HIPAA Compliance for Email: Your Complete Security Guide

Understanding HIPAA Email Requirements Without the Confusion
Trying to figure out HIPAA compliance for email can feel like you're lost in a sea of legal jargon. It's easy to get overwhelmed, which can lead to doing too little and risking a data breach, or doing too much and creating a frustrating, slow process for your team. The heart of the confusion usually comes down to one question: when does an email actually need to be HIPAA compliant? The answer isn't "always," and knowing the difference can make your daily operations so much smoother.
Let's look at a real-world example. Say the front desk coordinator at a dental office emails a patient, "Hi Alex, this is a reminder of your appointment with Dr. Smith tomorrow at 10 AM." Even though it's from a healthcare provider, this email doesn't contain any Protected Health Information (PHI). There's no mention of a diagnosis, what the appointment is for, or any billing details. Because of that, it doesn't need to be sent with the heavy-duty encryption that HIPAA requires.
But what if that same coordinator sends another email: "Hi Alex, Dr. Smith asked me to send over the pre-operative instructions for your root canal"? Suddenly, everything changes. The phrase "root canal" links the patient to a specific medical procedure, turning the message into PHI. This email absolutely must be sent through a secure, HIPAA-compliant channel. The critical line is crossed the moment you connect someone's identity to their health information.
Who Needs to Worry About This?
The rules for HIPAA compliance for email don't just apply to doctors and big hospitals. The regulations cover two primary groups: Covered Entities and their Business Associates.
- Covered Entities: These are the organizations providing direct healthcare services. This includes hospitals, private medical practices, dental offices, pharmacies, and health insurance companies.
- Business Associates: This is a broader category that includes third-party vendors who handle PHI for a covered entity. A billing company, an IT provider, a cloud storage service, or an email platform like Typewire would all be considered business associates.
If your work falls into either of these buckets, you have a legal duty to protect any PHI you handle in your emails. This is where a Business Associate Agreement (BAA) becomes essential. It’s a formal contract where a vendor promises a covered entity that they will also follow HIPAA's security rules. A key thing to remember is that the strict email rules only kick in when PHI is present. If there's no PHI, those rules don't apply—a common misunderstanding that can cause a lot of unnecessary work. You can get more details on these rules and see more scenarios over at HIPAA Journal.
Putting It All Together
So, what's the practical takeaway here? The goal isn't to lock down every single email your practice sends. It's about building the awareness to spot PHI before you hit the "send" button.
Train your team to ask one simple question: "Does this email connect a patient's name or identity with their health condition, treatment, or payment details?" If the answer is yes, that email needs to be protected. If it's no, a standard email is probably fine. This simple mental checklist helps your staff work efficiently while keeping patient data safe—finding that sweet spot between security and practicality.
The Hidden Costs of Getting Email Security Wrong
It's tempting to see HIPAA compliance for email as just another box-ticking exercise. But when things go wrong, the fallout is anything but theoretical. The fines are huge, sure, but that's only the start of the story. The real cost is the chaos that erupts from one simple email mistake—a single click that can trigger an organizational disaster, costing years of time, millions of dollars, and the priceless trust of your patients. These aren't just scary stories; they're the real experiences of healthcare organizations that have been through it.

Let's walk through a common scenario. A well-meaning staff member at a mid-sized clinic forwards an internal spreadsheet with patient names and treatment codes to their personal email so they can catch up on work from home. The email isn't encrypted. This one move could set off a chain of devastating events. Later, the employee’s personal account gets compromised in a widespread, unrelated phishing attack, and suddenly, that patient data is in the hands of cybercriminals. This isn't a small internal slip-up anymore; it's a full-blown, reportable breach.
From a Single Email to a Million-Dollar Problem
The numbers behind these incidents are startling. In the year from January 2024 to January 2025, over 180 healthcare organizations suffered email-based HIPAA breaches. The average cost of these breaches to the industry hit an estimated $9.8 million. A high-profile case involved the U.S. Department of Health and Human Services (HHS) settling with Solara Medical Supplies for $3 million after an email breach. That was followed by a separate class-action lawsuit that settled for $9.7 million. These figures highlight the immense financial damage that can result from email security failures. You can dive deeper into these statistics and read the full research about healthcare email security to see the broader trend.
Beyond the headlines and settlement figures, the true cost of a breach is often hidden in the operational storm that follows. The moment a breach is discovered, your organization is thrown into crisis mode.
