Sending Secure Emails: Your Complete Protection Playbook

Why Your Emails Are Sitting Ducks (And What It Really Costs)
Here's a hard truth most people don't think about: your standard email is basically a postcard. Imagine writing sensitive info on the back of a postcard and dropping it in the mail. It passes through countless hands (or servers, in this case), and anyone along the way can read it. This isn't an exaggeration; it’s just how basic email works.
It's easy to fall into the "it won't happen to me" trap, but that's a risky bet. Working in this field, I hear the horror stories all the time. One that sticks with me is about a company that lost a six-figure contract because a competitor intercepted an unencrypted email with their proposal details. The attacker didn't need any complex gadgets—just a spot on an unsecured Wi-Fi network.
More Than Just Money
A lost contract hurts, but the financial hit is often just the beginning. The fallout can be much worse. For businesses in fields like finance or healthcare, a single breached email can spiral into a full-blown compliance disaster. We're talking about massive fines and the fun task of publicly disclosing that you dropped the ball on client data. It's not just about the money you lose; it's the credibility that vanishes.
And this problem isn't getting smaller. The amount of email flying around the internet is staggering, with some estimates predicting over 523 billion emails sent per day by 2030. You can see more detailed email traffic projections here. Each one of those messages is a potential weak spot if not properly secured, which is why sending secure emails is no longer optional—it's a core business practice.
The Hidden Costs of a Breach
Even after you’ve dealt with the fines, there’s the reputational damage, which can stick around forever. Once your clients or partners find out their confidential information was exposed on your watch, rebuilding that trust is a massive uphill battle. For entrepreneurs and creators, it's even more direct—an intercepted email could mean watching a competitor launch your big idea before you ever get the chance.
Decoding Email Encryption Without The Technical Jargon

Now that we understand the risks, let's talk about the fix. And don't worry, we can do this without getting lost in technical weeds. At its heart, "encryption" is just a way of scrambling a message so only the intended recipient can read it. Think of it as putting a letter in a special locked box before you even drop it in the mail. The most important part of this whole process is knowing exactly who holds the key.
Transport Security vs. End-to-End Encryption
Most email services you use daily rely on Transport Layer Security (TLS). Picture your email traveling inside an armored truck on its way between servers—it’s safe while on the road. The problem is, once it arrives at the destination server, the server's owner (like Google or Microsoft) can still read it. TLS protects your message in transit, but not where it’s stored.
For genuine privacy, what you really need is End-to-End Encryption (E2EE). This is a completely different ballgame. Using our analogy, E2EE is like putting your letter inside your own personal safe before it ever goes into the armored truck. Only you and your recipient hold the unique key to that safe. To your email provider and any potential eavesdroppers, the message is just an unreadable, locked box. This is the core of how you send secure emails that are truly private.
To make this clearer, let's break down the most common encryption methods you'll encounter. This table compares TLS, PGP, and S/MIME side-by-side so you can see where each one shines.
| Encryption Type | Security Level | Ease of Setup | Best For | Compatibility |
|---|---|---|---|---|
| TLS | In-Transit Only | Automatic (Server-Side) | Basic, everyday email protection | Universal (Standard for most email) |
| PGP | High (End-to-End) | Complex (User-managed keys) | Individuals, journalists, activists | Requires specific software/plugins |
| S/MIME | High (End-to-End) | Moderate (Often managed by IT) | Corporate and government environments | Built into many corporate email clients |
As you can see, while TLS is a great baseline, it doesn't offer the same impenetrable privacy as E2EE methods like PGP or S/MIME. The real decision often comes down to balancing convenience against the need for absolute security.
The Main Players: PGP and S/MIME
The two heavyweights in the end-to-end encryption world are PGP and S/MIME. Pretty Good Privacy (PGP) is a time-tested, open standard celebrated for its robust security, making it a favorite among privacy advocates and individual users. On the other hand, S/MIME is more typically found in corporate settings, where digital certificates are managed centrally by an IT department.
Both methods are incredibly powerful, but they share a common challenge: security depends entirely on how well the encryption keys are managed. For the average user, generating, sharing, and protecting these digital keys can feel overwhelming and impractical for daily use.
This exact complexity is fueling massive growth in the email security market. The industry is projected to expand from $7.75 billion in 2024 to over $40 billion by 2035, driven by privacy regulations and ever-present cyber threats. You can discover the full market forecast here. People simply need security that works without the headache.
Ultimately, it all comes back to the keys. Losing an encryption key is the digital version of losing the only key to your house. A service that simplifies this process makes secure email a practical tool for everyone, not just a niche product for tech experts.
