Email Security for Business Guide

Effective email security for business isn't just about software or IT checklists. At its heart, it's a comprehensive strategy to protect your company's most used communication channel from being turned against you. It's about securing your digital front door.
Your Company's Digital Front Door
Imagine your company's email system as the main lobby of your office building. It’s where everything and everyone comes and goes—sensitive client data, financial reports, strategic plans, and everyday conversations. You wouldn't leave your physical lobby unguarded, and the same principle applies here.
A solid email security strategy is your digital gatekeeper. It's the security guard who checks IDs, inspects packages, and knows the difference between a welcome visitor and a threat. Without that guard on duty, you’re leaving your organization wide open to financial scams, data theft, and the kind of reputational damage that can take years to repair.
Why Every Message Matters
It’s easy to think that only emails containing invoices or contracts are high-risk. That's a dangerous assumption. Attackers are masters of disguise, crafting malicious emails to look like mundane shipping notifications or casual team updates. They know that blending in with the noise of a busy inbox is the best way to catch someone off guard.
This is exactly why a simple spam filter isn't enough anymore. You need a multi-layered defense that addresses threats from every angle.
A strong defense isn't about building one impenetrable wall; it's about creating multiple layers of security. If one layer fails, another is there to catch the threat, protecting your organization from the inside out.
The Core Pillars of Business Email Security
A truly resilient security plan is built on several fundamental components that work in tandem. Think of them as the pillars holding up your entire security structure, ensuring your digital front door is locked, monitored, and reinforced.
A successful strategy always includes:
- Threat Prevention: This is your first line of defense, proactively stopping threats like phishing and malware before they even have a chance to land in an employee's inbox.
- Authentication and Identity Verification: This pillar focuses on making sure senders are who they say they are. It prevents criminals from faking your company's domain or impersonating a trusted executive.
- Employee Awareness and Training: Your team is a critical part of your defense. Proper training gives them the skills to spot suspicious messages, turning your workforce into a human firewall.
- Incident Response: No defense is perfect. This is your action plan for when a threat gets through, allowing you to contain the breach quickly and minimize the damage.
Below is a quick breakdown of how these pillars support a comprehensive security strategy.
The Core Pillars of Business Email Security
| Security Pillar | Primary Goal | Common Tools and Methods |
|---|---|---|
| Threat Prevention | Block malicious content before it reaches the user. | Anti-spam/malware filters, sandboxing, link scanning. |
| Authentication | Verify sender identity and prevent spoofing. | SPF, DKIM, and DMARC protocols. |
| Employee Awareness | Turn employees into an active security asset. | Phishing simulations, regular training, clear reporting channels. |
| Incident Response | Contain and mitigate attacks that bypass defenses. | Automated remediation, threat intelligence, clear response plans. |
By weaving these elements together, you move from simply reacting to problems to proactively defending your organization. This approach doesn't just protect data; it secures your operations, your reputation, and your peace of mind.
Anatomy of a Modern Email Attack

To really defend your business, you have to get inside the head of your adversary. Modern email attacks aren't about brute-force hacking anymore; they’re about masterful deception. Attackers have shifted their focus from just targeting systems to targeting people by exploiting trust, urgency, and the simple reality of human error.
Many of these attacks sail right past traditional security filters because they don't carry any obvious malware. Instead, they weaponize social engineering—the art of psychological manipulation—to convince your employees to hand over sensitive information or authorize fraudulent payments all on their own.
The most damaging and widespread of these threats is Business Email Compromise (BEC). This isn't your typical spam. It's a highly targeted scam where an attacker convincingly impersonates someone trusted, like the CEO or a key vendor, to trick you out of money.
The Financial Threat of Impersonation
Business Email Compromise attacks have become a leading cause of financial loss for companies everywhere. In fact, research shows that BEC schemes are behind roughly 73% of all reported cyber incidents, which tells you just how common this threat has become.
Attackers often push for bogus wire transfers, with the average demand hitting a staggering $24,586. To pull this off, criminals rely on pretexting—they invent a believable story to make their request seem completely legitimate. This tactic has nearly doubled in frequency, proving just how effective it is.
It works so well because it hijacks established trust and authority, making it a critical threat that every single organization needs to take seriously.
