How to Password Protect Email: Expert Tips & Easy Steps

You can password protect an email in a few key ways. Your email client probably has built-in tools like Gmail's Confidential Mode, you can encrypt individual attachments before you hit send, or you can go all-in with a dedicated secure email provider.
Each of these methods adds a much-needed layer of security, making sure your sensitive information lands only in front of the right pair of eyes.
Why Email Security Is No Longer Optional
It’s almost second nature to fire off an email with sensitive information. We send financial details, personal IDs, and confidential business plans through the digital ether every single day, often without a second thought.
But a single unsecured message can have devastating consequences. Imagine a freelance designer emailing an unencrypted invoice with their banking info, only to have it intercepted and drained. Or a small business owner sharing a new product blueprint that gets leaked straight to a competitor. These aren't just far-fetched scenarios; they're very real risks.
This is exactly why knowing how to password protect an email has become a critical modern skill, not just another task for the IT department. It’s about taking control of your digital conversations and building trust with every message you send.
Quick Comparison of Email Protection Methods
Before we dive deeper, here's a quick overview of the main methods to password protect your emails, outlining their core function and when you should use each one.
| Method | Primary Function | Best For |
|---|---|---|
| Email Client Features | Adds a basic layer of protection like expiration dates and SMS passcodes directly within your existing email account (e.g., Gmail, Outlook). | Sending casually sensitive information quickly and easily without needing new software. |
| Attachment Encryption | Secures individual files (like PDFs or ZIP folders) with a password before you attach them to an email. | Protecting specific documents that contain highly sensitive data, like contracts or financial statements. |
| Secure Email Providers | Offers end-to-end encryption for the entire email, ensuring the message and attachments are secure from sender to recipient. | Consistently handling highly confidential information, such as legal, medical, or financial communications. |
Choosing the right method really depends on what you're sending and who you're sending it to. For a quick, one-off sensitive file, encrypting the attachment might be enough. But if you're a lawyer or accountant, a secure email provider is a much better fit for your day-to-day workflow.
The Growing Threat Landscape
The sheer number of digital credentials we juggle makes security a monumental challenge. The average person is now trying to manage over 250 passwords—a huge jump that makes keeping them all unique and strong a near-impossible task.
It's no surprise, then, that cybersecurity surveys show nearly half of all people have had a password stolen, with 35% of breaches traced back to weak passwords. To make things worse, 27% of stolen credentials are swiped from large company data breaches, which can have a ripple effect that compromises your email security.
Understanding the severe consequences of credential leaks is the first step to appreciating why proactive protection is so important. A single compromised password can set off a domino effect, giving a stranger access to a treasure trove of your personal and professional data.
Adopting a Security-First Mindset
Shifting to a more secure email habit really just means thinking a little differently about your digital communications. It’s about consciously deciding which information needs that extra layer of protection and then grabbing the right tool for the job.
A security-first mindset means treating every email as potentially sensitive until proven otherwise. It’s a shift from a reactive stance—cleaning up after a breach—to a proactive one where protection is just part of your workflow from the get-go.
This change in perspective is the true foundation of a solid security strategy. It encourages you to use tools that verify identity and limit access by default, rather than leaving the door wide open.
Adopting this mindset is the single most important step in safeguarding your digital life. To see how these ideas apply on a much larger scale, check out our guide on https://typewire.com/blog/read/2025-08-07/what-is-zero-trust-security-and-why-it-matters.
Using Your Email's Built-In Security Features
You don't always need to hunt down a third-party tool to lock down your emails. Truth be told, the most popular email clients out there—think Gmail and Outlook—already have some pretty powerful security features baked right in. People often overlook them, but they're an effective first line of defense to password protect an email with just a few clicks.
Gmail's Confidential Mode, for instance, is a fantastic tool for adding a ticking clock to your messages. It lets you set an expiration date, and once that time passes, the email becomes unreadable. You can even pull the plug and revoke access manually after you’ve hit send, giving you an impressive amount of control.
Not to be outdone, Microsoft 365 has its own robust encryption options. It gives you the power to stop recipients from forwarding, printing, or even copying the content of your email. These native features are usually the fastest way to add a solid layer of security.