- Forensic Investigation: You'll have to bring in cybersecurity experts to figure out exactly what happened and how far the damage spread. This process is expensive, disruptive, and can drag on for months.
- Legal Fees: Dealing with HHS investigations and potential lawsuits isn't something you can handle with just any lawyer. You'll need specialized legal counsel, and those bills can quickly climb into the hundreds of thousands, if not millions.
- Remediation and Notification: You are legally required to notify every single person affected. The costs for printing, mailing, and setting up call centers to field patient questions can be enormous.
- Lost Productivity: Your IT team will be completely consumed by the crisis, pulling them from every other important project. Your leadership team will spend countless hours in meetings with lawyers, investigators, and PR firms instead of focusing on what matters most—patient care.
The Unseen Damage: Rebuilding Patient Trust
Perhaps the most significant—and hardest to measure—cost is the erosion of patient trust. A data breach sends a clear message to your patients: the systems meant to protect their most private information have failed. Rebuilding that confidence is a long and difficult journey. Patients might leave your practice, and the negative press can make it incredibly hard to attract new ones.
Administrators who have lived through a breach often talk about the immense personal and professional toll it takes. It's a grueling marathon of damage control, regulatory scrutiny, and public apologies. This is the reality of non-compliance, where the consequences stretch far beyond a financial penalty and strike at the very heart of your organization’s reputation and stability.
Creating Email Policies That Actually Work in Practice
A detailed policy document is a cornerstone of HIPAA compliance for email, but its real value is measured by how well it translates into daily practice. A 30-page binder of rules that nobody reads is worse than useless; it creates a false sense of security. The goal is to build clear, practical guidelines that protect patient data without bringing your clinic’s operations to a grinding halt.
Successful healthcare organizations have learned that policy adoption comes down to one thing: making the rules make sense for the people who have to follow them.

Forget generic templates. Your policies must reflect your specific workflows. For example, a policy that completely bans sending PHI via email might seem secure, but it's impractical for a specialist's office that regularly coordinates care with referring physicians. A better approach is a policy that defines how to send PHI securely, such as mandating the use of your clinic’s encrypted email service and requiring a double-check of the recipient’s address before sending. This acknowledges the reality of healthcare communication while providing a clear, safe procedure.
Assigning Clear Security Responsibilities
One of the biggest hurdles in policy enforcement is ambiguity. Who is ultimately responsible for ensuring compliance? Policies that work in the real world don't just state rules; they assign ownership. This means designating a HIPAA Security Officer—even if it's a dual role in a smaller practice—who is accountable for overseeing the program.
From there, responsibilities are delegated. For instance, the IT manager is responsible for maintaining the encryption software, while the office manager is tasked with conducting quarterly access reviews to ensure former employees no longer have email access. This structure creates a clear chain of command and accountability. When everyone knows their specific role in protecting patient data, compliance becomes a shared team effort rather than an abstract concept. You can find more ideas on building guidelines that get results by checking out our guide on creating an email policy for employees that works.
To help map out these duties, here’s a look at some essential administrative controls and who should manage them.
| Safeguard Category | Required Actions | Responsible Party | Documentation Needed |
|---|---|---|---|
| Security Management | Conduct regular risk assessments of email systems. Develop and implement risk management policies. | HIPAA Security Officer | Risk Analysis Report, Risk Management Plan |
| Access Control | Grant email access based on job roles. Perform quarterly reviews of user access. Terminate access for former employees immediately. | Office Manager/IT Admin | Access Control Policy, User Access Review Logs |
| Training & Awareness | Provide initial and ongoing security training on email policies. Conduct phishing simulations to test staff awareness. | HIPAA Security Officer/HR | Training Completion Records, Phishing Test Results |
| Incident Response | Establish a clear process for reporting potential breaches. Investigate and document all email-related security incidents. | Incident Response Team/Security Officer | Incident Response Plan, Incident Logs & Reports |
This table shows how a clear delegation of duties turns abstract rules into concrete, manageable tasks for your team.
Key Policy Components for Practical Application
To ensure your policies are both complete and user-friendly, focus on these critical areas with clear, actionable language:
- Mobile Device Use: Don't just forbid using personal phones for work email. Instead, create a policy that requires any device accessing company email to have a passcode, enable remote wipe capabilities, and prohibit the use of public Wi-Fi for sending PHI.