A modern email attack is a confidence game. The attacker's goal is to win an employee's trust just long enough to trick them into making a critical mistake, such as paying a fake invoice or sharing their login credentials.
Common Attack Scenarios
So, what do these attacks actually look like in the wild? They aren't always technically complex. Their real power lies in their deceptive simplicity and their ability to create a false sense of urgency or normalcy.
Here are a few all-too-common scenarios:
-
The Fake Invoice: Someone in your accounts payable department gets an email that looks like it's from a regular supplier. Attached is an invoice with new banking details and a friendly note explaining the change. The logo, branding, and tone are all spot-on. Trying to be efficient, your employee pays the invoice, sending the money straight into a criminal's bank account.
-
The CEO's Urgent Request: A member of the finance team receives an email, seemingly from the CEO, who is "stuck in a meeting and can't be disturbed." The message demands an immediate wire transfer to close a time-sensitive, confidential deal. The pressure from the "CEO's" authority makes the employee act fast, skipping the usual verification steps.
-
Credential Phishing: An employee gets an email warning them of "suspicious activity" on their account and telling them to verify their login to secure it. The link leads to a pixel-perfect copy of your company's real login page. When they enter their username and password, they've just handed the keys directly to the attacker. For a deeper look at this, check out our guide on how to avoid phishing emails.
These examples show how attackers twist everyday business routines against you. They succeed not because of a technical breakdown, but because they so skillfully exploit the human element. This means that effective email security for business has to do more than just block malware; it must also account for the psychological tactics that make these scams so potent.
Why Your Spam Filter Is Not Enough
It’s a common mistake to think your inbox's built-in spam filter is all you need for email security for business. That's a dangerous assumption. Think of a standard filter as a bouncer at a nightclub who only checks for obvious red flags—like someone trying to bring in a weapon. It’s great at catching known malware attachments, the digital equivalent of a bulky, suspicious package.
But what about the smooth-talker who walks in confidently with no weapon at all? The one armed with a convincing story designed to get past the velvet rope? That’s what modern email attacks look like.
Attackers know the old playbook is obsolete. They've shifted from clunky viruses to "payload-free" attacks that are built to waltz right past those basic defenses. Instead of attaching a malicious file, they might send a QR code to a phishing site, a link to a legitimate cloud document with a hidden threat, or a simple but urgent request to call a "security verification" phone number.
These social engineering attacks don't ring any of the usual alarm bells because, on a technical level, the email is clean. There’s nothing to block. The real danger lies in manipulating the person reading the email—a threat signature-based detection was never designed to handle.
The Problem With Signature-Based Detection
So, how do those traditional filters work? They basically have a giant "most wanted" list. They scan incoming emails and compare files and links against a massive database of known threats. If they find a match, they block it. It’s a decent strategy for stopping widespread, cookie-cutter attacks.
But it fails spectacularly against anything new or creative.
The reality is that attackers are constantly innovating. They aren't just building new malware; they're figuring out how to weaponize legitimate online services to run their scams. By using trusted platforms for file sharing or building forms, they create links that look perfectly safe to both your employees and your security filters.
A recent analysis of over one million threats that slipped past email filters found a startling pattern: 99% of these attacks relied on phishing links or social engineering, not old-school malware. The report also highlighted a huge spike in cybercriminals misusing legitimate services, revealing a massive blind spot for security tools focused only on known bad files. You can discover more insights about these evolving threats and their impact on email security.
This is precisely where the greatest risks to your business now live. An attack that tricks an employee into handing over their login credentials or wiring money is every bit as damaging as a malware infection—and often, much harder to detect.
A Smarter Approach to Email Defense
To truly protect your business, you need a security solution that thinks less like a bouncer and more like a seasoned detective. It needs to look beyond the surface of a message and analyze the context, behavior, and intent behind every single email. This is where modern, AI-powered security changes the game.
Instead of just checking against a list of known criminals, these advanced systems get to know your organization's normal rhythm. They learn who typically emails whom, what kinds of requests are standard, and the language your team uses.
This contextual awareness allows them to spot anomalies that a signature-based filter would completely miss, such as:
- Impersonation Attempts: An email that looks like it's from your CEO but is sent from a strange new email address or at 3 AM.
- Unusual Requests: A sudden demand for a wire transfer to a brand-new bank account from a vendor you've worked with for years.