Activating Gmail's Confidential Mode
Whenever I need to send something sensitive through Gmail, like temporary login details or a private document that needs a quick review, Confidential Mode is my go-to. It isn't true end-to-end encryption, but it throws up some serious roadblocks for anyone trying to snoop.
It’s surprisingly easy to use. Just compose your email like you normally would, but before you send it, look for the little padlock icon with a clock on it in the bottom toolbar. A click on that opens up the Confidential Mode settings, letting you lay down the rules for your message.
This quick visual shows just how simple it is to flip the switch on these features and turn a standard email into a much more secure one.
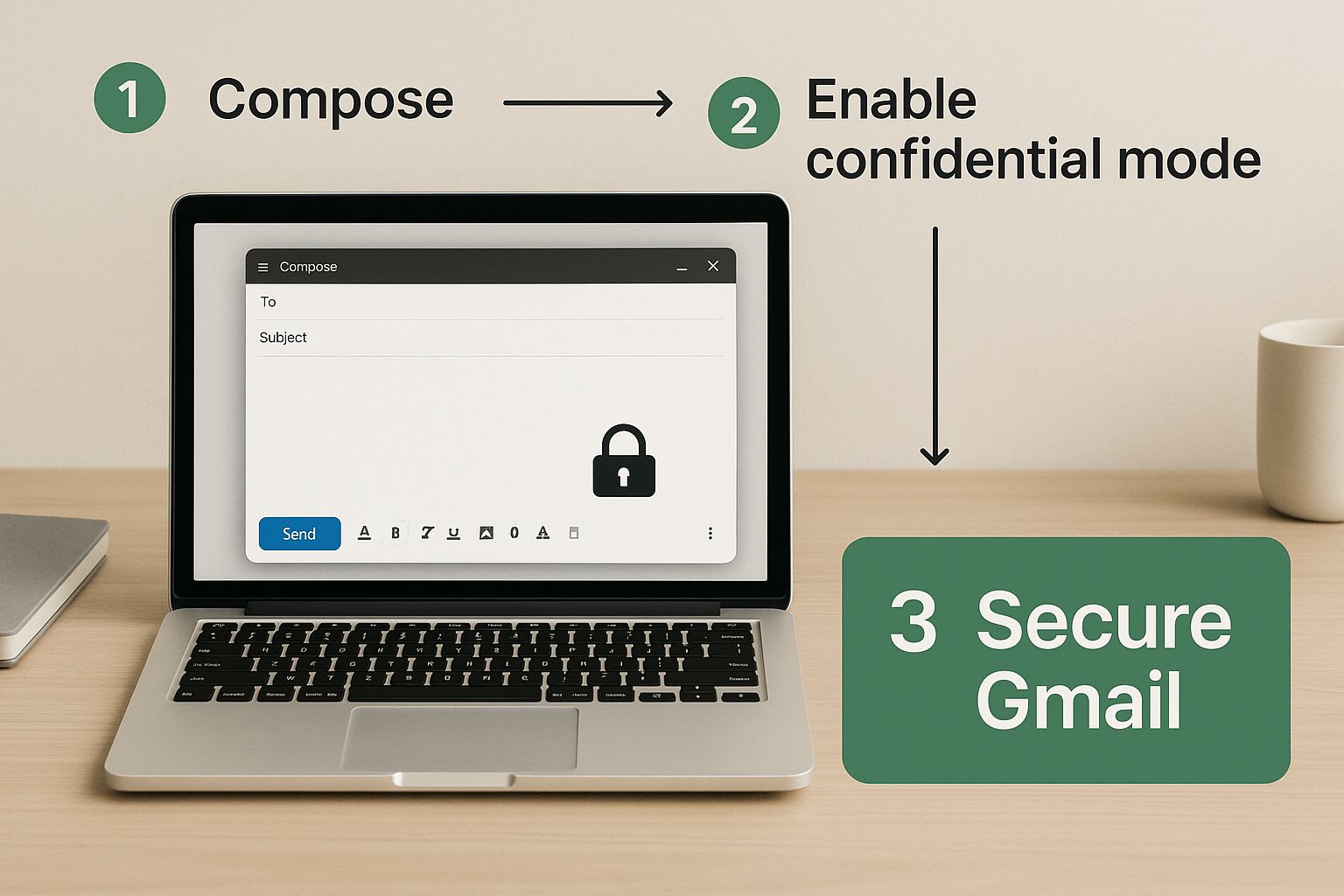
The best part? This security is literally one click away, right inside the compose window you use every single day.