Finding Your Perfect Secure Email Match

While you could set up something like PGP yourself, the technical hurdles can be a real headache. Thankfully, a whole market of secure email providers like ProtonMail, Tuta, and Typewire has emerged to handle the heavy lifting. The challenge is no longer about managing complex encryption keys but about choosing the right service that makes sending secure emails feel as natural as any other part of your workflow.
What to Look for Beyond the Marketing Hype
The absolute most important feature you should look for is zero-knowledge encryption. This isn't just a fancy term; it's a fundamental guarantee that the provider themselves cannot access your encryption keys. They store your encrypted emails, but you, and only you, hold the key. Even if their servers were compromised, your messages would just be a jumble of unreadable data.
Another critical detail is server jurisdiction. The physical location of a provider's servers determines which government's laws and data requests they must follow. Opting for a service based in a country with strong privacy laws, like Switzerland or Germany, adds a significant layer of legal protection for your data. It’s a small detail with massive implications for your digital sovereignty.
It's clear that users and businesses are taking this seriously. The global email security market was valued at US$18.5 billion in 2024 and is expected to climb to US$24 billion by 2030. This growth shows a massive shift towards prioritizing genuine email protection. You can discover more insights on this trend here.
To help you sift through the options, here’s a breakdown of what some of the most popular providers offer.
| Provider | Encryption Standard | Free Tier | Storage | Key Features | Best For |
|---|---|---|---|---|---|
| ProtonMail | PGP, End-to-End | Yes, 1 GB Storage | Up to 500 GB | Integrated Calendar, Drive, and VPN | Individuals seeking an all-in-one privacy ecosystem. |
| Tuta (formerly Tutanota) | AES & RSA, End-to-End | Yes, 1 GB Storage | Up to 1 TB | End-to-end encrypted calendar, "green email" focus | Privacy advocates who want a simple, highly secure service. |
| Typewire | PGP, End-to-End | Yes, with limitations | Scalable Plans | Advanced team management, custom domains, secure file sharing | Businesses and teams needing collaborative secure communication. |
As the table shows, your choice depends heavily on your specific use case. While all provide strong encryption, the surrounding features and focus areas differ significantly.
Key Features for Real-World Use
Beyond the core security, a few practical features will make or break your day-to-day experience with a secure email provider.
- Custom Domain Support: Absolutely essential if you're a business or professional wanting to send secure emails from your own branded address (e.g., you@yourcompany.com).
- Smooth Migration: A good service provides tools to easily import your existing emails and contacts, so you don't have to start from scratch.
- Team Management: For businesses, you'll need an intuitive dashboard to add or remove team members, set permissions, and manage billing for multiple users.
- Transparent Policies: A provider you can trust will have a privacy policy and terms of service that are easy to find, read, and understand. No hidden clauses or confusing language.
The best provider is the one that fits your personal or business needs like a glove. Are you a journalist protecting sources, a small business sharing client contracts, or just an individual who values their privacy? Figuring that out is the first step. For a deeper dive into the setup process, check out our guide on mastering safe communication.
Getting Your Secure Email System Up And Running
So, you’ve picked your secure email provider. The next move is to build out your new, private communication hub. This starts the moment you create your account, where your privacy decisions have an immediate impact. Think carefully about the personal info you share during signup. Many privacy-conscious users even use anonymous payment methods to keep their digital trail as clean as possible right from the start.
Fortifying Your New Account
Your password is the first line of defense, but it should never be the only one. The moment your account is active, set up two-factor authentication (2FA). Most secure email services work with authenticator apps like Authy, which are a huge security step up from SMS codes. You'll also get a set of recovery codes during this setup. Do not just click past this. Print these codes out and stash them somewhere safe, like a physical safe at home. It's a frustratingly common mistake to get locked out of your account simply because you lost your phone, and it's completely avoidable.
This flow chart gives you a bird's-eye view of what happens when you send your first encrypted message.