- Suspicious Language: The use of urgent, threatening, or overly emotional language designed to rush someone into making a mistake.
By focusing on behavior, these systems can identify and neutralize sophisticated social engineering attacks, even when there's no malicious file to be found. This smarter, behavior-first approach is the only way to get real protection against the full spectrum of modern email threats.
To get a better handle on these dangers, you might be interested in our complete defense guide on email security threats.
How To Build a Digital Fortress

When it comes to email security for business, there's no magic bullet. The real secret is to think like a medieval castle builder. You need to construct a digital fortress with multiple, overlapping layers of defense. A strong wall is a great start, but it's the combination of a high wall, vigilant sentries, and clear defensive protocols that makes a fortress truly impenetrable.
This approach ensures that if one defense fails or is bypassed, another is already in place to stop the threat. It’s about being proactive and protecting your organization from every angle. Let's walk through the blueprint for building that fortress, layer by layer.
Lock the Gates With Authentication
The first and most foundational layer is technology—specifically, email authentication protocols. Think of these as the official seals and signatures on your company's mail. They prove to the world that an email actually came from you, stopping attackers from slapping your good name on their malicious messages.
It’s like the difference between a handwritten return address and a unique, official wax seal. Anyone can fake the address, but only you have the seal. Protocols like SPF, DKIM, and DMARC work together to create that digital seal of authenticity.
- SPF (Sender Policy Framework): This is essentially a public list of every mail server authorized to send emails on your behalf. It’s like giving the post office a list and saying, "Only accept mail with my company's stamp if it comes from one of these specific locations."
- DKIM (DomainKeys Identified Mail): This adds a tamper-proof digital signature to every email you send. If a cybercriminal intercepts and changes your message—even by a single character—the signature breaks, telling the recipient’s email server it’s a forgery.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): This protocol is the rule-setter. It tells other mail servers exactly what to do with emails that fail the SPF or DKIM checks—whether they should be quarantined in a spam folder or rejected outright.
Putting these three protocols in place is a non-negotiable first step. It's the most effective way to shut down domain spoofing and protect your customers from phishing attacks done in your name.
Empower Your People as Sentries
Technology alone is never enough. Your employees are the sentries on the walls of your fortress, and their awareness is one of your most critical security assets. A well-trained person can spot a sophisticated threat that even the best software might miss, which is why ongoing security training is so important.
The goal isn't to scare your team; it's to empower them. Good training gives them the skills and confidence to spot and report suspicious emails. Phishing is still the number one cause of security breaches, involved in 36% of all incidents and responsible for over 3.4 billion malicious emails every single day. And considering that 94% of malware infections start with a phishing email, your team is truly your first line of defense. You can find more data on the prevalence and cost of phishing attacks from TechMagic.
Your workforce is not your weakest link; it's your most dynamic line of defense. Investing in their awareness transforms them from potential targets into active threat hunters who are part of the solution.
Standardize Your Defensive Procedures
The final layer of your fortress is a set of clear, simple, and mandatory internal procedures. These are your official "rules of engagement," designed to shut down the most common and damaging attacks, like Business Email Compromise (BEC).
Create ironclad rules for high-risk actions. For instance, any request to change vendor payment details or make an urgent wire transfer must be verified through a second channel. That means picking up the phone and calling a known, trusted contact number—never the one listed in the email—or confirming the request face-to-face.
This simple, process-driven step derails the attacker's entire game plan. It doesn't matter how convincing a fraudulent email looks if your team is required to verify it offline. These structured procedures are easy to implement and incredibly effective at preventing devastating financial fraud.
How To Choose Modern Email Security Tools
Picking the right technology partner is the final—and most crucial—piece of the puzzle. Now that you understand today's threats and the security frameworks that combat them, you're ready to find the tools that will act as a true force multiplier for your team. This isn't just about buying software; it's about investing in a solution that puts protection on autopilot, sharpens your visibility, and empowers your people.
Modern email security platforms are a world away from the simple spam filters of the past. They’re built specifically to handle the sophisticated, socially-engineered attacks that are now the biggest threat. What really sets them apart is their use of artificial intelligence to analyze behavior and context, which allows them to catch threats that don't carry any obvious malware.