- Password Requirements: Instead of a simple "use strong passwords" rule, be specific. Mandate a minimum of 12 characters, a mix of character types, and require changes every 90 days.
- Incident Reporting: Provide a simple, no-blame process for reporting a potential breach. Staff should know exactly who to contact immediately if they realize they've sent an email to the wrong person, without fear of automatic punishment.
By building policies around real-world scenarios and clear responsibilities, you move from a theoretical compliance document to a living guide that actively protects your organization and your patients.
Encryption Solutions That Don't Drive Your Team Crazy
Let's be honest: technical security measures are often seen as a necessary evil, something that just slows everyone down. But when it comes to HIPAA compliance for email, the right encryption solution can blend into the background, giving you solid protection without becoming a daily headache for your team. The secret is finding an approach that fits your actual workflow, not forcing your workflow to fit a clunky tool. From what I've heard from IT pros in the trenches, the best solutions are the ones users barely notice.
A very common method you'll see is Transport Layer Security (TLS). Picture TLS as a secure, private tunnel built between your email server and the recipient's. As long as both ends support it, the email is protected while it's flying across the internet. Many modern email providers, including Typewire, use TLS automatically. It’s a great baseline for security because it’s automatic and requires zero extra steps from your staff. The catch? TLS only protects the email during transit. Once it lands in the recipient's inbox, it's no longer encrypted.
The Trade-Off Between Security and Convenience
For true end-to-end protection that covers the email from the moment it's sent to the moment it's read, you need a different approach. This is where end-to-end encryption (E2EE) comes in. It scrambles the message on your end and only unscrambles it for the intended recipient. E2EE is the gold standard for security, but it has a reputation for being difficult, sometimes forcing recipients to log into a separate portal or manage special keys.
This screenshot shows the different technical layers that can be involved in email encryption.
While that might look complicated, modern tools are designed to hide all of this from the user. For a deeper look at choosing the right system, our essential guide to HIPAA-compliant email encryption offers some practical advice. The key is to find a service that makes E2EE feel effortless by integrating directly into familiar email clients like Outlook or Gmail. That way, your team’s process stays pretty much the same.
To help you weigh the options, here’s a quick comparison of the different encryption methods you're likely to encounter.
Email Encryption Solutions Comparison
| Encryption Type | Security Level | Implementation Complexity | User Experience | Typical Cost Range |
|---|---|---|---|---|
| TLS (Transport Layer Security) | Good | Low – Often enabled by default on modern email servers. | Seamless – Invisible to the end-user; no extra steps required. | Usually included with your email service provider. |
| S/MIME (Secure/Multipurpose Internet Mail Extensions) | High | High – Requires manual certificate exchange and management. | Complex – Can be confusing for non-technical users. | Varies; certificates may have an annual fee. |
| Portal-Based Encryption | High | Medium – Integration with your email system is required. | Moderate – Senders have it easy, but recipients must log into a web portal. | Per-user monthly fees. |
| Integrated E2EE (End-to-End Encryption) | Very High | Low to Medium – Depends on the solution; many offer simple plugins. | Seamless – The best solutions integrate directly into email clients (e.g., Gmail, Outlook). | Per-user monthly fees. |
This table shows there's a clear trade-off between security, cost, and how easy the system is for your team and your recipients to use. While TLS is a good start, integrated E2EE offers the best combination of top-tier security and a smooth user experience, making it a strong choice for healthcare organizations.
Making Controls and Audits Work for You
Encryption is just one piece of the puzzle. Strong access controls and detailed audit trails are equally important. It’s not enough to encrypt the data; you also have to control who can access it and keep an eye on that activity. A great first step is implementing multi-factor authentication (MFA), which adds a critical layer of security that’s much harder for an unauthorized person to get past than just a password.
Proper monitoring turns your audit logs from a massive data dump into a powerful security tool. The infographic below shows key metrics from a real healthcare organization's monthly email security audit.