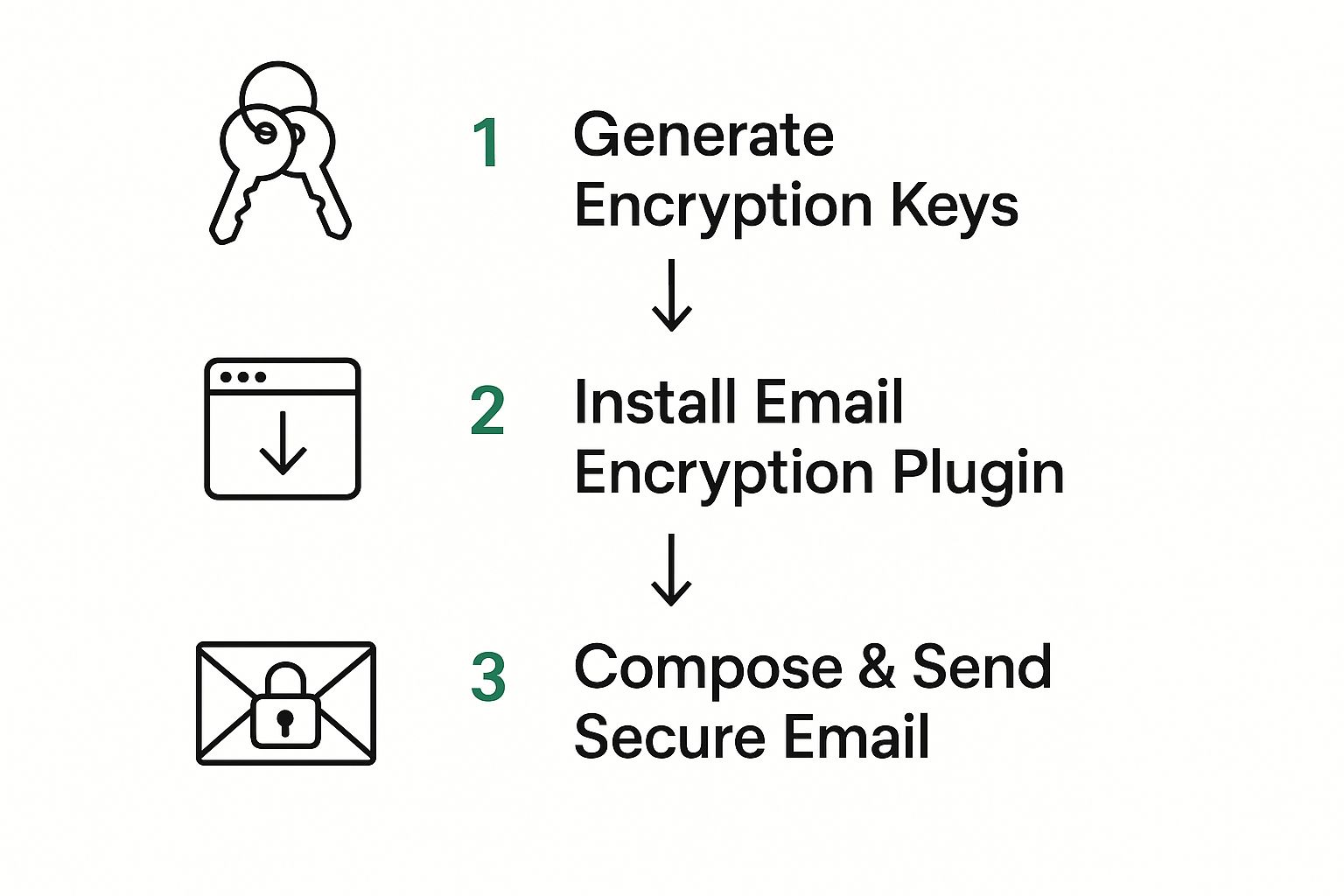
What's great is that the most complex part—the key generation—is usually handled for you by the service. This lets you focus on what you're actually there to do: communicate privately.
Connecting Your Apps
For many, the easiest path is to just use the provider's web client. There's no setup involved beyond logging in. A service like Typewire, for instance, provides a slick web interface that makes the whole encryption process feel invisible.

The main point is that today’s secure email platforms are built to feel familiar, removing the old technical hurdles. If you're someone who prefers a dedicated desktop app, however, most services have guides for setting up clients like Thunderbird or Apple Mail. This setup typically involves creating an app-specific password, which adds another layer of security for that connection.
Finally, remember that moving over is a gradual process. There's no need to switch everything and everyone in one go. A good starting point is to import your contacts. Then, begin using your new account for your most sensitive emails, letting your contacts know about your new secure address as you go. For everything else, you can set up forwarding from your old email. This slow-and-steady approach helps ensure you don't miss anything important while you build out your new private space.
Mastering Daily Secure Email Workflows That Actually Work

Having a secure email account is a fantastic start, but let's be honest—making it part of your everyday routine is where the real work begins. This is the point where the idea of sending secure emails bumps up against the reality of a busy workday. The aim is to get so comfortable with the tools that security becomes second nature, not another tedious task on your to-do list.
Communicating With the Outside World
One of the first questions people ask is, "How do I send an encrypted email to someone using a regular Gmail or Outlook account?" You can't just send them a fully locked-down message and expect it to open. Instead, secure providers like Typewire have a clever workaround. They generate a secure, one-time-use link to the message.