One of the strongest options here is the SMS passcode requirement. When you select this, Gmail sends a one-time code to the recipient's phone. They have to enter that code to even open the email. This is a great two-factor approach; even if someone hacks their inbox, they can't get into your specific message without having the person's phone in their hand.
This method is perfect for situations where you need to be sure you're dealing with the right person. Think about sending a contract to a new client—requiring an SMS passcode adds a strong layer of assurance that only they are seeing the terms.
Choosing the Right Protection in Outlook
If you're in the Microsoft ecosystem, both Microsoft 365 and the newer versions of Outlook offer direct email encryption. But you have a couple of important choices to make. You’ll usually find these settings under an "Encrypt" button or tucked away in the "Options" tab of a new message.
Knowing the difference between them is crucial for picking the right level of security.
- Encrypt-Only: This does exactly what it says—it encrypts the message. If your recipient also uses Microsoft 365 or Outlook.com, they can read it without a hitch. Everyone else gets a secure link to view the message online.
- Do Not Forward: This setting includes the same encryption but also adds some strict rules. It physically stops the recipient from forwarding, printing, or copying anything from the email, effectively locking the information inside that message.
"Encrypt-Only" is great for general privacy. But if I'm sending an internal memo with sensitive company data, "Do Not Forward" is the obvious choice.
For a deeper dive into all the different ways to lock down your messages, our guide on how to password protect an email securely has some really valuable insights. While these built-in tools are incredibly handy, remember they're just one piece of a comprehensive security puzzle.
Securing Attachments Before You Hit Send
While locking down the email body is a good start, the real prize for a hacker is usually tucked away in the attachments. Think about it—contracts, financial reports, personal ID scans, and confidential project plans are the kinds of things we attach every day. Learning to password-protect these files before they even leave your outbox is a game-changer for security.
This strategy works so well because it decouples the file's security from the email itself. If someone compromises the recipient's inbox, they still can't get into your document without a completely separate password. It’s like sending a locked safe through the mail; even if the package gets intercepted, the contents are still protected.
Locking Down Your PDFs
PDFs are a universal standard for sharing important documents, and the good news is they come with built-in security options. If you're using Adobe Acrobat, the process is simple and gives you strong encryption.
You can set a password that someone has to enter just to open the file. But you can also take it a step further by setting a separate "permissions" password. This lets you control whether someone can print, copy text, or edit the document. It's perfect for situations like sending a draft contract where you want feedback but need to prevent any unauthorized changes.
For example, imagine a real estate agent sending a purchase offer. By password-protecting the PDF, they guarantee that only their client can see the sensitive financial terms, even if the email accidentally gets forwarded to the wrong person.
Don't have a paid Adobe subscription? No problem. There are plenty of free online tools that can password-protect a PDF for you. Just make sure you're using a reputable service, since you’ll be uploading your sensitive file to their server.
Creating Encrypted ZIP Files
What if you need to send a whole batch of files at once? Maybe a folder with project mockups, a few spreadsheets, and a client agreement. Encrypting each one individually would be a huge hassle. This is exactly where a password-protected ZIP file comes in handy.
Both Windows and macOS give you ways to bundle multiple files into a single, encrypted archive.
- On Windows: You can right-click a file, go to its properties, and use the built-in "Encrypt contents to secure data" option. For more powerful encryption (like AES-256), a free tool like 7-Zip is an excellent choice.
- On macOS: You can create an encrypted archive right from the command line using Terminal. It’s a powerful, built-in way to secure a whole folder of files in one go.
This method is incredibly efficient for sending entire project folders without sacrificing security.
The Most Important Step: Sharing the Password
Here's where so many people go wrong. You can pick the strongest encryption in the world, but it's all for nothing if you make one critical mistake: sending the password in the same email as the attachment. That’s the digital equivalent of taping the key to the front of the safe you’re mailing.
The whole point of this system is to share the password through a completely separate channel.