Core Capabilities of a Modern Solution
When you're evaluating your options, a few features are completely non-negotiable for effective email security for business. These capabilities are designed to directly counter the attack methods we've already covered, from sneaky Business Email Compromise to zero-day phishing schemes that have no known signature.
Make sure any platform you consider delivers on these points:
- AI-Powered Threat Detection: This is the brains of the whole operation. Instead of just checking against a list of known threats, the system should analyze communication patterns, sender reputation, language, and context to spot anything out of the ordinary. This is how it catches that one convincing but fraudulent invoice or a sudden impersonation of your CEO.
- Robust Impersonation Protection: The tool has to be smart enough to identify and block attempts to mimic trusted people, whether it’s executives inside your company or key vendors you work with every day. It should be looking for subtle clues like mismatched display names, lookalike domains, and unusual sending patterns that a human eye might miss.
- Time-of-Click Link Analysis: Cybercriminals love to use links that look safe when an email first arrives, only to switch the destination to a malicious site later. Modern security doesn't just scan links on arrival; it checks them again at the exact moment a user clicks, giving you real-time protection against these weaponized URLs.
- Post-Delivery Remediation: Let's be realistic—sometimes, a threat might slip through or is only identified after it’s already in someone's inbox. An effective solution must be able to automatically find and yank those malicious emails from every user's inbox with a single click, stopping a potential disaster in its tracks.
Think of a modern security platform as a dedicated security analyst that works 24/7. It tirelessly sifts through every single message, applying advanced logic to catch threats a busy human might miss, and then gives you the power to instantly neutralize any that are found.
This image shows the very real impact of combining advanced tools with ongoing employee training. The results speak for themselves: a huge drop in risk and a big boost in security awareness.
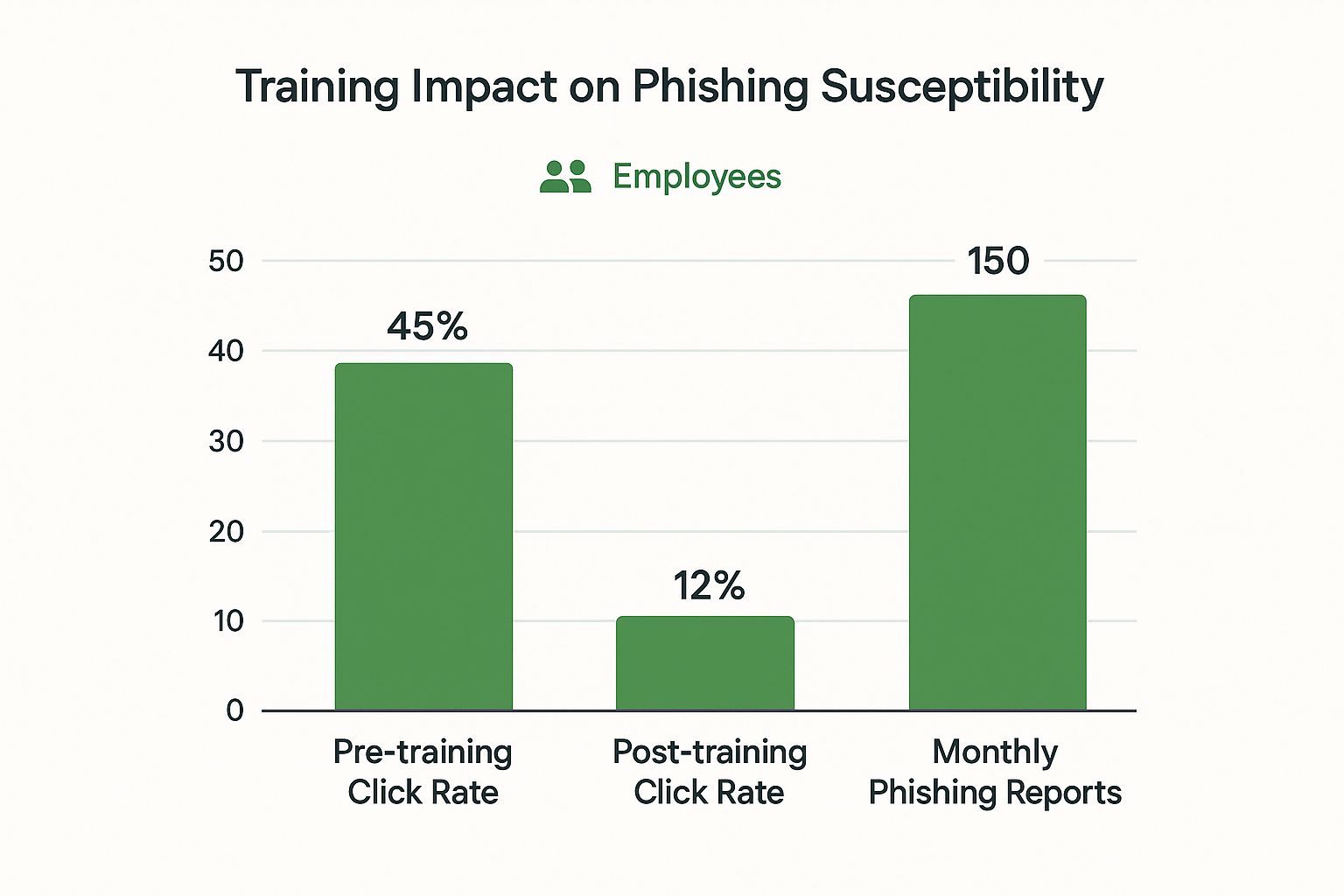
The data here makes it crystal clear. Integrating the right technology and processes dramatically lowers how susceptible your users are to phishing attacks while helping build a more proactive security culture.
Feature Comparison Traditional vs Modern Email Security
It's one thing to talk about features, but seeing them side-by-side really highlights the difference. Legacy tools were built for a simpler time, and their limitations are exactly what attackers exploit today. Modern platforms were designed to close those gaps.
| Capability | Traditional Security (e.g., Basic Spam Filter) | Modern Security Platform |
|---|---|---|
| Threat Detection | Relies on known malware signatures and blocklists. | Uses AI to analyze behavior, context, and intent. |
| Impersonation | Basic checks for domain spoofing; easily bypassed. | Advanced detection of lookalike domains & display names. |