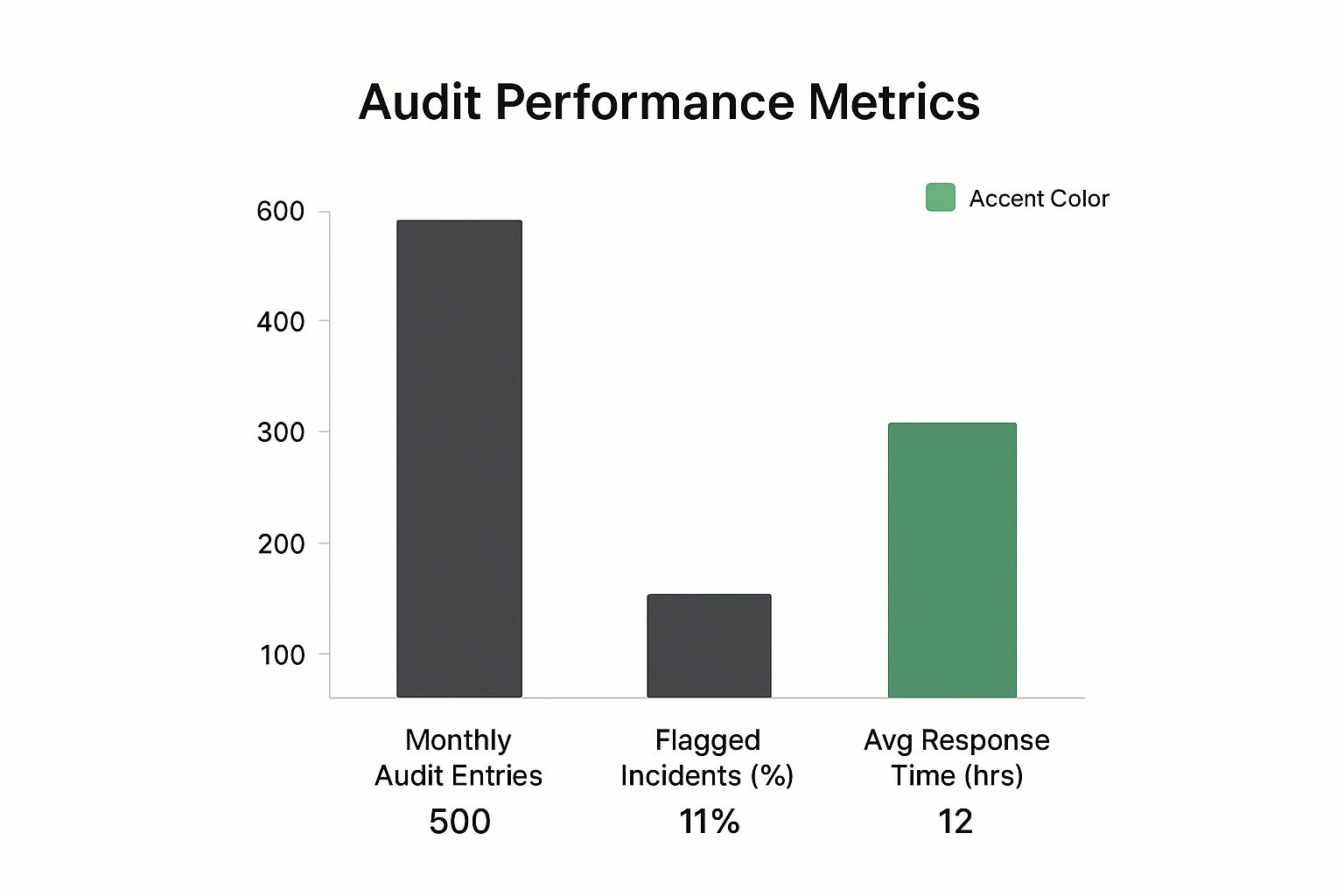
As the data shows, even with a high volume of logged events, the number of flagged incidents is very low and they are handled quickly. This points to an efficient and effective monitoring system. By setting up smart alerts for unusual behavior—like a user suddenly downloading hundreds of emails or multiple failed logins from a new location—you can catch potential breaches before they turn into major problems. This proactive mindset transforms compliance from a reactive chore into a dynamic defense for your organization.
Securing the Infrastructure Behind Your Email System
When we talk about HIPAA compliance for email, encryption often steals the spotlight. However, the security of your underlying infrastructure is just as vital. It's like building a high-tech vault; the strongest door in the world won't matter if the walls are made of plywood. Your email security is only as strong as the physical and network foundations it rests on. For IT directors in healthcare, this means looking beyond the inbox to secure the entire communication chain.

This process begins with the physical location of your servers. Whether they are on-site in a closet or housed in a professional data center, access must be strictly managed. This goes far beyond just a locked door. True physical security involves:
- Logged entry and exit for all personnel.
- Video surveillance covering server areas.