Your recipient gets an email notification, clicks the link, and views your message in a protected web portal. Usually, they'll need a password that you've shared with them through another channel, like a quick text message. Think of an accountant sending sensitive tax forms to a client. This method keeps the documents completely private without forcing the client to sign up for a new service. It's a smart balance between airtight security and real-world convenience.
Creating Security Protocols That Stick
When you're working with a team, a lack of clear rules can make your security efforts fall apart. If encryption is treated as "optional," it will almost always be skipped in a rush. The secret is to create simple, straightforward protocols that don't add friction to anyone's day.
For example, a law firm could establish a hard-and-fast rule: all communication involving a client's case must be sent with end-to-end encryption. No exceptions. A marketing team might have a different approach, only requiring encryption when discussing project launch dates or confidential campaign strategies.
So, how do you make these protocols stick? Here are a few practical ideas that have proven effective:
- Adopt a "when in doubt, encrypt" mindset. If you wouldn't want the information on a public forum, it belongs on your secure platform.
- Create simple data labels. Sorting information into buckets like Public, Internal-Only, or Confidential helps your team make quick, smart decisions about which email tool to use.
- Make it part of day one. Secure communication workflows should be a standard part of training for every new hire, right from their first day.
By building these habits, security stops being a hurdle and becomes a reflex. To dive deeper, you can explore our tips for private and safe communication to help reinforce these practices. At the end of the day, the most effective security workflow is the one that your team will actually follow without a second thought.
Advanced Protection Tactics And Staying Ahead Of Threats
So, you've mastered the basics of sending secure emails. That's a huge step, but true digital privacy goes a layer deeper. It's not just about hiding the message content; it's also about obscuring the patterns you create. Even with flawless end-to-end encryption, someone could still see who you're emailing and when. This is metadata, and for a determined adversary, it can tell a surprisingly detailed story through traffic analysis.
Protecting Your Patterns
Sophisticated snoops can use methods like timing correlation attacks to link your encrypted messages to real-world happenings. The defense against this is a classic intelligence technique: compartmentalization. This simply means using separate, isolated email identities for the different areas of your life. You might have one for sensitive work, another for private financial communications, and a third for personal advocacy.
By splitting your digital life this way, you shatter your digital footprint. It makes building a complete profile of your activities incredibly difficult. Think of it as wearing a different disguise for every secret meeting; if one identity is ever exposed, the others remain secure and anonymous.
Proactive Security Hygiene
Staying safe from digital threats isn't something you set up once and forget. It's a collection of smart, ongoing habits. One of the most effective habits is key rotation, which means you generate new encryption keys from time to time. This simple practice dramatically limits the damage if an old key were ever to be compromised.
Another crucial habit is to keep your email client and all related security software completely up-to-date. Patches and updates are released for a reason, and they often close security holes you might not even know about. The final piece is staying aware of how these systems work. The more you know, the better you can protect yourself without feeling overwhelmed. A great place to start is by reviewing and understanding the core secure email protocols.
Key Takeaways
We've covered the risks and the tools, but real, lasting security is all about building smart, repeatable habits. This is where theory turns into practice. It’s not about becoming a cryptography expert overnight, but about weaving a few simple, powerful actions into your daily routine to protect your most important conversations.
Putting Secure Email Into Practice
Forget the complex technical manuals. Here are the core habits that will make the biggest difference in your communication security, starting right now.
-
Choose a Zero-Knowledge Provider: This is my number one rule. A service that uses zero-knowledge encryption is the only way to guarantee that you, and only you, can read your emails. Take a few minutes to read their privacy policy and see where their servers are located. A provider based in a country with strong privacy laws gives you an essential legal shield.
-
Lock Down Your Account From Day One: Before sending a single message, set up two-factor authentication (2FA). Make sure to use an authenticator app, as it's far more secure than codes sent over SMS. Here’s a crucial tip: print out your recovery codes and store them somewhere safe offline. This simple step ensures a lost phone doesn't turn into a lost account.
-
Communicate Securely with Everyone: What happens when you need to email someone using a standard service like Gmail? You don't have to abandon security. Use your provider’s feature to send a password-protected link to your message. This keeps the content encrypted, while your recipient can still access it easily. Just be sure to share the password through a separate channel, like a quick text message.
-
Start Small and Build the Habit: Don't try to move your entire digital life over in one go—that's a recipe for feeling overwhelmed. Instead, begin by using your new secure account for your most critical conversations, like those with your lawyer, accountant, or business partners. This approach helps make security a reflex, not a chore.
True security isn't just about the technology; it's about the discipline to use it correctly every single day.
Ready to build your communication fortress on a foundation of privacy? Discover how Typewire makes secure email simple and start your free trial today.
Sending Secure Emails: Your Complete Protection Playbook
Posted: 2025-06-18
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16