| Phishing Links | Scans links only when the email arrives. | Scans links at time-of-click for real-time protection. |
| Response | Manual search and deletion from mailboxes (if possible). | Automated, one-click remediation across all inboxes. |
| Scope | Focuses only on external threats coming into the inbox. | Protects against internal and external threats. |
This comparison shows why simply having a "spam filter" isn't enough anymore. The fight has moved from blocking obvious junk to outsmarting clever impersonators, and that requires a fundamentally different set of tools.
Connecting Features to Business Outcomes
At the end of the day, the value of these features is measured by their real-world impact on your organization's safety and efficiency. A great technology partner like Typewire doesn't just block threats—it delivers solid business outcomes that strengthen your entire security posture.
For instance, AI-based anomaly detection is what directly stops the BEC attacks that lead to six-figure financial losses. It flags the unusual payment request before your finance team ever has to make a judgment call. Likewise, post-delivery remediation turns a potential company-wide crisis into a minor incident that's cleaned up in minutes, not days. By automating these advanced actions, you free up your IT team to focus on strategic work instead of constantly fighting fires.
Choosing the right partner means finding a platform that not only has these technical capabilities but also respects your company's need for privacy and control. With a secure email hosting solution like Typewire, you get advanced anti-spam and virus protection built-in, ensuring your communications are protected by design. For more practical advice, check out these 8 email security best practices to implement now.
Your Final Business Security Checklist
Think of your email security not as an IT problem, but as a core business strategy. It's about shifting from simply reacting to threats to proactively locking down your digital front door. This isn't just about preventing problems; it's about building the resilience your company needs to grow and thrive.
Success means creating a culture where protecting data is second nature to everyone. The threats are definitely real, but thankfully, the solutions are too. When you combine the right technology with well-trained people and clear, simple procedures, you build a defense that’s both powerful and practical.
Technology and Authentication
It all starts here. The bedrock of your defense is controlling who can send emails that look like they're from you. This is non-negotiable if you want to stop brand impersonation and keep your customers safe.
- Lock Down Your Domain: Get SPF, DKIM, and DMARC in place. These protocols are the single most important technical step you can take to prevent attackers from spoofing your domain and abusing your brand's good name.
- Pick a Modern Security Platform: You need a solution that’s smarter than the average threat. Look for AI-powered detection that understands behavior and context, not just old-school signature matching. This is the only way to reliably catch sophisticated attacks like Business Email Compromise (BEC).
