own inbox isn't encrypted.
This method is a smart workaround that bridges the gap between secure and non-secure email services. It ensures true end-to-end encryption is never broken, making secure communication practical for everyone, not just tech experts.
Isn't Gmail's Confidential Mode the Same Thing?
This is a big one, and the answer is a firm no. They are fundamentally different. Gmail's Confidential Mode is a handy feature for adding a layer of control, but it's not true encryption.
With Confidential Mode, you can:
- Set an expiration date so the email disappears later.
- Block the recipient from forwarding, copying, or printing.
- Add an SMS passcode for an extra verification step.
But here's the catch: Google can still read the content of those emails on its servers. With true end-to-end encryption (E2EE), mathematically, no one besides you and your recipient can decipher the message. Not your provider, not Google, nobody. For anything truly sensitive, E2EE is the only way to go.
Should I Just Encrypt Every Single Email I Send?
Definitely not. That would be completely impractical and, frankly, a bit of a headache for everyone involved. The real skill is learning to be selective and thinking with a security-first mindset.
Before you hit send, just ask yourself one simple question: "Does this message contain sensitive information?"
If the answer is yes, encrypt it. This is a must for things like:
- Financial details (bank statements, credit card info).
- Personal health records or sensitive legal documents.
- Proprietary business data, contracts, or client credentials.
- Any personally identifiable information that could be risky if exposed.
For casual chats, meeting invites, or newsletters, standard email is perfectly fine. It's all about building the habit of pausing for a second to assess the risk.
Ready to take control of your inbox with true privacy and security? Typewire offers private, encrypted email hosting without ads, tracking, or data mining. Start your free 7-day trial and experience what secure communication should be. Learn more at https://typewire.com.
A Practical Guide to Sending Secure Mail
Posted: 2025-09-17
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31