- Clear protocols ensuring only authorized IT staff can physically touch the hardware.
I recall a situation where a clinic learned this lesson the hard way. A third-party cleaning crew was mistakenly given a master key that unlocked their server closet. While no data was actually stolen, the potential for a breach triggered a full-scale internal investigation and a costly overhaul of their access policies. Physical security is your first line of defense.
Fortifying Your Network and Remote Access
Beyond physical safeguards, the way your network is structured plays a massive part in your defense. A "flat" network, where every single device can see and communicate with every other device, is a huge liability. Imagine a scenario where a receptionist’s workstation is compromised with malware. On a flat network, that attacker could potentially move sideways and gain access to the email server with alarming ease.
This is where network segmentation becomes a lifesaver. By creating separate, isolated zones within your network, you can effectively contain threats. For instance, your email server should reside in a highly restricted zone, protected by a firewall from general-use areas like the guest Wi-Fi network or administrative workstations. This setup ensures that even if a less critical part of your network is breached, the path to your sensitive email data is blocked.
Remote access policies are another frequent weak spot. As more staff members work from home, simply providing VPN access isn't enough. Your policy must be explicit, mandating that any device connecting to your network—whether it's a company-issued laptop or a personal computer—meets strict security standards. This includes running up-to-date antivirus software and having an active firewall.
Planning for the Unexpected: Backups and Recovery
Finally, a solid backup and disaster recovery plan specifically for your email system is absolutely non-negotiable. It isn't a question of if you'll face an emergency, but when. Your plan should be detailed and regularly tested. Make sure it includes:
- Regular, encrypted backups of all email data.
- Storing these backups in a separate and secure physical location.
- A well-documented procedure for restoring email services quickly to maintain continuity of care.
The organizations that navigate emergencies most effectively are always the ones that have tested their recovery plans before a crisis hits. Running drills to restore a single mailbox or even the entire server can reveal surprising gaps in your strategy while the stakes are low. By layering these infrastructure defenses, you build a resilient environment that guards against a wide range of threats, from complex cyberattacks to simple human error.
Selecting Email Solutions That Actually Meet Your Needs
Picking an email platform is already a big decision, but when you add the layer of **HIPAA compliance for email**, it can feel downright daunting. You’ll find the market is crowded with services that all say they’re “HIPAA compliant,” but that term can be misleading. The reality is that no software is compliant on its own; it’s a partnership between your organization and the vendor. You’re looking for a partner who not only provides the right security tools but is also willing to legally back their services.
Your search for an email provider has to begin with one critical, non-negotiable document: the Business Associate Agreement (BAA). This is a formal contract where the vendor promises to protect any Protected Health Information (PHI) they manage for you, just as HIPAA requires. If a provider seems hesitant or flat-out refuses to sign a BAA, that's your cue to walk away. It’s a major red flag that they aren't equipped to handle the legal duties that come with healthcare data.
Beyond the BAA: Features That Truly Matter
With the BAA confirmed, it's time to look at the actual features. A flashy dashboard is nice, but it doesn't do much for security. Instead, focus on the tools that will directly support your compliance and make daily work easier for your team.
- End-to-End Encryption: This is an absolute must. The best solutions make encryption almost invisible to your staff. Look for services that plug directly into familiar platforms like Outlook or Gmail, as this avoids the headache of teaching everyone a clunky new system. The goal is to make the secure path the easiest one to take.
- Access Controls and Audit Logs: You need precise control over who can see what. Your chosen platform must let you manage user permissions with ease and provide detailed audit logs. These logs, which track who accessed which emails and when, are vital if you ever need to investigate a security incident.
- Integration Capabilities: Your email service is part of a larger ecosystem. Think about how a new platform will connect with your existing Electronic Health Record (EHR) system or other practice management software. Seamless integration prevents data from getting trapped in separate systems and keeps your workflows running smoothly.
If you're looking for a detailed analysis of providers who do these things well, you might find our comparison of the top 7 HIPAA compliant email hosting providers in 2025 helpful.
Balancing Security, Cost, and User Adoption
Even the most common consumer email platforms can be used in a HIPAA-compliant way, but it's not a simple plug-and-play setup. It demands very specific configuration.
Here is an example of what a common consumer email platform interface looks like.
While a familiar interface can make it easier for your team to adapt, you have to ensure the business-grade subscription you choose comes with a BAA and that you've correctly enabled all the required security features. It's important to remember that HIPAA compliance is not the default setting on these platforms; it's a configuration you must actively create and maintain.