- Text Message: A quick text or a message on an end-to-end encrypted app like Signal or WhatsApp is a great option.
- Phone Call: A simple phone call is one of the most direct and secure ways to relay a password. There’s no digital trail left behind.
- In-Person: If you're dealing with local clients or colleagues, sharing the password face-to-face is unbeatable for security.
By separating the locked file from its key, you create a simple two-factor system that makes it exponentially harder for anyone to access your sensitive information. This last step isn't just a suggestion—it's absolutely essential.
Exploring Dedicated Secure Email Services
When you're dealing with truly sensitive information, the built-in security features of standard email clients just won't cut it. For professionals like lawyers, healthcare providers, or anyone handling confidential client data, this is the point where you need to look at dedicated secure email services. These platforms are built from the ground up with privacy and encryption as their absolute priority, offering a level of protection that a standard provider simply can't match.
The key technology here is end-to-end encryption (E2EE). Think of it like sending a physical package in a locked box where only the recipient has the key. Your message gets scrambled on your device and stays that way until your recipient opens it on theirs. Nobody in the middle—not your internet provider, not even the email service itself—can peek inside.
Getting to Know the Key Players
The secure email space has a few major players, each offering a slightly different flavor of security. Some are designed to be a complete replacement for your current inbox, while others act as powerful add-ons that beef up the security of the tools you already use.
-
Proton Mail: Based in Switzerland, a country known for its rock-solid privacy laws, Proton Mail is one of the most recognized names in secure email. It automatically applies end-to-end encryption for any messages sent between Proton Mail users. If you're emailing someone on a different service, you can send them a password-protected link to view the secure message.
-
Virtru: If you're not looking to switch providers, Virtru is an excellent choice. It’s an add-in that integrates directly into your existing Gmail or Outlook inbox, layering powerful E2EE on top of the platform you're already comfortable with.
Many of these services have free tiers for personal use, with more robust paid plans available for businesses that need advanced features and support.
Feature Comparison of Secure Email Solutions
Choosing the right tool can feel overwhelming, so it helps to see a direct comparison. This table breaks down some of the most popular third-party email encryption solutions, giving you a clear view of their features, encryption methods, and pricing to help you decide.
| Service | Encryption Type | Key Feature | Pricing Model |
|---|---|---|---|
| Proton Mail | End-to-End & Zero-Access | Swiss-based privacy, self-destructing emails | Freemium |
| Virtru | End-to-End Encryption | Integrates with Gmail/Outlook | Subscription-based |
| Tutanota | End-to-End Encryption | Encrypts calendar and contacts | Freemium |
| Mailvelope | PGP (Browser Extension) | Open-source, works with existing webmail | Free (Open Source) |
Ultimately, the best service for you depends on your workflow. Do you want a brand-new, secure ecosystem like Proton Mail, or do you prefer to enhance your current setup with something like Virtru?
Unique Features That Give You Control
Beyond standard encryption, these platforms often come packed with features that give you granular control over your messages. One of my favorites is the self-destructing email. You can set a timer, and once it expires, the email is gone for good. It's incredibly useful for sharing temporary info like a Wi-Fi password or a one-time access code.
Another game-changer is the ability to revoke access to an email after you’ve sent it. We’ve all had that heart-stopping moment of sending something sensitive to the wrong person. With this feature, you can simply pull back access, making the message unreadable. These are the kinds of advanced controls that really define how to password protect an email in a modern, professional context.
The real value of these dedicated services is that they shift the security burden from you to the platform itself. Encryption becomes the default setting, not an extra step you have to remember, which goes a long way in preventing accidental data leaks.
Of course, even the best tools can be undermined by poor user habits. It's wild to think about, but studies show that 36% of people still write their passwords down on paper, and a staggering 79% use weak, predictable passwords. You can find more fascinating (and slightly terrifying) details on these password habits on spacelift.io. This just goes to show why services that make strong security automatic are so important—they protect us from ourselves.
Building a Truly Secure Email Strategy

Knowing how to lock down a single email is a great start, but real, lasting security comes from building better habits around your entire email account. Think of it this way: locking your front door is good, but having strong windows and an alarm system is even better. It’s about creating layers of defense.
This means shifting your focus from securing individual messages to fortifying the very foundation of your email world. The goal is to build a system where one weak link—like a stolen password—doesn't bring everything crashing down.