- Insist on Privacy-First Hosting: Where your data lives matters. A secure email host like Typewire, which runs on private infrastructure, ensures your sensitive communications stay under your control and aren't scanned or sold to third parties.
Getting the technology right creates a strong foundation that makes every other security effort that much more effective.
People and Processes
Your employees aren't your weakest link; they're a vital line of defense. When you give them the right knowledge and tools, they become a powerful, active part of your security posture.
Investing in comprehensive email protection is one of the smartest decisions a company can make. It's not an expense—it's an investment in operational continuity, financial stability, and brand trust.
You can neutralize the most common social engineering tricks by creating simple, non-negotiable rules for high-risk situations.
- Make Training an Ongoing Habit: Threats are always changing, so your team's awareness needs to keep up. Run regular phishing simulations and security training to keep their skills sharp.
- Create "Stop and Verify" Rules: For any request involving money transfers, changing payment information, or sharing sensitive data, require out-of-band verification. This means a quick phone call to a number you know is legitimate, not one from the email itself.
- Build a "See Something, Say Something" Culture: Make it incredibly easy—and safe—for employees to report suspicious emails. A fast report from one person can shut down an attack before it spreads and causes real damage.
Your Path Forward
Strong email security isn’t a project you finish; it’s a commitment you live by. It requires continuous attention, regular check-ins, and the willingness to adapt as new threats emerge. By following this checklist, you’re not just buying a piece of software—you’re adopting a comprehensive security strategy.
This blended approach—marrying technology with empowered people and standardized processes—is the key to protecting your company's money, data, and hard-earned reputation. In a world where email is still the #1 way attackers get in, taking proactive control is the best way to ensure your business is built to last.
Frequently Asked Questions

When you're trying to wrap your head around email security, a few common questions always seem to pop up. Let's tackle some of the ones we hear most often from business leaders trying to protect their organizations.
Is Email Security a Major Concern for a Small Business?
Absolutely. In fact, you could argue it's even more critical for smaller companies. Many cybercriminals specifically target small businesses because they bank on them having fewer security resources, making them softer targets.
They're playing a numbers game, and they know a single successful scam, like a BEC attack or stolen login credentials, can be devastating for a small business. That's why strong email security for business is a must-have, regardless of your company's size.
My Employees Are Smart. Do We Still Need Training?
Yes, and that's not a reflection on your team's intelligence. Even the sharpest, most cautious person can be tricked by a sophisticated social engineering attack. Modern phishing scams are masterful at creating a false sense of urgency or mimicking authority to get people to click before they think.
Think of it this way: your security software is the technical safety net, but regular training builds the human firewall. It equips your team to spot the latest tactics and report them, turning your employees from a potential vulnerability into your first line of defense.
Even if a sophisticated threat is removed automatically by a security tool, it was still seen by a user. Training helps employees understand these near-misses, reinforcing the importance of a multi-layered defense and building a stronger security culture.
What Is DMARC and Is It Hard To Set Up?
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It's a powerful standard that stops scammers from "spoofing" your domain—that is, sending malicious emails that look like they came directly from your company. It puts you in the driver's seat, letting you declare which servers are authorized to send mail for your domain.
While it sounds technical (and the setup does involve editing your domain's DNS records), it's gotten much easier over the years. Many modern security platforms and secure email providers offer guided setup wizards that walk you through it. These tools make implementing DMARC a completely manageable task, even if you don't have a dedicated IT security expert on staff.
Ready to take control of your digital communications? Typewire offers secure, private email hosting with advanced anti-spam and virus protection built-in. Start your 7-day free trial and experience true peace of mind. Learn more at the Typewire website.
Email Security for Business Guide
Posted: 2025-07-26
Professional Email Addresses: Your First Line of Defense for Trust and Security
Posted: 2026-02-21
How Do I Block Gmail and Reclaim Your Inbox Privacy
Posted: 2026-02-17
7 Top Canadian Tech Companies Leading in Privacy and Security for 2026
Posted: 2026-02-13
Professional Email Greeting: Master the professional email greeting today
Posted: 2026-02-10
What is Email Phishing: Securing Your Inbox Against Digital Fraud
Posted: 2026-02-06
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27