Ultimately, the best solution is one your team will actually use. If a system is too difficult, staff might revert to their unsecured personal email accounts to get things done, opening up a huge security vulnerability. It's a good idea to involve your team in the selection process. Running a small pilot test with a few staff members can give you priceless feedback on how user-friendly a system really is. By balancing strong security with user convenience and a practical budget, you can find an email solution that protects your patients' data and helps your practice thrive.
Building a Sustainable Compliance Program That Lasts
Getting your email HIPAA compliant isn't a one-time project you can just check off a list. It’s an ongoing commitment, a living part of your organization's culture that needs regular attention to stay effective. The most successful healthcare organizations I've worked with don't see compliance as a chore. Instead, they treat it as a continuous process of improvement, building smart, sustainable systems that do more than just pass an audit—they actively protect patient data every single day without overwhelming their teams with endless alerts.
This proactive mindset means you stop just reacting to problems after they happen. It's about getting into a rhythm of monitoring, auditing, and fine-tuning your security measures. Think of it like preventive care for your organization. You wouldn't wait for a major illness to visit a doctor; you get regular check-ups. In the same way, a lasting compliance program involves regular "health checks" on your email security to find and fix small issues before they blow up into serious breaches.
From Reactive to Proactive: Monitoring That Matters
The secret to a durable program is switching from a reactive, "firefighting" mode to a proactive monitoring stance. This starts with figuring out what actually needs your attention. Being flooded with thousands of log entries every day is just noise. Instead, you need to concentrate on Key Performance Indicators (KPIs) that give you real, actionable insight into your email security.
For example, a hospital IT director I worked with focused his team on three main metrics:
- Failed Login Attempts: A sudden jump in failed logins from a single account or a specific location can be the first red flag of a brute-force attack.
- Unusual Email Forwarding Rules: A classic move by attackers who've compromised an account is to set up a sneaky rule that forwards all incoming emails to an outside address.
- Large Data Exfiltration Alerts: Keeping an eye on emails with abnormally large attachments being sent outside the organization can help catch unauthorized data transfers in the act.
By setting up automated alerts for these specific, high-risk events, their team can jump on real threats right away instead of wasting time digging through irrelevant data. This approach turns monitoring from a passive, overwhelming chore into a sharp, effective defense.
Audits and Incident Response: Learning from Experience
Regular audits are like a check-up for your compliance program, but they're only useful if they lead to real improvements. A good audit isn't about pointing fingers; it's about uncovering weak spots in your process. For instance, a quarterly audit might show that several former employees still have active email accounts—a common but very serious mistake. The solution isn't just to disable those accounts, but to update the employee offboarding checklist so that HR and IT are perfectly in sync from now on.
This dedication to learning becomes absolutely vital when you're dealing with a security incident. A well-practiced incident response plan is a must-have. It should spell out exactly who to contact, how to contain the threat, what your legal obligations are for breach notifications, and—most importantly—how to perform a post-mortem analysis. Learning from a real-world incident, or even a close call, provides lessons that no training manual can replicate. Every event, big or small, is a chance to make your defenses stronger. This cycle of monitoring, auditing, and learning is what transforms compliance from a static checklist into a dynamic asset that protects your patients and your reputation for years to come.
Ready to build a compliance program on a foundation of effortless security? Typewire provides the secure, private email hosting you need, with robust encryption and clear controls that make ongoing management simple. Start your free trial today and see how easy sustainable compliance can be.
HIPAA Compliance for Email: Your Complete Security Guide
Posted: 2025-06-24
10 Email Retention Policy Best Practices for Security and Privacy in 2026
Posted: 2026-02-03
Top 12 Secure Alternatives to Gmail for Privacy in 2026
Posted: 2026-01-31
What Is Email Alias: A Guide to Better Email Security and Privacy
Posted: 2026-01-27
How to Send an Encrypted Email and Protect Your Digital Privacy
Posted: 2026-01-23
Email Hosting Canada The Definitive Guide to Privacy and Security
Posted: 2026-01-20
How to Send Email Securely: A Guide to Real Privacy & Security
Posted: 2026-01-16
Why Am I Getting So Many Junk Emails? A Guide to Email Security and Privacy
Posted: 2026-01-13
How to Disable Email Tracking and Protect Your Email Privacy
Posted: 2026-01-09