Adopt a Password Manager
Let's be honest, no one can create and remember dozens of unique, complex passwords for every website they use. It’s just not humanly possible. This is exactly why a good password manager isn't just a nice-to-have; it's essential.
These tools do the heavy lifting for you. They generate incredibly strong, random passwords for each account and store them in an encrypted vault. When you need to log in, they fill in the details automatically. This single-handedly solves the massive security hole of password reuse. If you use the same password everywhere and one site gets breached, criminals suddenly have the keys to your entire digital life.
Enable Two-Factor Authentication
If you do only one thing from this list, make it this. Two-factor authentication (2FA) is your account’s best friend. It requires a second piece of proof—usually a code from your phone—before allowing anyone to log in, even if they have your password.
It’s simple but incredibly effective. A thief could have your password in hand, but without that second code, the door to your account stays shut. This is the single most powerful step you can take to prevent unauthorized access. The principles of layered security are universal, and you can get a better sense of how encryption works by understanding SIP TLS security, which applies similar concepts to communications.
The scale of the problem is staggering. One data leak alone exposed around 16 billion stolen credentials. Considering 94% of people admit to reusing passwords, a breach on one minor website can quickly spiral into a major personal security crisis.
Learn to Spot Phishing Scams
All the best security tools can’t protect you from a clever trick. The final line of defense is always your own judgment. Phishing scams have become alarmingly sophisticated, perfectly imitating emails from banks, delivery services, and tech companies to fool you into giving up your login details.
Cultivate a healthy dose of skepticism. Be wary of any email that demands immediate action or asks you to click a link to "verify your account." A great habit is to always hover your mouse over a link to see the real web address before you click. Even security experts can get caught off guard.
When you put these pieces together—a password manager, 2FA, and a sharp eye for scams—you're no longer just protecting one message. You're building a fortress around your entire digital identity. For more on this, check out our guide on how to https://typewire.com/blog/read/2025-07-18/send-a-password-protected-email-the-right-way.
Common Questions About Password-Protecting Emails
Even when you know the steps, putting email encryption into practice can bring up a few questions. Let's walk through some of the most common things people ask when they start locking down their messages.
What Does the Recipient Actually See?
When you send a protected email, it's not going to look like a normal message on the other end. The experience really depends on the tool you're using, and it’s smart to know what your recipient is in for.
- Gmail's Confidential Mode: They’ll get an email telling them it’s a confidential message from you. Instead of seeing the content right there, they'll have to click a link to view it in a secure web portal. If you added the SMS verification, they’ll be prompted to enter a code sent to their phone before they can see anything.
- Outlook's Encryption: If they're also on a Microsoft email account, it can be pretty smooth—sometimes the email just opens. For everyone else (like a Gmail or Yahoo user), they get a notification with a link. They'll have to click it and verify who they are to read the message on a secure Microsoft page.
- Encrypted Attachments (PDFs/ZIPs): The email itself will look totally normal, but the attachment will be locked. When they try to open that file, it will ask for the password you (hopefully) sent them separately.
It’s always a good idea to give your recipient a heads-up. A quick text or a separate, non-sensitive email saying "Hey, I just sent you a protected file, I'll call you with the password" can save a lot of confusion.
Is Just Password-Protecting a Message Enough?
Adding a password is a huge improvement over sending sensitive info in plain text, but it's not a silver bullet. Think of it as just one important layer of your security.
A password on an email attachment protects that specific file. It does nothing to stop someone from gaining access to your actual email account and causing all sorts of other problems.
That’s why you have to pair message encryption with strong account security. This means using a unique, complex password for your email (a password manager is great for this) and, most importantly, turning on two-factor authentication (2FA). This combination is what truly secures your communications—you're not just locking one file, you're securing the whole system.
Ready to take control of your inbox with a platform built for security from the ground up? Typewire offers private, ad-free email hosting that puts you in charge of your data. Start your free 7-day trial today and experience truly secure communication!
How to Password Protect Email: Expert Tips & Easy Steps
Posted: 2025-09-04
The 12 Best Email Clients for Mac in 2026: A Guide to Privacy and Security
Posted: 2026-02-24
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31